当前位置:网站首页>FatMouse' Trade (Hangdian 1009)
FatMouse' Trade (Hangdian 1009)
2022-07-07 20:59:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack .
FatMouse’ Trade
Time Limit : 2000/1000ms (Java/Other) Memory Limit : 65536/32768K (Java/Other)
Total Submission(s) : 1 Accepted Submission(s) : 1
Font: Times New Roman | Verdana | Georgia
Font Size: ← →
Problem Description
FatMouse prepared M pounds of cat food, ready to trade with the cats guarding the warehouse containing his favorite food, JavaBean. The warehouse has N rooms. The i-th room contains J[i] pounds of JavaBeans and requires F[i] pounds of cat food. FatMouse does not have to trade for all the JavaBeans in the room, instead, he may get J[i]* a% pounds of JavaBeans if he pays F[i]* a% pounds of cat food. Here a is a real number. Now he is assigning this homework to you: tell him the maximum amount of JavaBeans he can obtain.
Input
The input consists of multiple test cases. Each test case begins with a line containing two non-negative integers M and N. Then N lines follow, each contains two non-negative integers J[i] and F[i] respectively. The last test case is followed by two -1’s. All integers are not greater than 1000.
Output
For each test case, print in a single line a real number accurate up to 3 decimal places, which is the maximum amount of JavaBeans that FatMouse can obtain.
Sample Input
5 3
7 2
4 3
5 2
20 3
25 18
24 15
15 10
-1 -1Sample Output
13.333
31.500// This is a simple greedy problem . It means that rats have m Bang cat food , By giving cat food data[i].b Be able to exchange data[i].a, Ask how much food you can exchange at most .// Just put data[i].a/data[i].b The value of can be sorted from large to small . #include<stdio.h>struct st{ double a; double b; double c;}data[1000];int main(){ int i,j,m,n; struct st data[1000],t; while(scanf("%d %d",&m,&n)&&(m!=-1||n!=-1)) { double sum=0.000; for(i=0;i<n;i++) { scanf("%lf %lf",&data[i].a,&data[i].b); } for(i=0;i<n;i++) { for( j=i+1;j<n;j++) { if((data[i].a/data[i].b)<data[j].a/data[j].b) { t=data[i]; data[i]=data[j]; data[j]=t;} } } for(i=0;i<n;i++) { if(m-data[i].b>=0.001) { sum+=data[i].a; m-=data[i].b; } else { sum=sum+m*data[i].a/data[i].b; break; } } printf("%.3lf\n",sum); } return 0;}Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116298.html Link to the original text :https://javaforall.cn
边栏推荐
- Postgresql数据库character varying和character的区别说明
- Intelligent transportation is full of vitality. What will happen in the future? [easy to understand]
- How to choose financial products? Novice doesn't know anything
- [paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System
- Mongodb learn from simple to deep
- 微服务远程Debug,Nocalhost + Rainbond微服务开发第二弹
- Measure the height of the building
- Object-C programming tips timer "suggestions collection"
- Helix QAC 2020.2 new static test tool maximizes the coverage of standard compliance
- Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]
猜你喜欢

ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your
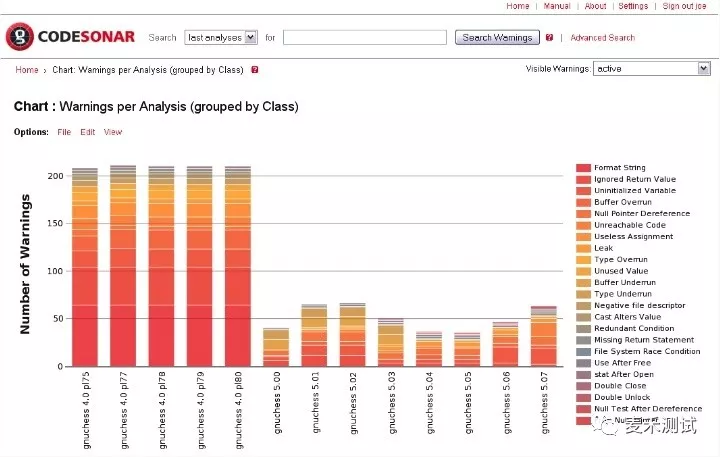
软件缺陷静态分析 CodeSonar 5.2 新版发布
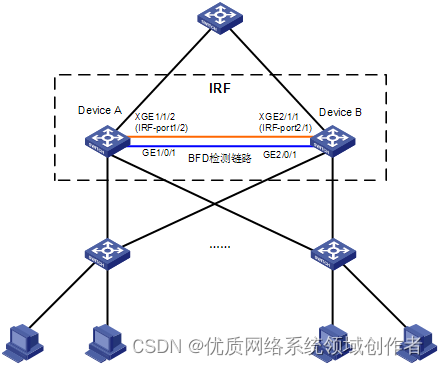
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
Codesonar enhances software reliability through innovative static analysis

ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your
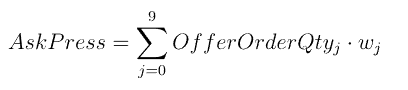
复杂因子计算优化案例:深度不平衡、买卖压力指标、波动率计算

H3C S7000/S7500E/10500系列堆叠后BFD检测配置方法

【论文阅读】MAPS: Multi-agent Reinforcement Learning-based Portfolio Management System
![[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System](/img/76/b725788272ba2dcdf866b28cbcc897.jpg)
[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System
解决使用uni-app MediaError MediaError ErrorCode -5
随机推荐
Klocwork code static analysis tool
ERROR: 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your
Micro service remote debug, nocalhost + rainbow micro service development second bullet
Codeforces 474 F. Ant colony
目标:不排斥 yaml 语法。争取快速上手
Codesonar enhances software reliability through innovative static analysis
软件缺陷静态分析 CodeSonar 5.2 新版发布
现在网上开户安全么?想知道我现在在南宁,到哪里开户比较好?
智能交通焕发勃勃生机,未来会呈现哪些巨变?[通俗易懂]
Solve the problem that the executable file of /bin/sh container is not found
Object-C programming tips timer "suggestions collection"
论文解读(ValidUtil)《Rethinking the Setting of Semi-supervised Learning on Graphs》
Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
如何满足医疗设备对安全性和保密性的双重需求?
上海交大最新《标签高效深度分割》研究进展综述,全面阐述无监督、粗监督、不完全监督和噪声监督的深度分割方法
OneSpin 360 DV新版发布,刷新FPGA形式化验证功能体验
95年专注安全这一件事 沃尔沃未来聚焦智能驾驶与电气化领域安全
Apifox interface integrated management new artifact
MySQL约束之默认约束default与零填充约束zerofill
Codeforces Round #296 (Div. 2) A. Playing with Paper[通俗易懂]