当前位置:网站首页>The essence of transaction and the principle of deadlock
The essence of transaction and the principle of deadlock
2020-11-06 21:35:00 【Irving the procedural ape】
Only with MySQL and spring For example ,, This article does not introduce the concepts of transactions and locks .
This paper uses pseudo code to represent method code , Only express the meaning of the method and transaction annotation
〇、 The shape of the transaction
In my heart , Business has always been like this 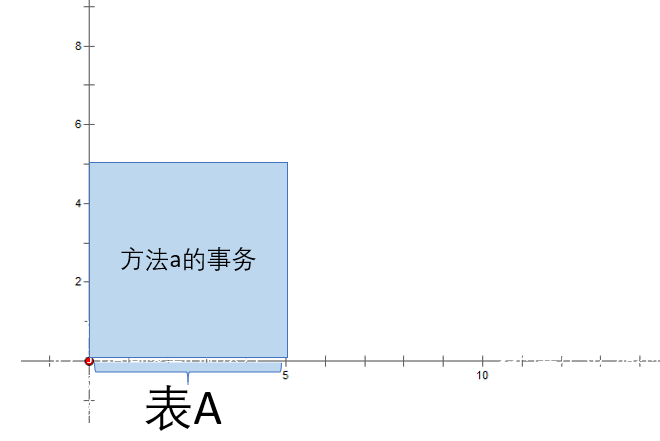
x Axis is a locked resource ,y The axis is the time consumed ,
The transaction box moves down over time ,
When touching x Lock the shaft , Skip over x When the axis is unlocked
The picture above is about the method a The transaction shape of , I named it 【 Transaction box 】, I'm sorry I don't know how to do motion maps , In this paper, we express the best by moving graph .
@Transactional function a(){
Yes A Table modification , It took five seconds }
One 、 A lot of business
When a method calls multiple child methods annotated by a transaction, the situation is 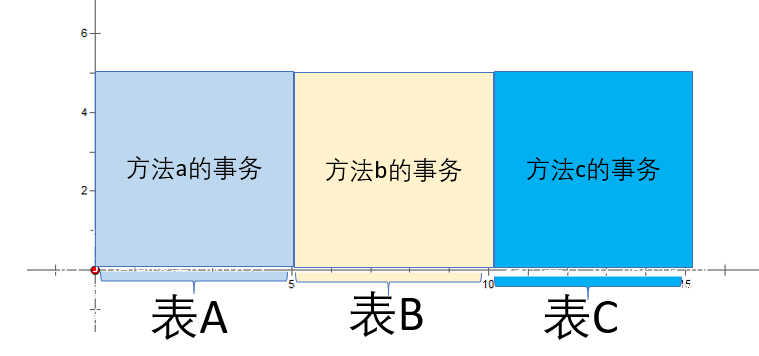
The picture above is about the method abc Invocation time ,a Method 、b Method 、c The transaction shape of the method function abc(){
this.a(){}
this.c(){}}@Transactional function a(){
Yes A Table modification , It took five seconds }@Transactional function b(){
Yes B Table modification , It took five seconds }@Transactional function c(){
Yes C Table modification , It took five seconds }
among abc When the method starts to execute , Execute to a Method , lock a surface , When a Method end b At the beginning of the method ,a Table unlocking ,b Table locking , When b Method end c At the beginning of the method ,b Table unlocking c Table locking .
It is equivalent to that the three transaction blocks in the figure below are united and locked together , Total operation time 15 second 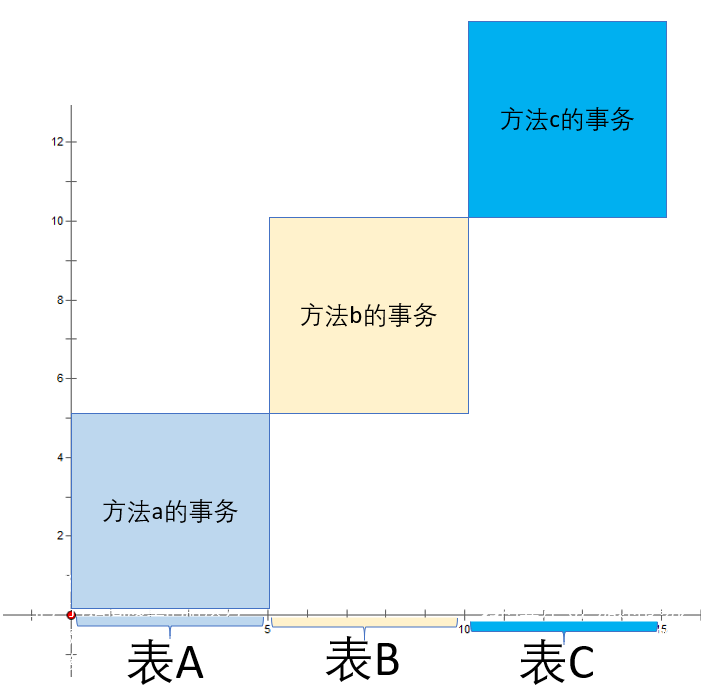
If concurrent requests are made twice abc Method, the transaction box is shown in the figure below 
among a The watch will be asked first 1 lock 5 Seconds later to unlock , Be asked again 2 lock 5 second ,
among b The watch will also be requested first 1 lock 5 Seconds later to unlock , Be asked again 2 lock 5 second ,
among c The watch will also be requested first 1 lock 5 Seconds later to unlock , Be asked again 2 lock 5 second ,
The request 1 In the unlock table a And then it locked the watch b Five seconds , At the same time a Be asked again 2 lock 5 second
By analogy , request 2 All asking for 1 After unlocking the corresponding table , Lock the table ,
So the total running time 20 second
Two 、 Large transactions @Transactional function abc(){
this.a(){}
this.b(){}
this.c(){}}
funct.........
版权声明
本文为[Irving the procedural ape]所创,转载请带上原文链接,感谢
边栏推荐
- 消防器材RFID固定资产管理系统
- 预留电池接口,内置充放电电路及电量计,迅为助力轻松搞定手持应用
- ERD-ONLINE 免费在线数据库建模工具
- Countdown | 2020 PostgreSQL Asia Conference - agenda arrangement of Chinese sub Forum
- 非易失性MRAM存储器应用于各级高速缓存
- image operating system windows cannot be used on this platform
- PHP application docking justswap special development kit【 JustSwap.PHP ]
- ES6 learning notes (4): easy to understand the new grammar of ES6
- 打工人好物——磨炼钢铁意志就要这样高效的电脑
- 2020-08-15:什么情况下数据任务需要优化?
猜你喜欢

意派Epub360丨你想要的H5模板都在这里,电子书、大转盘、红包雨、问卷调查……

What the hell is fastthreadlocal? The existence of ThreadLocal!!

Will blockchain be the antidote to the global epidemic accelerating the transformation of Internet enterprises?
![What grammar is it? ]](/img/3b/00bc81122d330c9d59909994e61027.jpg)
What grammar is it? ]

ES中删除索引的mapping字段时应该考虑的点

How about small and medium-sized enterprises choose shared office?

2020-08-19:TCP是通过什么机制保障可靠性的?

window系统 本机查找端口号占用方法

2020-08-14:数据任务的执行引擎用的哪些?
![Tron smart wallet PHP development kit [zero TRX collection]](/img/3b/00bc81122d330c9d59909994e61027.jpg)
Tron smart wallet PHP development kit [zero TRX collection]
随机推荐
To Lianyun analysis: why is IPFs / filecoin mining so difficult?
An article takes you to understand CSS gradient knowledge
The native API of the future trend of the front end: web components
迅为-iMX6ULL开发板上配置AP热点
How about small and medium-sized enterprises choose shared office?
Exclusive interview of guests at | 2020 PostgreSQL Asia Conference: Wang Tao
Some operations kept in mind by the front end foundation GitHub warehouse management
Take you to learn the new methods in Es5
小熊派开发板实践:智慧路灯沙箱实验之真实设备接入
What the hell is fastthreadlocal? The existence of ThreadLocal!!
Zero basis to build a web search engine of its own
2020 database technology conference helps technology upgrade
谷歌浏览器实现视频播放加速功能
迅为iMX6开发板-设备树内核-menuconfig的使用
Swagger 3.0 brushes the screen every day. Does it really smell good?
STM32F030K6T6兼容替换灵动MM32F031K6T6
Road to simple HTML + JS to achieve the most simple game Tetris
2020-08-20:GO语言中的协程与Python中的协程的区别?
Can you do it with only six characters?
jenkins安装部署过程简记