当前位置:网站首页>[trusted computing] Lesson 13: TPM extended authorization and key management
[trusted computing] Lesson 13: TPM extended authorization and key management
2022-07-07 18:01:00 【Godams】
TPM2.0 Has unified all by TPM The authorization mode of the controlled entity . The previous chapters have discussed passwords and HMAC Authorization data required for authorization . This chapter will discuss in detail TPM A new and very powerful authorization method — Extend Authorization , Also known as policy authorization .
Policy authorization : If a user wants to restrict an entity from being used only under certain circumstances , The sum of all restrictions on the use of this entity is called a policy .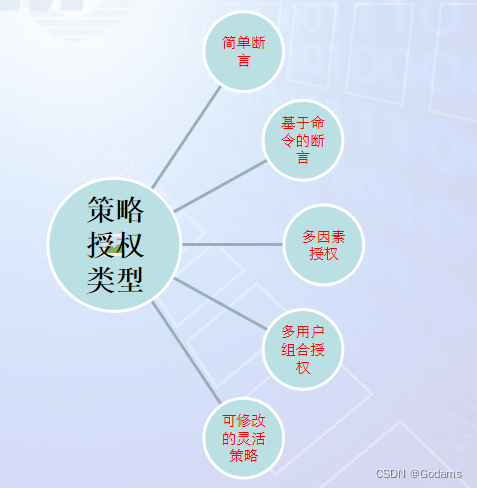
Policy authorization and password authorization
all TPM Entities can be authorized in two basic ways . The first is the password associated with the entity creation period , The other is the strategy associated with the entity when it is created .
Some by TPM The entity created by the system itself has a default access password and policy ( Such as various basic organizational structures 、 Dictionary attack reset handle ). Such entities have fixed names , It does not depend on the accompanying strategy , At the same time, these strategies can be changed .
Many entities ( Such as NV Index and key ) The name of is calculated by hashing according to the policy assigned when they are created , So the password to access these entities can be changed , But its access policy cannot be changed , The authenticity of the modified entity cannot be verified .
Anything that can be done directly with a password can also be done through strategy , But the opposite is not true , Some things ( Such as key replication ) Authorization can only be done through policies .
Policy authorization is more flexible , The strategy can be finely adjusted . You can set the policy to never be satisfied NULL Strategy , You can also provide different authentication methods for individual commands or different users applicable to an entity through policies .
Advantages of policy authorization
Authorization that allows multiple changes ( password , Biological information, etc ).
Allow multi factor authorization ( More than one authorization type ).
Allow when not in use TPM To create a policy . The policy itself does not contain any secret information , So it can be completely created by software . But this is not to say that a strategy does not require secret information .
Policies that allow authentication associated with an entity . In order to use entities , It should be possible to prove which authorizations are necessary .
Allow multiple users or roles to meet a policy .
It allows the function of a specific role of an object to be limited to a specific operation or user .
Fixed a PCR The problem of vulnerability . stay TPM1.2 in , If an entity is “ lock ” To a group containing a specific configuration PCR in , Once the configuration has to be changed , Then this entity cannot be used .
Multifactor certification
Many different kinds of technologies and devices are used for licensing . Password is the oldest way of authorization ( Perhaps the weakest ). Biological information, such as fingerprints , Iris scanning , Face recognition , Handwritten signature , Even the heart rate can be used to authorize . Digital signatures and HMAC It is an encrypted authentication form used in a token or key . The bank clock takes the time of day as authorization information , It does not allow the vault to be opened outside trading hours .
Multifactor authentication is one of the manifestations of security , And it is very popular nowadays . To authorize the execution of a command , Multiple authorization methods are required . These authorizations can take many forms —— The smart card , password , Biological information, etc . The basic principle is that attacking multiple authorizations is more difficult than attacking only one . Different types of authorization have different advantages and disadvantages . for instance , Passwords can be easily provided remotely —— But fingerprints are not that easy , Especially when the design is correct .
password .
HMAC.
Smart cards that provide digital signatures .
Physical existence / Contact (Physical presence).
The state of the machine (PCR).
TPM The state of ( Counter , Time ).
Status of external equipment ( Fingerprint card reader ,GPS wait ).
Each mechanism used for authentication is called assertion .
How extended authorization works
A policy is a hash value that can represent a set of authorizations , Together, these authorizations can describe how to meet a policy . When an entity ( For example, a key ) When the policy is created , It may be associated with a policy . In order to use this entity , Users need to ask TPM Prove that this strategy has been met .
- Create a policy session . When the policy session is started ,TPM A session policy buffer will be created for this session .( The size of the buffer matches the hash algorithm selected when creating the session , And initialize to all 0)
- Used by TPM2_PolicyXXX The command to TPM The session provides one or more authorization information . These operations will change the value of the session policy buffer . These operations may also set some flag bits of the session , These flags are used to indicate TPM Some checks that must be performed when executing commands .
- When a command uses an entity ,TPM The session policy buffer will be compared with the authorization policy of the entity . If the two are different , The command will not be executed .( here , The session flag bits related to policy authorization will also be checked . If they are not satisfied , This command will not be executed ).
The policy does not contain any secret information . in other words , All strategies can be implemented in a pure software way TPM Create . however , To use them ,TPM It must be possible to regenerate these policies ( In the form of a policy summary of the session ). because TPM Have the ability to generate strategies , So allow users to use TPM It is more reasonable to use this function to generate strategies . This is through Trial Strategy to achieve . One Trial Policies cannot be used to satisfy a policy , But it can be used to calculate the hash value of a policy .
The policy session used to satisfy the authorization policy is somewhat better than the one used to create the policy Trial Policy sessions are complex . Some policy commands will immediately check some assertions and update the policy buffer stored in the session . Other commands set flags or variables in the session , These flags and variables are checked when the command is actually executed .
Types of policies that can be created
- Simple assertion strategy : Create a policy using an authentication method . Like passwords , The smart card , Biological information , Time, etc. .
- Multi assertion strategy : Combine several assertions , For example, require biological information and password at the same time ; Or smart cards and PIN code ; Or password , The smart card , Biological information , as well as GPS Location information . Such a strategy is equivalent to using AND Operation combines multiple assertions .
- Hybrid strategy : Logical operations are introduced here OR, for instance ”Bill You can use a smart card to authorize or Sally You can authorize with a password “. Hybrid strategies can consist of any other kind of strategy .
- Flexible strategies : Use wildcards or placeholders , The specific authorization content will be defined later . A specific part of a policy can be replaced by other allowed policies . This looks like a simple assertion , But it's actually arbitrary ( Simple or complex ) Strategies can replace it .
How policy authorization works
A policy is represented as a hash value , This hash value represents the way to meet this policy . A policy starts as a buffer , The buffer size is the hash length corresponding to the hash algorithm of the related entity , The buffer will be initialized to full 0. When some strategies are met , This buffer will be extended to represent this event ( Specifically, it is the execution of policy related commands ) Value . The operation of expanding the buffer is to connect the current value of the buffer with the new data , Then use the specified hash algorithm to hash the above connection results , Update the buffer to this hash value .
Simple assertion strategy
Password or HMAC( You need to TPM prove , The policy that the user knows the password of the object ).
digital signature ( The smart card ).
Certification of external equipment ( A biometric card reader is used to verify the identity of a specific user , Or one used to prove that the machine is in a specific position GPS equipment ).
Physical existence ( It is a switch like indication , It can prove that a user can physically contact TPM. Although this is defined in the specification , But it may not happen , So we will ignore this function later ).
PCR(TPM The state of the host device ).
Locality( Means to send out TPM The system privilege level of the software of the command ).
TPM Internal state ( Counter value , Timer value, etc ).
General steps for creating assertion policies
Create a Trial Policy session , Execute the following command :
TPM2_StartAuthSession
( Pass a parameter TPM_SE_TRIAL inform TPM Start a Trial conversation , You also need a parameter of the hash algorithm to calculate the value of the policy . This command will return the... Of the session handle, It can be called myTrialSessionHandle)Execute the TPM2 Policy command .
Request by executing the following command TPM Create hash value of policy
TPM2_PolicyGetDigest
This command needs to be passed Trial The session Handle:myTrialSessionHandle.End the session by executing the following command
TPM2_FlushContext
This command also needs to be passed Trial The session Handle:myTrialSessionHandle.
step 1,3,4 All simple assertions are common , There are only steps 2 It's unique .
Create password based ( Plaintext and HMAC) Assertion strategy for :
- Configure the policy buffer and clear , The buffer length is set to the output length of the hash algorithm .
Initialize policy values : 0x0000…0000 - Match the buffer with TPM_CC_PolicyAuthValue come together .
Change value :0x0000…0000TPM_CC_ Strategy AuthValue - according to TPM2.0 Regulation No 2 Some will TPM_CC_PolicyAuthValue Replace with the corresponding value ( Example )
Change value :0x0000…00000x0000…000016B - Calculate the hash value of the value after the above connection , Then put the result in the buffer . The final result is a simple asserted policy value :0x8fcd2169ab92694…1fc7ac1eddc1fddb0e
In the current example ,TPM_CC_PolicyAuthValue Will be set by the caller to the value related to the password .
utilize HMAC Assert authorization
Method is similar to plaintext password , Just set up different TPM_CC_PolicyAuthValue.
Set up TPM_CC_PolicyAuthValue value
stay TPM A flag is set in the session of to indicate TPM, When an object used by a command needs to be authorized by this policy , Need an independent HMAC conversation .TPM Will check the HAMC Value and compare it with the authorization value of the object , Access is allowed only if it matches .
utilize PCR( The state of the machine ) To authorize
TPM Medium PCR It is usually used by the software before and after startup , Thus, it is used to indicate the status of the current system running software . stay TPM1.2 In the design of , Only a few functions can use this authorization . What's worse is , Because use PCR to grant authorization TPM1.2 The key of is a very fragile operation , This restriction also makes PCR Difficult to use for authorization .
TPM2.0 The design of allows for PCR Used to authorize any command or entity . The policy only needs to specify that it is referenced PCR And the corresponding hash value . in addition ,TPM2.0 There are many ways to deal with PCR The fragility of . All policies consist of a full size corresponding to the hash algorithm 0 The buffer starts . In order to use PCR Assertion , The policy will be extended with the following values :TPM_CC_PolicyPCR||PCRs selected||digest of the values to be in the PCRs selected.
In case the above assertion is passed PCR What if the value of changes ? In execution TPM_PolicyPCR On command ,TPM Will pass the record TPM In session state PCR Generate counters to prevent such vulnerabilities . When a policy session is being used for authorization of a command ,TPM Will check the current PCR Whether the counter of matches the previously recorded value , If it doesn't match , Then this session cannot be used for authorization .
Use the location of the command to authorize
TPM1.2 There is a feature in the design of version called Locality, It is used to decide to send to TPM What kind of software stack does the device command come from .TPM1.2 in ,Locality The main purpose of is to prove CPU In a special mode , This special mode refers to entering Intel TXT perhaps AMD-V Command mode ( These two modes are located in Intel and AMD Of CPU in ). These commands are mainly used to perform dynamic trust root measurement when the machine is in an untrusted system running state (DRTM), In this way, the status of the software can be reliably reported .
stay TPM2.0 in , It's like PCR Assertions are extended to any authorization Application ,Locality It is also extended to general assertion operations . When an assertion of a policy is used Locality when , The policy summary of the session will be extended by the following values :TPM_CC_ Strategy Locality||locality(ies).
When a conversation needs to be satisfied Locality When asserting , Users also need to use TPM2_PolicyLocality Command to pass the Locality Information . At this time, the following two things will happen :
- The summary of the session is extended by the following values :TPM_CC_PolicyLocality||locality(ies).
- The variables of a session are set as the parameters of the command Locality.
When the user uses this session to execute commands ,TPM Will compare Locality Information ( Check out PTP Normative Bit Protocol) And variables recorded before the session Locality Information . If it doesn't match , The command will not be executed .
Locality It can be applied in many places . It can be used to represent the source of the command to create entities . They can also be used to bind some functions to specific software . stay 1.2 in ,Locality Will be used to put CPU Specific to reset and expansion PCR Bind together ( such as PCR17,18), This is for DRTM Previously reset the machine to a known state .SourceForge Upper tboot The software shows how it works Locality Of ; From CMU Of Flicker Use tboot With the OS Perform safety related operations in independent memory space .
therefore ,Locality Will tell TPM What software does the current command come from ( Or hardware ). because TPM I already know the specific information of the order (TPM When parsing commands, you can use Bit Protocol It is concluded that Locality Etc ),Locality Can be used to authorize .
utilize TPM Internal state of ( Boot counters and timers ) To authorize
TPM1.2 The device has an internal timer for measuring TPM Time elapsed since last startup ( This value may be related to external time ), There is also an internal one-way counter . But neither of these features can be used for authorization .TPM2.0 There is a timer , A clock , And start counter , They can provide new assertions through complex configurations . The start counter is used to record the number of times the device has been started . Timers are used to record TPM The time elapsed after the device is started . A clock is much like a timer , But the clock can only be updated forward , And can be set to the same value as the external time , stay TPM Stop working after power failure ( This is the same as that on the motherboard RTC Would have been different , This clock doesn't need extra battery power ).
These features can be used to limit TPM The entity can only start when the counter does not change , Or the clock is used in a certain period of time . The use of entities can also be limited to the time of day . The latter is the most likely application scenario —— Restrict file access to a computer to daytime working hours , This helps prevent hackers from illegally accessing files at night .
TPM You can always check the values of the internal clock and the start counter , So they are called internal states . The internal state assertion requires that a policy session be created before the authorized command is executed , And these assertions are passed before the command is executed . These assertions do not necessarily pass when the command is executed .
utilize NV Memory location for authorization
TPM2.0 A new command has been added to the specification , It is used to use specific NVRAM Area stores values to authorize TPM Access to entities . for instance , If one NV The index corresponds to one 32 Memory area of bits , You can use the state of one of them to control TPM Access rights of entities . If every bit is assigned to different users , The permission of a user to access a specific entity can be modified NVRAM In response to the value of the bit to undo or enable . Of course , This also means that you have permission to write this NVRAM People in the region have the highest access to the key .
The function of this command is more than that , because TPM Allow for NVRAM The area performs logical operations . So you can set the following assertion conditions :
6 <= NVRAM location < 8 OR 9 < NVRAM location < 23
TPM2.0 Of NVRAM Areas can be configured as counters . This means that you can configure counters to be used only through flexible configuration in the policy n Time .
Such a policy requires extending the policy buffer to the following values :TPM_CC_PolicyNV||calculated Value||name of NV location.calculated value Express HASH(value to compare to || offset inito the NVRAM location) || number that represents the operation)
Treat an entity as a lock , that NVRAM The value in the field is like the brake bolt of the lock . If their values are correct , You can use this entity . If the internal state of the entity is correct , The lock will be opened .
Use external device status (GPS, fingerprint identification device ) To authorize
TPM2.0 The most interesting new assertion in design is , Assertions depend on the state of an external device . This external device can represent a public-private key pair . The state of a device can be anything that can be signed with its private key ( Of course, it should be combined TPM Produced nonce value ). If the device is a biological information device , The form of authorization can be “Bob Proved his identity to me ”. If the device is a GPS equipment , That's it “ My current location is Baltimore ”. If it is a time service , The assertion may be “ The current time is trading time ”. Related assertions will identify the public key representing the device and the value representing the device state ( A signature value ).TPM Just compare the signature with the expected authentication information .TPM No further calculations will be made on the results of the comparison , So it is (making the representation) The device needs to decide that its input is consistent with its signature .
This feature provides flexibility for biological information : If Bob Registered the fingerprints of several fingers with the fingerprint recognizer ,TPM There is no need to know which fingerprint information is signed —— Just know that the fingerprint corresponds to the user Bob. One GPS The equipment does not need to be particularly accurate —— Just a designated area . Assertions do not need to specify a particularly precise time , Instead, specify an acceptable period of time . But this flexibility is not completely universal . This is not to say “ Some fingerprint recognizers have proved Bob The device has been authenticated ”; But rather “ This particular fingerprint recognizer has proved Bob The device has been authenticated ”. This allows the creator of the strategy to decide to use his trusted biometric devices , So as to prevent being easily deceived .
Once this strategy is met , There is no further inspection , So it is possible to execute a command , Relevant assertions can no longer be passed .
Create such a strategy It is also composed of a full 0 The buffer starts . Then the buffer will be expanded by the following values :TPM_CC_PolicySigned||SHA256(publicKey)|| stateOfRemoteDevice,stateOfRemoteDevice There are two parts : The size of the description , And the description itself .
If you use Trial Session creation strategy , You need to perform TPM2_ Strategy Signed command . Explain again , Must pass Trial The session handle, The public key corresponding to the private key of the device handle, Status of the remote device . for instance , If the remote device is a fingerprint recognizer , It can sign this message “Sally correctly authenticated”.
Use wildcards for authorization
TPM1.2 A major problem in design is PCR Too fragile . When an entity is locked to a PCR after , You can't change it PCR The value of the .PCR0 Used to represent BIOS The firmware , Security is important . If PCR0 The value of has changed , That may indicate a security vulnerability . Microsoft BitLocker Applications use it to provide security . however ,BIOS Firmware may need to be upgraded . When the upgrade is complete ,PCR0 Will change , That makes it locked to the old PCR Value entities can no longer be used .
Applications can bypass this PCR The limitation of , It is through upgrading BIOS Decrypt the previously locked key , Then upgrade , Finally, use the new PCR0 To lock the key . But this process is very cumbersome , And upgrading BIOS During this period, these keys are in clear text . therefore ,EA It can be modified PCR But it is important not to decrypt the locked data . But it still needs to clearly check under what circumstances the strategy can change . Many possible solutions have been considered , Including adding an authorization specifically for modifying this policy .
The final solution is clever , It uses TPM2_PolicyAuthorize Command to implement , I call this method the coordinated strategy . When playing poker , A general distribution card can replace any card that the general distribution card holder wants to replace . A generic strategy can also replace any strategy that the holder wants to change . Go further , Any policy agreed by the generic policy owner can be used to meet this generic policy . When creating a generic policy , Through a wildCardName Parameters to limit policy . This means that the owner of a generic policy can choose a policy with a specific name to meet the generic policy . With a OEM Of BIOS In theory, the general allocation strategy related to the signature key can be used by any process BIOS Signature policy replacement .
The creation method of general configuration strategy is similar to that of using the state of external devices . By extending the policy session to :TPM_CC_PolicyAuthorize||keySign->nameAlg||keyName||wildCardName. And strategy Signed The assertion is the same , If you use Trial The strategy of session creation through configuration , First, you need to load a public key to TPM( Use TPM2_LoadExternal command ), Then execute the strategy Authorize command .
TPM2_LoadExternal The command will return the loaded public key handle, It's called aPublicHandle. Then you can execute TPM2_ Strategy Authorize, And transmission Trial The session handle,wildCardName, as well as aPublicHandle.
TPM2_PolicyAuthorize yes TPM One of the most useful strategies in , Therefore, it is the only way to modify the object policy after the object is created . This means that if the object has been locked to a group PCR value ( Corresponding to a specific system configuration ), Then the configuration of the system changed , The policy of the object can be effectively modified in this way to match the new configuration .
Command based assertions
Although this feature is not strictly an assertion ,TPM You can restrict a policy to specific commands . for instance , You can restrict one key to signing but not to authenticating other keys . If this restriction is made , Policy can only be used by this specific command . Generally speaking , This restriction will not be used as a separate assertion , But there is no technical problem if you have to do this . Declare in the policy of a key that this key can only be used for signing , Then this key can neither authenticate other keys nor be authenticated by other keys . This is because when a key is authenticating or being authenticated , It needs to provide authorization that it cannot provide .
To create such policy assertions , You first initialize the buffer matching the hash algorithm to all 0. Then extend with the following values :TPM_CC_PolicyCommandCode||the command code to which the Policy is to be restricted. If using Trial Session to create this policy , You need to perform TPM2_PolicyCommandCode, Deliver at the same time Trial The session handle And the corresponding command code (command code).
Generally speaking , If you restrict an entity, such as a key, to only one command , You should also be able to authenticate the use of this command . This requires more than one restriction on this key , This is the theme of multi-element authentication .
Use multiple factors for authentication and authorization
TPM Know how to use assertions to authenticate . It can also use multiple assertions to do . for instance , Log in to one PC when , Users may need to provide both fingerprint and smart card for identity authentication .
We have seen in the previous introduction , The process of policy creation is similar to PCR The extended operation is similar . They all have a whole set 0 Start with the value of ( The size of this set of values depends on the hash algorithm selected when creating the policy ). When a policy command is invoked , The value of the current policy will be updated , First, extend the new parameter based on the old value , Then hash the result , Finally, replace the old hash value with the new hash value . This operation is PCR It is called extension . A logic for strategy AND Operation is achieved by extending new assertions on the policy . Like a PCR equally , The policy is initialized before the first assertion 0, But then the assertion will be updated on the original basis .
Authorization example 1: Smart card and password authorization
If you want to include a password and use a key signature in the policy, and the corresponding public key is S Smart card assertion , When creating a policy , You can first expand all with the following values 0 The buffer :
TPM_CC_PolicySigned||SHA256(publicKey)||0x0000=0x0000060||SHA256(S)||0x0000```
notes : final 0x0000 Indicates that you have not provided a strategy for signing Reference, So the final value is 2 All zeros of bytes .
Then expand the password related requirements
TPM_CC_PolicyAuthValue=0x0000016B
If you want this order, it can only be in Locality4 In the implementation of , You also need to extend the following values :
TPM_CC_PolicyLocality||Locality4
Extending a new requirement is equivalent to executing a logic AND operation .
Example 2: utilize PC state 、 Password and fingerprint for authorization
Bob Created a key , It requires PCR1 The value of is approvedPCRdigest, A password , And a fingerprint . Use TPM The process of creating this strategy is as follows :
- Start a Trial conversation .
Use TPM2_PolicyPCR Command to lock the policy to approvedPCRdigest. - Use TPM_PolicyAuthValue command ( instructions TPM Enter the password when the command is executed ).
- Load fingerprint recognizer publicKey To TPM in .
- Use TPM2_PolicySigned And pass the public key handle and stateOfRemoteDevice( That is to say “Bob Fingerprint information ”).
- from TPM Get the value of the policy .
- End the conversation .
The composite strategy assumes the following application scenarios :
- Dave When using a machine, use a policy that requires fingerprints and passwords for authentication .
- Dave You can also use passwords and smart cards for authentication .
- Sally Use smart cards and iris scanners for authentication .
- IT Administrators can only use the key copy function , And must be in the system PCR0-5 This operation is authorized through the smart card when it contains a known value .
The first policy specifies Dave It must be through an external device ( fingerprint identification device ) To verify your identity . Then he must provide the password . We have already introduced it before , The specific steps are as follows :
- Start a Trial conversation .
- perform TPM2_PolicySigned command ( Pass the public key of the fingerprint recognizer and the appropriate strategy Ref value ).
- perform TPM2_PolicyAuthValue.
- from TPM Get the value of the strategy , We call it strategy Dave1.
- End the conversation .
The second strategy (Dave2) requirement Dave Enter the password and sign a message from TPM Of nonce value , To prove that he is the owner of the smart card :
- Start a Trial conversation .
- perform TPM2_PolicyAuthValue.
- perform TPM2_PolicySigned command ( Provide the public key of the smart card ).
- from TPM Get the value of the policy . We call it strategy Dave2.
- End the conversation .
The third strategy requires Sally You must first use her smart card to sign one from TPM Of nonce To prove that she is the authorized owner of the smart card , Then authorize herself through external devices , Iris scanner , So that external devices can send TPM prove Sally The identity of the :
- Start a Trial conversation .
- perform TPM2_PolicySigned command ( Use the public key of the smart card ).
- perform TPM2_PolicySigned command ( Provide the public key of iris scanner and appropriate strategy Ref).
- from TPM Get the value of the policy . We call it strategy Sally.
- End the conversation .
Last ,IT The administrator's policy requires the administrator to sign a with its smart card TPM Produced nonce, Then check that the PCR0-5 In the desired state . Further more ,IT Administrators can only use this authorization to copy keys :
- Start a Trial conversation .
- perform TPM2_PolicySigned( Use the public key of the smart card ).
- perform TPM2_PolicyPCR( Pass the selected PCR, And their expectations ).
- perform TPM2_PolicyCommandCode, Pass on TPM_CC_Duplicate.
- from TPM Get the value of the strategy . We call it strategy IT.
- End the conversation .
Key management
Use TPM There are many things to consider when designing a key management system . If the key is used for important operations , Such as encryption or identity authentication , It is important to use an architecture that provides a standard way to manage keys , At the same time, this architecture also takes into account the hardware damage . Such a key management architecture must be able to handle key generation , Key distribution , Key backup , Key destruction .
Key generation
When we generate a key , The most important thing to consider is whether the key is really generated randomly . If you choose a poor random number generator , Then the generated key will be insecure . The second is to ensure the confidentiality of key information .TPM Designed to protect against software attacks . The manufacturer is responsible for resisting hardware attacks , Does not belong to TPM The scope to be considered in the design itself .TPM The design of allows the creation of separate keys , This refers to the entropy used to create the key in TPM Both internal and external storage , thus , When not used TPM when , Even if someone can physically touch TPM, The key is also secure .
Key in TPM There are three forms of existence in . The key can be generated by a seed , from TPM Random number generator of , Or imported into TPM in . The master key is through TPM Generated by seeds in . Used to generate EK The seed of is related to the endorsement key organization structure , And end users are unlikely to modify it .
On the other hand , The seed value related to the storage key organization architecture is TPM received TPM_Clear It changes when it's ordered . This operation can be organized by using the platform BIOS perform , Or the end user can use dictionary attack to reset the password .
Master key usage FIPS Approved KDF Generate ,KDF The main seed and key template will be combined to hash . The template of key generation is divided into two parts . Yes, the first part Description of key type —— Is it a signature key , Specific algorithm and key size , wait . Another part describes The key generation command is used to generate where the entropy of the key comes from . Most of the time , The second part is set to complete 0(TCG Published by the infrastructure Working Group EK There are... In the template ). however , If users don't believe TPM Internal entropy generator , They can use this function to separate the entropy of the key , That is, key generation segmentation .
Key segmentation is a cryptographic construct , It contains two parts of entropy —— Each part has the same entropy as the final key —— Used to generate key . Neither of these two can provide the entropy of the final key of even one bit —— So both of these are necessary . thus , One can be independent of TPM Storage , The other is stored in TPM in .
For a master key , Part of the partition value is the seed of the organization structure corresponding to the key , It exists in TPM in . Another part is stored in TPM In the key template other than , It can be stored in a safe place when not in use ( For example, it is stored in a smart card ).
The master storage key has a symmetric key associated with it , It is generated together with the master storage key . The master key is also derived from the master seed and externally introduced entropy . As long as the seeds related to the organizational structure remain unchanged , Using the same key template will always produce the same master key and related symmetric key . Because both keys use key templates , If entropy is provided by the template , The entropy in the template is also the entropy of partial segmentation .
Generating the master key may take a relatively long time ( If the key is RSA secret key ), Or almost instantly ( If it is ECC secret key ). If key generation takes a long time , The user may decide to store the key in TPM Persistent memory , This is through TPM2_EvictControl Command to achieve , This command requires the authorization of the relevant organizational structure . under these circumstances , The key will be assigned a persistence handle, And power on again will not affect the existence of this key . This key can be erased with the same command . Users can make different attacks according to their concerns , Decide whether to make the key persistent .
If a user is worried TPM The seeds of may be unsafe , Then they will worry that the master key is not secure . If the master key is not secure , All keys stored under this master key are not secure . under these circumstances , Users can introduce their own entropy by using key segmentation through templates , And let the key become a persistent key , Then the template of the key is placed where the attacker cannot access . This prevents you from knowing TPM The attacker of the seed gets the secret information of the master key ( There is no other part of entropy ).
Yes Standard key templates are used to create keys , In general, it is more reasonable to use these templates than to create them yourself . Because the template will use the algorithm of intensity matching . When choosing a symmetric key, you may use an algorithm with mismatched strength .TPM2.0 Load other keys with symmetric keys , Not like it TPM1.2 Use asymmetric keys as in . therefore , We can design a system , The system uses a symmetric key with a higher strength than the asymmetric key used for the master key . Once such a system is implemented , from TPM The generated key will not face the risk of asymmetric key or weak algorithm strength .
Key tree
Although technically , Different algorithms can be mixed —— Use an algorithm to create a key , Then protect the key with a key of a different algorithm —— This is a bad habit ( First , I have seen ,TSS Of FAPI It's not allowed to do that ). The reason why this is problematic is , The overall strength of a group of keys is determined by the key with the weakest strength . That means , Not only should we not mix algorithms , And the key chain ( It is the key behind a key encryption , Such a chain structure ) It should also be as short as possible . If any key in the key chain is destroyed , Then all the keys behind this key have also been destroyed . So in the face of violent attacks , The strength of a key chain composed of four keys is one quarter of that of a single key .
Key duplication
In the key tree , The key that may be copied is a personal key , Enterprise key , Financial key ( Individuals or businesses ), Entertainment key ,HR secret key . In order for the key to be copied , When creating keys, you need to configure them to be replicable , And the key also needs to contain TPM2_PolicyCommandCode Command strategy ,TPM2_PolicyCommandCode The specified command is TPM2_Duplicate. in the majority of cases , A user will create two replication policies —— A personal key , The other is for Business Keys —— And connect them with a personal replicable key (Personal Duplicable Key) And a replicable key for business (Business Duplicable Key) Connect .
If we don't want a key to be copied , You can set the attribute to fixedParent. If a key wants to be independent of its parent key SDK perhaps UDK Be copied , Then the key itself must have a policy that allows replication .
Key distribution
In some cases , Some keys need to be distributed long after the initial configuration of the system . At this time , It is very important that the system can safely distribute keys .TPM The design of can make key distribution simple . When each system is in initial configuration , The system will generate a non replicable storage key , The central management system will record the key and the name of the system where the key is located ( Or the serial number of the system ).Active Directory perhaps LDAP The database can do this . in addition , During the initial configuration of the local platform , The public key corresponding to a signature private key in the central management system will be backed up to the platform .
If the central management system wants to distribute one HMAC When the key is transferred to the local platform , The following steps are performed :
- Central management system IT Department use TPM2_GetRandom Create a HMAC secret key .
- The central management system uses the stored public key of the target system to encrypt the above HMAC secret key .
- Central management system IT Some use their own signature private key to encrypt HMAC Signature . This allows the local system to confirm that the content it receives is authorized .
- Encrypted HMAC The key and corresponding signature are sent to the local system .
- The local system uses the public key of the signature key of the central system backed up at the initial configuration to verify the signature .( If you will , Can pass TPM2_LoadExternal Load public key , And then through TPM2_VerifySignature To verify the signature .)
- The local system uses TPM2_Import The command will be encrypted HMAC Import the key into TPM in , Then get a loadable , contain HMAC Data block of key .
- When users need to use HMAC Key time , The local system uses TPM_Load Command to load this HAMC secret key , Then it can be used normally . here , A local system gets one from the central management system HMAC secret key , And this key has not appeared in clear text in the memory of the local system in the whole process .
Key activation
because TPM Have the ability to create and re create keys from seeds , Therefore, multiple key templates can be used in the initial configuration stage of the system , And by the central IT System backup key template and public part of the key . Then the center IT The system can be restarted TPM Thereby deleting the key on the system . thus , When a system is distributed to end users , There is no key available on system . after , When IT When you want to activate these keys , It only needs to send the key template to the corresponding system , The system can pass TPM2_CreatePrimary Command to recreate the key . It should be noted that the key template contains the key policy , But the password without the key , The password is set every time the key is recreated . If the center IT The system hopes to avoid using password to authorize key access , It can be achieved by configuring two bits in the template :userWithAuth and adminWith Strategy . The setting of these two bits can make the key inaccessible through password . If userWithAuth Set bit False, also adminWith Strategies for True, So the password can't do anything .
If you use the above technology to regenerate the key , The template of the key needs to contain entropy . There is no template , The key cannot be recreated , Therefore, the central management system can ensure that the client will not use this key before receiving the template .
There is another way to activate the key , This is related to TPM1.2 In a similar way : Use a portable key . When a key is copied , You can double encrypt it : Encrypt with the new parent key at once , Use one symmetric key at a time to encrypt after the copy secret order operation is completed . This produces a double encrypted data block . The outer layer of encryption can be decrypted by the private key of the new parent key . Inner layer encryption uses a symmetric key . under these circumstances , When we execute TPM2_Import On command ,TPM The private key of the new parent key must have been loaded ; This private key handle Will pass on to TPM2_Import command , There is also a secret message . This secret information is used to calculate the symmetric key of inner layer encryption , Then it is used to decrypt the encrypted data in memory . The process is as follows :
- The central management system generates a replicable key .
- Use the symmetric key option to copy this key to the client system . The symmetric key option refers to TPM2_Duplicate Functional encryptionKeyIn Parameters .
- The central management system signs the key data block and sends it to the client system , however IT Be responsible for safe storage encryptionKeyIn Parameters .
- When IT When the administrator wants the client system to use the copied key , Provide encryptionKeyIn, So that the client system can pass TPM2_Import The command successfully imported the key .
Key destruction
Once the key is created , Sometimes it's important to destroy it successfully . One example is , If a user is going to sell his surplus or recycle a computer , And he wants to make sure that the encrypted data and keys on the system are no longer available .TPM Provides a variety of easy to implement key destruction methods .
If you want to destroy the master key , The simplest way to destroy it is to modify the seed of the key organization architecture used to create this master key ( It is usually a storage key organization ).TPM2_Clear You can clear the seed of the storage key organization structure . This clears TPM The operation of will destroy all non replicable keys related to the key organization architecture , Clear all keys under the key organization structure , And modify the seed , This prevents all previous master keys related to this organizational structure from being recreated . This command also clears the endorsement key organization , But don't modify its seed (EK And the equipment manufacturer's certificate is still valid ). Replicable keys can no longer be loaded into the system , If they have been copied to another system , Then they may not have been deleted .
If a master key is generated by entropy in the template , And configured as a persistent key , So what you need to do to destroy this key Just destroy the key template and all its copies , Then delete the master key from the persistent storage . Once this operation is completed , The master key disappears , And it cannot be recreated . Because there can be different key trees under different master keys , So this provides a way to destroy a specific key tree without affecting other key trees . At that time, multiple users of the system were using the same TPM when , This ability is particularly important .TPM Can be destroyed in TPM Key generated outside , These keys are imported into TPM And configured as a persistent key . If TPM The copy of the key other than was destroyed ( This key has been successfully imported into TPM after ), Then just delete the key from the persistent memory and destroy it .
边栏推荐
- Easy to understand [linear regression of machine learning]
- 深入浅出图解CNN-卷积神经网络
- 自动化测试:Robot FrameWork框架大家都想知道的实用技巧
- Mysql 索引命中级别分析
- Native JS verification code
- Chapter 3 business function development (user access project)
- Chapter 1 Introduction to CRM core business
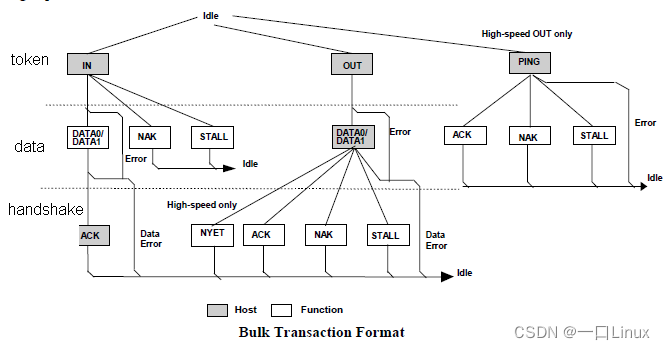
- In depth understanding of USB communication protocol
- Audio Device Strategy 音频设备输出、输入 选择 基于7.0 代码
- [answer] if the app is in the foreground, the activity will not be recycled?
猜你喜欢
随机推荐
目标检测1——YOLO数据标注以及xml转为txt文件脚本实战
USB通信协议深入理解
Functions and usage of imageswitch
Ansible learning summary (9) -- ansible loop, condition judgment, trigger, processing failure and other task control use summary
[re understand the communication model] the application of reactor mode in redis and Kafka
What skills can you master to be a "master tester" when doing software testing?
Cf:c. factors and powers of two [DP + sort + Select Board + select several numbers equal to the minimum number of known sums]
Chapter 3 business function development (user login)
imageswitcher的功能和用法
SD_DATA_RECEIVE_SHIFT_REGISTER
Pytorch中自制数据集进行Dataset重写
请将磁盘插入“U盘(H)“的情况&无法访问 磁盘结构损坏且无法读取
DatePickerDialog和trimepickerDialog
青年时代历练和职业发展
Chapter 3 business function development (to remember account and password)
讨论 | AR 应用落地前,要做好哪些准备?
2021-06-28
【解惑】App处于前台,Activity就不会被回收了?
讨论| 坦白局,工业 AR 应用为什么难落地?
数学分析_笔记_第11章:Fourier级数


![Easy to understand [linear regression of machine learning]](/img/db/f300457165de7ab12aefac8842330f.jpg)