当前位置:网站首页>7.5 simulation summary
7.5 simulation summary
2022-07-05 23:57:00 【Flame*】
I can't hold it Forget to open a place longlong One place forgot to take the mold Break defense Break defense
Time arrangement
1.00-3.00
Look at the question Then I thought about T1 The last two gears won't Everything else is made up
T2 Pushing for a long time still only leads to violence
T3 No idea
3.00-4.30
T1
4.30-5.00
Another push T2 But it will only be violent
5.00-5.50
Thought about it for a while T3 Then write it out and find it false Then I thought This thing and a The value of has nothing to do with The number of occurrences should be a combined number But there is no time to push
Topic analysis
T1
First of all, you can think of n 2 n^2 n2 How to do it : l , r l,r l,r At most n position ( Otherwise, it is impossible to combine the answers ) And the carry will not exceed 16, So subtract the offset and then simulate the violence
Then consider a Smaller approach
You can build a segment tree Then maintain all left endpoints for a right endpoint You can notice that the value on the line segment tree must not increase
Then there will only be 50 Kind of a k a^k ak
After enumeration, it can be divided into two parts on the line segment tree to determine whether it exists and find the corresponding interval length
It feels that the positive solution should be in the sense of modulus balabalabalaba But I don't know how to do this better ( Not sure 2 k 2^k 2k)
T2
Don't understand, don't understand, don't understand If I ask for the last and I will do )
T3
At first, I made up a greedy conclusion I found something wrong after writing it
There is no network flow ( It's impossible to determine the left and right points like the general matching
But you can feel it when you write This thing and a irrelevant It's a combination number. It should
边栏推荐
- Senparc.Weixin.Sample.MP源码剖析
- 【EF Core】EF Core与C# 数据类型映射关系
- 18. (ArcGIS API for JS) ArcGIS API for JS point collection (sketchviewmodel)
- 哪些偏门项目可以做到?自媒体做到月赚一万以上很难吗?
- Qt QPushButton详解
- Huawei equipment configuration ospf-bgp linkage
- GFS distributed file system
- 多普勒效應(多普勒頻移)
- C# 反射与Type
- Rasa 3. X learning series -rasa x Community Edition (Free Edition) changes
猜你喜欢
4点告诉你实时聊天与聊天机器人组合的优势
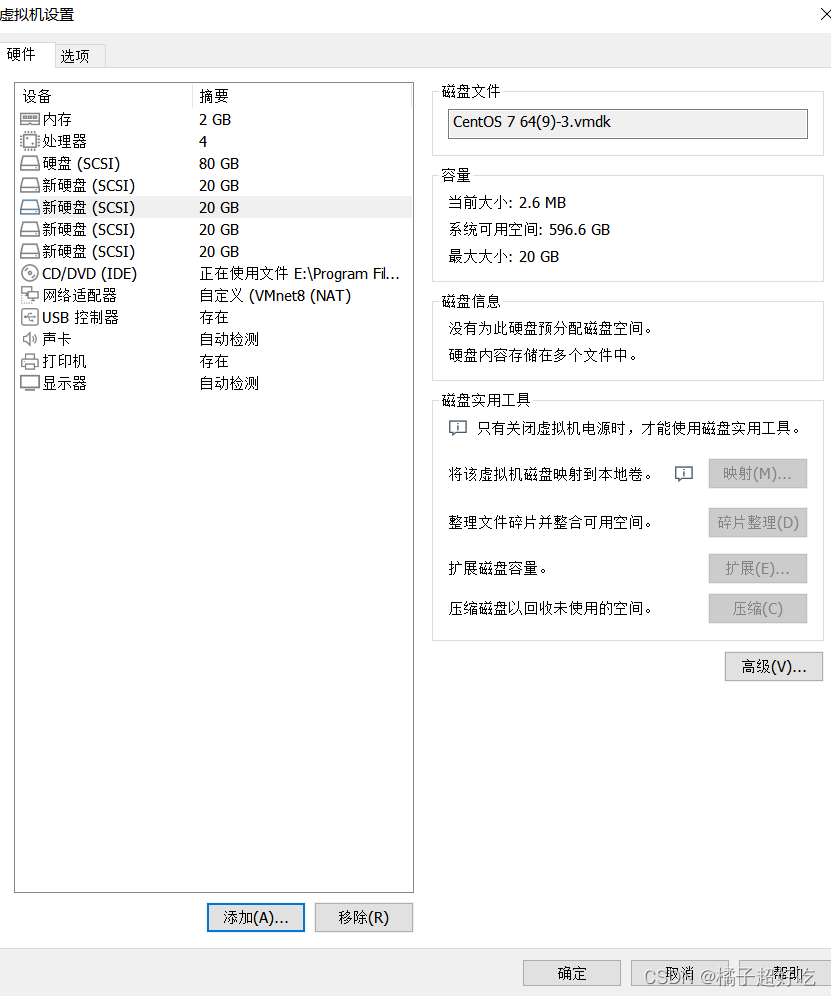
GFS distributed file system
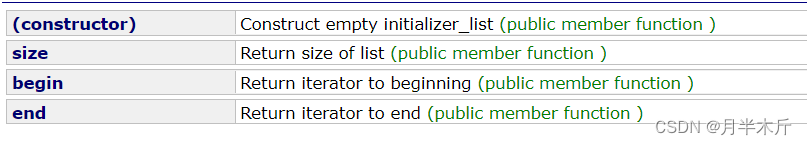
Initialize your vector & initializer with a list_ List introduction
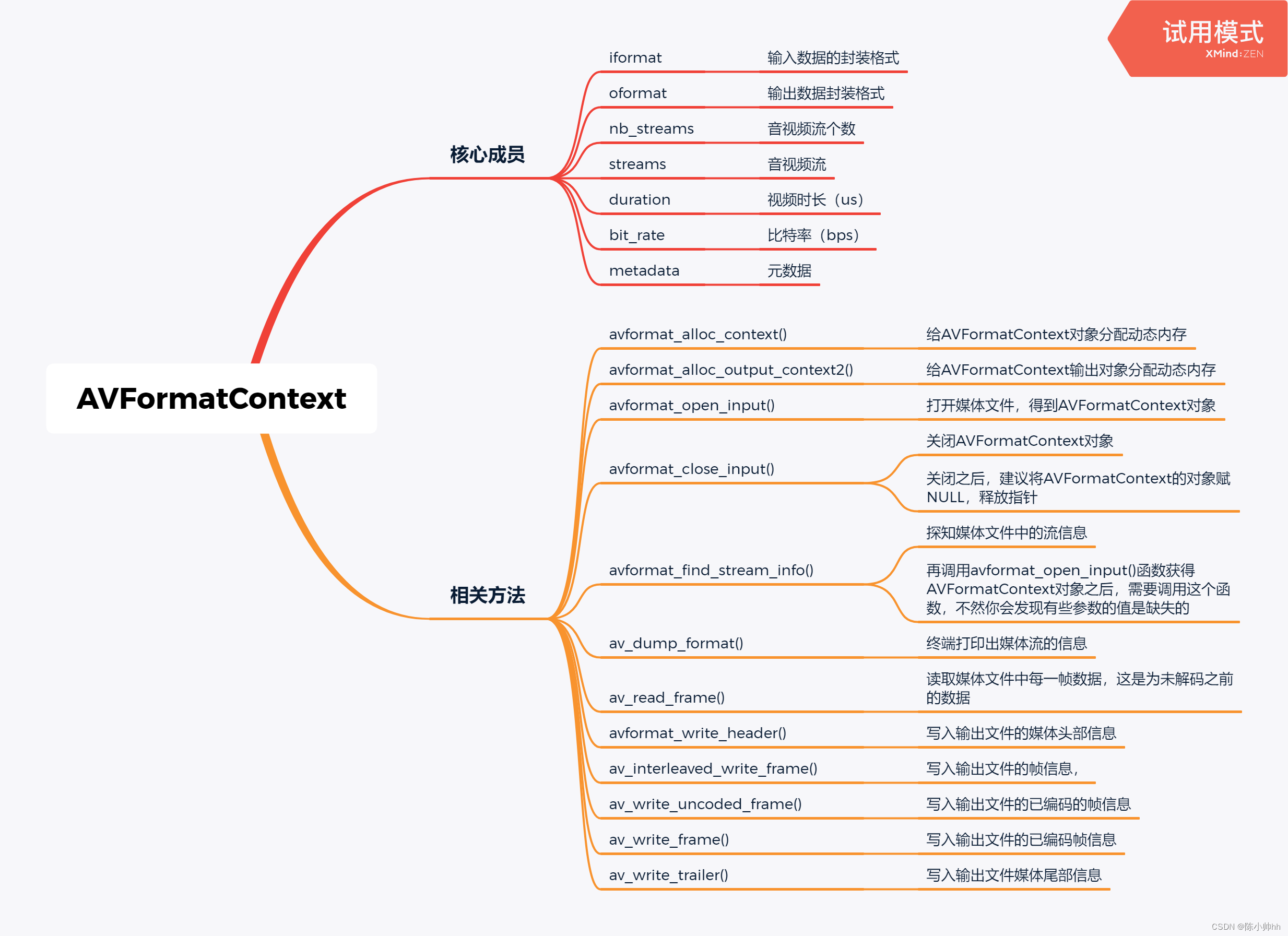
FFMPEG关键结构体——AVFormatContext

What are the functions of Yunna fixed assets management system?
如何获取localStorage中存储的所有值

After summarizing more than 800 kubectl aliases, I'm no longer afraid that I can't remember commands!
Bao Yan notes II software engineering and calculation volume II (Chapter 13-16)
亲测可用fiddler手机抓包配置代理后没有网络

4 points tell you the advantages of the combination of real-time chat and chat robots
随机推荐
Qt 一个简单的word文档编辑器
有什么不起眼却挣钱的副业?
做自媒体影视短视频剪辑号,在哪儿下载素材?
哪些偏门项目可以做到?自媒体做到月赚一万以上很难吗?
Zhongjun group launched electronic contracts to accelerate the digital development of real estate enterprises
Biased sample variance, unbiased sample variance
保研笔记二 软件工程与计算卷二(13-16章)
Doppler effect (Doppler shift)
Yunna | what are the main operating processes of the fixed assets management system
MySQL global lock and table lock
Use CAS instead of synchronized
QT -- thread
wx.getLocation(Object object)申请方法,最新版
上门预约服务类的App功能详解
Bao Yan notebook IV software engineering and calculation volume II (Chapter 8-12)
Zhuan: in the future, such an organization can withstand the risks
[online chat] the original wechat applet can also reply to Facebook homepage messages!
PV静态创建和动态创建
Make a short video clip number of we media film and television. Where can I download the material?
Asynchronous task Whenall timeout - Async task WhenAll with timeout