当前位置:网站首页>Xiaomi written test real question 1
Xiaomi written test real question 1
2022-07-05 06:50:00 【An embedded enthusiast】
Xiaomi written test real question 1
The first question is
The time complexity of the following algorithm is ()
A、O(log2n)
B、O(n)
C、O(nlog2n)
D、O(n^2)
intfact(int n) {
if (n <= 1) return 1;
return n * fact(n-1);
}
answer :B
analysis : This is equivalent to traversing , from N To 1 Value . Then multiply each time by the last value . The time complexity is linear , Simply speaking, it is to use recursion to solve N The factorial , Code execution n Time
The second question is
In modern times Linux Systems and Windows In the system , If you want to run a program in any directory directly by entering the file name , You need to add the path of the program to which environment variable ?( )
A、PWD
B、PATH
C、SHELL
D、EXEC
answer :B
analysis :linux The script file can be run directly by entering the file name in any path , So treat the program as a script .Linux Commands can be divided into internal commands ( Built in commands ) And external orders : The built-in command is called into memory when the system starts , It's memory resident , So the execution efficiency is high . The external command is the software function of the system , Read in the memory from the hard disk when the user needs it . After entering and running an external command ,shell adopt path The environment variable finds the location of the command , That is, go to these directories to find the corresponding application , If you find it , Just create a process , Execute this command in this process , If you don't find it, report it wrong
Recommended reading :Linux The essential foundation
Third question
The consumption records of Xiaomi Youpin are 900,512,613,700,810, If the selection sorting algorithm is used to sort them incrementally , Then the third sorting result is ( )
A、900 512 613 700 810
B、512 900 613 700 810
C、512 613 700 900 810
D、512 613 700 810 900
answer :C
analysis : Incremental selection sort : Select the smallest element from the data elements to be sorted for the first time , Store at the beginning of the sequence , Then find the smallest element from the remaining unordered elements , Then put it at the end of the sorted sequence , Compare this to the last number
The first round : 512 900 613 700 810
The second round : 512 613 900 700 810
The third round : 512 613 700 900 810
Fourth question
About inline Use of functions , Which of the following options are described correctly ()
A、 In a .c Defined in the file inline Function can be in another .c Use... In the document , And if less than 10 That's ok , The compiler will put inline Function expansion , Take advantage of its performance .
B、inline Functions should be concise , If there are many sentences , It is not suitable to define as an inline function
C、inline Function , It is generally not recommended to have a cycle 、if or switch sentence , otherwise , When defining a function, even if there is inline keyword , The compiler may also treat this function as a non inline function .
D、inline A function must be declared before it is called .
answer :B C D
analysis :C++ The concept of inline function
Fifth question
Suppose there is a stack , The order in which elements are put on the stack is A,B,C,D,E. The following impossible stack order is ( )
A、E,D,C,B,A
B、A,B,C,D,E
C、B,C,D,E,A
D、E,A,B,C,D
answer :D
analysis :↓ For stack entry ,↑ Stand for out of the stack .
A Options :A↓,B↓,C↓,D↓,E↓,E↑, D↑, C↑, B↑, A↑
B Options :A↓, A↑,B↓, B↑,C↓, C↑,D↓, D↑,E↓, E↑
C Options :A↓, B↓, B↑, C↓, C↑,D↓, D↑,E↓, E↑, A↑
D Options : It can't be done
Sixth question
The following is about deadlock , The correct description is ? ( )
A、 Orderly allocation of lock resources can prevent deadlocks
B、 Banker algorithm is used to detect deadlock
C、 Depriving the deadlock process of all its resources can release the deadlock
D、 Other descriptions are all wrong
answer :A C
analysis : Banker algorithm is used to prevent deadlock
Question seven
About the primary key , The right description is ()
A、 A table can have multiple primary keys
B、 The primary key cannot be empty
C、 A unique index will be created when the primary key is created
D、 A primary key can contain multiple attributes , Such as joint primary key
answer :B C D
analysis : A table can only have one primary key , Cannot have multiple primary keys . Primary key cannot be empty , To ensure that the data in the table is unique . A federated primary key is also a primary key .
The eighth question
In the process of sampling the signal , When the sampling frequency is at least greater than () when , It is possible to completely retain the information in the original signal .
A、 The highest frequency
B、 The highest frequency of 2 times
C、 The highest frequency of 4 times
D、 Can never be completely preserved
answer :B
analysis : In the process of simulation / In the process of digital signal conversion , When the sampling frequency fs.max Greater than the highest frequency in the signal Fmax( Low pass , There are other conversion methods for bandpass or highpass ) Of 2 Times , namely :fs.max>=2Fmax, Then the sampled digital signal completely retains the information in the original signal , It can recover the original analog signal without distortion . In general practical applications, the sampling frequency is guaranteed to be the highest frequency of the signal 5~10 times ; Sampling theorem is also called Nyquist sampling theorem .
Question 9
The following description of processes and threads is wrong ()
A、 address space : The process has at least one thread , Threads share the address space of the process , The process has its own address space
B、 Processes are units of resource allocation and ownership , Threads in the same process share the resources of the process
C、 Both can be executed concurrently
D、 Process is the basic unit of processor scheduling , But threads are not
answer :D
analysis :
Difference between process and thread
address space : Threads share the address space of this process , There are independent address spaces between processes .
resources : Threads share resources of this process, such as memory 、I/O、cpu etc. , Not conducive to the management and protection of resources , The resources between processes are independent , Good resource management and protection .
Robustness, : Multiprocessing is more robust than multithreading , After a process crashes , No impact on other processes in protected mode , But when a thread crashes, the whole process dies .
Execution process : Each independent process has an entry for the program to run 、 Sequential execution sequence and program entry , High execution overhead . But the thread cannot execute independently , Must exist in the application , Multiple thread execution control provided by the application , Low execution overhead .
Concurrency : Both can be executed concurrently .
Resource consumption during switching : Process switching , It consumes a lot of resources . When it comes to frequent switching , It's better to use threads than processes . Also, if concurrent operations of some variables are required to be performed at the same time and shared at the same time , Only threads, not processes .
Basic unit : Threads are the basic unit of processor scheduling , Process is the basic unit of resource allocation and scheduling .
Question 10
Which of the following methods can prevent the compiler from optimizing the alignment of structures ?()
A、
struct
{
unsigned char head;
unsigned char sector;
unsigned char cylinder;
};
B、
struct
{
unsigned char head;
unsigned char sector;
unsigned char cylinder;
}__attribute__((pack));
C、
struct
{
unsigned char head;
unsigned char sector;
unsigned char cylinder;
}__attribute__((packed));
D、
struct
{
unsigned char head;
unsigned char sector;
unsigned char cylinder;
}__attribute__((aligned(0)));
answer :C D
analysis : add __attribute__((packed)), It can prevent the compiler from optimizing the byte alignment of the structure . Use __attribute__((aligned(0)))(0 Is the number of aligned bytes ), Force the compiler to follow 0 Byte alignment .
Recommended reading : Alignment rules and examples of structures
Eleventh questions
The following statements about constructors and destructors are correct ( )
A、delete The destructor will only be called once , and delete[] Will call the destructor of each member
B、 The calling order of the destructor : Destruct the derived class first and then the base class
C、 Call order of constructor : Construct the base class first and then the derived class
D、 The calling order of the destructor : Destruct the base class first and then the derived class
answer :A B C
analysis : Constructors : First there is the base class construction , Then there are derived class constructions . Derived classes can overload the base class constructor . Destructor : Start from the derived class to destruct , Re destruct the base class . Because the derived class constructor is overloaded , So we have to destruct first . The process of the two is opposite .
Twelfth questions
C In language ,static The key words are correct :()
A、 use static Modified global variables can be modified at run time
B、 use static Modified function , Its internal variables can be passed to other functions
C、 stay a.c In file , There is one static Modified function , Under no circumstances is it possible to b.c In the called
D、 The rest is wrong
answer :A B
analysis : The investigation is right static Keyword understanding , Use const Keywords can be set as variables and cannot be modified . Same as in the document , Functions can be passed to other functions by returning variable values , added static Keywords do not affect
Recommended reading :static、register、volatile、const、extern keyword
Thirteenth questions
ARM In the register $r13 representative (1) The pointer , Point to (2);$15 representative (3) The pointer , Point to (4).
right key :
1 SP
2 To the top of the stack
3 PC
4 The address of the next instruction the program will execute
analysis :
PC:program counter Is a general purpose register , Can be used to point to the next instruction of the currently running instruction
SP:stack pointer Stack pointer , It is also accessed by general-purpose registers , It is used for related operations of posting and stack
ARM Microprocessors share 37 individual 32 Bit register , General purpose registers include R0~R15, Can be divided into 3 class :
(1) Ungrouped registers R0~R7
(2) Grouping register R8~R14
(3) Program counter PC(R15)
R13 stay ARM Instructions are often used as stack pointers SP
R14 Called subroutine link register LR(Link Register), When executing a subroutine call instruction (BL) when ,R14 available R15( Program counter PC) Backup of
summary
The Xiaomi real topic knowledge points on niuke.com are quite miscellaneous , I haven't found a place to classify yet
边栏推荐
猜你喜欢
2. Addition and management of Oracle data files
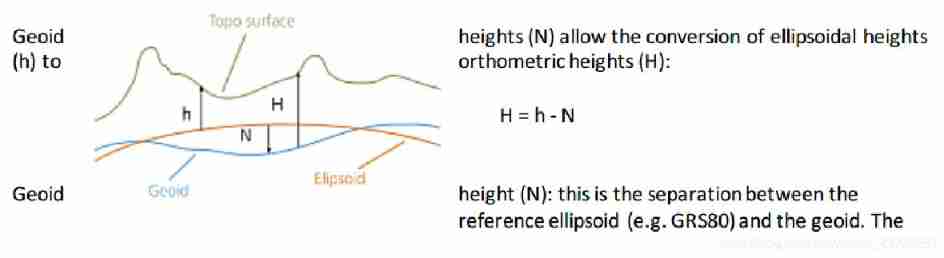
Positive height system

Knapsack problem acwing 9 Group knapsack problem
What is linting
Orin 安装CUDA环境

Volcano 资源预留特性

Find the combination number acwing 888 Find the combination number IV
. Net core stepping on the pit practice
Package webapp or H5 pages into apps

Volcano resource reservation feature
随机推荐
如何正确在CSDN问答进行提问
Use the Paping tool to detect TCP port connectivity
La redirection de l'applet Wechat ne déclenche pas onload
Preemption of CFS scheduling
【高德地图POI踩坑】AMap.PlaceSearch无法使用
Paper reading report
Getting started with typescript
Relevant information of National Natural Science Foundation of China
H5内嵌App适配暗黑模式
Chinese remainder theorem acwing 204 Strange way of expressing integers
Adg5412fbruz-rl7 applies dual power analog switch and multiplexer IC
MQClientException: No route info of this topic: type_ topic
LSA Type Explanation - lsa-5 (type 5 LSA - autonomous system external LSA) and lsa-4 (type 4 LSA - ASBR summary LSA) explanation
MPLS experiment
How to correctly ask questions in CSDN Q & A
Rehabilitation type force deduction brush question notes D2
Error: “MountVolume.SetUp failed for volume pvc 故障处理
Find the combination number acwing 888 Find the combination number IV
【MySQL8.0不支持表名大写-对应方案】
Dameng database all