当前位置:网站首页>APR protocol and defense
APR protocol and defense
2022-07-05 14:21:00 【Cwxh0125】
Catalog
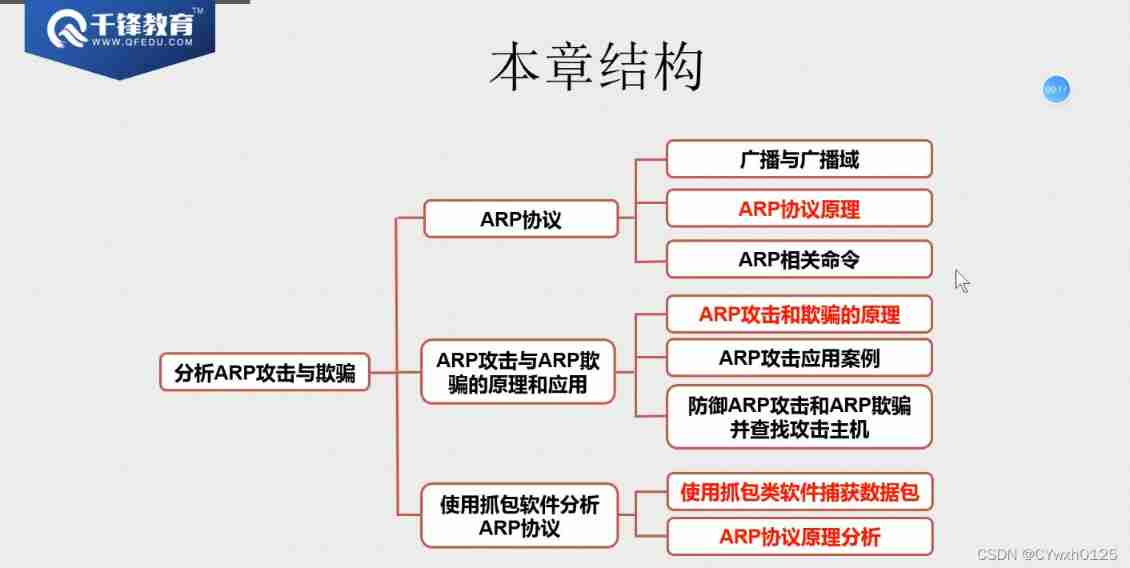
Broadcast and broadcast domain overview
ARP agreement ( The network layer )
ARP
Broadcast and broadcast domain overview

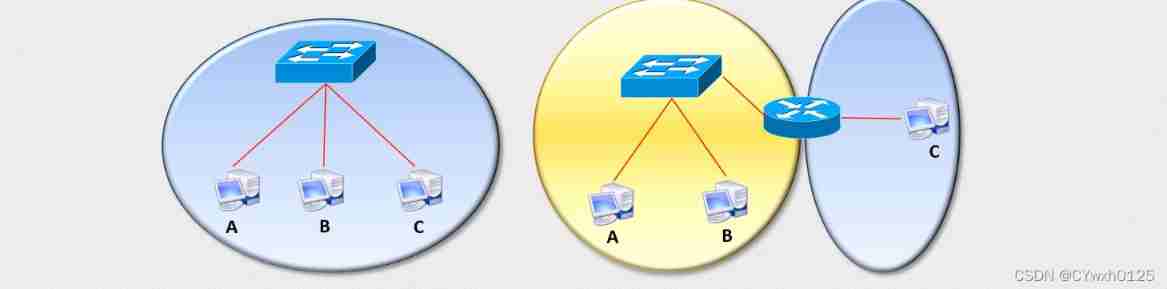
The larger the broadcast domain, the lower the communication efficiency
The switch cannot control the broadcast, but the router can control
ARP agreement ( The network layer )
ARP Reasons for appearance
ARP Agreement is “Address Resolution Protocol”( Address resolution protocol ) Abbreviation . Its function is in Ethernet environment , The transmission of data depends on MAC Address, not IP Address , And will know IP Address conversion to MAC The work of the address is by ARP Agreement to complete .
In the LAN , The actual transmission in the network is “ frame ”, There is a target host in the frame MAC Address of the . In Ethernet , One host communicates directly with another host , You have to know the... Of the target host MAC Address . But this goal MAC How did you get the address ? It is obtained through the address resolution protocol . So-called “ Address resolution ” That is, the host sends the target before sending the frame IP Address to target MAC Address process .ARP The basic function of the protocol is through the target device IP Address , Query the... Of the target device MAC Address , To ensure smooth communication .
arp Cache table 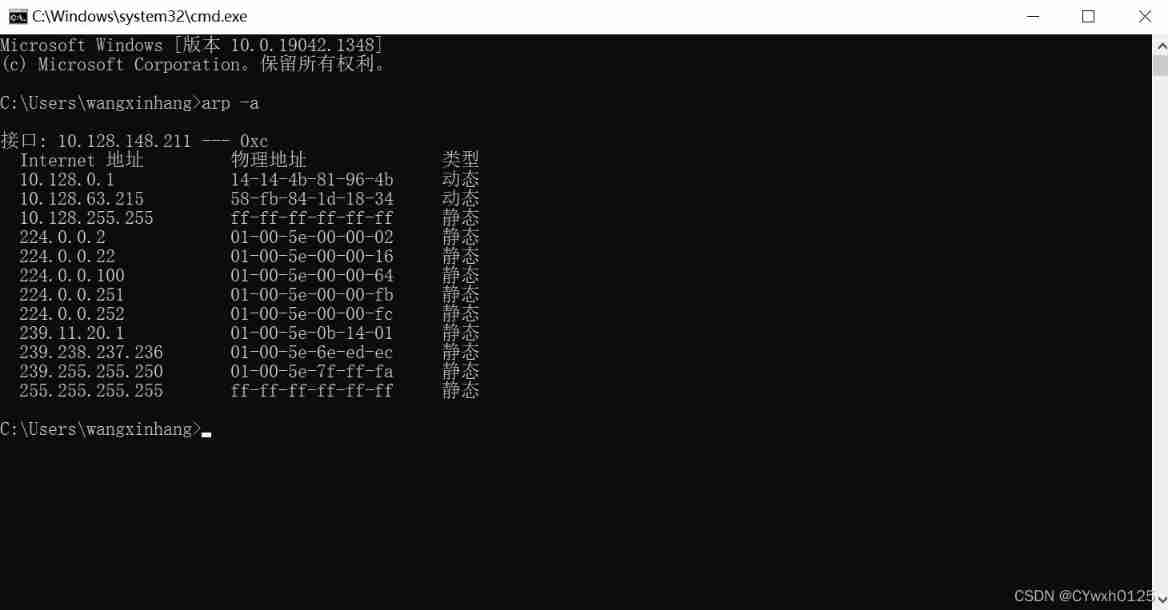
principle :
At any time , A host has IP The data message is sent to another host , It needs to know the logic of the receiver (IP) Address . however IP The address must be encapsulated into frames to pass through the physical network . This means that the sender must have the physical address of the receiver (MAC) Address , Therefore, it is necessary to complete the mapping from logical address to physical address . and ARP The protocol can receive data from IP The logical address of the protocol , Map it to the corresponding physical address , Then submit the physical address to the data link layer .
ARP request
anytime , When the host needs to find the physical address of another host in the network , It can send a ARP Request message , This message wraps the sender's MAC Address and IP Address and recipient's address IP Address . Because the sender doesn't know the physical address of the receiver , Therefore, this query packet will be broadcast in the network layer .
ARP Respond to
Every host in the LAN will accept and process this ARP Request message , Then verify , View the recipient's IP Is the address your own address , Only the host that has successfully verified will return a ARP response message , This response message contains the... Of the receiver IP Address and physical address . This message uses the received ARP The physical address of the requester in the request message is directly sent to ARP The requester of the request message .
demonstration
ARP Relevant command (windows)
arp -a see ARP Cache table
arp -d clear ARP cache
arp -s ARP binding
ARP attack
ARP The limitations of the attack :ARP Attacks can only be carried out on the local area network , Can't attack the Internet .
The reply radio broadcast Can attack
principle :arp The protocol has no verification mechanism
The way :
By sending fake ARP message ( Broadcast or unicast ), To attack or cheat
Such as false message MAC It's fake, it doesn't exist , Realization ARP attack , The result is terminal communication / Broken net
Such as false message MAC It's the attacker's own MAC Address , Realization ARP cheating , As a result, you can monitor 、 steal 、 Tampering 、 Control flow , But without interrupting communication 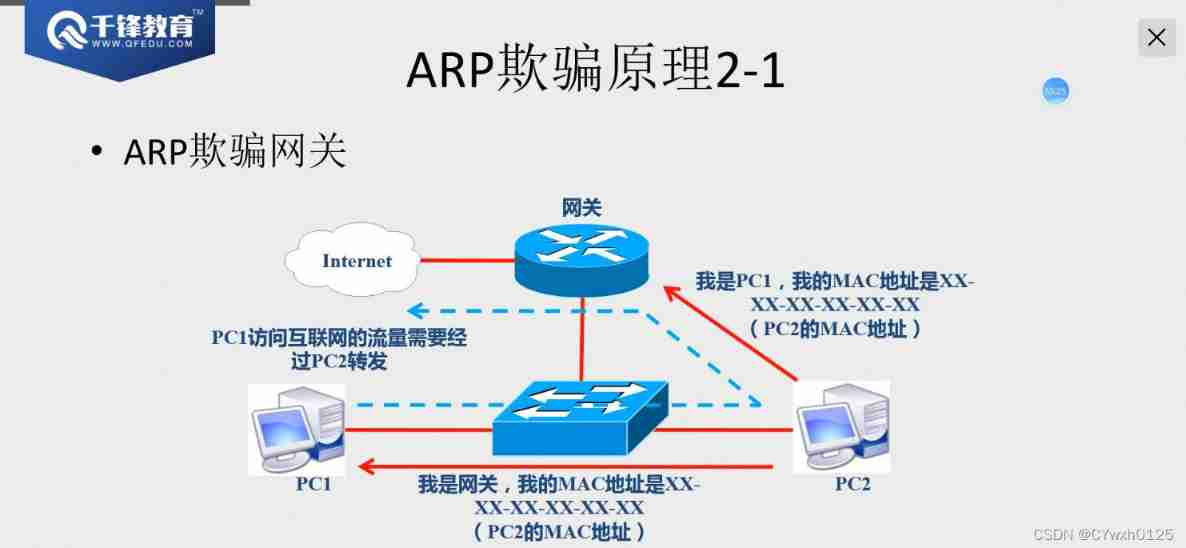
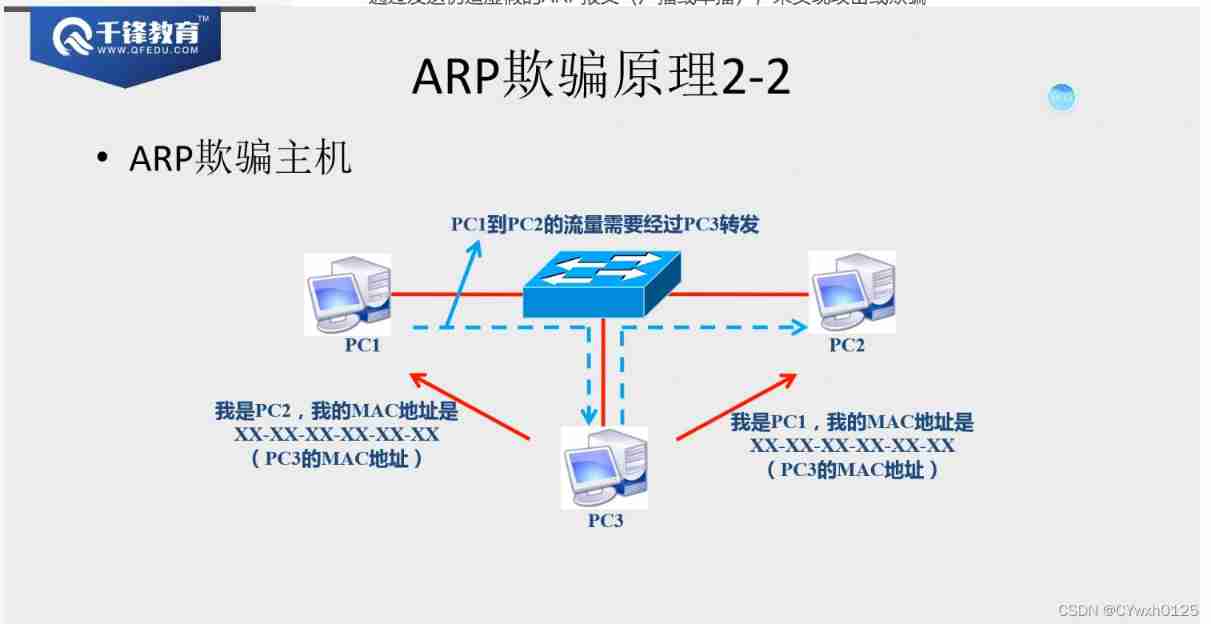
Complete process demonstration
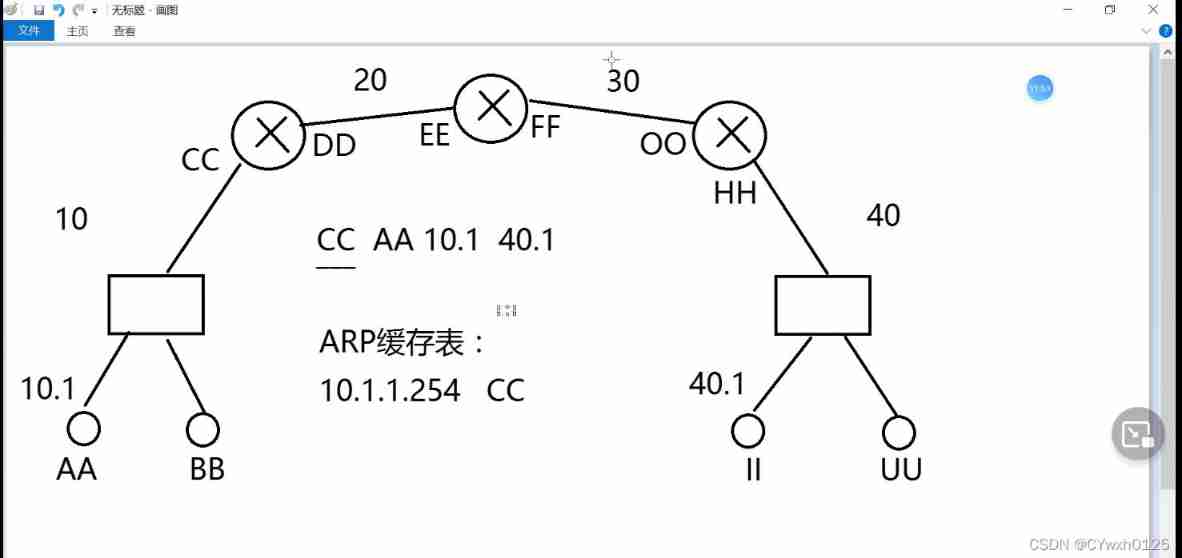
The flow chart above
hypothesis MAC The address is AA Of PC Direction direction II Send a message ( Suppose you don't know II Of MAC Address )
The data frame is — AA 10.1 40.1 Judge the target first IP Whether they are in the same network segment be not in So send the information to the gateway At this time, a ARP message —— AA 10.1 10.254 After receiving the reply from the gateway AA Of arp The cache table will generate a 10.1.1.254 CC At this time, the transmitted frame becomes CC AA 10.1 40.1 After the switch accepts Check the original first MAC Address Whether you cache ( Suppose you have learned ) Then send the frame to the router The router judges the target first MAC Whether it's me After finding that the two are consistent delete AA CC Expose three, four, five layers of data Then reseal the router ( initial MAC The address is the router itself , Get the next hop through broadcast response MAC Address as the target MAC Address ) Then forward according to the routing table
Standard process
1) A frame arrival route , The router first checks the target MAC Whether the address is itself , If not, discard , If it is
Then unpack , And will IP The packet is sent to the inside of the router
2) Router check IP The goal in Baotou IP, And match the routing table
If the match fails , Then discard , And to the source IP Feedback error information, such as successful matching , Will IP Packets are routed to the outgoing interface .
3) Encapsulation frame , First, the of the interface MAC Address as source MAC Package it , Then check that the ARP Cache table , Check if there is a next jump MAC Address , if there be , Extract and target MAC The address is encapsulated in the frame , If not , Then send ARP Broadcast request for next hop MAC,G And get each other's mac Address , Then record the cache , And encapsulate the frame , Finally, send the frame .
ARP defense
1、 static state ARP binding
Manual binding / Two way binding
Windows On the client :
arp -s 10.1.1.254 00-20-2c-a0-e1-o9
2、ARP A firewall
Automatically bind static data ARP
Active defense
3、 Hardware level ARP defense
Switch support ” port “ Do something dynamic ARP binding ( coordination DHCP The server )
Or do static ARP binding
边栏推荐
- R语言ggplot2可视化密度图:按照分组可视化密度图、自定义配置geom_density函数中的alpha参数设置图像透明度(防止多条密度曲线互相遮挡)
- How to deeply understand the design idea of "finite state machine"?
- The function of qualifier in C language
- 03_Solr之dataimport
- Opengauss database source code analysis series articles -- detailed explanation of dense equivalent query technology (Part 2)
- Solution of commercial supply chain collaboration platform in household appliance industry: lean supply chain system management, boosting enterprise intelligent manufacturing upgrading
- Thymeleaf th:classappend属性追加 th:styleappend样式追加 th:data-自定义属性
- Countermeasures of enterprise supply chain management system in UCA Era
- How to call the function mode of one hand and one machine
- R语言使用nnet包的multinom函数构建无序多分类logistic回归模型、使用coef函数获取模型中每个变量(自变量改变一个单位)对应的对数优势比(log odds ratio)
猜你喜欢
Thymeleaf 模板的创建与使用
![[learning notes] stage test 1](/img/22/ad16375d8d1510c2ec75c56403a8bf.png)
[learning notes] stage test 1
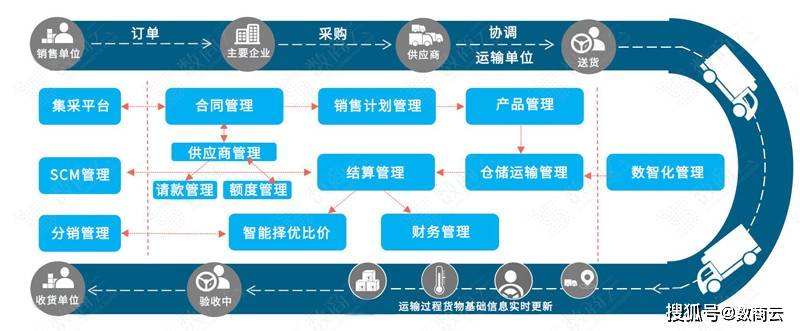
Countermeasures of enterprise supply chain management system in UCA Era
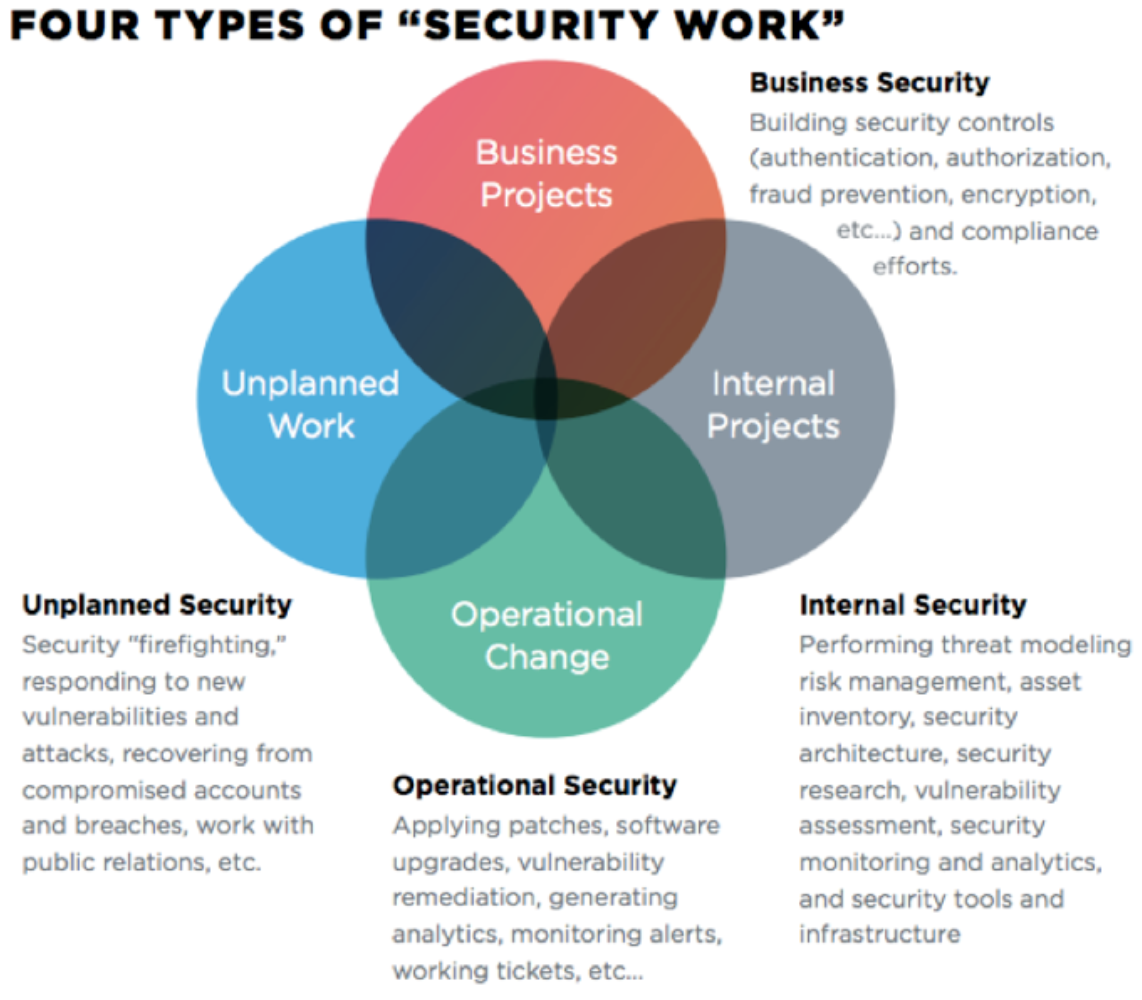
How to introduce devsecops into enterprises?
TiFlash 面向编译器的自动向量化加速

乌卡时代下,企业供应链管理体系的应对策略

直播预告|如何借助自动化工具落地DevOps(文末福利)

Mingfeng medical sprint technology innovation board: annual revenue of 350million yuan, proposed to raise 624million yuan

魅族新任董事長沈子瑜:創始人黃章先生將作為魅族科技產品戰略顧問
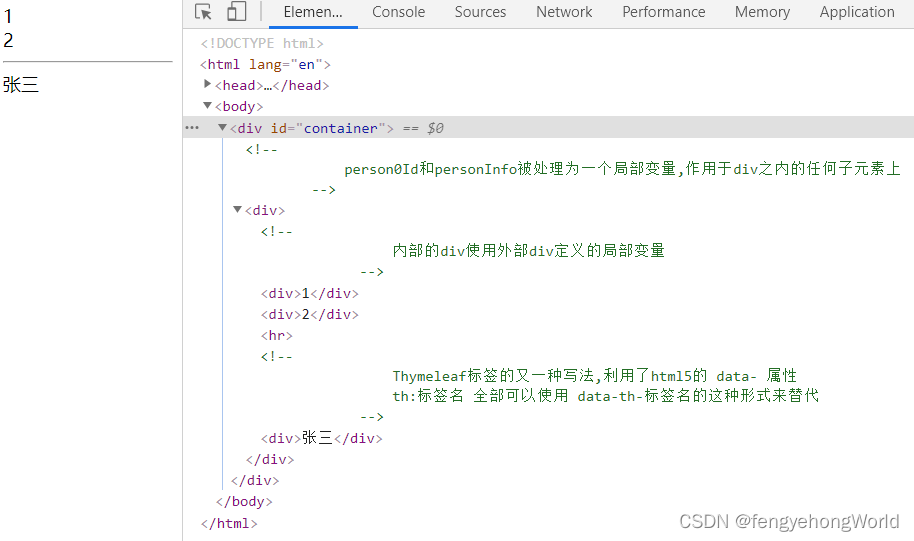
Thymeleaf th:with use of local variables
随机推荐
Introduction, installation, introduction and detailed introduction to postman!
Share 20 strange JS expressions and see how many correct answers you can get
How does redis implement multiple zones?
别不服气。手机功能升级就是强
无密码身份验证如何保障用户隐私安全?
LeetCode_ 69 (square root of x)
C - Divisors of the Divisors of An Integer Gym - 102040C
CyCa children's physical etiquette Ningbo training results assessment came to a successful conclusion
POI set the data format of the column (valid)
Thymeleaf th:with局部变量的使用
3W principle [easy to understand]
R語言ggplot2可視化:可視化折線圖、使用theme函數中的legend.position參數自定義圖例的比特置
How to make a second clip of our media video without infringement
Mingfeng medical sprint technology innovation board: annual revenue of 350million yuan, proposed to raise 624million yuan
快消品行业SaaS多租户解决方案,构建全产业链数字化营销竞争力
Thymeleaf 常用函数
展现强大。这样手机就不会难前进
The IPO of Ruineng industry was terminated: the annual revenue was 447million and it was planned to raise 376million
R语言使用MASS包的polr函数构建有序多分类logistic回归模型、使用coef函数获取模型中每个变量(自变量改变一个单位)对应的对数优势比(log odds ratio)
Mysql database installation tutorial under Linux