当前位置:网站首页>Radar equipment (greedy)
Radar equipment (greedy)
2022-07-06 16:08:00 【AC__ dream】
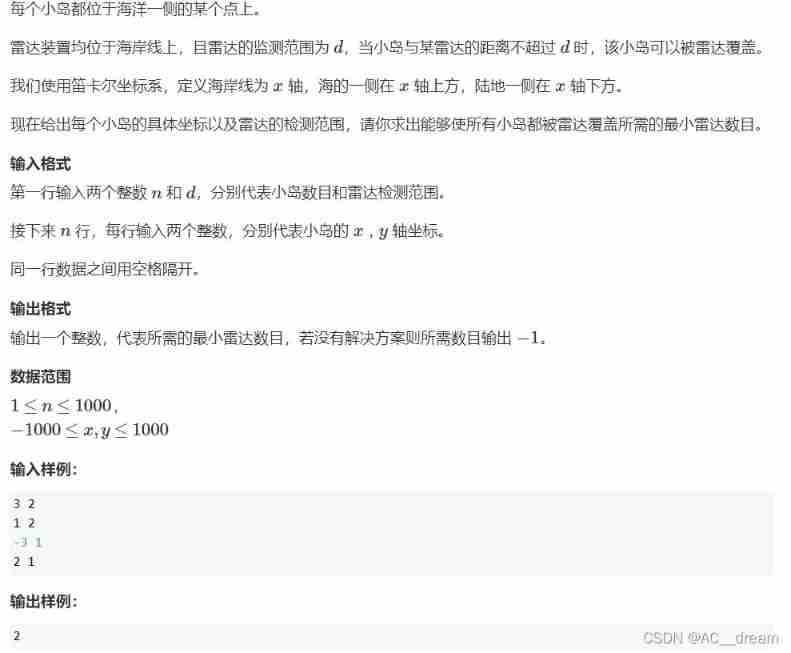
analysis : First, give the location of an island , We can find out the position range where this radar can be placed , It means that as long as the radar is placed in this section , Then the island can be covered by radar , Altogether n An island , Then the corresponding can also be found n Intervals , At this time, there should be at least one radar in each section , But there may be coincidence between intervals Of , In other words, we require a minimum number of radars so that there is at least one radar in each interval , Then this is obviously a greedy problem , Let's sort all the intervals according to the right endpoint , Then we record a r Represents the location of the last radar , If the current range is r To the right of , Then we should at least install another radar , Because there is no longer an island on the left side of the current range that is not covered , So our radar is placed on the right as far as possible , But also within the current range , So it is placed on the right end of the current interval , Place in sequence , Add the number of radars every time you place one 1, Finally, output the number of radars .
Here is the code :
#include<cstdio>
#include<iostream>
#include<cstring>
#include<vector>
#include<algorithm>
#include<map>
#include<cmath>
#include<queue>
using namespace std;
const int N=1003;
int n,d;
struct node{
double l,r;
}p[N];
bool cmp(node a,node b)
{
return a.r<b.r;
}
void f(int i,int x,int y)
{
p[i]={x-sqrt(1.0*d*d-y*y),x+sqrt(1.0*d*d-y*y)};
}
int main()
{
cin>>n>>d;
int x,y;
for(int i=1;i<=n;i++)
{
scanf("%d%d",&x,&y);
if(y>d)
{
puts("-1");
return 0;
}
f(i,x,y);
}
sort(p+1,p+n+1,cmp);
double r=-9999;
int cnt=0;
for(int i=1;i<=n;i++)
{
if(p[i].l>r)
{
r=p[i].r;
cnt++;
}
}
printf("%d",cnt);
return 0;
}边栏推荐
- SSM框架常用配置文件
- socket通讯
- 【练习-4】(Uva 11988)Broken Keyboard(破损的键盘) ==(链表)
- 1903. Maximum odd number in string
- 【练习-6】(PTA)分而治之
- [exercise-3] (UVA 442) matrix chain multiplication
- [exercise -11] 4 values why sum is 0 (and 4 values of 0)
- Luogu P1102 A-B number pair (dichotomy, map, double pointer)
- 628. Maximum product of three numbers
- 409. Longest palindrome
猜你喜欢
渗透测试 ( 4 ) --- Meterpreter 命令详解

渗透测试 ( 2 ) --- 渗透测试系统、靶机、GoogleHacking、kali工具
![[exercise-7] crossover answers](/img/66/3dcba2e70a4cd899fbd78ce4d5bea2.png)
[exercise-7] crossover answers

Programmers, what are your skills in code writing?

2027. Minimum number of operations to convert strings
b站 實時彈幕和曆史彈幕 Protobuf 格式解析
Penetration testing (5) -- a collection of practical skills of scanning King nmap and penetration testing tools
Vs2019 initial use
【练习-5】(Uva 839)Not so Mobile(天平)
信息安全-安全编排自动化与响应 (SOAR) 技术解析
随机推荐
Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
Find 3-friendly Integers
【练习-2】(Uva 712) S-Trees (S树)
Research Report on surgical fluid treatment industry - market status analysis and development prospect prediction
Research Report of cylindrical grinder industry - market status analysis and development prospect forecast
Nodejs+vue网上鲜花店销售信息系统express+mysql
C language must memorize code Encyclopedia
nodejs爬虫
Penetration test (1) -- necessary tools, navigation
Penetration test (4) -- detailed explanation of meterpreter command
Ball Dropping
Truck History
Shell Scripting
628. Maximum product of three numbers
MySQL授予用户指定内容的操作权限
[exercise-6] (UVA 725) division = = violence
7-1 understand everything (20 points)
渗透测试 ( 7 ) --- 漏洞扫描工具 Nessus
Auto. Getting started with JS
Shell脚本编程