当前位置:网站首页>B - Code Party (girls' competition)
B - Code Party (girls' competition)
2022-07-06 16:03:00 【It's Xiao Zhang, ZSY】
B - Code Party 
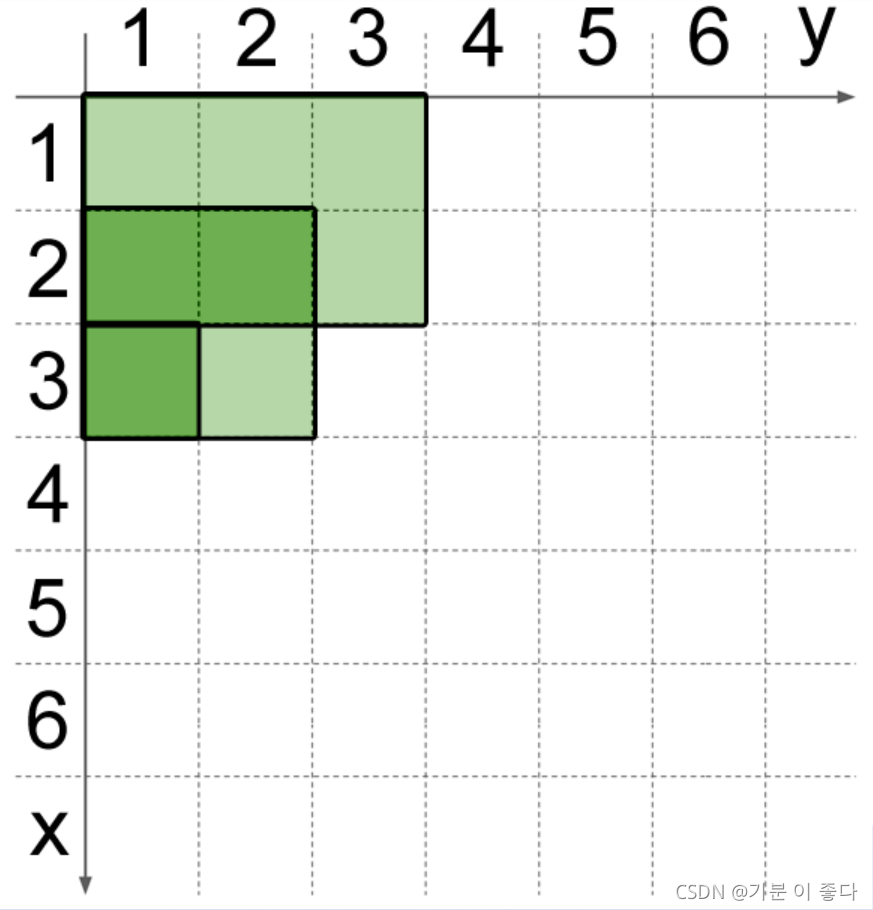
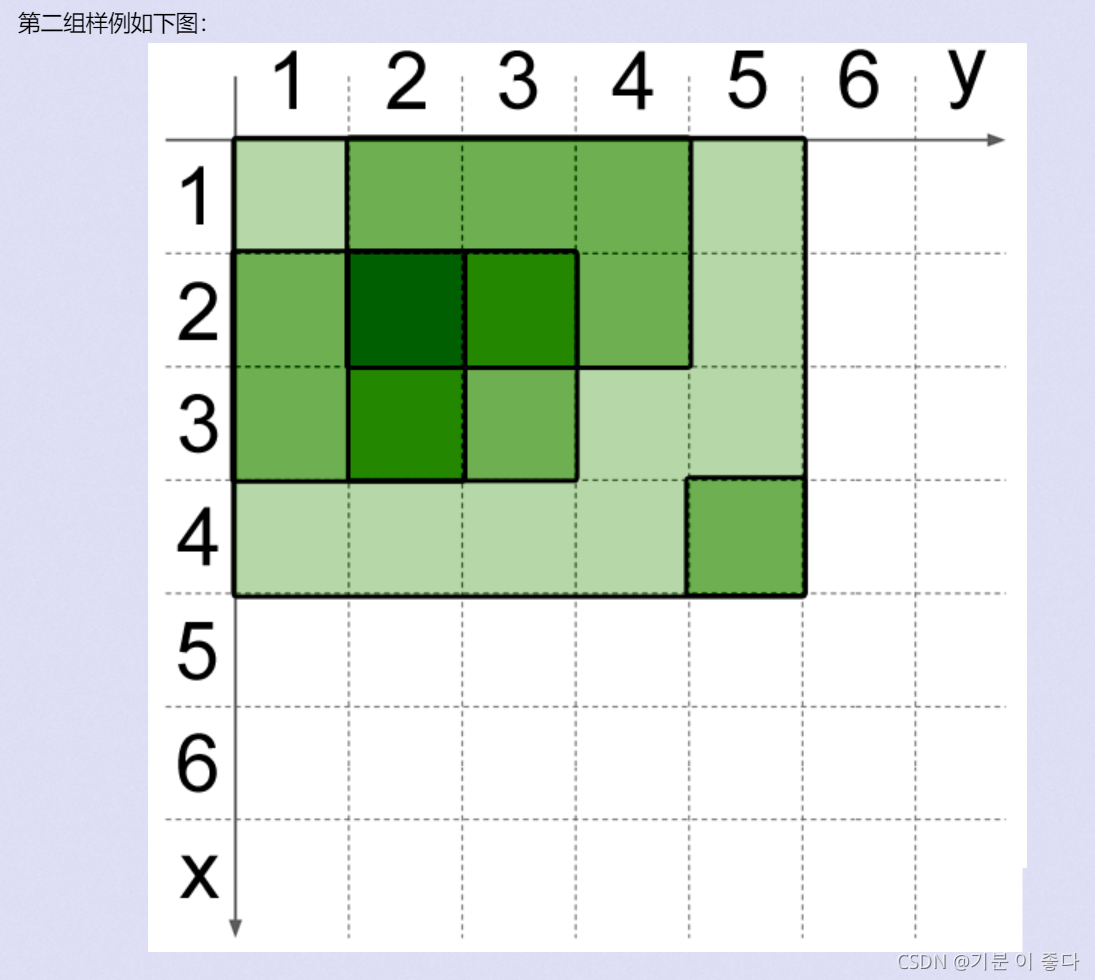
Sample Input
2
3
3 1 3 1
1 1 2 3
2 1 3 2
5
1 1 4 5
2 1 3 2
2 2 3 3
4 5 4 5
1 2 2 4
Sample Output
0
4
// Now it's time ,2021 year 10 month 28 Number 00:38 I finally ac 了 ,,,, Woo woo
/* Their thinking Using the difference and two-dimensional prefix sum, the number of intervals covered on each lattice is calculated g[i][j]. If you ask at this time C(g[i][j],3) And , Then there will be a lot of repetition , Because the same three intervals can cover multiple grids . So we only keep the grid in the upper left corner of the coverage area , Because this grid must be on the top and left of the interval , So the final answer is : The sum of the - Delete the sum after the left - Delete the sum after the top + Delete the sum after the top and left ( This piece has been repeatedly reduced in the front , So add it back ). */
#include<iostream>
#include<cstdio>
#include <cstring>
#include <algorithm>
#include <cstring>
#define N 1005
using namespace std;
typedef long long ll;
int a1[N][N],a2[N][N],a3[N][N],a4[N][N];
ll c3[100005];
ll wo(int a[N][N])
{
for(int i=1;i<=1000;i++){
for(int j=1;j<=1000;j++){
a[i][j]=a[i][j]+a[i-1][j]+a[i][j-1]-a[i-1][j-1];// Sum up ;
}
}
ll ans=0;
for(int i=1;i<=1000;i++){
for(int j=1;j<=1000;j++){
ans+=c3[a[i][j]]; // altogether ( Buckle ) Overlapping ans;
}
}
return ans;
}
int main(){
int T;
c3[3]=1;
cin>>T;
for(int i=4;i<=100000;i++){
c3[i]=(ll)i*(i-1)*(i-2)/6;// If there is i The situation of the same Geke team
}
while(T--)
{
int n;
cin>>n;
memset(a1,0,sizeof(a1));// Each cycle assignment 0;
memset(a2,0,sizeof(a2));
memset(a3,0,sizeof(a3));
memset(a4,0,sizeof(a4));
int x1,y1,x2,y2;
for(int i=1;i<=n;i++){
scanf("%d%d%d%d", &x1, &y1, &x2, &y2);// It works cin It's over time , There will be no competition in the future cin;
a1[x1][y1]++,a1[x2+1][y1]--,a1[x1][y2+1]--,a1[x2+1][y2+1]++;
// Two dimensional difference , Give (x1,y1) To (x2,y2) Add 1;
a2[x1+1][y1]++,a2[x2+1][y1]--,a2[x1+1][y2+1]--,a2[x2+1][y2+1]++;
// Subtract the left from each matrix ( Except for the first line ),x1+1;
a3[x1][y1+1]++,a3[x2+1][y1+1]--,a3[x1][y2+1]--,a3[x2+1][y2+1]++;
// Subtract the upper edge from each matrix ( Except for the first column ),y1+1;
a4[x1+1][y1+1]++,a4[x2+1][y1+1]--,a4[x1+1][y2+1]--,a4[x2+1][y2+1]++;
// Plus plus minus ;
}
cout<<wo(a1)-wo(a2)-wo(a3)+wo(a4)<<endl;
}
return 0;
}
边栏推荐
- Gartner:关于零信任网络访问最佳实践的五个建议
- 程序员的你,有哪些炫技的代码写法?
- Information security - Epic vulnerability log4j vulnerability mechanism and preventive measures
- 用C语言写网页游戏
- 信息安全-威胁检测引擎-常见规则引擎底座性能比较
- Auto.js入门
- 0-1背包问题(一)
- Cost accounting [18]
- 通俗地理解什么是编程语言
- China chart recorder market trend report, technology dynamic innovation and market forecast
猜你喜欢
基于web的照片数码冲印网站

Optimization method of path problem before dynamic planning
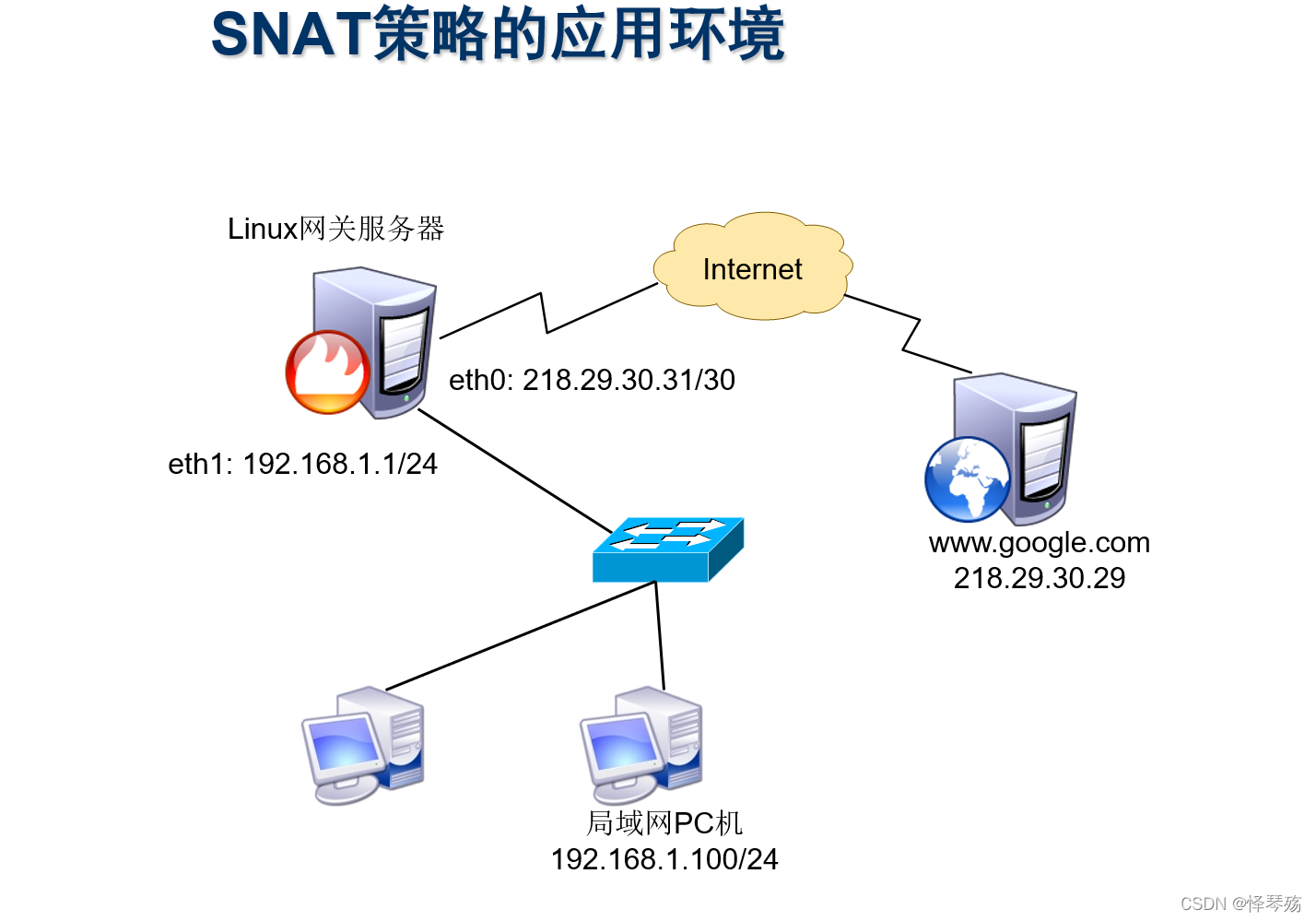
Information security - threat detection - detailed design of NAT log access threat detection platform
![[exercise-7] crossover answers](/img/66/3dcba2e70a4cd899fbd78ce4d5bea2.png)
[exercise-7] crossover answers
Pyside6 signal, slot
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
![[exercise-5] (UVA 839) not so mobile (balance)](/img/8e/48dcf75f7347b36301df6fc129c09d.png)
[exercise-5] (UVA 839) not so mobile (balance)

B - 代码派对(女生赛)
用C语言写网页游戏
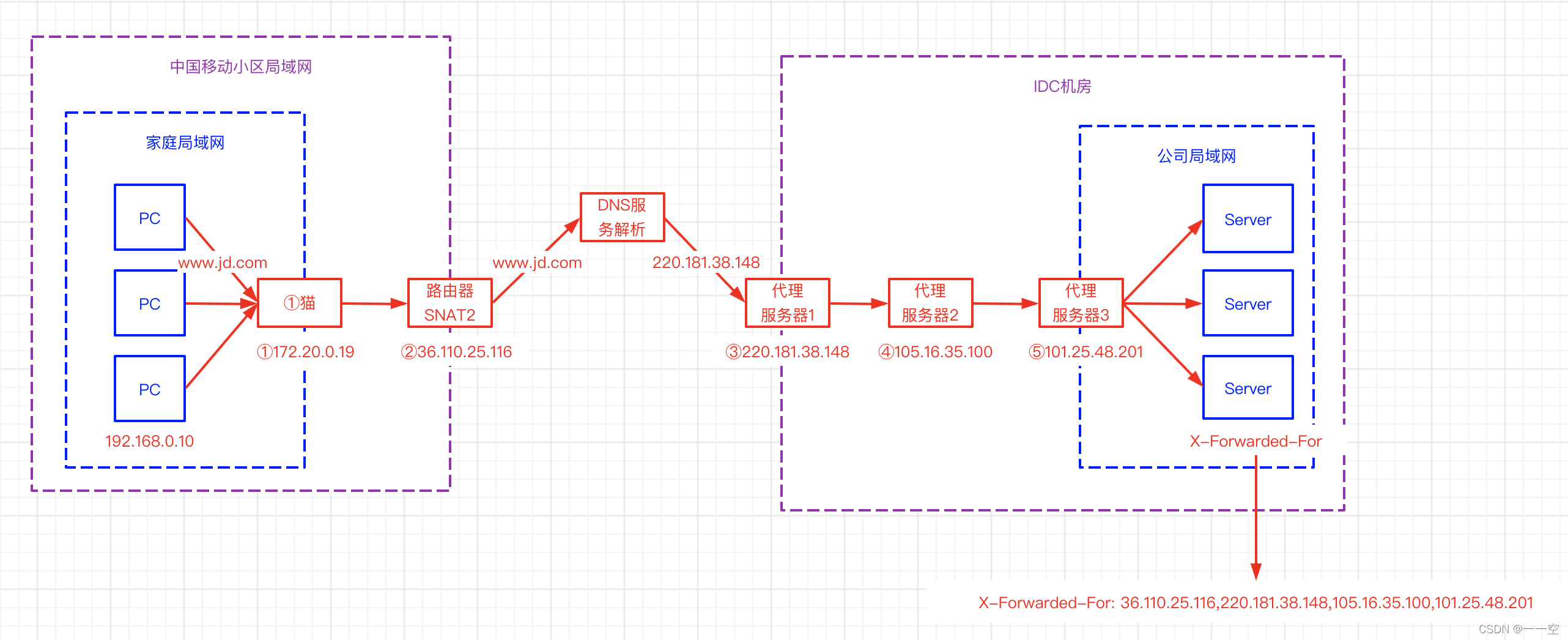
X-Forwarded-For详解、如何获取到客户端IP
随机推荐
Opencv learning log 30 -- histogram equalization
Matlab comprehensive exercise: application in signal and system
最全编程语言在线 API 文档
Cost accounting [18]
渗透测试 ( 1 ) --- 必备 工具、导航
[exercise-8] (UVA 246) 10-20-30== simulation
Information security - security professional name | CVE | rce | POC | Vul | 0day
Information security - threat detection - detailed design of NAT log access threat detection platform
Opencv learning log 19 skin grinding
快速转 TypeScript 指南
渗透测试 ( 3 ) --- Metasploit Framework ( MSF )
[exercise -10] unread messages
C语言数组的概念
Gartner: five suggestions on best practices for zero trust network access
Research Report on surgical fluid treatment industry - market status analysis and development prospect prediction
0 - 1 problème de sac à dos (1)
b站 實時彈幕和曆史彈幕 Protobuf 格式解析
Research Report on market supply and demand and strategy of China's earth drilling industry
TCP的三次握手与四次挥手
HDU-6025-Coprime Sequence(女生赛)