当前位置:网站首页>Alice and Bob (2021 Niuke summer multi school training camp 1)
Alice and Bob (2021 Niuke summer multi school training camp 1)
2022-07-06 16:02:00 【It's Xiao Zhang, ZSY】
Alice and Bob
2021 Niuke summer multi school training camp 1 The first question is , I didn't do it at that time , Read this blogger's blog , I understand instantly.
Topic link :https://ac.nowcoder.com/acm/contest/11166/A
source : Cattle from
Title Description
Alice and Bob like playing games. There are two piles of stones with numbers n and m. Alice and Bob take turns to operate, each operation can take away k(k>0) stones from one pile and take away s×k(s≥0) stones from another pile. Alice plays first. The person who cannot perform the operation loses the game.
Please determine who will win the game if both Alice and Bob play the game optimally.
Input description :
The first line contains an integer T(1≤T≤10^4 ) denotes the total number of test cases.
Each test case contains two integers n,m(1≤n,m≤5×10^ 3) in a line, indicating the number of two piles of stones.
Output description :
For each test case, print “Alice” if Alice will win the game, otherwise print “Bob”.
Example 1
Input
Copy
5
2 3
3 5
5 7
7 5
7 7
Output
Copy
Bob
Alice
Bob
Bob
Alice
The main idea of the topic :
A game of two , Each time one person takes one from the pile , At the same time, take it away from another pile k*s individual , Ask who can take it first ;
Ideas :
enumeration , violence , In fact, the idea is very simple , If you can take all the stones in one operation, you will win at this time , We use a two-dimensional array f[i][j] To indicate that the number of stones in the first pile is i The number of stones in the second pile is j The situation of ,f[i][j]=1 Indicates that the state faces two piles of stones, and the number is i,j You can take all the stones in one step ,f[i][j]=0 Indicates that the state faces two piles of stones, and the number is i,j You can't take all the stones at once . According to the title f[k][sk] or f[sk][k] It must be able to take it all at once , So enumeration s And k Find out the status of all the first to win
#include <iostream>
#include <cstdio>
#include <algorithm>
#include <math.h>
#include <string.h>
using namespace std;
bool f[5001][5001];
int main()
{
for(int i=0;i<=5000;i++)
{
for(int j=0;j<=5000;j++)
{
if(f[i][j]==0)
{
for(int k=1;k+i<=5000;k++)
{
for(int s=0;s*k+j<=5000;s++)
f[i+k][j+s*k]=1;
}
for(int k=1;k+j<=5000;k++)
{
for(int s=0;s*k+i<=5000;s++)
f[i+s*k][j+k]=1;
}
}
}
}
int t,n,m;
cin>>t;
while(t--)
{
scanf("%d%d",&n,&m);
if(f[n][m]==0)
cout<<"Bob"<<endl;
else
cout<<"Alice"<<endl;
}
}
边栏推荐
- Information security - threat detection - Flink broadcast stream broadcaststate dual stream merging application in filtering security logs
- MySQL import database error [err] 1273 - unknown collation: 'utf8mb4_ 0900_ ai_ ci’
- 【练习-8】(Uva 246)10-20-30==模拟
- Penetration testing (5) -- a collection of practical skills of scanning King nmap and penetration testing tools
- Research Report of exterior wall insulation system (ewis) industry - market status analysis and development prospect prediction
- Opencv learning log 18 Canny operator
- C语言学习笔记
- 用C语言写网页游戏
- Information security - security professional name | CVE | rce | POC | Vul | 0day
- 渗透测试 ( 4 ) --- Meterpreter 命令详解
猜你喜欢
Web based photo digital printing website
b站 实时弹幕和历史弹幕 Protobuf 格式解析
信息安全-威胁检测-NAT日志接入威胁检测平台详细设计
VS2019初步使用
D - Function(HDU - 6546)女生赛
Determine the Photo Position
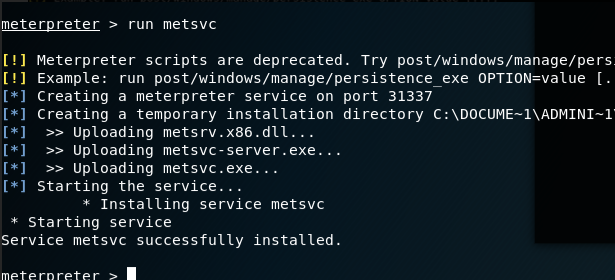
渗透测试 ( 3 ) --- Metasploit Framework ( MSF )
![MySQL import database error [err] 1273 - unknown collation: 'utf8mb4_ 0900_ ai_ ci’](/img/e6/f4a696179282fe1f4193410c5a493a.png)
MySQL import database error [err] 1273 - unknown collation: 'utf8mb4_ 0900_ ai_ ci’

STM32 how to use stlink download program: light LED running light (Library version)
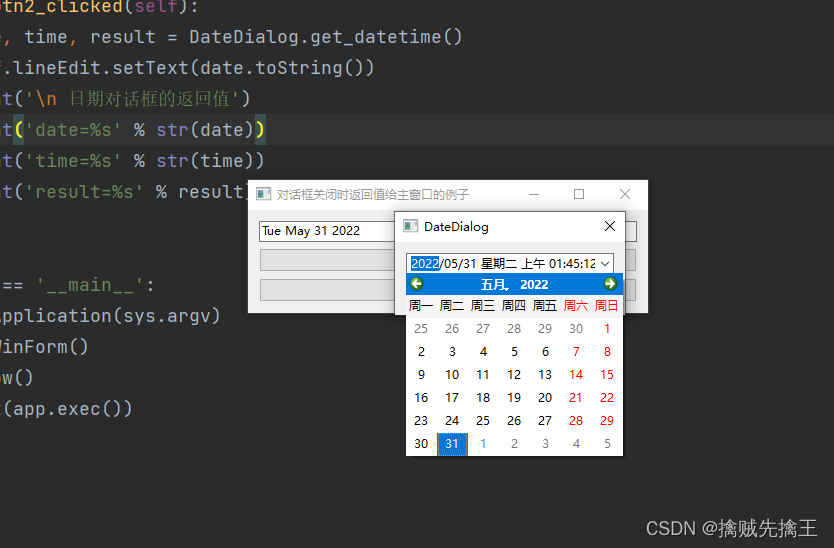
PySide6 信号、槽
随机推荐
Common configuration files of SSM framework
F - Birthday Cake(山东省赛)
Research Report on market supply and demand and strategy of China's earth drilling industry
[exercise-8] (UVA 246) 10-20-30== simulation
Essai de pénétration (1) - - outils nécessaires, navigation
PySide6 信号、槽
New to redis
Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
Analyse du format protobuf du rideau en temps réel et du rideau historique de la station B
China's salt water membrane market trend report, technological innovation and market forecast
Research Report of cylindrical grinder industry - market status analysis and development prospect forecast
Gartner:关于零信任网络访问最佳实践的五个建议
HDU-6025-Coprime Sequence(女生赛)
[exercise-5] (UVA 839) not so mobile (balance)
Research Report of exterior wall insulation system (ewis) industry - market status analysis and development prospect prediction
【练习-7】Crossword Answers
Accounting regulations and professional ethics [2]
渗透测试 ( 5 ) --- 扫描之王 nmap、渗透测试工具实战技巧合集
渗透测试 ( 4 ) --- Meterpreter 命令详解
b站 实时弹幕和历史弹幕 Protobuf 格式解析