当前位置:网站首页>Gartner: five suggestions on best practices for zero trust network access
Gartner: five suggestions on best practices for zero trust network access
2022-07-06 15:47:00 【Empty one by one】
In recent years , Zero trust has been widely recognized at home and abroad , For example, the United States Department of defense 、 Standardization Organization NIST Are actively promoting the landing and standardization of zero trust , The Ministry of industry and information technology will also “ Zero trust security ” Include key network security technologies that need to be broken through , Many domestic zero trust standard projects are also being actively promoted . however , The road of zero trust Still full of challenges . Although zero trust can bring many benefits , But when it really starts to be implemented , Many enterprises still lack experience in landing .Gartner Through research and Analysis , Summarize the successful implementation of zero trust network access (ZTNA) Five suggestions for the project . Qianxin identity security laboratory combines its own practical experience , Here I'll give you some simple explanations .
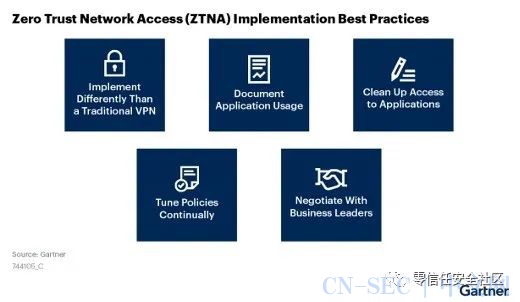
Plan your business needs as early as possible
Gartner It is suggested that business organizations should implement zero trust , Start analyzing and recording the usage of enterprise applications and other services as soon as possible . for example , utilize ZTNA Provided by the supplier “ Application discovery ” Tools , Analyze the business needs of all departments in the enterprise , You can ask the department leaders to know the access rights required by each department . Use similar methods , Get a standardized configuration , It can speed up the implementation process .
Actually , The implementation of zero trust largely depends on the business status of the enterprise 、 The security situation 、 Team status and other factors . therefore , It is suggested to use system engineering thinking to achieve zero trust , Application “ Planning first , Step by step construction ” To carry out zero trust construction . for example , We should first sort out the applicable scenarios of zero trust , And set the priority of construction work according to business needs .
Combing the scene is to find the entry point of zero trust construction , At the same time, it helps strengthen the architectural vision , Avoid ignoring the scalability of the overall architecture during later construction .
Get the support of enterprise executives and leaders
Obtaining the support of senior executives and leaders of all departments is also an important prerequisite for the implementation of the zero trust project , Also accord with “ Planning first , Step by step construction ” The idea of .
Build any infrastructure 、 Start a new business , First of all, the vision should be clear . Through the enterprise business and IT Achieve the strategic vision of zero trust , Analyze the current situation to clarify the gap with the ultimate goal of zero trust , And form a construction road map through Task Disassembly , Follow the road map , Build and run one by one .
Simply speaking , When building zero trust projects , A clear vision is to let the enterprise CIO The person in charge of the level knows the value of zero trust , Bring zero trust into the enterprise's security strategy , It needs to combine the business strategy of the enterprise with IT Strategy to align . If executives and other leaders disagree , They should communicate with them to understand their concerns , And solve the problem to dispel their doubts .

Zero trust is not “ Upgraded version ”VPN
VPN The purpose of existence is to connect the remote network , Employees on the external network can also connect to the internal network to access the required resources . stay VPN Many safety factors were not considered at the beginning of the design , So that remote access has become a short board of many enterprise security systems . In many public reports , You can see it VPN Related security incidents emerge in endlessly , Many enterprises have also realized the tradition VPN The limitations of , We hope to replace the existing products with zero trust access VPN product .
According to the Gartner Research findings , Some enterprises initially deployed zero trust network access (ZTNA) It adopts the tradition of configuration VPN In a similar way , All users are granted the same permission to access all applications . However , This is just going to ZTNA As a VPN Of “ upgrade ” edition , Did not realize the real benefits of zero trust .
Zero trust is actually transferring security measures from the network to specific personnel 、 Equipment and business assets ; Superimpose identity based logical boundaries on network boundaries ; Its essence is based on identity 、 Fine grained dynamic access control mechanism .
therefore , We should first identify and analyze the user's identity , Based on the analysis and evaluation results, users are appropriately grouped and configured with appropriate access rights . for example , Cooperative suppliers cannot access or obtain sensitive data of the enterprise .
In other words , Zero trust is a fine-grained access control system based on identity superimposed on the existing security system of the enterprise , In this way, a dynamic virtual identity security boundary is constructed . Complex network access control rules are transferred to a unified identity based access control policy , It is conducive to the safe operation and maintenance and the improvement of operation efficiency , It can also better meet the regulatory and compliance needs of enterprise data and privacy .
Sort out and update the access rights of enterprise applications
Under the trend of boundary fuzziness , Security challenges have become unprecedented , After the event statistics and in-depth investigation and analysis of various security incidents , It is not difficult for us to find out the main and identity of these events 、 jurisdiction 、 The loopholes in the three dimensions of business are closely related . The privilege vulnerability is mainly reflected in the lack of fine-grained privilege control 、 Lack of dynamic access control mechanism . These two points lead to abuse of authority 、 The root cause why attackers can move sideways wantonly .
therefore , Enterprises should take the opportunity of implementing zero trust projects , Reorganize and update the access rights of applications, data and other services . for example , Clean up third parties that no longer have business relations ( supplier ) Access rights of 、 Cancel the access rights of the resigned employees 、 And update access permissions for employees whose roles have changed .
Constantly adjust access policies to suit 、 Changing business needs
according to Gartner The research of , Many enterprises with zero trust implementation experience feedback that , They found that “ Once and for all ” The access strategy of is unrealistic , The access strategy should be constantly adjusted with the development and change of enterprise business requirements . If the enterprise needs to deploy new applications due to business expansion , Then the implementation team needs to add new access policies .
The newly added and existing access policies are not immutable , In addition to upgrading according to the application 、 Business needs adjustment and update , It should also be based on user identity 、 Terminal environment 、 Access context and other aspects are dynamically adjusted . The implementation team should realize that updating and adjusting the access policy is a continuous work , Only in this way can we meet and adapt to the development of the enterprise .
That's what it's all about Gartner Successfully implement zero trust remote access for enterprises (ZTNA) Some simple interpretations of the five suggestions summarized , It is some suggestions on specific construction work when implementing the zero trust project , It is also some lessons learned by early adopters of zero trust .
All in all , The construction of zero trust needs to be managed and promoted through the engineering system , Planning first , Step by step construction . Aggregate zero trust capability and architecture with the target operating environment , Endogenously generate security capabilities into various business scenarios , Escort the digital transformation of enterprises .
边栏推荐
- Shell脚本编程
- 渗透测试 ( 7 ) --- 漏洞扫描工具 Nessus
- Opencv learning log 19 skin grinding
- Medical colposcope Industry Research Report - market status analysis and development prospect forecast
- Market trend report, technical innovation and market forecast of Chinese hospital respiratory humidification equipment
- China's earthwork tire market trend report, technical dynamic innovation and market forecast
- Learning record: understand systick system timer and write delay function
- Research Report on shell heater industry - market status analysis and development prospect forecast
- Accounting regulations and professional ethics [4]
- 【练习4-1】Cake Distribution(分配蛋糕)
猜你喜欢
1010 things that college students majoring in it must do before graduation
【练习-7】Crossword Answers
Learning records: serial communication and solutions to errors encountered
Record of force deduction and question brushing
学习记录:STM32F103 时钟系统概述工作原理
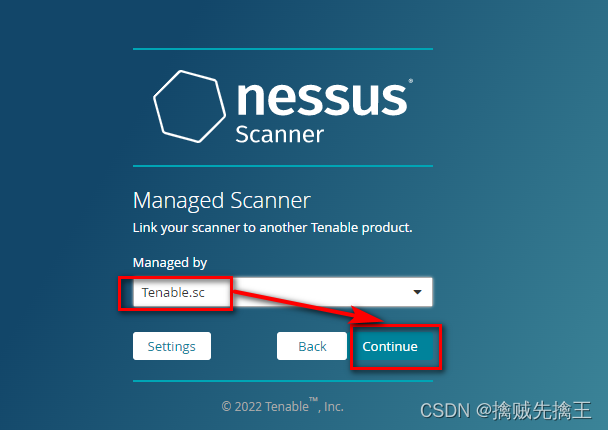
渗透测试 ( 7 ) --- 漏洞扫描工具 Nessus
STM32学习记录:LED灯闪烁(寄存器版)

动态规划前路径问题优化方式
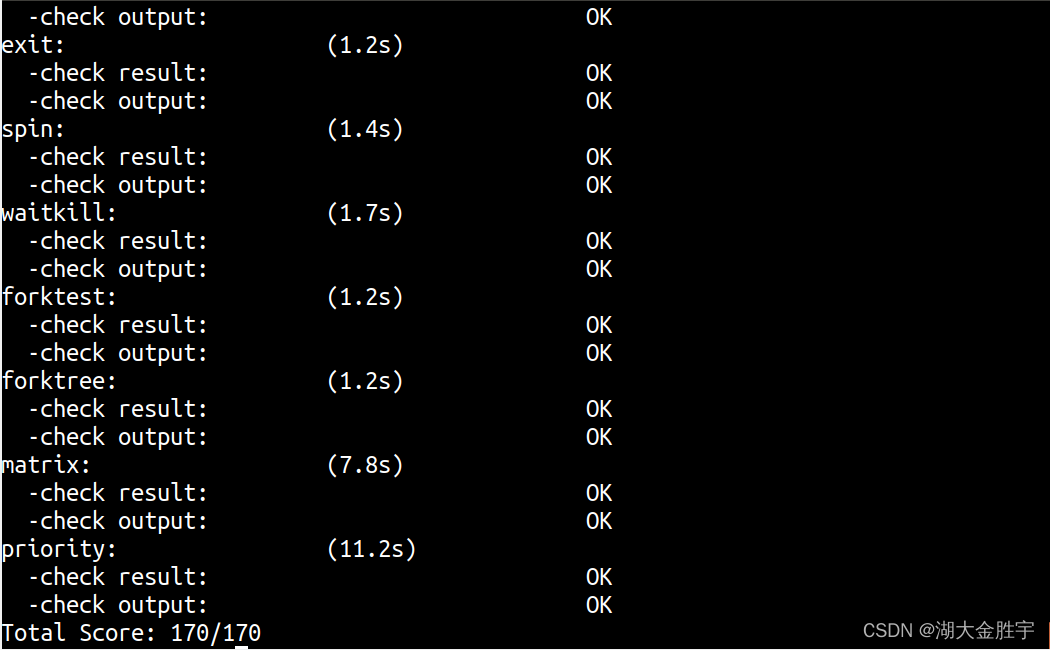
ucore lab 6
C语言是低级和高级的分水岭
随机推荐
JS调用摄像头
Accounting regulations and professional ethics [5]
对iptables进行常规操作
China's earthwork tire market trend report, technical dynamic innovation and market forecast
nodejs爬虫
Cost accounting [18]
Research Report on market supply and demand and strategy of Chinese graphic screen printing equipment industry
Borg Maze (BFS+最小生成树)(解题报告)
Record of force deduction and question brushing
ucorelab4
TCP的三次握手与四次挥手
Accounting regulations and professional ethics [1]
信息安全-安全专业名称|CVE|RCE|POC|VUL|0DAY
【练习-6】(Uva 725)Division(除法)== 暴力
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
Research Report on market supply and demand and strategy of China's earth drilling industry
[analysis of teacher Gao's software needs] collection of exercises and answers for level 20 cloud class
初入Redis
C语言数组的概念
【练习-9】Zombie’s Treasure Chest