当前位置:网站首页>Technology sharing | packet capturing analysis TCP protocol
Technology sharing | packet capturing analysis TCP protocol
2022-07-06 19:59:00 【Hua Weiyun】
This article is excerpted from the internal textbook of Hogwarts testing and development society
TCP The protocol is in the transport layer , A connection oriented 、 reliable 、 Transport layer communication protocol based on byte stream .
Environmental preparation
Classify interface testing tools , It can be classified as follows :
- Network sniffer tool :tcpdump,wireshark
- Agent tools :fiddler,charles,anyproxyburpsuite,mitmproxy
- Analysis tools :curl,postman,chrome Devtool
Caught analysis TCP agreement
tcpdump
tcpdump Is a The of packets transmitted over a network “ head ” Completely intercepted to provide analysis Tools for . It supports for network layer 、 agreement 、 host 、 Network or port filtering , And provide and、or、not And other logical statements to remove useless information .
Give Way tcpdump Always monitor 443 port , If there is any difference, enter it into log In file
sudo tcpdump port 443 -v -w /tmp/tcp.log Use this command , Will put the report in the directory /tmp/tcp.log in .
| Common parameters | meaning |
|---|---|
| port 443 | monitor 443 port |
| -v | Output more detailed information |
| -w | Write data to log in |
wireshark
wireshark It is also a network sniffing tool , In addition to having tcpdump function , There are more extensions , For example, analysis tools , But in interface testing , The process of capturing packets is often carried out on the server , Servers generally do not provide UI Interface , therefore wireshark Unable to work on server , Can only use tcpdump Grab bag generation log, And then log Import wireshark Use , There is UI Analysis on the client of the interface .
Caught analysis TCP agreement
Grab one http Of get request :
- Search on Baidu mp3
http://www.baidu.com/s?wd=mp3 - use tcpdump Intercept this get request , And generate log
- use wireshark open tcpdump Generated log
Use wireshark see log:

log The first few messages are three handshakes . Because the channel is unreliable , Before sending the data , It is necessary to ensure channel stability , And three handshakes are like the following operations :
- The first handshake : When establishing a connection , The client sends syn package (syn=j) To the server , And enter SYN_SENT state , Wait for server to confirm .
- The second handshake : Server received syn package , Must confirm customer's SYN(ack=j+1), At the same time, I also send a SYN package (seq=k), namely SYN+ACK package , At this time, the server enters SYN_RECV state ;
- The third handshake : Client receives server's SYN+ACK package , Send confirmation package to server ACK(ack=k+1), This package has been sent , Client and server access ESTABLISHED(TCP Successful connection ) state , Complete three handshakes .
After three handshakes , Can further communicate , It looks like this :

At the end of the communication , Four waves are also required :

- First wave : The client sends a... To the server FIN, Request to turn off data transfer .
- Second wave : The server received... From the client FIN, Send a ACK, among ack The value is equal to the FIN+SEQ.
- Third wave : The server sends a... To the client FIN, Tell client application to close .
- Fourth wave : The client receives... From the server FIN, Reply to one ACK To the server . among ack The value is equal to the FIN+SEQ.
Be careful : A request may be divided into multiple packets , So is a data , So in wireshark You'll see a lot of bags .
边栏推荐
- 121. The best time to buy and sell stocks
- 转让malloc()该功能后,发生了什么事内核?附malloc()和free()实现源
- golang的超时处理使用技巧
- Example of applying fonts to flutter
- 腾讯字节等大厂面试真题汇总,网易架构师深入讲解Android开发
- Configuration and simple usage of the EXE backdoor generation tool quasar
- JVM_常见【面试题】
- Social recruitment interview experience, 2022 latest Android high-frequency selected interview questions sharing
- 腾讯T2大牛亲自讲解,跳槽薪资翻倍
- MySql必知必会学习
猜你喜欢
Analysis of rainwater connection
Systematic and detailed explanation of redis operation hash type data (with source code analysis and test results)
Cesium 点击绘制圆形(动态绘制圆形)
枚举根据参数获取值
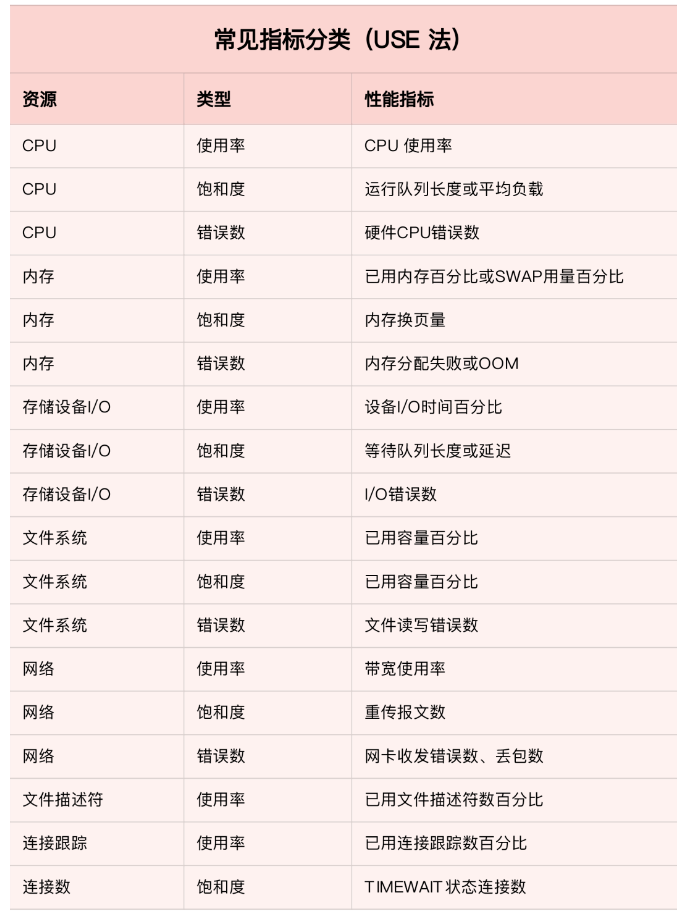
系统与应用监控的思路和方法
Information System Project Manager - Chapter VIII project quality management
Learn to explore - use pseudo elements to clear the high collapse caused by floating elements

Social recruitment interview experience, 2022 latest Android high-frequency selected interview questions sharing
Tencent T3 teaches you hand in hand. It's really delicious
学习打卡web
随机推荐
Phoenix Architecture 2 - accessing remote services
Groovy基础语法整理
logstash高速入口
Transformer model (pytorch code explanation)
[translation] linkerd's adoption rate in Europe and North America exceeded istio, with an increase of 118% in 2021.
使用ssh连接被拒
微信小程序常用集合
Web开发小妙招:巧用ThreadLocal规避层层传值
算法面试经典100题,Android程序员最新职业规划
The "white paper on the panorama of the digital economy" has been released with great emphasis on the digitalization of insurance
测试用里hi
Poj1149 pigs [maximum flow]
js获取浏览器系统语言
PHP and excel phpexcel
Tencent Android development interview, basic knowledge of Android Development
Database specific interpretation of paradigm
力扣101题:对称二叉树
A5000 vgpu display mode switching
小微企业难做账?智能代账小工具快用起来
Recursive implementation of department tree