当前位置:网站首页>HW primary flow monitoring, what should we do
HW primary flow monitoring, what should we do
2022-07-07 15:22:00 【The end of the world and you】
HW Primary flow monitoring , What the hell to do
1. Primary monitoring tasks
Daily flow alarm detection and preliminary flow detection , Maybe sometimes the project manager asks to upgrade the equipment , And the daily newspaper of that day ( Where will the project manager have a special template , You don't need to download templates on the network or edit them yourself )
Overall process :
Generally, the monitoring group reports the monitored malicious attack traffic to the research and judgment group ( There is a special submission template ), After analyzing the reported traffic, the research and judgment team determines that the traffic is attack traffic , Then transfer to the disposal group , The disposal group will this malicious ip To ban ; If there is a successful attack , The research and judgment team needs to be synchronized to the traceability reaction team and the emergency response team , The personnel of the traceability reaction group and the research and judgment group trace the source of the event , The of the emergency response group shall carry out emergency response for the machine .
2. common HW equipment
1- Chianxin's heavenly eye ( Flow analysis and flow monitoring , And you can use his log retrieval module to trace the source .)
2- Chianxin's pepper map
3- Green alliance's missing scanning equipment
4- Micro step honeypot
5- A convincing firewall
6- Deeply convinced VPN
7- Tianqing of chianxin ( The function and interface are similar to 360 Safety guard )
More about safety equipment , Please refer to this article
3. Job content
Project start , Check familiar equipment
Generally, the central console of the equipment has the usage information of the equipment , Mainly look at the equipment :
- CPU Usage rate
- Memory usage
- Data throughput
- Space storage rate
If the occupancy rate is found to be too high , It has affected the normal operation of the platform , Report to the project manager in time !
Daily flow analysis
In the threat analysis, you can see the specific information of attack traffic , Generally, you can filter the flow of the day
Attack traffic with Web Mainly attack traffic , It mainly looks at the request packets and response packets of traffic (PCAP) Content :
When there are a lot of traffic packets , Need to use the fuzzy search function of the device , Perform filter analysis
Request header :
- url Location
- rerfer Field source IP
- X-Forwarded-For(XFF)
- Cookie
- …
Request body :
- Is there malicious code
- Is there any sensitive information such as user name or password
- …
Response package :
- Status code
- Response Content ( Can be copied as html View in the browser )
4. dried food : Common vulnerability traffic characteristics
Catalog explosion
- A large number of server logs appear 404 request
- There are a lot of non business requests ( Such as accessing a large number of sensitive directories )
sql Inject
- There is obvious malice in the request sql Statements or sensitive characters
- Request body
User-AgentThere may be sqlmap identification - Echo package exists sql Query results ( At this moment, it means that the injection has been successful )
Upload files
- The file name is script file , As malicious php file
- Look at the upload file
Content-typeWhether it has been modified - Check whether the uploaded content contains malicious code ( Generally, they are encrypted Trojans )
- Check whether the echo status is 200, If for 200 Look at the upload path , Find the file on the corresponding server for cloud sandbox analysis ( Don't be silly to analyze locally , General manufacturers will have supporting cloud sandbox equipment ), If the malicious Trojan horse GG 了
XSS
In the attack and defense drill ,XSS Attacks are very uncommon
- Whether there is XSS sentence
- Echo whether there is XSS sentence ( The key )
Command execution
It's usually exposed RCE Vulnerability execution , More commonly, red teams use 0day The attack , If it does 0day attack , The device must not recognize the attack , The defender needs to judge according to his own experience
- JAVA Developed website , Pay attention to whether there is java Deserialized string format ( Such as
ROOAB,abecd), If not, see if there is java Calls to sensitive execution classes ( Such asRuntime.java), Also pay attention to whether there isRMI,LDAPWait for such sensitive characters to appear - The data package has system commands ( Such as
whoami) - Check whether the status of the response package is 200, Combine request and response to analyze
Webshell
If you encounter this traffic characteristic and judge that there is no false alarm , You can write a report GG 了
Common kitchen knives , Ice scorpion , Ant sword , Flow characteristic diagram of Godzilla :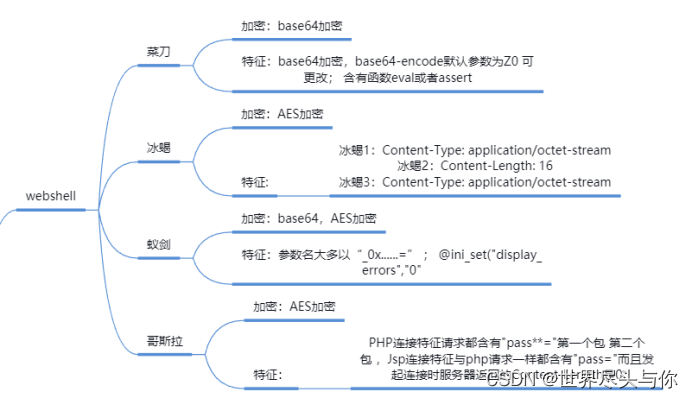
kitchen knife
payload features :
PHP: <?php @eval($_POST['caidao']);?>
ASP: <%eval request(“caidao”)%>
ASP.NET: <%@ Page Language=“Jscript”%><%eval(Request.Item[“caidao”],“unsafe”);%>
Example traffic packets :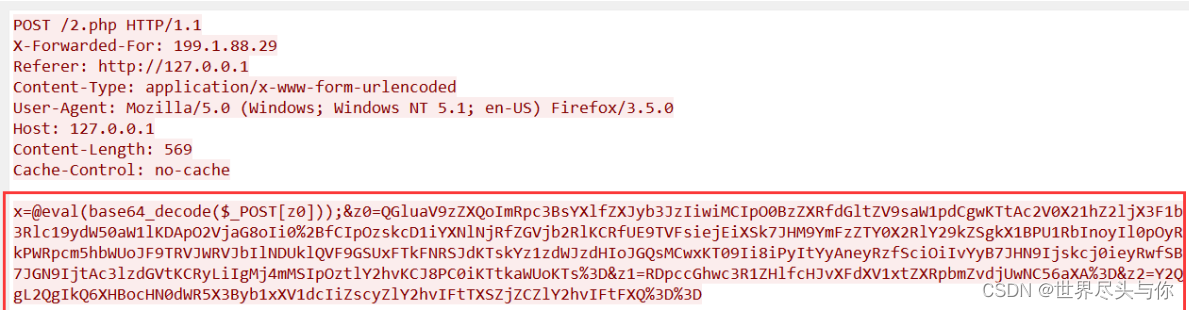
Leech sword
payload features :
Php Use in assert,eval perform ,
asp Use eval
stay jsp It uses Java Class loading (ClassLoader), At the same time, there will be base64 Character features such as encoding and decoding
Example traffic packets :
Every request body exists @ini_set(“display_errors”, “0”);@set_time_limit(0) start . And there are base64 Equal character 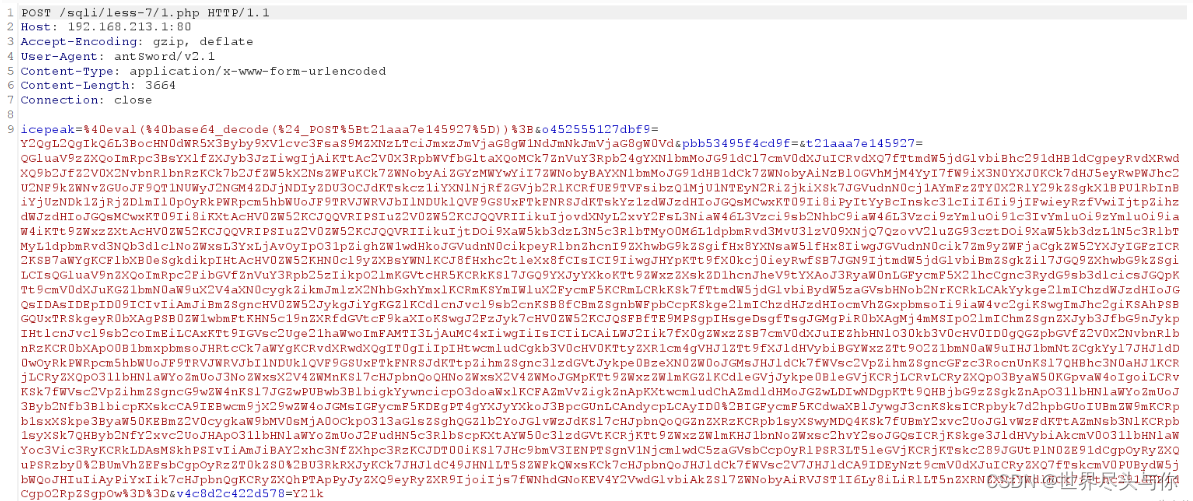
Ma encryption has an obvious feature , That is, parameter names are mostly in "
_0x...." In the form of
Ice scorpion
paylaod analysis :
php There will also be... In the code eval or assert And so on
stay aps Will be in for Loop through a segment of XOR processing
stay jsp Medium is used java Reflection of , So there will be ClassLoader,getClass().getClassLoader() And so on
Ice scorpion 2.0 Flow characteristics :
The returned package status code in the first stage request is 200, The return must be 16 A key
Request package exists :Accept: text/html, image/gif, image/jpeg, ; q=.2, /; q=.2
After establishing the connection cookie There are characteristic characters , All requests Cookie It's all in the form of : Cookie: PHPSESSID=; path=/;
Ice scorpion 3.0 Flow characteristics :
In the request package content-length by 5740 or 5720( May be based on Java Change with version )
In every request header, there is
Pragma: no-cache,Cache-Control: no-cache
Accept:text/html,application/xhtml+xml,application/xml;
q=0.9,image/webp,image/apng,/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Godzilla *️
payload features :
jsp There will be xc,pass Characters and Java Reflection (ClassLoader,getClass().getClassLoader()),base64 Add and decode
php,asp Is a common sentence
Godzilla flow analysis :
Of all requests Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Of all responses Cache-Control: no-store, no-cache, must-revalidate,
And in all requests Cookie Both the middle and the back ; features
At present, the traffic from Godzilla can bypass the detection of security equipment if it is slightly confused , It's dangerous , Generally, the only way to take is to check and kill the virus on the ground
Common framework vulnerabilities
It mainly depends on your familiarity with the framework
边栏推荐
猜你喜欢

Guangzhou Development Zone enables geographical indication products to help rural revitalization

数学建模——什么是数学建模
【OBS】RTMPSockBuf_Fill, remote host closed connection.

【OBS】RTMPSockBuf_ Fill, remote host closed connection.
CTFshow,信息搜集:web6
【跟着江科大学Stm32】STM32F103C8T6_PWM控制直流电机_代码
There is a cow, which gives birth to a heifer at the beginning of each year. Each heifer has a heifer at the beginning of each year since the fourth year. Please program how many cows are there in the
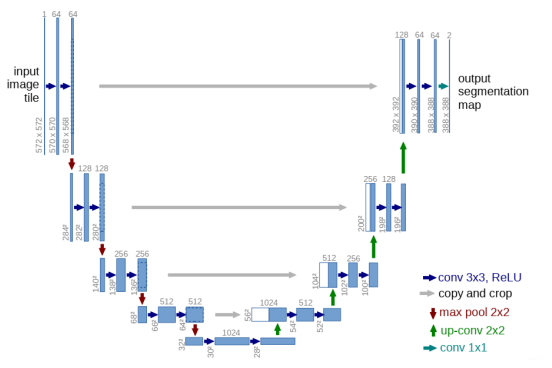
【深度学习】语义分割实验:Unet网络/MSRC2数据集
【数字IC验证快速入门】26、SystemVerilog项目实践之AHB-SRAMC(6)(APB协议基本要点)

TypeScript 发布 4.8 beta 版本
随机推荐
【數字IC驗證快速入門】26、SystemVerilog項目實踐之AHB-SRAMC(6)(APB協議基本要點)
Briefly describe the working principle of kept
Why do we use UTF-8 encoding?
广州开发区让地理标志产品助力乡村振兴
【服务器数据恢复】某品牌StorageWorks服务器raid数据恢复案例
【数字IC验证快速入门】26、SystemVerilog项目实践之AHB-SRAMC(6)(APB协议基本要点)
Andriod --- JetPack :LiveData setValue 和 postValue 的区别
CTFshow,信息搜集:web5
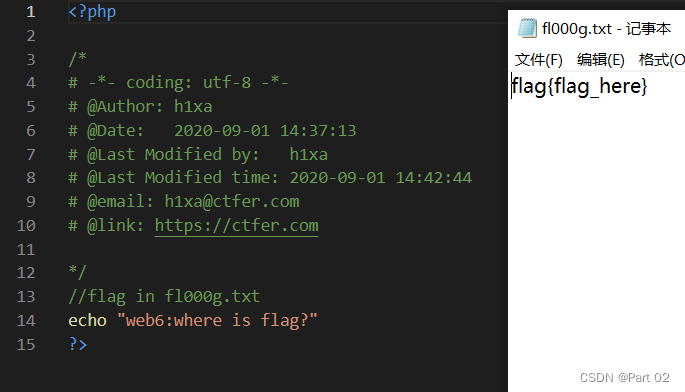
Ctfshow, information collection: web6
STM32F103C8T6 PWM驱动舵机(SG90)
MySQL bit type resolution
2022全开源企业发卡网修复短网址等BUG_2022企业级多商户发卡平台源码
[target detection] yolov5 Runtong voc2007 data set
Ctfshow, information collection: web8
Stm32f103c8t6 PWM drive steering gear (sg90)
Niuke real problem programming - day15
#HPDC智能基座人才发展峰会随笔
Niuke real problem programming - Day11
简述keepalived工作原理
2022年5月互联网医疗领域月度观察