当前位置:网站首页>Billions of citizens' information has been leaked! Is there any "rescue" for data security on the public cloud?
Billions of citizens' information has been leaked! Is there any "rescue" for data security on the public cloud?
2022-07-04 21:17:00 【Sina Finance blockchain】
Past two days , A piece of news , Cause the industry boiling !
The user data of a public cloud organization leaked on the Internet , It may involve hundreds of millions of citizens , And has flowed overseas .
Some people in the dark network even openly 10 Bitcoin sells the leaked data , It also provides data types and descriptions :
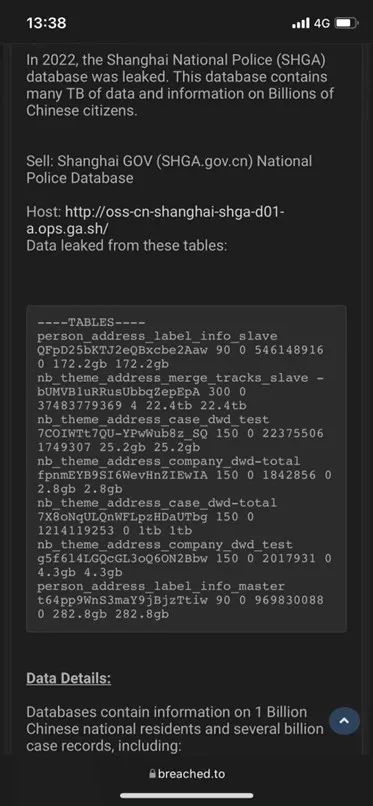
According to netizens, deep grilling , The leaked database is suspected to be built by well-known public cloud institutions in China , The bid winning funds of the project amount to 2000 More than ten thousand .

If this massive data leak is true and the data is used by criminals , In the later stage, we may face various uncontrollable consequences , such as : fraud 、 Loan fraud and so on , Creepy .
This is not the case , There is also a problem of public cloud data leakage in the world . According to foreign media reports , After American private security company TigerSwan 9,400 Employment resumes in unprotected AWS After the leak on the database , Security company researchers Kromtech Expose another AWS Storage data leakage events , Well known cloud service providers BroadSoft The data hosted by Time Warner on Amazon storage server is not properly protected , Cause to exceed 400 Million customer information leaked online , This includes the customer address 、 Account settings 、 Phone number 、 user name 、MAC Address 、 Modem hardware serial number and other sensitive information .
stay 2018 At the beginning of year , Hackers are suspected of using iCloud Security mechanism defects , Got many nude photos of women , And spread crazily on the Internet that Apple doesn't have its own public cloud service , Instead, Amazon AWS And Microsoft Azure Services provided .iCloud The safety problem is that at that time “ Find my iPhone” Functional design flaws , And there was no mandatory double verification .
Some netizens commented on it , The risk of data security mainly comes from three aspects , The risk of the first user , Second, the risk of ash production , Third, the risks of cloud merchants , One of the biggest risks is the risk of cloud merchants , The eggs are in people's baskets. Don't you just pinch them .
Yun Shang is both a referee and an athlete , Unless there is some hope for third-party supervision .
Frequent public cloud security problems , I can't help but question : Can the data on the public cloud be safe ?

Security becomes a public cloud “ Final examination ”
Public cloud (public cloud) Is a model based on standard Cloud Computing , In public , Service providers create resources , Such as application and storage , The public can access these resources through the Internet ,IaaS( Infrastructure as a service )、PaaS( Platforms and services ) and SaaS( Software and services ) There are three service modes of cloud computing . all the time , Public cloud is considered to be the main form of Cloud Computing , In the domestic development in full swing , For relatively low cost and reliable and secure distributed data storage . And the properties of shared resources , Become the first choice for enterprise customer data storage and Computing .
According to the type of market participants , It can be divided into five categories :
1、 Traditional telecom infrastructure operators , Include China Mobile 、 China Unicom and China Telecom ;
2、 Local cloud computing platform led by the government
3、 The public cloud platform created by internet giants
4、 Partial original IDC Operator,
5、 For domestic enterprises with foreign technical background or introducing foreign cloud computing technology
The public cloud has a stable user base . near 60% Has been used by enterprises for more than two years , Public cloud has been recognized . According to the 2021 year ,IDC Release 《 China's public cloud service market (2020 In the fourth quarter ) track 》 The report , Show 2020 China in the fourth quarter of IaaS The market scale is 34.9 Billion dollars , but “ Joy and sorrow ” Half , According to relevant research results , The lack of information security is the most important problem faced by enterprises applying public cloud, and it is also the most concerned problem of enterprises .50.8% Of enterprises believe that the problem of applying public cloud is that information security is not guaranteed .
And Internet security level protection and trusted cloud authentication are the most valued qualifications of enterprises . Investigation found , More than 90% of the surveyed enterprises believe that cloud service providers need to have relevant qualifications . among , Enterprises protect the Internet security level (69.6%) And trusted cloud (65.2%) Highest recognition , Security and credibility have become the primary needs of enterprise users .

There are also data security issues “ save ” Do you ?
Before the question , We need to ask more “ How to solve ”?
Some enterprises speak from their own experience : Part of our business is on the public cloud , The core business data is still under your control , At the same time, it is also found that the asset exposure of the public cloud is relatively large , Need more refined asset management , Cloud manufacturers should do a good job. Even they can't parse data , Only in this way can party a have a higher sense of security .
This is a risk sharing approach . But the symptoms still need to be addressed , We need to start with the security of the public cloud .
The present , There are several major safety methods that have been widely verified by the market :
encryption
According to the research , People's awareness of data encryption is still not strong , This is also the root cause of many catastrophic data leakage events . The data in the public cloud is not encrypted , It is no different from a dereliction of duty for managers : Enterprise managers need to carefully check the encryption options of cloud computing service providers , Limit the number of administrators who know the key , Do not use drive based encryption , And use a key for all objects .
Multifactor certification
Enterprises should enforce strong passwords for users accessing cloud computing data , Or take password protection beyond , The latter often means taking multifactor certification : Through fingerprints 、 Voiceprint scanning , Or set what only a few users know “ clearance ” problem . However , Even with strong authentication , There is still no way to avoid the risk from internal personnel management . Enterprises can apply data analysis to find some strange access patterns , Such as downloading key files or peeping into areas unrelated to work tasks , And strictly restrict the regional access of managers and coders .
VPN management
In Cloud Computing VPN yes “ free ” Set up and manage , So please use them to protect data . Restrict users to their own areas , And lock it out of the visibility of other areas . This is particularly important for preventing command and control botnets , Because these attacks allow attackers to do a lot of damage effortlessly . Enterprises access as many layers as possible , So that the cleanup path of a given data set does not exist at all . Traffic monitoring is very useful here , Because unusual downloads or uploads can be marked as suspicious .
Data management tools
People often hear that data objects are leaked , The solution is to deploy data management software tools , Search and locate data and monitor usage . In addition, in the virtual machine , Temporary local instance drives can also expose data . Such as instance crash , But the staff couldn't find the data changes , It indicates that the server may have crashed , Use your own removable drive . If the server crash is only temporary , and SSD The hard disk has a lot of spare space , And can only be deleted in the background , Cloud computing providers should pay attention to preventing new tenants from entering the spare space , Avoid data theft .
Backup and disaster recovery (DR)
For data protection , How important can continuous backup or snapshots play , There is always controversy in the industry . Snapshots are attractive because they provide good metrics , If you do well , The snapshot permanent storage strategy with multi region or multi cloud replication looks very promising , This is true both economically and from the perspective of data protection . however , It is suggested that enterprises should do some research on this problem , Because not all solutions are equal .
In dealing with safety issues , The security personnel of a large cloud platform responded to this : Do a good job in safety , Not just based on safety , If you think about finding events, you will get grades , Instead, we should have the idea of reducing the occurrence , Analyze the root cause , Provide the ability to help the business , Avoid safety incidents , Through this reduction , Improve the positive and negative play of recall , To approach serious security incidents 0 happen . At the same time, ensure the security of a large cloud platform , It needs a combination of dynamic and static , The dynamic part requires a large number of experts to continuously engage in security attack and defense , The static level needs to provide strong impetus for cloud security attack and defense from the technical aspect .
Data security is like a sword hanging high , Point directly at each of us . Especially for the public cloud, which stores huge amounts of personal information and privacy data , Once leaked , Its secondary disasters and threats will increase exponentially . When will public cloud data leakage stop ? We need to keep asking questions and taking actions .
边栏推荐
猜你喜欢
华为ensp模拟器 三层交换机

Pytorch---使用Pytorch实现LinkNet进行语义分割
Render function and virtual DOM

Detailed explanation of multi-mode input event distribution mechanism
![[1200. Différence absolue minimale]](/img/fa/4ffbedd8f24c75a20d3eaeaf0430ae.png)
[1200. Différence absolue minimale]

Explication détaillée du mécanisme de distribution des événements d'entrée multimodes
FastDfs的快速入门,三分钟带你上传下载文件到云服务器
接口設計時的一些建議
UTF encoding and character set in golang

仿ps样式js网页涂鸦板插件
随机推荐
杰理之AD 系列 MIDI 功能说明【篇】
Why is TCP three handshakes and four waves
[observation] Lenovo: 3x (1+n) smart office solution, releasing the "multiplier effect" of office productivity
The video sound of station B is very low - solution
Configuration of DNS server of Huawei ENSP simulator
In the face of the same complex test task, why can the elder sort out the solution quickly? Ali's ten-year test engineers showed their skills
多模输入事件分发机制详解
Google colab踩坑
福昕PDF编辑器v10.1.8绿色版
Advantages of semantic tags and block level inline elements
y56.第三章 Kubernetes从入门到精通 -- 业务镜像版本升级及回滚(二九)
Hands on deep learning (III) -- convolutional neural network CNN
【1200. 最小絕對差】
记一次重复造轮子(Obsidian 插件设置说明汉化)
Y56. Chapter III kubernetes from entry to proficiency -- business image version upgrade and rollback (29)
[solution] paddlepaddle 2 X call static graph mode
torch.tensor和torch.Tensor的区别
Remember to build wheels repeatedly at one time (the setting instructions of obsidian plug-in are translated into Chinese)
测试员的算法面试题-找众数
吐槽 B 站收费,是怪它没钱么?