当前位置:网站首页>DDoS attack principle, the phenomenon of being attacked by DDoS
DDoS attack principle, the phenomenon of being attacked by DDoS
2022-07-05 11:10:00 【IDC02_ FEIYA】
DDOS Attack principle , By ddos The phenomenon of attack
Distributed denial of service (DDOS:Distributed Denial of Service) Attack means with the help of customers / Server technology , Combine multiple computers as an attack platform , Launch on one or more targets DoS attack , This will multiply the power of denial of service attacks . Usually , An attacker using a stolen account will DDoS The master program is installed on a computer , At a set time, the master program will communicate with a large number of agents , The agent has been installed in Internet On many computers on . When the agent receives instructions, it launches an attack . Using customers / Server technology , The master program can activate hundreds of agent runs in a few seconds .
· DDOS Attack principle
DoS There are many ways to attack , The most basic DoS An attack is to use reasonable service requests to occupy too much service resources , So that legitimate users can not get the response of the service .
DDoS The means of attack are traditional DoS A kind of attack mode based on attack . Single DoS Attacks are usually one-on-one , When attacking the target CPU Low speed 、 The performance indexes such as small memory or small network bandwidth are not high, and its effect is obvious . With the development of computer and network technology , The processing power of computers is growing rapidly , Memory is greatly increased , At the same time, there are Gigabit networks , This makes DoS The difficulty of the attack has increased - Target against malicious attack packets ” Digestion ” A lot more , For example, your attack software can send every second 3,000 An attack pack , But my host and network bandwidth can handle every second 10,000 An attack pack , In this way, the attack will have no effect .
At this time, distributed denial of service attacks (DDoS) And that's what happened . You understand. DoS Words of attack , Its principle is very simple . If we say that the processing capacity of computers and networks has increased 10 times , If attacking with an attacker no longer works , Use by attackers 10 Two attack planes attack at the same time ? use 100 What about Taiwan ?DDoS It's using more puppet machines to launch attacks , Attack the victim on a larger scale than ever before .
The high-speed and widely connected network brings convenience to everyone , Also for the DDoS The attack created extremely favorable conditions . In the era of low-speed networks , When hackers occupy the puppet machine for attack , Always give priority to machines close to the target network , Because the number of hops passing through the router is small , The effect is good . Now, the connection between backbone nodes of telecommunications is based on G For the level of , Between big cities can reach 2.5G The connection of , This allows attacks to be launched from further places or other cities , The location of the attacker's puppet machine can be distributed in a larger range , It's more flexible to choose .
· By DDoS The phenomenon of attack
1、 There is a lot of waiting on the attacked host TCP Connect
2、 The network is full of useless packets , Source address is false
3、 Making high traffic useless data , Causing network congestion , Make the victim host unable to communicate with the outside world
4、 Take advantage of the defects in the service or transport protocol provided by the victim host , Repeatedly send specific service requests at high speed , So that the victim host cannot process all normal requests in time
5、 If it is serious, it will cause system crash
边栏推荐
- Sqlserver regularly backup database and regularly kill database deadlock solution
- Do you really understand the things about "prototype"? [part I]
- 【全网首发】(大表小技巧)有时候 2 小时的 SQL 操作,可能只要 1 分钟
- 第五届 Polkadot Hackathon 创业大赛全程回顾,获胜项目揭秘!
- 【DNS】“Can‘t resolve host“ as non-root user, but works fine as root
- 力扣(LeetCode)185. 部门工资前三高的所有员工(2022.07.04)
- Crawler (9) - scrape framework (1) | scrape asynchronous web crawler framework
- 数据类型 ntext 和 varchar 在not equal to 运算符中不兼容 -九五小庞
- Web Security
- 【广告系统】增量训练 & 特征准入/特征淘汰
猜你喜欢
Go language-1-development environment configuration
磨砺·聚变|知道创宇移动端官网焕新上线,开启数字安全之旅!

About the use of Vray 5.2 (self research notes)
DDR4的特性与电气参数

2022 Pengcheng cup Web

如何让全彩LED显示屏更加节能环保
32: Chapter 3: development of pass service: 15: Browser storage media, introduction; (cookie,Session Storage,Local Storage)

基于昇腾AI丨以萨技术推出视频图像全目标结构化解决方案,达到业界领先水平
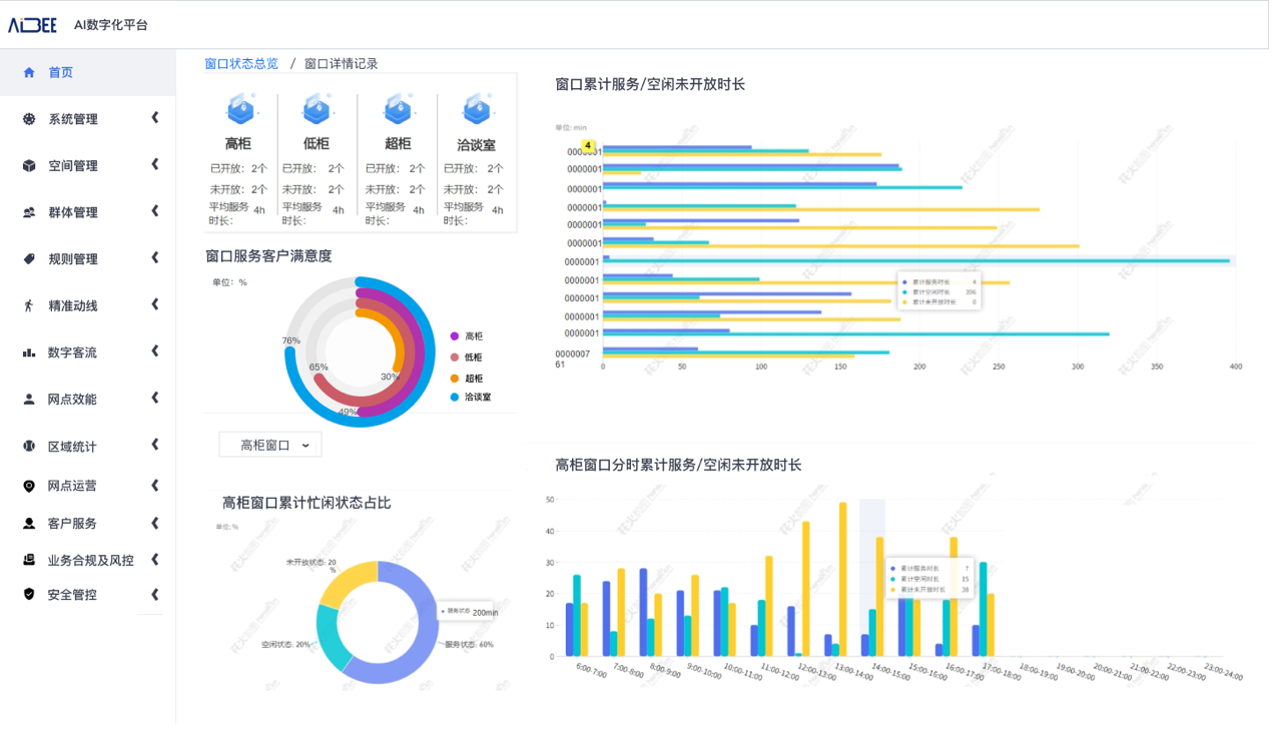
Based on shengteng AI Aibi intelligence, we launched a digital solution for bank outlets to achieve full digital coverage of information from headquarters to outlets
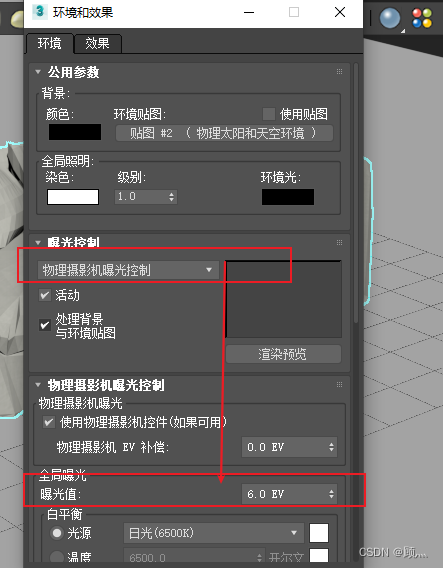
关于vray 5.2的使用(自研笔记)
随机推荐
Bidirectional RNN and stacked bidirectional RNN
关于vray 5.2的使用(自研笔记)(二)
Implement the rising edge in C #, and simulate the PLC environment to verify the difference between if statement using the rising edge and not using the rising edge
Nuxt//
Wechat nucleic acid detection appointment applet system graduation design completion (8) graduation design thesis template
Lazy loading scheme of pictures
Buried point 111
In the last process before the use of the risk control model, 80% of children's shoes are trampled here
LSTM applied to MNIST dataset classification (compared with CNN)
Talk about the understanding of fault tolerance mechanism and state consistency in Flink framework
Go-3-第一个Go程序
When using gbase 8C database, an error is reported: 80000502, cluster:%s is busy. What's going on?
iframe
Advanced scaffold development
Web3基金会「Grant计划」赋能开发者,盘点四大成功项目
关于 “原型” 的那些事你真的理解了吗?【上篇】
上拉加载原理
SQL Server monitoring statistics blocking script information
基础篇——REST风格开发
Basic testing process of CSDN Software Testing Introduction