当前位置:网站首页>Registration opportunity of autowiredannotationbeanpostprocessor in XML development mode
Registration opportunity of autowiredannotationbeanpostprocessor in XML development mode
2022-07-02 19:31:00 【Light dust ×】
AutowiredAnnotationBeanPostProcessor It's the realization of @Autowired The key to , When was it added to sping In container ?
xml The way
In the use of xml In the process of mode development , Our program entry is generally ClassPathXmlApplicationContext
@Test
public void test() throws Exception{
ClassPathXmlApplicationContext applicationContext = new ClassPathXmlApplicationContext("spring-test.xml");
Student student = (Student)applicationContext.getBean("student");
System.out.println(student.getUsername()+" "+student.getPassword());
}establish ClassPathXmlApplicationContext when , Would call this Constructors

Call the parent constructor in the constructor , Finish loading some properties , And the resolution of the configuration file path , Then get to the point ——refresh()
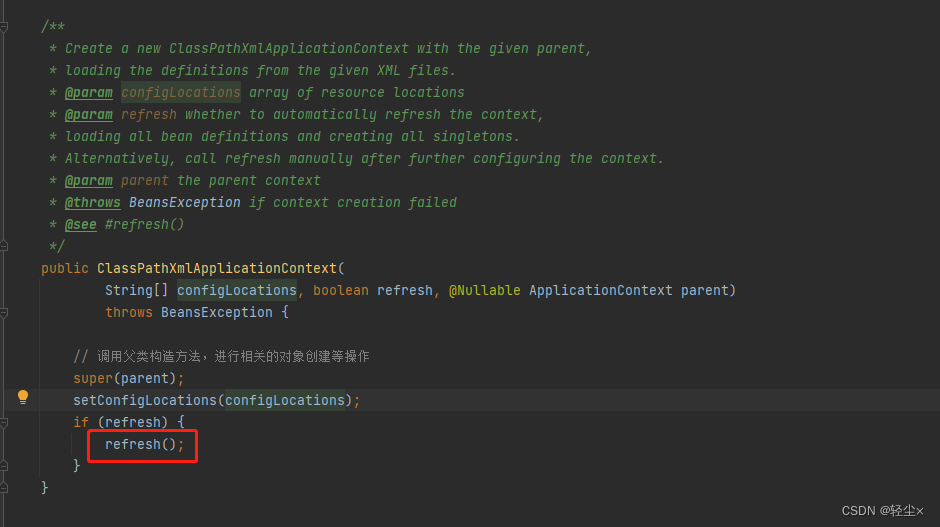
At the core refresh() In the method , One step is to create BeanFactory

establish BeanFactory after , It incidentally brings our xml The configuration file is also parsed

establish BeanFactory, then loadBeanDefinitions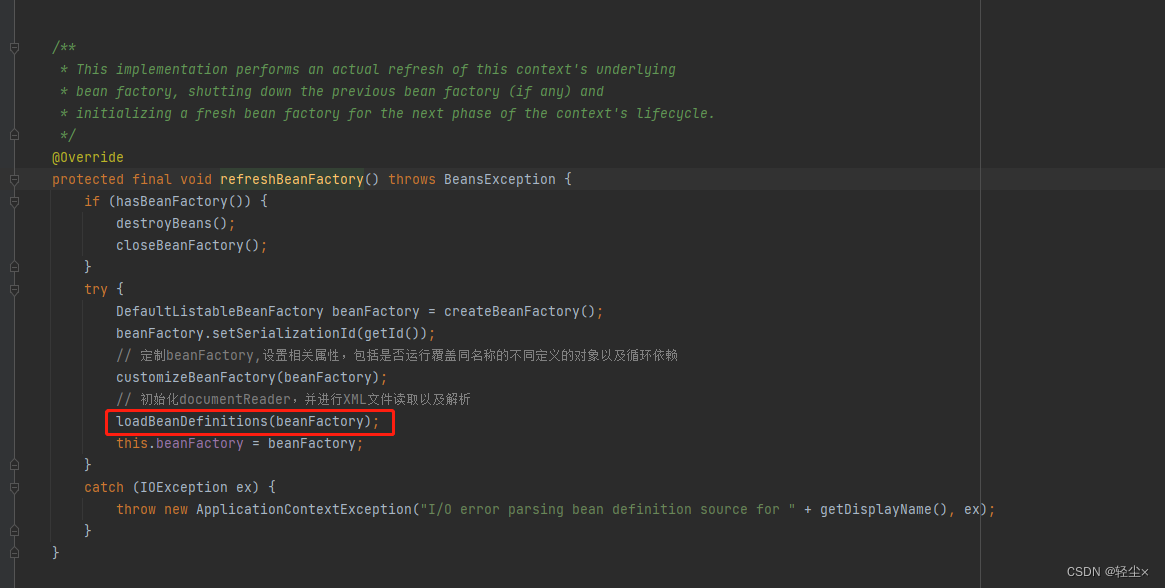
loadBeanDefinitions The process is complicated , Those who are interested can go line by line degbug Source code , Here are a few key steps

Several of the same name loadBeanDefinitions Tune in and out , It's best to transfer to a real worker doLoadBeanDefinitions

loadBeanDefinitions Not the focus of attention this time ,doLoadBeanDefinitions There is no need to delve into the details of , What's important is that doLoadBeanDefinitions After completion , I just got one Document Get object , It's not what we want bean Defining information , namely BeanDefinition, So we went on a call registerBeanDefinitions Steps for

In this registerBeanDefinitions In the process of , Nine twists and eighteen turns

Also tone do The first method is to do real work 
Start parsing the previous Document 了

There are two types of parsed tags , One is DefaultElement, One is CustomElement
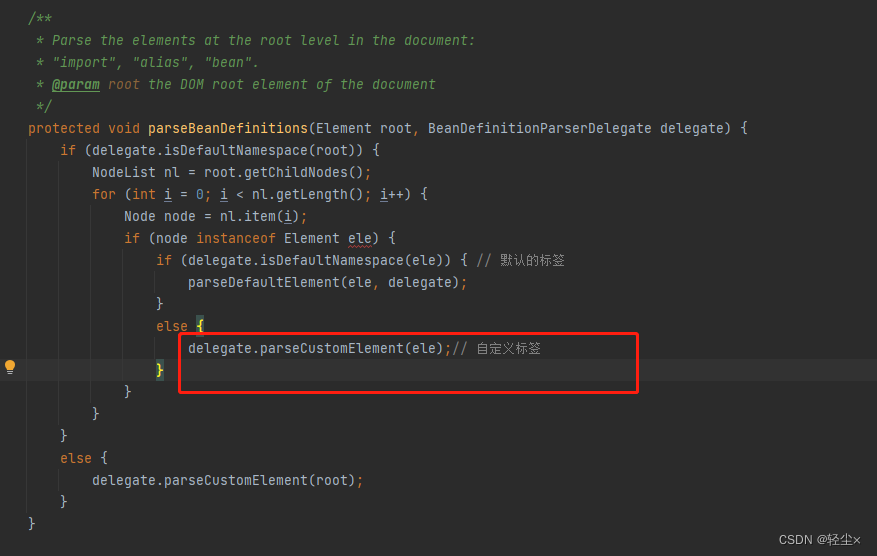
A digression , What is? DefaultElement, These four are , Namely import、alias、bean、beans, let me put it another way , Except for these four , Everything else is CustomElement

In my test environment , The first label is context, Nature is walking parseCustomElement
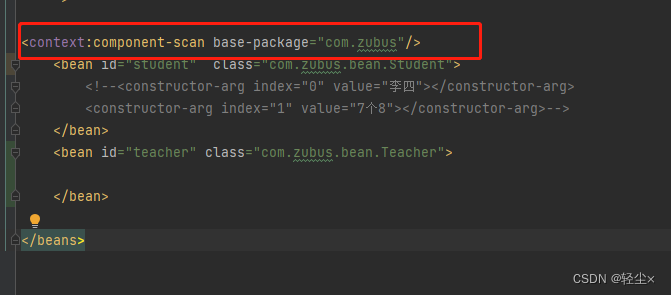
Then continue to analyze

Transfer to NamespaceHandlerSupport Of parse Method
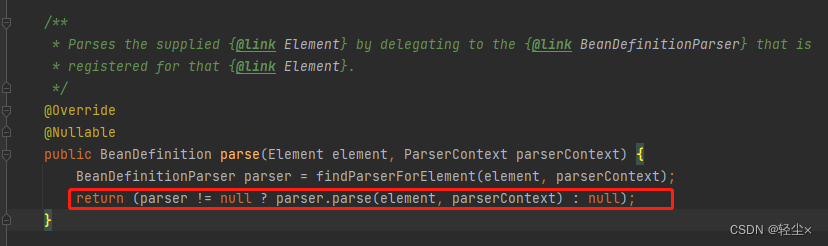
Further down is ComponentScanBeanDefinitionParser Of parse Method , It's finally over , The tag is parsed and encapsulated into BeanDefinitionHolder, Then there is another action registerComponents

It's this humble little action ,registerComponents, It contains mystery

In this, a AnnotationConfigUtils.registerAnnotationConfigProcessors, It's done here AutowiredAnnotationBeanPostProcessor Registration of
To make a long story short , In short , After creating the container ,loadBeanDefinitions Registered at .
Annotation mode
The same whole test method , This time new Yes. AnnotationConfigApplicationContext Not the one above ClassPathXmlApplicationContext
@Test
public void test() {
AnnotationConfigApplicationContext ac = new AnnotationConfigApplicationContext("com.zubus.bean");
BeforeInstantiation bean = ac.getBean(BeforeInstantiation.class);
bean.doSomeThing();
}It's a different route , Into the this()

It will new One AnnotatedBeanDefinitionReader

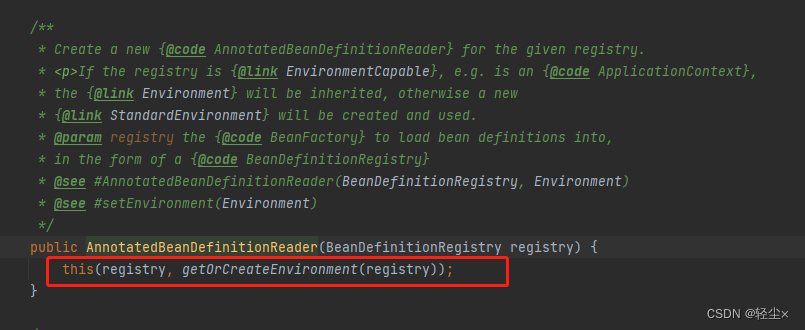
new AnnotatedBeanDefinitionReader() There is a familiar figure in the process of
AnnotationConfigUtils.registerAnnotationConfigProcessors(this.registry);
Is it with the above xml The resolved registerComponents It's as like as two peas

you 're right , It's right here
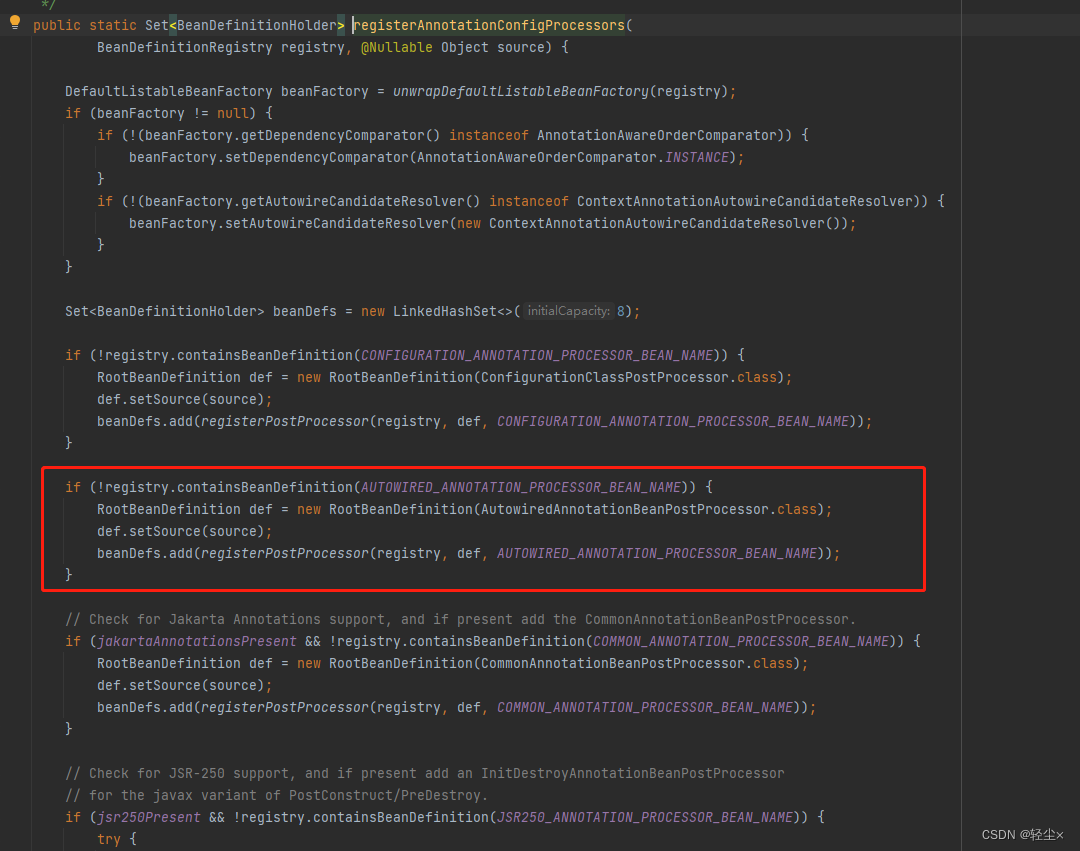
thus , Under two development modes AutowiredAnnotationBeanPostProcessor We have mastered the registration time
This is just registration , The next step is to analyze where it was not created as an object
The next step is to analyze where it is called and executed
Please look at the next breakdown ~
边栏推荐
- End to end object detection with transformers (Detr) paper reading and understanding
- IDEA编辑器去掉sql语句背景颜色SQL语句警告No data sources are configured to run this SQL...和SQL Dialect is Not Config
- 《架构整洁之道》读书笔记(下)
- Yolov3 trains its own data set to generate train txt
- The mybatieshelperpro tool can be generated to the corresponding project folder if necessary
- IEDA refactor的用法
- Emmet basic syntax
- 搭建哨兵模式reids、redis从节点脱离哨兵集群
- Juypter notebook modify the default open folder and default browser
- Codeworks 5 questions per day (1700 average) - day 4
猜你喜欢

Markdown basic grammar
Yolov3 trains its own data set to generate train txt
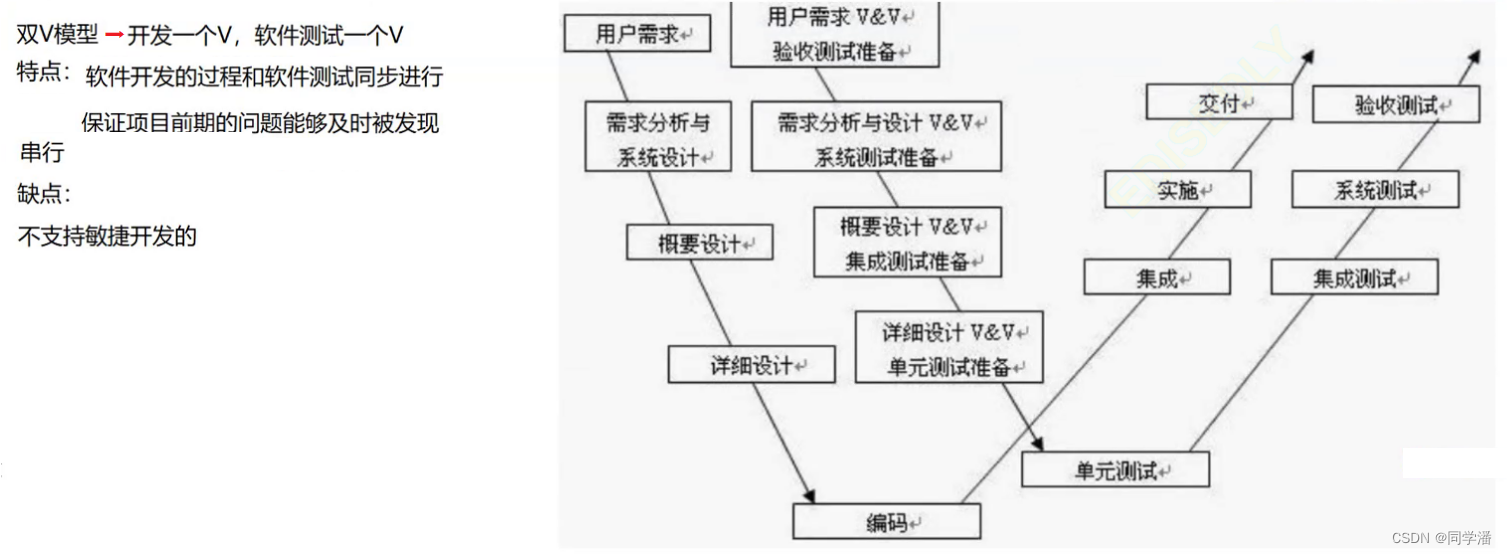
【测试开发】软件测试—概念篇
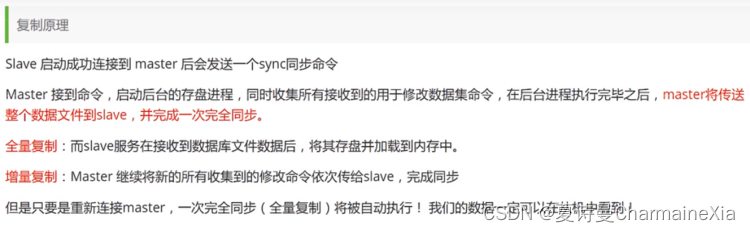
搭建主从模式集群redis

守望先锋世界观架构 ——(一款好的游戏是怎么来的)

Yunna | why use the fixed asset management system and how to enable it

线程应用实例

PHP parser badminton reservation applet development requires online system

PHP-Parser羽毛球预约小程序开发require线上系统
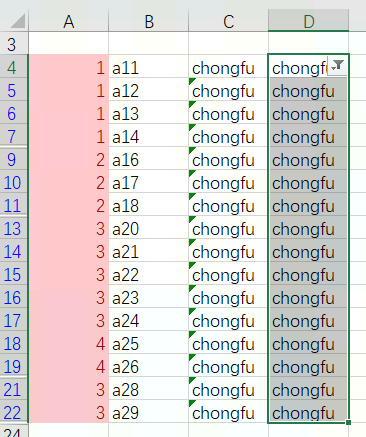
Excel finds the same value in a column, deletes the row or replaces it with a blank value
随机推荐
Date tool class (updated from time to time)
Watchful pioneer world outlook Architecture - (how does a good game come from)
Getting started with typescript
思考变量引起的巨大变化
Quanzhi A33 uses mainline u-boot
mysql备份后缀是什么_mysql备份还原
[error record] problems related to the installation of the shuttle environment (follow-up error handling after executing the shuttle doctor command)
Use cheat engine to modify money, life and stars in Kingdom rush
Emmet basic syntax
GMapping代码解析[通俗易懂]
codeforces每日5题(均1700)-第四天
《代码整洁之道》读书笔记
A4988驱动步进电机「建议收藏」
Obligatoire pour les débutants, cliquez sur deux boutons pour passer à un contenu différent
ICDE 2023|TKDE Poster Session(CFP)
以太网PHY层芯片LAN8720A简介
MySQL
AcWing 1137. 选择最佳线路 题解(最短路)
golang:[]byte转string
IDEA编辑器去掉sql语句背景颜色SQL语句警告No data sources are configured to run this SQL...和SQL Dialect is Not Config
