当前位置:网站首页>How to verify accesstoken in oauth2 protocol
How to verify accesstoken in oauth2 protocol
2022-07-07 03:00:00 【Misty jam】
Hello everyone , I am ethereal . Let's talk today oauth2.0 Of accesstoken Check logic .
summary
This article is from golfers Never Sett* The question of
Finish this problem , I feel that readers are interested in accesstoken The verification logic of is not clear , So I specially wrote this article to explain .

First we need to know Oauth2 It's a licensing agreement , Before the client accesses a protected resource , You need to get through the authentication server first accesstoken, Then by putting accesstoken Access resource server .
secondly ,Oauth2 There are two kinds of tokens issued by the authentication server : Opaque token (opaque tokens) and Transparent token (not opaque tokens) To put it bluntly, it is uuid and jwt The difference between .
Okay , Now comes the question , On the client side accesstoken Access resource server , How does the resource server know about you accesstoken It's legal ?
When you get the token is uuid when , The resource server cannot judge the validity of your token by itself .
At this time, there are generally two kinds of verification logic :
Remote verification
The authorization server exposes an endpoint , For valid tokens , It returns the permissions previously granted by the user who issued the token , This port is called check_token Endpoint ( In many places, it is also called token introspection endpoint ). We can Directly use the default interface provided by the authentication server /oauth/check_toen You can also customize an interface .
The resource server calls for each request check_token Endpoint , such , It will validate the token received from the client , And get the permission granted to the client . The resource server can be accessed through yaml Middle configuration security.oauth2.resource.user-info-uri Specify the authentication server check_token Endpoint address .
Blackboard mode
Resource servers and authorization servers use shared storage , Common ones are database and redis.
Authorization server generates accesstoken Then it will be persisted and stored , In this way, the resource server can also verify by accessing this shared storage accesstoken The effectiveness of the .
JWT
If the authentication server issues you jwt, At this time, the client will bring jwt Access resource server , The resource server can resolve the token directly , No need to call the authentication server . But you need to pay attention to the use of jwt Be sure to configure the key , Asymmetric keys are recommended for production environments .
Summary
oauth2 in accesstoken The verification logic is basically the above three
Call the authorization server directly
Use shared database ( Blackboard mode )
Use it directly JWT, Resource server self verification
Now in actual development, it is used in most cases jwt, This can reduce the interactive requests between the resource server and the authentication server , Improve access efficiency .
Of course , If you are right about oauth2 The agreement is not well understood , I recommend you to watch a short video I recorded before , It has a detailed description of .
边栏推荐
- Redis Getting started tutoriel complet: positionnement et optimisation des problèmes
- 哈希表及完整注释
- Huitong programming introductory course - 2A breakthrough
- PSINS中19维组合导航模块sinsgps详解(初始赋值部分)
- Convert widerperson dataset to Yolo format
- S120驱动器基本调试步骤总结
- [secretly kill little partner pytorch20 days] - [Day1] - [example of structured data modeling process]
- 普通测试年薪15w,测试开发年薪30w+,二者差距在哪?
- MySQL
- Cglib agent in agent mode
猜你喜欢
牛客编程题--必刷101之双指针篇

Niuke programming problem -- double pointer of 101 must be brushed
密码学系列之:在线证书状态协议OCSP详解
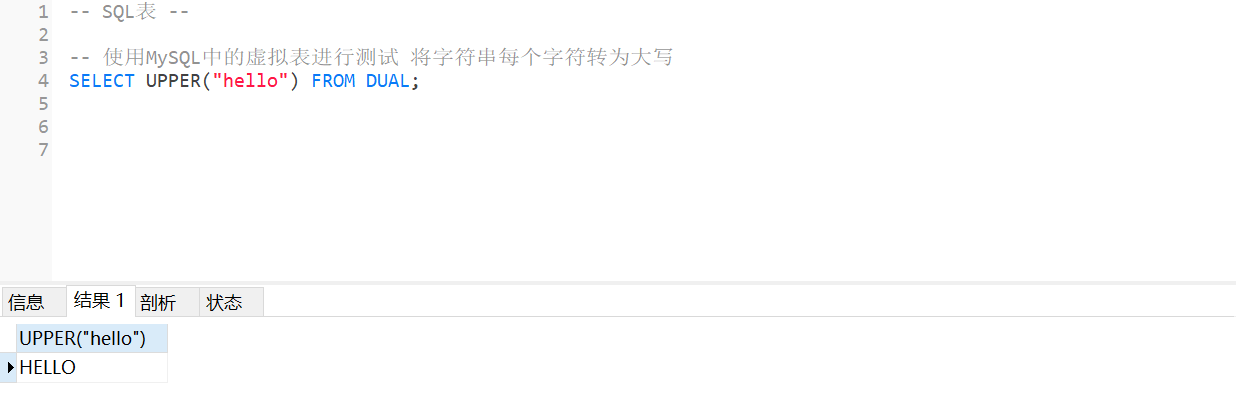
MySQL - common functions - string functions
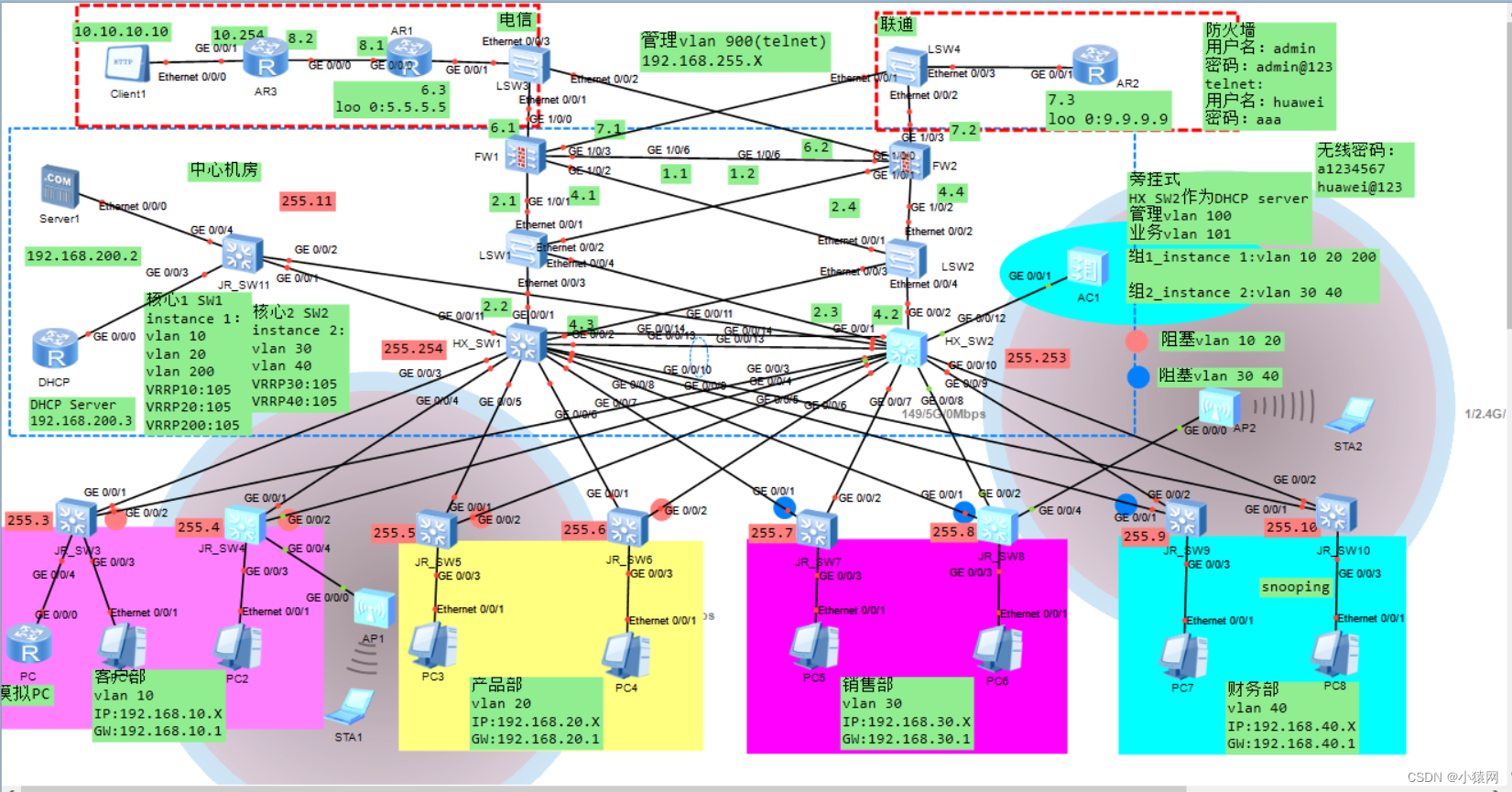
Planning and design of double click hot standby layer 2 network based on ENSP firewall
Install redis from zero

从零安装Redis
商城商品的知识图谱构建
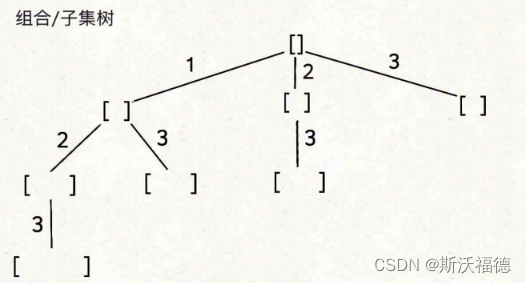
Leetcode 77: combination

换个姿势做运维!GOPS 2022 · 深圳站精彩内容抢先看!
随机推荐
Form validation of uniapp
How-PIL-to-Tensor
Code debugging core step memory
写作系列之contribution
The panel floating with the mouse in unity can adapt to the size of text content
简单冒泡排序
KYSL 海康摄像头 8247 h9 isapi测试
How to write test cases for test coupons?
Redis introduction complete tutorial: client case analysis
Es6中Promise的使用
fasterxml ToStringSerializerBase报错
What management points should be paid attention to when implementing MES management system
Left value, right value
How to find file accessed / created just feed minutes ago
Unity custom webgl packaging template
Redis入门完整教程:问题定位与优化
Es6中Promise的使用
Redis introduction complete tutorial: replication principle
MySQL --- 常用函数 - 字符串函数
测试优惠券要怎么写测试用例?