当前位置:网站首页>CSRF, XSS science popularization and defense
CSRF, XSS science popularization and defense
2022-07-05 15:21:00 【Shepherd Wolf】
CSRF (Cross Site Request Forgery) Cross-site request forgery
CSRF The attack just borrowed Cookie, Can't get Cookie Information in , So we can't get Cookie Medium token, You can't send a request in POST perhaps GET Set in token, When sending a request to the server ,token Verification failed , Then the request will not be processed .
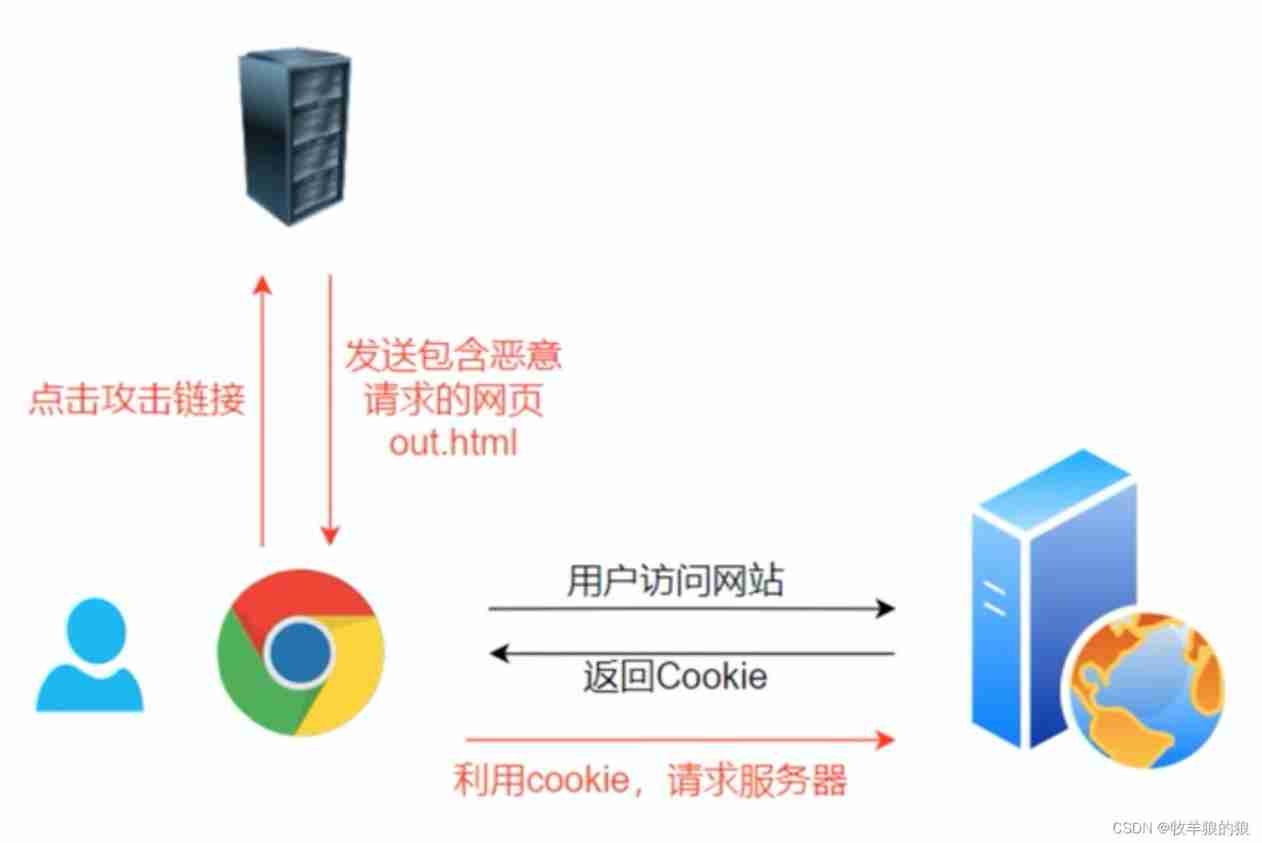
Case presentation :
The user login http://127.0.0.1:9000 Website , Enter the user name and password to log in to a website , The server records the login of the user cookie Save to browser , At this time, the login status of the user is logged in 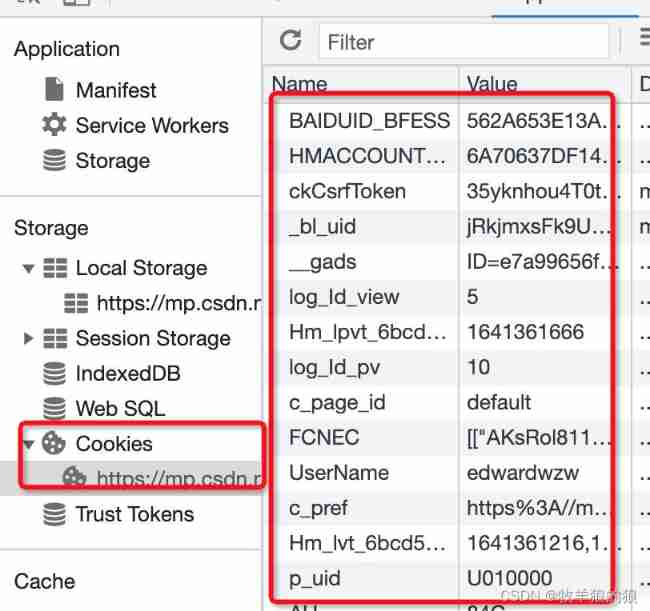
Since then, each interface request under the website domain name will carry cookie( After receiving the request, the interface considers that the user has logged in )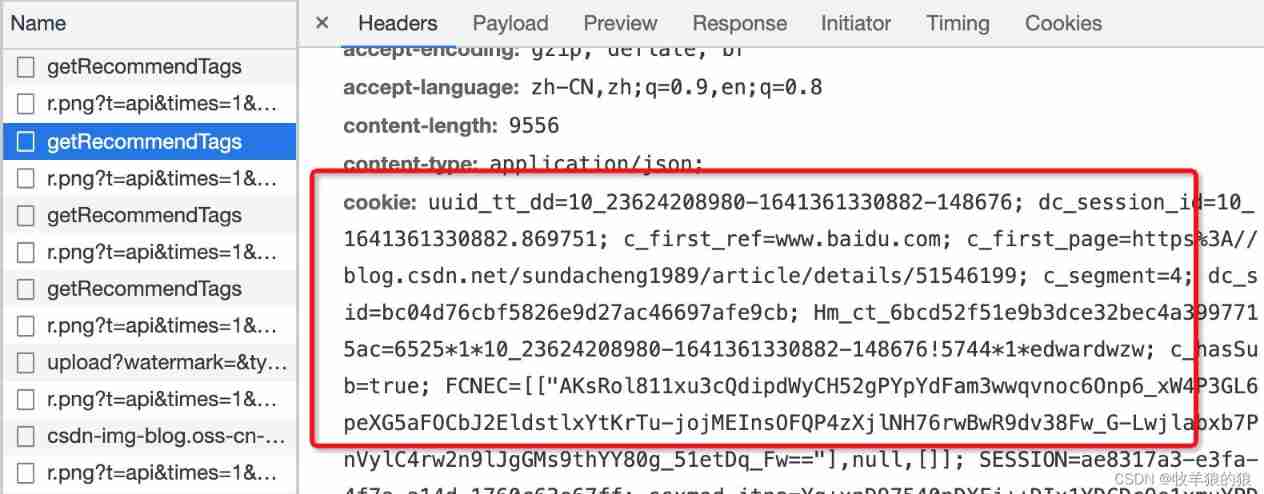
At this time, the user calls the interface to realize transfer :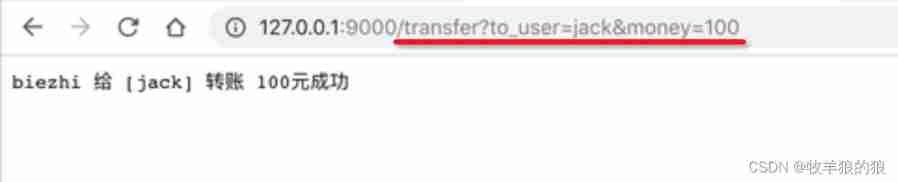
After the user completes the transfer , Did not log out in time (cookie There is still user login status in ),
At this time, a phishing website induces users to visit : The phishing website has a picture ( Wisely , Width and height are 0, At this time, the user can't see at all ), The image src The path is the transfer interface address ,
When the phishing website is loaded , It is equivalent to calling the transfer interface :( Because the domain name cookie For logged in , I brought this... With me when I asked cookie To the server , Transfer interface call succeeded !)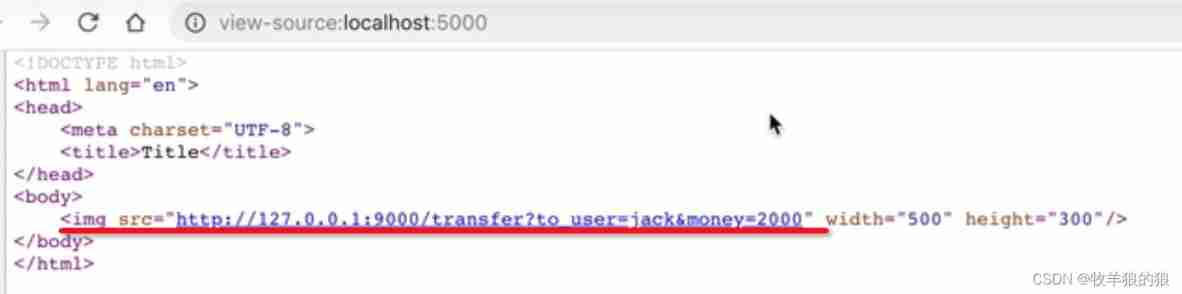
If it is POST Submit Form , You can do this :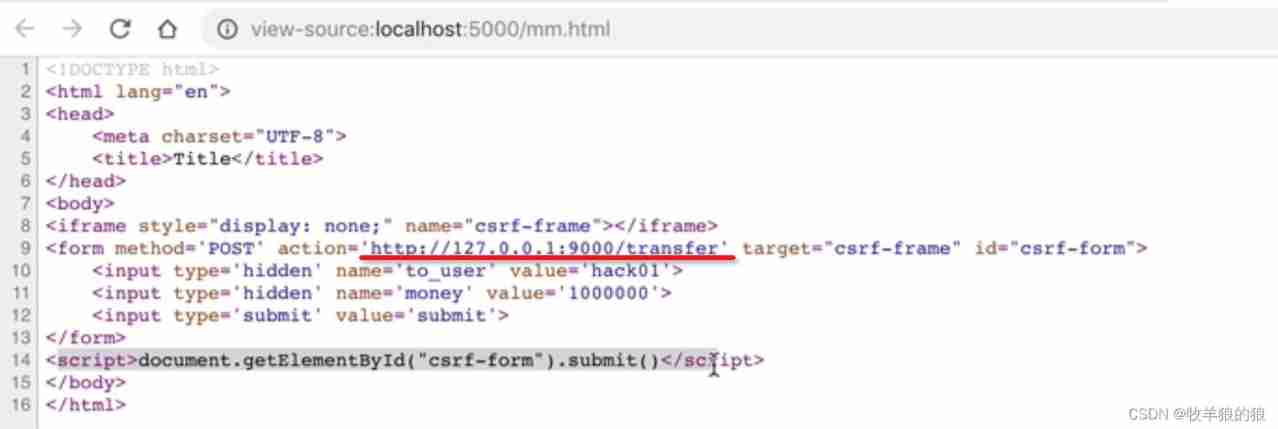
User identification is the use of cookie, Then the way to pretend to be a user is to visit other pages under a domain name , The browser will carry cookie This feature .
Defensive thinking :
1. Distinguish whether the request comes from your front-end page or a third-party website
2. Make your front-end page request different from the third-party forged request
Solution :
Use as much as possible POST, Limit GET
GET Interfaces are too easy to make CSRF attack , Just look at the example above , Just construct a img label , and img Tags are unfilterable data . Interfaces are best limited to POST Use , GET It doesn't work , Reduce the risk of attack .
Of course POST It's not foolproof , The attacker just constructs a form Can , But it needs to be done on the third party page , This increases the likelihood of exposure .
take cookie Set to HttpOnly
CRSF The attacks are largely browser based cookie, In order to prevent XSS Loopholes steal cookie, Need to be in cookie Set in “HttpOnly” attribute , So go through the process ( Such as JavaScript Script 、 Applet etc. ) Can't read it cookie Information , Avoid forgery by attackers cookie The situation of .
stay Java Of Servlet Of API Set in cookie by HttpOnly The code for :response.setHeader("Set-Cookie","cookiename=cookievalue;HttpOnly");
increase Token
CSRF The attack was successful , It's because an attacker can fake a user's request , All user authentication information in the request exists in cookie in , So the attacker can directly use the user's cookie To pass security verification . Thus we can see that , To resist CSRF The key to the attack is : Put information in the request that the attacker can't forge , And the letter never existed in cookie In . In view of this , The system developer can be in HTTP Was added a request in the form of randomly generated parameter token, And on the server token check , If not in the request token perhaps token The content is not correct , Think it is CSRF Attack and reject the request .
adopt Referer distinguish
according to HTTP agreement , stay HTTP There is a field in the header called Referer, It records the time to HTTP The source address of the request . In general , All requests to access a restricted page come from the same website . For example, the transfer of a bank is through user access http://www.xxx.com/transfer.do Page completed , Users must log in first www.xxx.com, Then click the submit button on the page to trigger the transfer event . When a user submits a request , Of the transfer request Referer The value would be The page where the submit button is located URL.
If the attacker wants to execute on the bank website CSRF attack , He can only construct requests on other websites , When a user sends a request to the bank through another website , The requested Referer The value of is the address of other websites , Not the address of the bank transfer page . therefore , Be defensive CSRF attack , The bank website only needs to verify each transfer request Referer value , If so www.xx.om Address at the beginning of the domain name , It means that the request is from the bank's website , It's legal. ; If Referer It's another website , It could be CSRF attack , Then reject the request .
XSS (Cross-Site Scripting) Cross-site scripting attacks
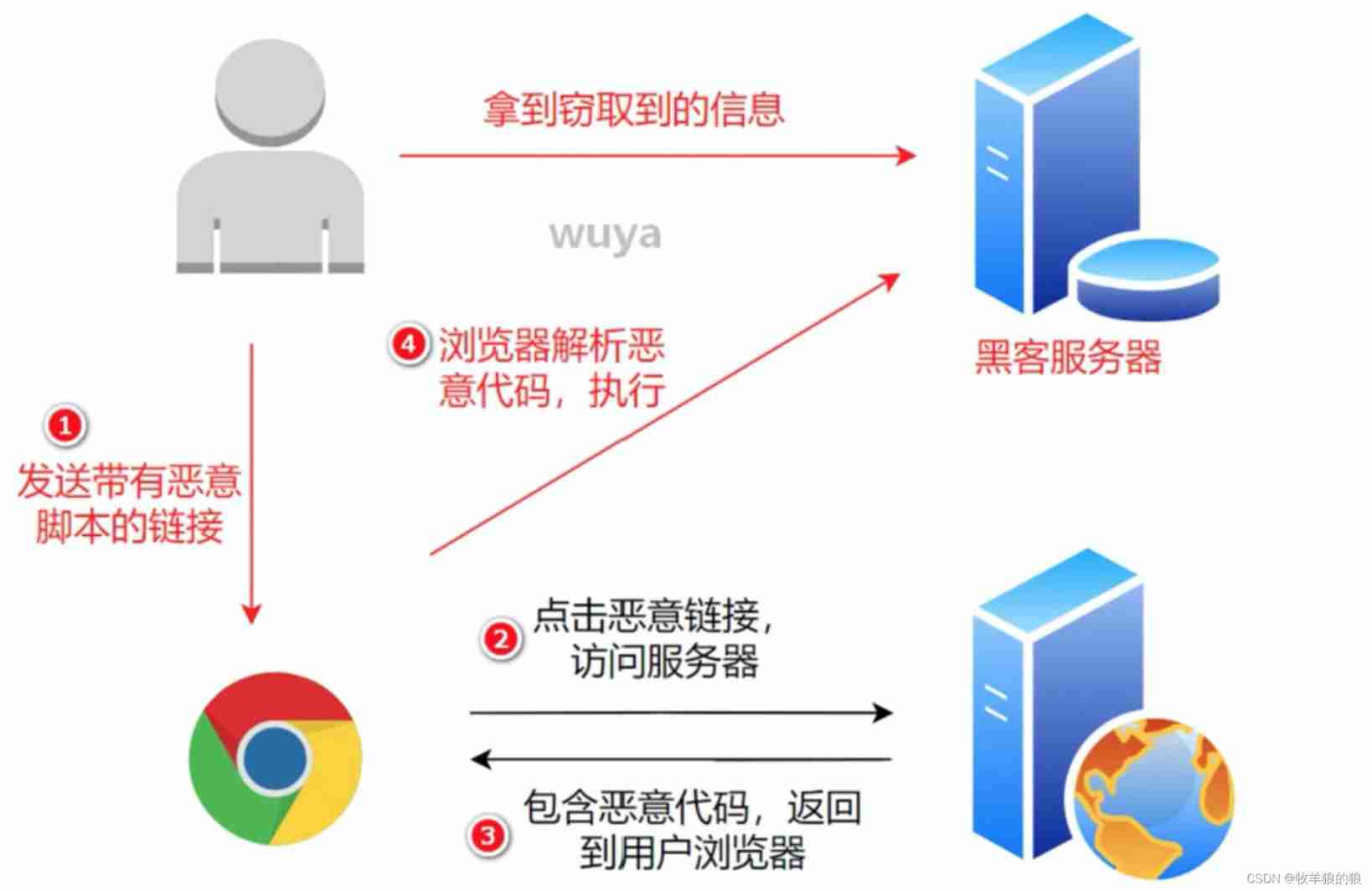
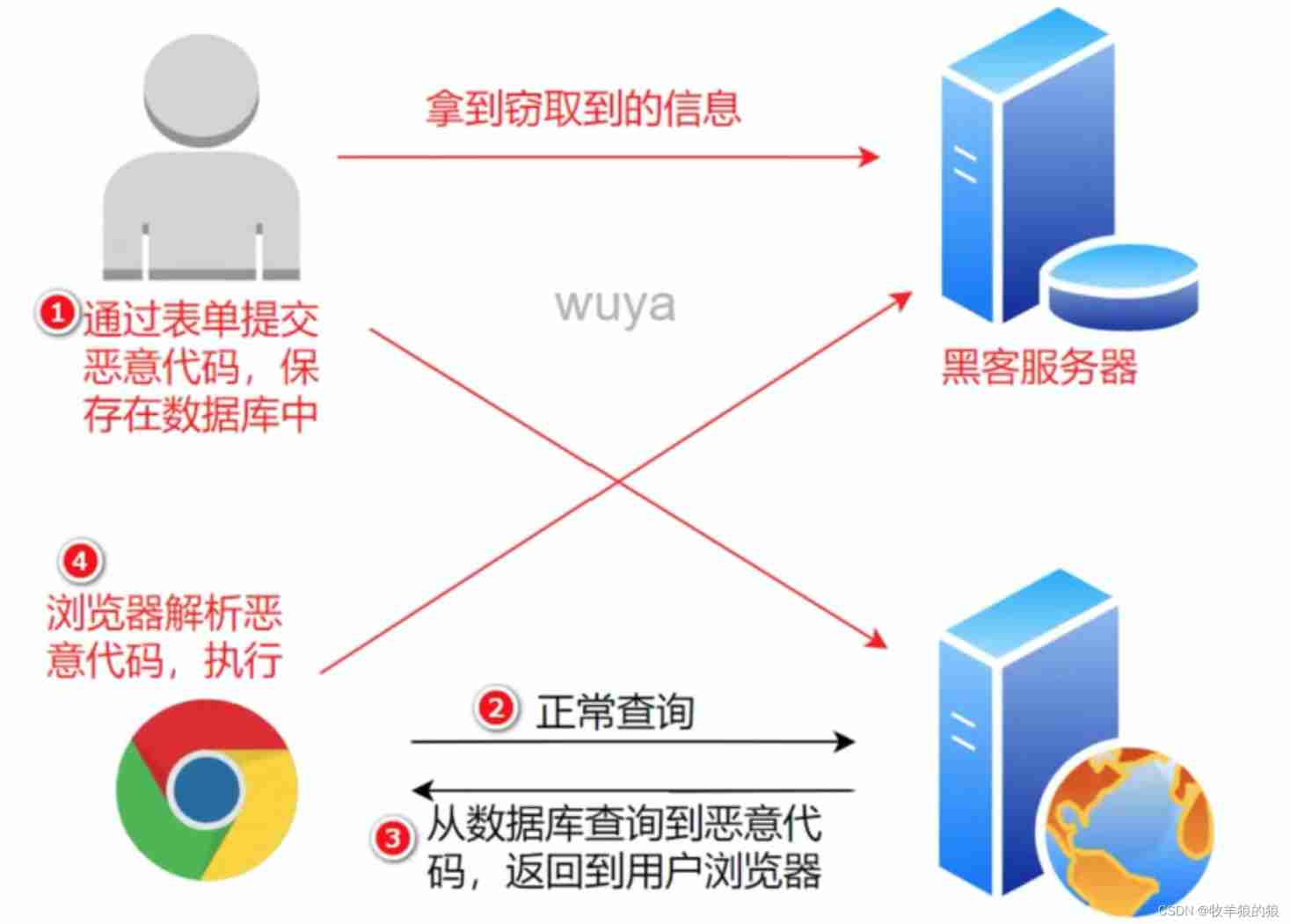
utilize xss, Hackers can forge user login , So as to pretend to be a user 、 Brush Click 、 Play the advertisement 、 Spread worms and so on . According to the type, it can be divided into reflection type and storage type .
reflective XSS:
Storage type XSS:
Case presentation :
The user enters information in the browser :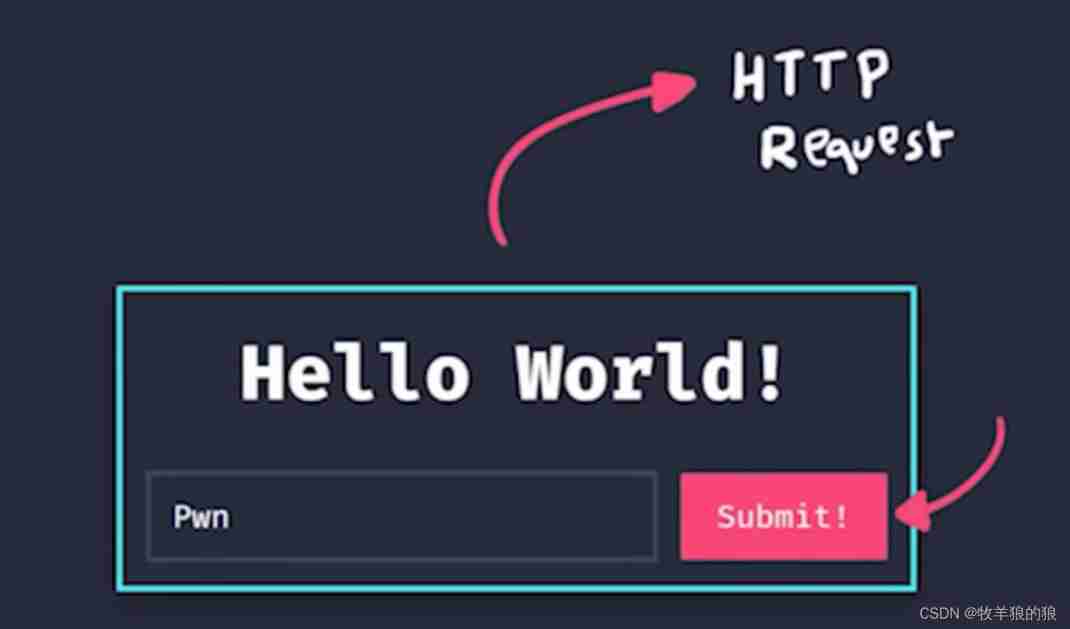
Server side html Form returns part of the input :
If injected script label :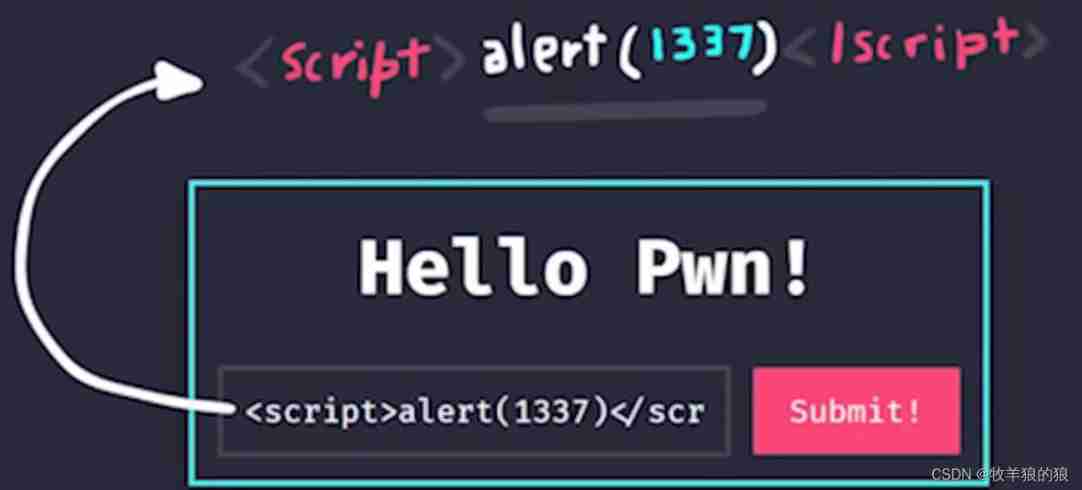
After successful submission , The server still returns script label , This constitutes XSS attack :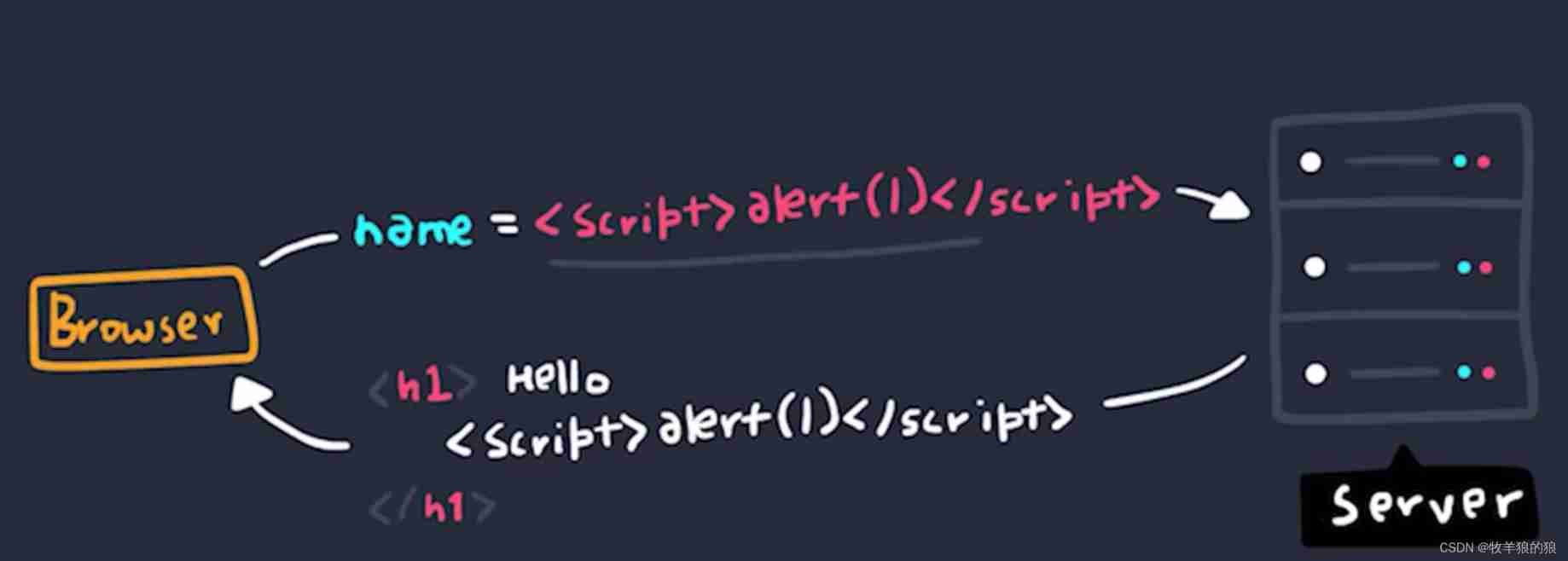
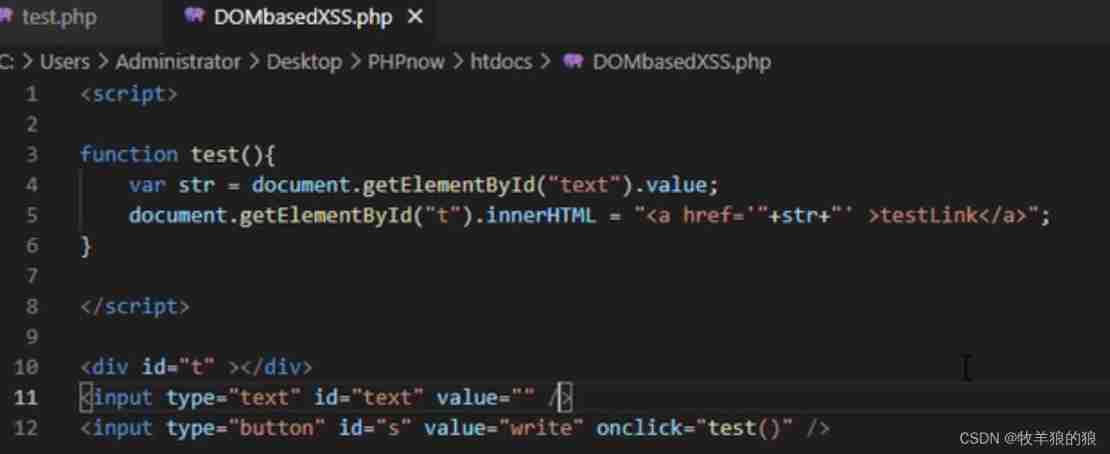
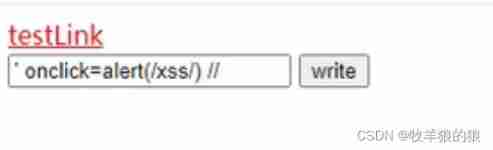

Solution :
1. WAF Rule library code (Web Application Firewall , Web Application firewall , To guard against SQL Inject ,XSS etc. )
边栏推荐
- I want to inquire about how to ensure data consistency when a MySQL transaction updates multiple tables?
- Cartoon: programmers don't repair computers!
- Install PHP extension spoole
- Your childhood happiness was contracted by it
- Photoshop插件-动作相关概念-非加载执行动作文件中动作-PS插件开发
- CPU design practice - Chapter 4 practice task 3 use pre delivery technology to solve conflicts caused by related issues
- GPS原始坐标转百度地图坐标(纯C代码)
- Ctfshow web entry information collection
- 我想咨询一下,mysql一个事务对于多张表的更新,怎么保证数据一致性的?
- Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
猜你喜欢

Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
12 MySQL interview questions that you must chew through to enter Alibaba
![[12 classic written questions of array and advanced pointer] these questions meet all your illusions about array and pointer, come on!](/img/d2/c0a19c85b2011ecd07c9944d996c4d.png)
[12 classic written questions of array and advanced pointer] these questions meet all your illusions about array and pointer, come on!
Select sort and bubble sort
Talk about your understanding of microservices (PHP interview theory question)

Bugku's steganography

市值蒸发超百亿美元,“全球IoT云平台第一股”赴港求生
I include of spring and Autumn
MySQL----函数
计算中间件 Apache Linkis参数解读
随机推荐
Garbage collection mechanism of PHP (theoretical questions of PHP interview)
JS bright blind your eyes date selector
做研究无人咨询、与学生不交心,UNC助理教授两年教职挣扎史
Ecotone technology has passed ISO27001 and iso21434 safety management system certification
可转债打新在哪里操作开户是更安全可靠的呢
What are the domestic formal futures company platforms in 2022? How about founder metaphase? Is it safe and reliable?
1330: [example 8.3] minimum steps
MongDB学习笔记
P1451 calculate the number of cells / 1329: [example 8.2] cells
How can I quickly check whether there is an error after FreeSurfer runs Recon all—— Core command tail redirection
Fr exercise topic - simple question
P6183 [USACO10MAR] The Rock Game S
How can the boss choose programmers to help me with development?
Can gbase 8A view the location of SQL statement history?
Dark horse programmer - software testing -10 stage 2-linux and database -44-57 why learn database, description of database classification relational database, description of Navicat operation data, de
Selection and use of bceloss, crossentropyloss, sigmoid, etc. in pytorch classification
mapper. Comments in XML files
ionic cordova项目修改插件
漫画:优秀的程序员具备哪些属性?
Visual task scheduling & drag and drop | scalph data integration based on Apache seatunnel