当前位置:网站首页>Reading notes on how to connect the network - hubs, routers and routers (III)
Reading notes on how to connect the network - hubs, routers and routers (III)
2022-07-04 08:59:00 【Adong】
Key points of this chapter
- How signals are transmitted over network cables and hubs ? How to suppress distortion in signal transmission ?
- What is the function and working mode of the switch ?
- Router packet forwarding details , And the difference with the switch .
- Additional router functions , It's not just a medium to access the Internet , There are also many other functions .
- Understanding hubs 、 Router 、 The switch is in OSI Model (TCP/IP Model ) The location of .
Hub and network cable signal transmission
If you understand [[《 How the network is connected 》 Reading notes - ADSL]] and [[《 How the network is connected 》 Reading notes - FTTH]] The content of two parts , It should be clear that network packets are eventually transformed into electrical or optical signals during transmission , What we usually call TCP agreement 、IP agreement 、 Ethernet and so on have actually been “ shielding ” Of .
The final packet transmission is just a signal transmission from one forwarding device to another forwarding device , All network packets are transmitted as an independent express .
This transmission process involves the three most important contents of this chapter , That's the hub , Switch , Router , The whole transmission process is similar to the following :
Prevent signal attenuation
The so-called Ethernet signal can actually be regarded as a positive and negative voltage , NIC PHY The module is responsible for the output of the positive and negative electronic signal circuit .
The fundamental problem of signal transmission is that the longer the network cable , The more serious the signal attenuation and loss . Because Ethernet uses square wave signal transmission , High frequency signals are easily lost , This will easily lead to signal distortion , In addition, whether the line noise condition is good or bad, it may cause signal distortion , So the problem is obviously in the transport material .
The Internet was first used Twisted pair , The so-called twisted pair is the earliest ADSL It is a special design mode born of the mixed mode of telephone line and network line used to access the Internet .
And the earliest Ethernet used a dedicated coaxial cable , Later, it became American indoor electricity An improved version of the telephone line , The reason is that it can be compatible with the wiring tools and materials of telephone lines , It's more convenient .
How to avoid signal distortion and noise problems for twisted pair cables , We need to understand how noise comes from , Here we need to introduce some physical knowledge :
The signal noise comes from the electromagnetic wave around the network cable , There are mainly two kinds of electromagnetic waves that affect the transmission of network cable signals , The first is the electromagnetic wave leaked from the liquid crystal display device , The second is electromagnetic crosstalk caused by adjacent network cables , The signal transmission depends on the current , Electric current will generate electromagnetic wave around the network cable , Electromagnetic wave interference between network cables is called crosstalk .
To solve the problems of the above two kinds of electromagnetic waves , There are usually the following ways :
- The first way is to let the current be transmitted in a spiral way through different ways through twisted pair , The direction of the noise current generated in two of the signal lines will change contrary , At this time, the signal can still be transmitted normally , But the noise has been controlled .
- The second kind of electromagnetic crosstalk can be solved by winding , Because there is a very regular gap between the strands , The distance between positive and negative signals is offset by winding , Therefore, even if the neighboring parts are intertwined correctly, the noise can be cancelled .
Therefore, the spiral winding method of the network cable itself is exquisite , It can not only solve the noise caused by current passing other electromagnetic wave equipment , It can also prevent the electromagnetic wave noise generated by the cross current of different network cables .
Hub works
After the signal is transmitted to the whole network, it will be broadcast to the whole network , In the first chapter “ Ethernet MAC Head ” It introduces MAC The address contains the recipient's “ Shipping address ”, The hub is responsible for broadcasting signals in the Ethernet architecture . In fact, it can be imagined that it is receiving the electrical signal transmitted by the network card at one end , Then it is transferred to the other end through the network cable .
We can observe the hub design ,PHY The function of the module is basically the same , Note that the wiring method here is cross connected , It is impossible to receive signals by direct connection .
If the hub does not want to communicate with a network card, an intermediate medium is required to complete the switching action .
RJ45 Interface : Usually used for data transmission , The most common application is network card interface .RJ45 It is a type of various joints ;RJ45 There are two different ways to sort the head according to the lines , One is orange white 、 orange 、 Green and white 、 blue 、 Bluish white 、 green 、 Brown and white 、 Brown ; The other is green and white 、 green 、 Orange white 、 blue 、 Bluish white 、 orange 、 Brown and white 、 Brown ; Therefore use RJ45 There are also two types of connector wires, namely : Through line 、 Cross line .
To make different interfaces implement “ Access ” and “ close ” The operation of , Need to rely on MDI/MDI-X Toggle switch , If this switch exists, it can be switched MDI/MDI-X Pattern , The direct connection of the hub can be changed to MDI Pattern ( That is, the direct connection mode ).
But if you need to interact with the network cards of other computers , You need to switch to MDI-X Patterns interact , Also note that not all hubs have a toggle switch , So if a hub has only MDI-X Interface , You can also use the default MDI- X Interface completes cross interaction .
It may be a little difficult to understand , So to put it another way : We know that the current flows from the positive pole to the negative pole , Therefore, when the hub interacts with the network cards of the two computers, it is necessary to “ The sender ” and “ The receiver ” Positive and negative cross connect of .
The design of hub is “ Parallel equipment ”, It may only support positive and negative signal interaction or direct connection to complete the interaction , Therefore, the mode change-over switch is required for compatibility , But if the hub has only positive and negative signal interaction interfaces , Then the signal exchange is directly completed by means of cross interactive connection .
Now let's take a look at the other end to splice the received content into a complete structure diagram , As mentioned above, it is at this end of the network card .
Why are there direct and cross lines ?
The following sections are not covered in the book , I have some questions about why the hub should be broken MDI/MDI-X Direct connect and cross connect mode , Although I know his role , But I don't know the history .
To explain in detail , First, let's talk about what is a straight line , What is a crossline .
- Straight line : Both ends of the network cable are pressed T568A perhaps T568B Sort .
- Cross line : One end is pressed T568A Sort , One end is pressed T568B Sort .
Here, I found a diagram of the Internet to compare the different access modes of two different connection methods on the network cable :
The difference between direct connection and cross connection
In fact, there is no essential difference , It's just that different network cables adapt to different scenarios . See the screenshot above for specific usage scenarios , Here is a simple example .
Direct connection is used between two different devices :
- The host is connected to the hub or switch .
- Router switches and hubs .
- Switches use different ports .
The cross line uses the same type of equipment , Here, just remember that the crossover applies to the same type of equipment .
Here's a rule to remember : Crossover for the same equipment , Direct connection for different equipment .
However, with the development of technology and iteration, modern equipment does not rely on the network cable interface very much , The same kind of equipment is also compatible with direct connection , So the above rule can only be used as a reference .
Switch signal transmission
Switches usually belong to OSI The second layer of the model ( Data link layer ), The operation of the switch depends on MAC Identification of address .
Switch The design is to forward the network packet to the destination as it is , The purpose is to realize long-distance network packet transmission without data distortion .
Because you need to exchange data , The interface of exchange and PHY(MAU) The module is also based on MDI-X Mode , When the network packet enters the interface, it first translates the signal into the general format of the switch , Then use MAC The module part parses the network packet , And use the... At the end of the package FCS Check error .
Switches seem to work like network cards, but they actually have similar functions , By inquiring MAC Address and port to find the corresponding destination address , Then forward to the next address closer to the destination .
The port of the switch does not check the receiver MAC Address , Instead, all packets are received directly and stored in the buffer , As mentioned in the previous chapter, the network card itself will Bring your own one MAC Address And you need to check the information you send and receive MAC Address .
Obviously, there are still many differences between network cards and switches , because Switch port MAC Module does not have MAC Address .
The following is a more detailed explanation of the operation of the switch , The whole job is in short : Switch based on MAC Address table lookup MAC Address , Then send the signal to the corresponding port .:
When a switch receives a packet from one of its ports , First read the source in the header MAC Address ( That is, the network card of the device that sent the packet MAC Address ), Will be MAC The address and port are added to the address table in the switch memory ; Then read the destination in the header MAC Address , Check the address table in the memory MAC Which port does the address correspond to .
If there is this... In the address table MAC The corresponding port of the address , Copy the packet directly to the corresponding port , If it is not found, the data frame is sent to all ports as a broadcast frame , Corresponding MAC The address device will automatically receive the frame data , At the same time, the switch will connect the port that receives the frame data with this purpose MAC The address corresponds to , Finally, put it into the address table in memory .
Quickly understand the characteristics of the switch : Ethernet data transmission equipment with most network card characteristics .
Here is a review of the previous chapters FCS Content .
FCS: Check the waveform disorder caused by noise during packet transmission 、 Data error , It's a string 32 A sequence of bits , Is through a formula to the package from beginning to end All the contents of the . For details, please refer to the structure diagram of the network package .
Switch internal structure
MAC Address maintenance
The basic work of the switch is to find and check MAC Address and maintenance MAC The work of the address table ,MAC Address maintenance mainly includes the following two details :
- The sender MAC Write the address and the number of its input port MAC In the address table .MAC The data of the address table is very large, but the number of ports is limited , To quickly find and manage , As long as a device has sent network packets , its MAC The address will be recorded in the address table , This structure is similar to caching .
- MAC The address list is usually “ Real time updates ” Of , The purpose is to prevent device movement problems . Because modern mobile devices frequently switch network environment and port status , In order to adapt to the frequency of the sender, the switch “ change ” The port needs to delete the mapping record of the address table in time .
In addition, it should be added that it is the same as most cache features ,MAC Address deletion is not real-time , So sometimes packets may be sent to the previous , But this kind of thing usually does not need to worry and is relatively rare , Usually, the switch is restarted and flushed MAC Address and port mapping , The exchange opportunity updates or deletes the records in the address table by itself , No manual maintenance is required .
Switch special handling
Here are some special cases of switches .
The first is if the sender and destination addresses of network packets are the same mapping port , In this case, the target machine will receive two duplicate packets, resulting in no communication , So this network packet switch will discard it directly after receiving it .
In another case, the specified... Cannot be found in the address table MAC Address , This may be because the destination address has never interacted on the Internet , Or the device does not work for a long time, and the address is deleted by the switch .
In this case, the exchange will broadcast to all network devices until the responder is found , Once the reply is received, it will be stored MAC Address and mapping port , This design itself is also consistent with the original design considerations of Ethernet .
The last is if the receiver MAC The address is a Broadcast address , The switch then sends the packet to all ports except the source port .
Full duplex protocol
Full duplex protocol exists in switches , Hubs do not have this feature , The hub will cause signal collision due to multiple incoming signals. It is a half duplex protocol .
The switch is a full duplex protocol , Therefore, in the transmission process, whether there is a network packet switch or not, it can also send and receive data by itself . Signal collision does not occur in full duplex mode , Therefore, collision detection is not required in this mode .
The early emergence of full duplex protocol requires manual switching , Of course, with the development of technology, there was an automatic switching of working mode .
In addition, in the early stage, in order to ensure normal communication , If there is no signal transmission in the Ethernet architecture , By default, the filling pulse signal flows continuously in the network , In order to be compatible with the transmission rate of new and old equipment , Pulse signal transmission will use “ Barrel effect ” The short board of can automatically complete the pulse signal transmission of full duplex protocol .
Finally, the switch supports full duplex protocol , When the port does not need to transmit data, the forwarding operation of multiple ports can be realized , More information about switches can be found in the resources .
Router signal transmission
After the data is sent by the switch , The signal will be transmitted to the router .
The router is based on IP The design of the , The switch is designed based on Ethernet , Although it seems that the work is similar, look up the table to determine where the package should be sent , However, due to the different design intentions , So there is still a big difference .
The internal structure of the router focuses on Forwarding module and Port module , The forwarding module is responsible for determining the forwarding destination of the packet , The port module is responsible for sending and receiving packets , It is similar to the protocol stack IP Relationship between module and network card .
Routers support multiple protocols , As long as the port module is installed with relevant protocols, it can support signal transmission , Complete the work of different protocols through different ports , Each port of the router has one MAC Address and IP Address .
Ethernet port as an example , The router's port has MAC Address , So it can be the sender and receiver of Ethernet , In addition, the port also has IP Address , So it can be used as a network card .
Routing table information
The table information in the router is called the routing table , The basic idea of judging the forwarding target by looking up the table is similar to that of the switch , But it works in a different way .
The main differences can be compared from the design of the routing table , Here we need to use the knowledge of subnet mask again , First of all, you can see that the host number of the target address storage is 0, So the obvious storage here is the target IP Subnets of .
The router will ignore the host number , Only match the network number , As long as you receive IP The network number is consistent , It can be regarded as data transferred from the same direction .
In order to improve the address management efficiency of routing table in router , Sometimes the actual subnet mask and subnet mask of the target address do not exactly match , Here's an analogy DNS about IP Address maintenance .
The router maintains the destination address and subnet mask , The route aggregation will combine several sub nodes The net is merged into a subnet , And only one record is generated in the routing table , such as 10.10.1.0/24、10.10.2.0/24、10.10.3.0/24 These three addresses do not belong to the same subnet , But it can go through 10.10.0.0/16( Note that the network number changes to 16 position ) This form is similar to the secondary mask matching operation for the mask .
Therefore, the subnet mask column of the routing table only indicates the number of bits to be compared when matching the destination address of the network packet , Using route aggregation can reduce unnecessary table lookup and improve routing efficiency .
Finally, the maintenance of routing table information , The main methods are the following two :
- Route records are maintained manually by a human .
- According to the routing protocol mechanism , The information exchange between routers is maintained by the routers themselves Record the routing table .
Router packet sending and receiving operation
The signal is transmitted to the interface section , Interface PHY Module and MAC The module converts and translates the signal , The end also needs to be verified FCS.
Then check MAC Address , The ports of routers also have MAC Address , Accept only packets that match its address , Mismatched packages are discarded . The recipient MAC The address is the router port Of MAC Address .
It is easy to misunderstand that the address of the receiver may be regarded as the address of the host , It's actually Of the receiving port of the router MAC Address , Because network packets are sent to routers , Then the router looks up the table and sends it to the specific host .
Routing table lookup
The routing table lookup rule is to match according to the longest matching network number ratio , Because the more network numbers, the greater the range of the subnet mask, and the less hosts the subnet covers , The more likely it is to find the corresponding host address . Such a matching rule is also called The longest matching rule .
The server usually has a fixed public network IP Your device will have a routing table such as 192.168.1.10/255.255.255.255 Form of expression , In this way IP When searching, you can match according to the longest match rule .
Note that if a matching record cannot be found in the routing table , The router will discard the packet , And pass ICMP The message informs the sender . Why do you just throw away the packets ? This is because the number of Internet devices is too large , The query cost is hard to estimate .
Default routing
It is obviously unrealistic for all forwarding operations to match the routing table , Therefore, the router is configured by default 0.0.0.0 So that any address can be matched to , In addition, this line of configuration is also called The default gateway .
At the computer TCP/IP There is also a box to fill in the default gateway in the setting window , On the computer There is also a routing table similar to the router , The address of the default gateway is the address we filled in the setting window .
stay IPV4 in ,0.0.0.0 The address is used to indicate an invalid , Unknown or unavailable targets .
- In the server ,0.0.0.0 Indicates that it is all... On this computer IPV4 Address , If a host has two IP Address , such as 192.168.1.1 and 10.1.2.1, And a service listening address on the host is 0.0.0.0, Then through two ip All addresses have access to the service .
- In routing ,0.0.0.0 Represents the default route , That is, when the route table does not find a fully matched route, the corresponding route .
0.0.0.0 Main purpose of :
- DHCP Before allocation, it means local .
- Used as the default route to represent any host .
- Used as a server to represent any of the local IPV4 Address .
- Indicates that the target machine is not available
Routers and switches The difference
Finally, let's look at the difference between routers and switches
- Switch through MAC Header receiver MAC The address determines the forwarding target , The router goes through IP Module judgment IP Address to determine the forwarding destination .
- The switch is at the address Only exactly consistent records are matched in the table , The router ignores the host number part , Matches only the network part .
Validity of the package
Before the router sends the network packet , There is still some work to be done : to update IP The head of the TTL Field ,TTL It refers to the validity period of the package , If this value is zero 0 It means forward , For example, the sender will send a packet TTL Set to 64 or 128, That is to say, the package has gone through so many After the router “ die in one's bed ”. This mechanism is designed to prevent unlimited packet forwarding .
The fragmentation function splits large network packets
Here the pieces and TCP Splitting data is different ,TCP The operation of splitting data is to load the data into a package What happened before , In other words, a split data block is just put into a package . and IP Sharding is the operation of sharding a composite package again .
decision IP The main limitation of whether the module is partitioned is MTU Parameters and supported by the output port MTU size , If the output port is too small, the packet should be partitioned according to the limited size , If the query flag field finds that fragmentation is not possible , Then you can only discard this package , And pass ICMP The message informs the sender .
It should be noted that each piece of data will be preceded by IP Head , Adding headers is similar in most cases , It's just = Some of these fields need to be updated , These fields are used to record scores Film related information .
Router send operation
The router judges the next forwarding target as follows :
- If the gateway column of the routing table is IP Address , Then this address is the next forwarding destination .
- Router usage ARP To query the next forwarding target MAC Address .
- If the gateway column of the routing table is empty , be IP Receiver in header IP The address is the next forwarding destination .
These steps are described in detail , The following procedure can be obtained :
- First judgement MAC Address , Take out MAC The header determines the gateway of the routing table , If the gateway is empty , be IP Reception in the head Fang IP Address is the destination address to be forwarded .
- ARP The broadcast protocol is based on IP Find each other MAC Address , And store the uncollected party MAC Address .
- Fill in the sender of the output terminal MAC Address field , Fill in the output port here MAC The address also has an Ethernet type field , Fill in 0080( Hexadecimal ).
- Transfer network packets into electrical signals , If the signal collides, it will be retransmitted , If it is not in full duplex mode, wait for no signal from the line for transmission , Otherwise, there is no need to confirm whether other signals are directly transmitted .
- The sent packet is transmitted to the next router through the switch , Then, the router forwards to the destination layer by layer according to the rules .
The whole process is similar to the transmission of Modern Express , From one site to the next , Finally arrive at the destination address . The role of the switch is also very obvious , He and the router belong to the division of labor and cooperation ,IP ( Router ) Responsible for the overall process of sending packets to the communication object , The process of transferring the packet to the next router is carried by Ethernet ( Switch ) To be responsible for the .
The router is the role of the steering wheel here , The switch is more like a driver .
Other functions of the router
IP The length of the address is 32 individual bit, So in many cases, users of different LANs may have the same I P. To solve the same IP On the Internet “ coexistence ” problem , It is necessary to use the fixed address allocation method to distinguish the internal and external networks .
Usually we call the network for internal use of the company private address , The fixed address that provides external access is called the fixed address . The difference between public address and private address is that private address will be converted when accessing the Internet and can only communicate directly in the intranet , And this transformation mechanism is crucial ,
Address translation
The basic principle of address translation is to forward network packets IP The head of the IP Address and port number To rewrite . See the following example for details , When only one public address can be used externally , You can use different port numbers to distinguish between Different terminal .
The address translation device will find... From the address correspondence table through the public address and port number Corresponding private address and port number , Look up the private address according to the corresponding table And public address , Then rewrite the address and port number for forwarding .
On the surface, address translation is similar to delegate operation , The communication object of the receiver is actually completed with the address conversion device .
Rewrite the port number
The meaning of rewriting the port number is to make a public address correspond to more private addresses , For a large company, a public network address can support tens of thousands of ports .
In addition, if the communication of the intranet address does not exist in the address conversion device table, it can also communicate normally , Because the address of the forwarding device itself is the public network address used to rewrite .
Router packet filtering
Finally, filter the routing packets , Basically through IP modular ,MAC Module and TCP The module cooperates to verify whether a network packet request is legal .
Of course, the meaning of packet filtering is to ensure network security , Prevent the Internet from forging network packets to enter the content and damaging the system application of the intranet .
When the network packet is connected to the router through the Internet , The next part is ADS L perhaps FTTH The work of , This part is mainly about operators .
Other content
A hub (repeater hub) Switch (switching hub) though The name is the same, but the internal structure is completely different , Early routers were actually less efficient than switches , But if the router is called hub Obviously, it will make users think it is expensive and difficult to accept , But if you tell the customer to connect to the Internet cable, you can access the Internet , Things will be different .
In addition, the switch developed a two-layer switch in the later historical development , We show it in the summary . From the literal understanding, small and cheap popular products are generally called switches , Large high-performance products are generally called layer-2 switches .
Summary
Here is the summary hub 、 What are switches and routers , Next, we will supplement the subsequent development of the switch .
A hub
A hub ( namely HUB, Physical devices ) It is a device that connects multiple twisted pairs or optical fibers in the same physical medium , It usually works in the physical layer ( namely OSI Refer to the first layer of the model ), Used to connect LAN segments .
The hub has multiple ports , When one of the ports receives a signal , The attenuated signal will be shaped and amplified , Then the amplified signal broadcast is forwarded to all other ports , So that all segments of the LAN can see the packets . In the network , The hub acts as a common connection point for the device .
stay OSI The bottom of the reference model . Common devices also include network cards 、 A hub 、 Repeater 、 modems 、 Ethernet cable 、 Twisted pair 、 Coaxial cable .
Switch
Switch is a kind of optical / Network equipment for transmitting electrical signals , Usually work in Data link layer or network layer ( namely OSI The second and third layers of the reference model ), Support various packet protocols . At present, there are many types of switches , Such as LAN switch 、 Ethernet switch, etc .
LAN switch is mainly used for data exchange in switched LAN , Ethernet switch is mainly used for data transmission in Ethernet .
In a network, a switch is a device used to filter and forward packets between LAN segments .
Router
A router is a connection Internet Local area networks in 、 Wan devices , It is usually located at the gateway of two or more network connections , Working in The network layer , It is used to realize the network connection between two LANs or two WANs or one LAN and Internet service providers .
A routing table is usually stored in the router , It will automatically select and set the route according to the channel , Then send the signal in the best path . in addition , Router support Internet Control message protocol ( namely ICMP) Similar agreement , Can help IP host 、 Routing control messages between routers , Configure the best route between any two hosts .
Layer 2 and layer 3 switches
Layer-2 switches are usually used to connect network devices and client devices in Ethernet , To identify and forward MAC Address . But with the increasing diversity of network applications and the development of converged network applications , The application of layer 3 switch in Data Center , Complex enterprise networks , Business applications and even high-level customer projects .
Layer 2 switch works in OSI Second layer of model ( Data link layer ), So it's called layer 2 switch , The main functions include physical addressing 、 Error checking 、 Frame sequence and flow control . The layer 3 switch is located on the layer 3 ( The network layer ), It's a Equipment with three-layer switching function , That is, a layer-2 switch with layer-3 routing function , But it is an organic combination of the two , It is not simply superimposing the hardware and software of the router device on the LAN switch .
The difference between layer 2 and layer 3 switches
The main difference between layer 2 and layer 3 switches is whether they have routing function .
Two-layer switch : It belongs to data link layer equipment , Can identify... In the packet MAC Address information , according to MAC Address forwarding , And these MAC The address and the corresponding port are recorded in an internal address table .
Three layer switch : Is to have Switching of some router functions machine , Working in OSI Three layers of network standard model : The network layer , The purpose is to speed up the data exchange within a large LAN , The routing function is also used for this purpose , Be able to route once , Forward many times . Besides , Layer 3 switches can perform static routing and dynamic routing .
OSI Reference model
although OSI The original idea of the model is very beautiful , However, it is actually TCP/IP Network model substitution , However, the contents of the following three layers are basically unchanged , After learning the contents of this chapter , We should have a more in-depth understanding of the entire Internet Architecture .
边栏推荐
- L1 regularization and L2 regularization
- C, Numerical Recipes in C, solution of linear algebraic equations, Gauss Jordan elimination method, source code
- Solve the problem of "Chinese garbled MySQL fields"
- C语言-入门-基础-语法-数据类型(四)
- Newh3c - network address translation (NAT)
- In depth research and investment strategy report on China's hydraulic parts industry (2022 Edition)
- UML 时序图[通俗易懂]
- [Chongqing Guangdong education] National Open University spring 2019 455 logistics practice reference questions
- Internal learning
- How to choose solid state hard disk and mechanical hard disk in computer
猜你喜欢
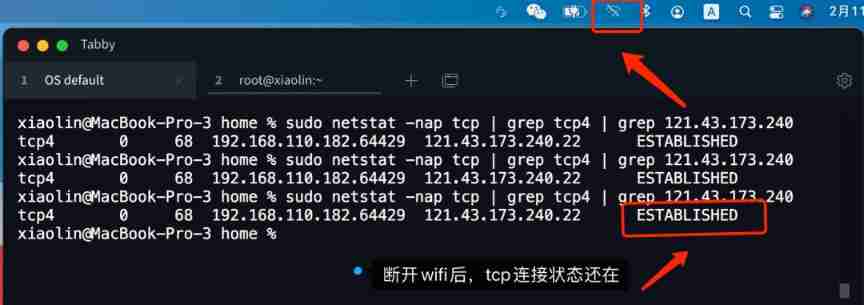
After unplugging the network cable, does the original TCP connection still exist?
](/img/dc/5c8077c10cdc7ad6e6f92dedfbe797.png)
C语言-入门-基础-语法-[变量,常亮,作用域](五)

Awk from entry to earth (12) awk can also write scripts to replace the shell
go-zero微服务实战系列(九、极致优化秒杀性能)
埃氏筛+欧拉筛+区间筛

What exactly is DAAS data as a service? Don't be misled by other DAAS concepts
Display Chinese characters according to numbers
![[C Advanced] file operation (2)](/img/50/e3f09d7025c14ee6c633732aa73cbf.jpg)
[C Advanced] file operation (2)
Ehrlich sieve + Euler sieve + interval sieve
System disk expansion in virtual machine
随机推荐
Educational Codeforces Round 119 (Rated for Div. 2)
From scratch, use Jenkins to build and publish pipeline pipeline project
[C Advanced] file operation (2)
awk从入门到入土(9)循环语句
swatch
How does Xiaobai buy a suitable notebook
C语言-入门-基础-语法-[主函数,头文件](二)
awk从入土到入门(10)awk内置函数
China electronic grade sulfur trioxide Market Forecast and investment strategy report (2022 Edition)
Cancel ctrl+alt+delete when starting up
std::is_ union,std::is_ class,std::integral_ constant
Codeforces Round #803 (Div. 2)(A-D)
Openfeign service interface call
C#实现一个万物皆可排序的队列
Flutter integrated amap_ flutter_ location
Launpad | 基础知识
How to choose solid state hard disk and mechanical hard disk in computer
Codeforces Round #803 (Div. 2)(A-D)
什么是权限?什么是角色?什么是用户?
Go zero micro service practical series (IX. ultimate optimization of seckill performance)