当前位置:网站首页>test about BinaryTree
test about BinaryTree
2022-07-06 10:53:00 【Frank.Ren】
/**
* Definition for a binary tree node.
* public class TreeNode {
* int val;
* TreeNode left;
* TreeNode right;
* TreeNode(int x) { val = x; }
* }
*/
class Solution {
public boolean getPath(TreeNode root, TreeNode node, Stack<TreeNode> stack) {
if (root == null || node == null) {
return false;
}
stack.push(root);
if (root == node) {
return true;
}
boolean key = getPath(root.left, node, stack);
if (key) {
return true;
}
key = getPath(root.right, node, stack);
if (key) {
return true;
}
stack.pop();
return false;
}
public TreeNode lowestCommonAncestor(TreeNode root, TreeNode p, TreeNode q) {
Stack<TreeNode> stack1 = new Stack<>();
getPath(root, p, stack1);
Stack<TreeNode> stack2 = new Stack<>();
getPath(root, q, stack2);
int diff = stack1.size() - stack2.size();
while (diff > 0) {
diff--;
stack1.pop();
}
while (diff < 0) {
diff++;
stack2.pop();
}
while (stack1.size() > 0) {
TreeNode cur = stack1.pop();
if (Objects.equals(cur, stack2.pop())) {
return cur;
}
}
return null;
}
}/**
* Definition for a binary tree node.
* public class TreeNode {
* int val;
* TreeNode left;
* TreeNode right;
* TreeNode(int x) { val = x; }
* }
*/
class Solution {
public TreeNode lowestCommonAncestor(TreeNode root, TreeNode p, TreeNode q) {
if (root == null) {
return null;
}
if (root == p || root == q) {
return root;
}
TreeNode leftNode = lowestCommonAncestor(root.left, p, q);
TreeNode rightNode = lowestCommonAncestor(root.right, p, q);
if (leftNode != null && rightNode != null) {
return root;
} else if (leftNode != null) {
return leftNode;
} else if (rightNode != null) {
return rightNode;
}
return null;
}
}边栏推荐
- Epoll () whether it involves wait queue analysis
- Self supervised heterogeneous graph neural network with CO comparative learning
- ORACLE进阶(四)表连接讲解
- STM32+ESP8266+MQTT协议连接OneNet物联网平台
- Numerical analysis: least squares and ridge regression (pytoch Implementation)
- 【中山大学】考研初试复试资料分享
- Atcoder a mountaineer
- Optical blood pressure estimation based on PPG and FFT neural network [translation]
- Penetration test information collection - App information
- C#/VB.NET 给PDF文档添加文本/图像水印
猜你喜欢
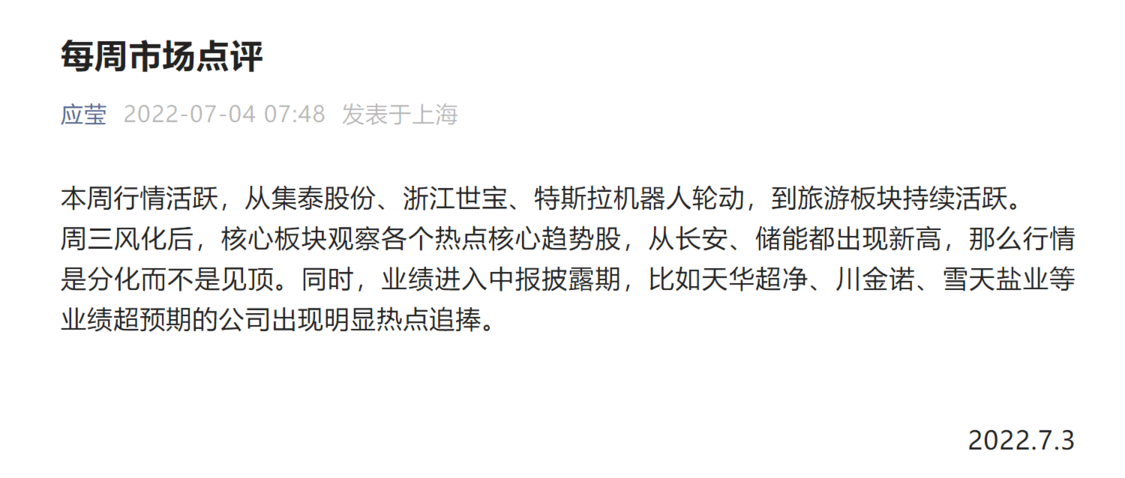
徐翔妻子应莹回应“股评”:自己写的!
Introduction and case analysis of Prophet model
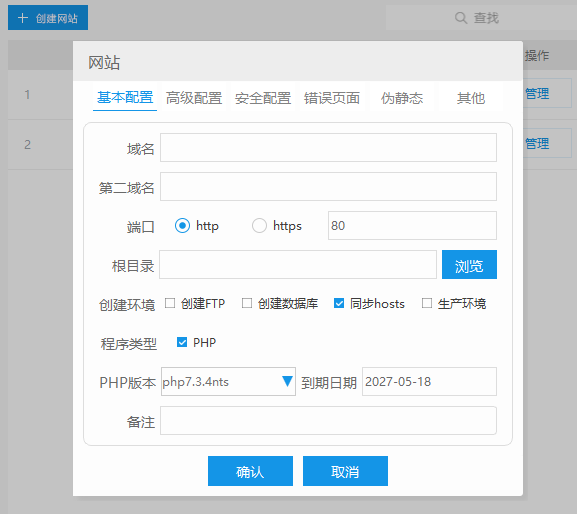
使用cpolar建立一个商业网站(1)

C#/VB.NET 给PDF文档添加文本/图像水印

【中山大学】考研初试复试资料分享

SAP Fiori 应用索引大全工具和 SAP Fiori Tools 的使用介绍
![Optical blood pressure estimation based on PPG and FFT neural network [translation]](/img/88/2345dac73248a5f0f9fa3142ca0397.png)
Optical blood pressure estimation based on PPG and FFT neural network [translation]
![[.Net core] solution to error reporting due to too long request length](/img/62/6bdc43885f9be3fa4538276c0dc122.png)
[.Net core] solution to error reporting due to too long request length
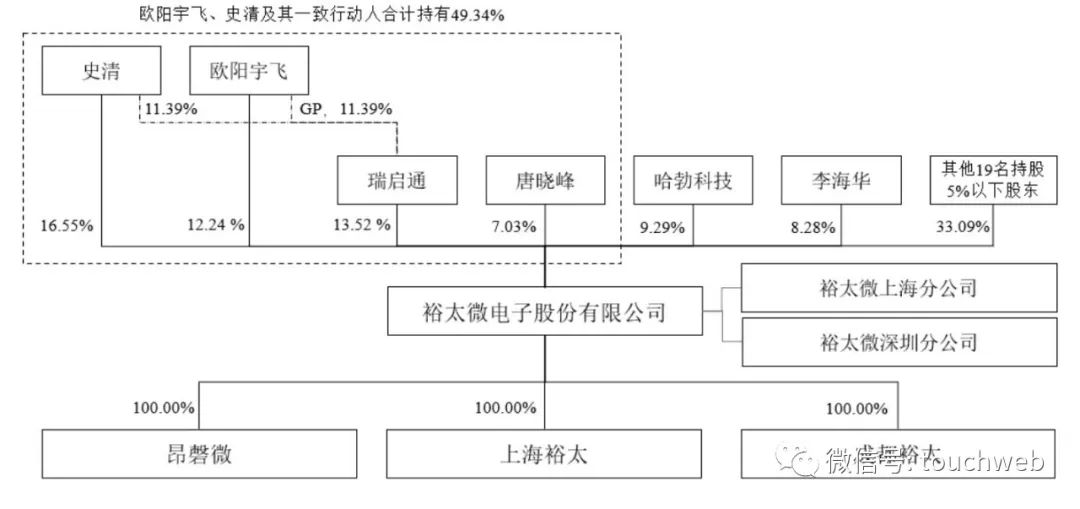
裕太微冲刺科创板:拟募资13亿 华为与小米基金是股东

Summary of performance knowledge points
随机推荐
美庐生物IPO被终止:年营收3.85亿 陈林为实控人
测试123
Breadth first traversal of graph
二叉搜索树
被疫情占据的上半年,你还好么?| 2022年中总结
bonecp使用数据源
DOM简要
Epoll () whether it involves wait queue analysis
使用cpolar建立一个商业网站(1)
atcoder它A Mountaineer
Mathematics in machine learning -- common probability distribution (XIII): Logistic Distribution
关于npm install 报错问题 error 1
Xu Xiang's wife Ying Ying responded to the "stock review": she wrote it!
Maixll dock camera usage
The role of applet in industrial Internet
Deep circulation network long-term blood pressure prediction [translation]
RedisSystemException:WRONGTYPE Operation against a key holding the wrong kind of value
Self-supervised Heterogeneous Graph Neural Network with Co-contrastive Learning 论文阅读
A wearable arm device for night and sleeveless blood pressure measurement [translation]
AFNetworking框架_上传文件或图像server