当前位置:网站首页>Penetration test information collection - WAF identification
Penetration test information collection - WAF identification
2022-07-06 18:35:00 【Aspirin. two thousand and two】
List of articles
waf distinguish
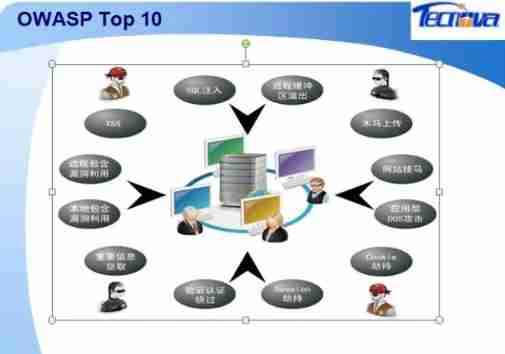
Web Application protection system ( Also known as : Website application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF). Use an internationally accepted saying :Web The application firewall is designed by performing a series of actions against HTTP/HTTPS The security policy for Web An application that provides protection
WAF Difference from network firewall
Network firewall as access control device , The main work is OSI Model three 、 four layers , be based on IP Message detection . Just limit the port , Yes TCP The agreement is blocked . Its product design does not need to be understood HTTP conversation , It also determines that you can't understand Web Application languages such as HTML、SQL Language . therefore , It's impossible HTTP Communication for input verification or attack rule analysis . in the light of Web Malicious attacks on websites Most of them will be encapsulated as HTTP request , from 80 or 443 The port successfully passed the firewall detection .
waf species
- Hardware equipment ( Green League 、 Venus 、 Anheng 、 Know Chuangyu 、 Tianrongxin, etc )
- Software products ( Safe dog 、 Cloud lock 、D Shield, etc )
- Cloud based WAF( Alibaba cloud 、 Anheng 、 Know Chuangyu )
waf distinguish
wafwoof—https://github.com/EnableSecurity/wafw00f
see X-Powered-By: WAF Parameters
Tool use
The target site :https://www.safedog.cn/
Under folder `python main.py https://www.safedog.cn/
Know that the site uses waf after , It can be judged that the manufacturer is trying to bypass , And know that the site exists waf after , Pay attention when using scanning tools , Easy to ban ip
边栏推荐
- Shangsilicon Valley JUC high concurrency programming learning notes (3) multi thread lock
- Specify flume introduction, installation and configuration
- Maixll dock camera usage
- 随着MapReduce job实现去加重,多种输出文件夹
- Transport layer congestion control - slow start and congestion avoidance, fast retransmission, fast recovery
- CSRF vulnerability analysis
- Automatic reservation of air tickets in C language
- Jerry is the custom background specified by the currently used dial enable [chapter]
- 2022暑期项目实训(二)
- [sword finger offer] 60 Points of N dice
猜你喜欢
虚拟机VirtualBox和Vagrant安装
30 分钟看懂 PCA 主成分分析
从交互模型中蒸馏知识!中科大&美团提出VIRT,兼具双塔模型的效率和交互模型的性能,在文本匹配上实现性能和效率的平衡!...
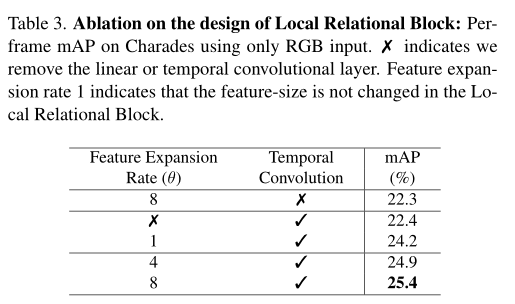
Ms-tct: INRIA & SBU proposed a multi-scale time transformer for motion detection. The effect is SOTA! Open source! (CVPR2022)...
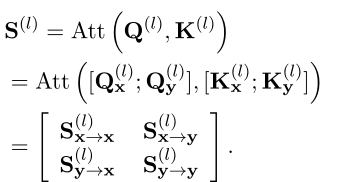
Distiller les connaissances du modèle interactif! L'Université de technologie de Chine & meituan propose Virt, qui a à la fois l'efficacité du modèle à deux tours et la performance du modèle interacti
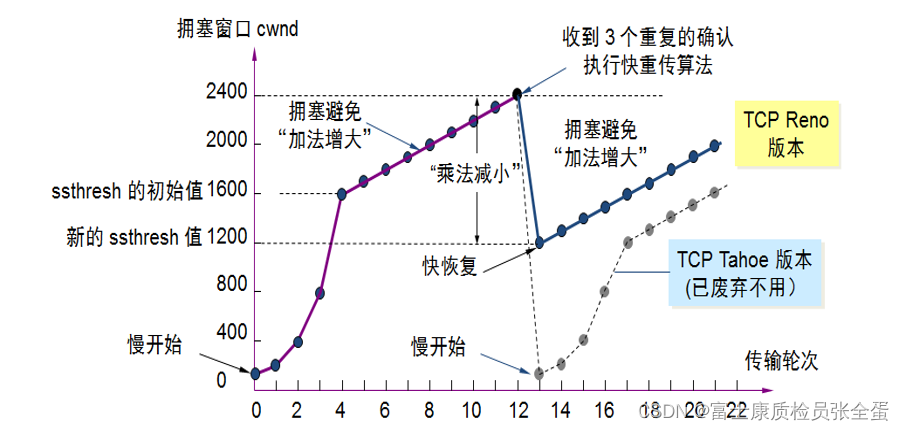
传输层 拥塞控制-慢开始和拥塞避免 快重传 快恢复
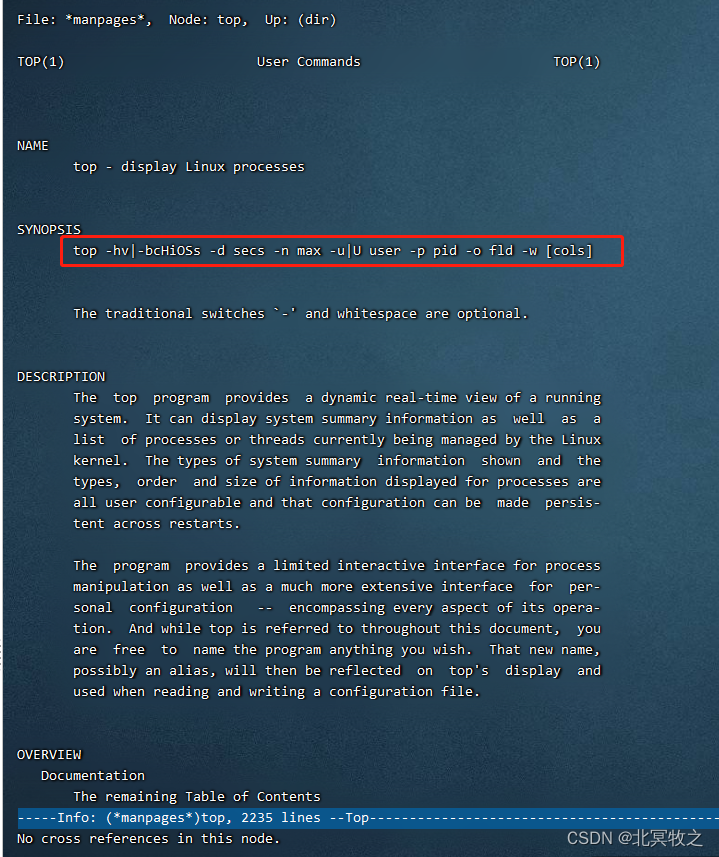
Top command details

面向程序员的精品开源字体
Implementation of queue

2022-2024年CIFAR Azrieli全球学者名单公布,18位青年学者加入6个研究项目
随机推荐
Comparative examples of C language pointers *p++, * (p++), * ++p, * (++p), (*p) + +, +(*p)
递归的方式
Docker安装Redis
Xu Xiang's wife Ying Ying responded to the "stock review": she wrote it!
2022暑期项目实训(三)
First, look at K, an ugly number
【.NET CORE】 请求长度过长报错解决方案
图片缩放中心
Cocos2d Lua smaller and smaller sample memory game
Bonecp uses data sources
测试123
Test 123
Compilation Principle -- C language implementation of prediction table
Will openeuler last long
2022-2024年CIFAR Azrieli全球学者名单公布,18位青年学者加入6个研究项目
【Swoole系列2.1】先把Swoole跑起来
30 分钟看懂 PCA 主成分分析
2022暑期项目实训(一)
Shangsilicon Valley JUC high concurrency programming learning notes (3) multi thread lock
AFNetworking框架_上传文件或图像server