当前位置:网站首页>Gartner released the prediction of eight major network security trends from 2022 to 2023. Zero trust is the starting point and regulations cover a wider range
Gartner released the prediction of eight major network security trends from 2022 to 2023. Zero trust is the starting point and regulations cover a wider range
2022-07-06 00:52:00 【CSDN cloud computing】
Gartner The recently released forecast of important trends in network security shows : Executive performance evaluation will be increasingly linked to network risk management capabilities ; In the next three years , Nearly one-third of the world's countries will adopt legislation to regulate the countermeasures against extortion software ; The integration of security platforms will ensure the rapid development of enterprises even in harsh environments .
edit | Song Hui
Contribution | Gartner
In the near future Gartner In the opening keynote speech of the safety and Risk Management Summit ,Gartner Senior Research Director Richard Addiscott And executive vice president Rob McMillan Discussed Gartner Important trend prediction proposed by network security experts , These predictions can help security and risk leaders succeed in the digital age .
Addiscott Express :“ We can't be conservative , It is not feasible to solve all problems with the past methods . Most safety and risk leaders have realized , In the event of a crisis , It will cause serious business interruption . Although we cannot control the crisis , But we can constantly adjust our way of thinking 、 idea 、 Plan and structure .”
Gartner Suggest , Network security leaders should grasp the following strategic predictions , Reasonably formulate the security strategy for the next two years .
From now to 2023 year , Laws and regulations that require enterprises and institutions to protect consumers' privacy rights will cover 50 Billion citizens and more than 70% The world GDP.
By 2021 year , existing 50 Countries are close to 30 The privacy rights of 100 million consumers have been protected , And the coverage of privacy laws continues to expand .Gartner Suggest , The enterprise should track the indicators of the subject's claim , For example, the processing cost and completion time of each request , Find out the links that need to be improved in efficiency , And prove the necessity of accelerating Automation .
To 2025 year ,80% Of enterprises will take advantage of a single manufacturer SSE Platform access network 、 Strategies for cloud services and dedicated applications .
at present , Mixed office mode has been gradually popularized , The need to access data through any device anytime, anywhere is also increasing . So , Manufacturers began to launch comprehensive security service edge (SSE) Solution , Around the network 、 Private access and SaaS application , Create consistency 、 Simple security function . Compared with solutions with single advantages , Comprehensive solutions from a single manufacturer can improve operational efficiency and safety , Including tighter integration 、 Console reduction , And data decryption 、 The location of checking and re encrypting is reduced .
To 2025 year ,60% Enterprises and institutions will take zero trust as the starting point of safety work , More than half of enterprises and institutions will not be able to play the advantage of zero trust .
Now , The word "zero trust" is very common in the marketing of security manufacturers and the security guidance of the government . Zero trust use based on identity and context 、 Trust with moderate risk replaces implicit trust , Is a very powerful mode of thinking . However , Zero trust is both a security principle , It is also an organizational vision , Therefore, enterprises and institutions need to connect with business results through cultural change and effective communication , To give full play to its advantages .
To 2025 year ,60% Of enterprises and institutions will regard network security risk as a major determinant of third-party transactions and business transactions .
Cyber attacks related to third parties are increasing . but Gartner Research shows , have only 23% The security and risk leaders of the company conduct real-time monitoring of third-party network security risks .Gartner Think , As consumer concerns intensify and regulators' attention heats up , From simple key technology supplier monitoring to complex M & A due diligence , Enterprises and institutions will begin to regard network security risk as an important determinant when conducting business with third parties .
To 2025 year ,30% The country will approve the legislation , Pay for ransomware 、 Make provisions for fines and negotiations , and 2021 This proportion was less than in 1%.
Now , Modern extortion software gangs not only steal data , And the data will be encrypted . Business organizations often start from a business rather than a security perspective , Decide whether to pay the ransom .Gartner Suggest , Before negotiation , It should communicate with professional incident response teams as well as law enforcement departments and relevant regulatory agencies , Get advice .
To 2025 year , Threat actors will successfully turn the operational technology environment into weapons , Causing casualties .
Attacks against operational technologies have become more common ( Operation technology refers to equipment 、 Hardware and software for monitoring or controlling assets and processes ), Will cause greater damage .Gartner Think , Safety and risk management leaders are in the process of ensuring the safety of the operating environment , Protecting people and the environment from real harm should be placed in a more important position than preventing information theft .
To 2025 year ,70% CEO of (CEO) It will require the establishment of a resilient corporate culture , To deal with all kinds of threats at the same time : Cyber crime 、 Bad weather events 、 Civil strife and political unrest .
COVID-19 has exposed the limitations of traditional business continuity management planning , That is, it cannot help enterprises and institutions cope with large-scale disruption . In view of the possible continuous interruption ,Gartner It is suggested that risk leaders make Organizational Resilience a strategic priority , And make a plan to let employees 、 Interested parties 、 Corporate level resilience strategies in which customers and suppliers participate .
To 2026 year ,50% The performance requirements related to risks will be added to the labor contract of the chief executive of .
Gartner A recent survey found , Most boards now view cybersecurity more than IT Technical problems , It is also considered a business risk . therefore ,Gartner expect , Senior business leaders will officially replace security leaders , Become the person in charge of network security .
边栏推荐
- CTF daily question day44 rot
- Data analysis thinking analysis methods and business knowledge -- analysis methods (II)
- 小程序容器可以发挥的价值
- Fibonacci number
- [EI conference sharing] the Third International Conference on intelligent manufacturing and automation frontier in 2022 (cfima 2022)
- esxi的安装和使用
- Promise
- golang mqtt/stomp/nats/amqp
- [groovy] JSON serialization (jsonbuilder builder | generates JSON string with root node name | generates JSON string without root node name)
- MIT doctoral thesis | robust and reliable intelligent system using neural symbol learning
猜你喜欢
![[groovy] JSON serialization (jsonbuilder builder | generates JSON string with root node name | generates JSON string without root node name)](/img/dd/bffe27b04d830d70f30df95a82b3d2.jpg)
[groovy] JSON serialization (jsonbuilder builder | generates JSON string with root node name | generates JSON string without root node name)
The population logic of the request to read product data on the sap Spartacus home page
数据分析思维分析方法和业务知识——分析方法(三)
VSphere implements virtual machine migration
How to make your own robot
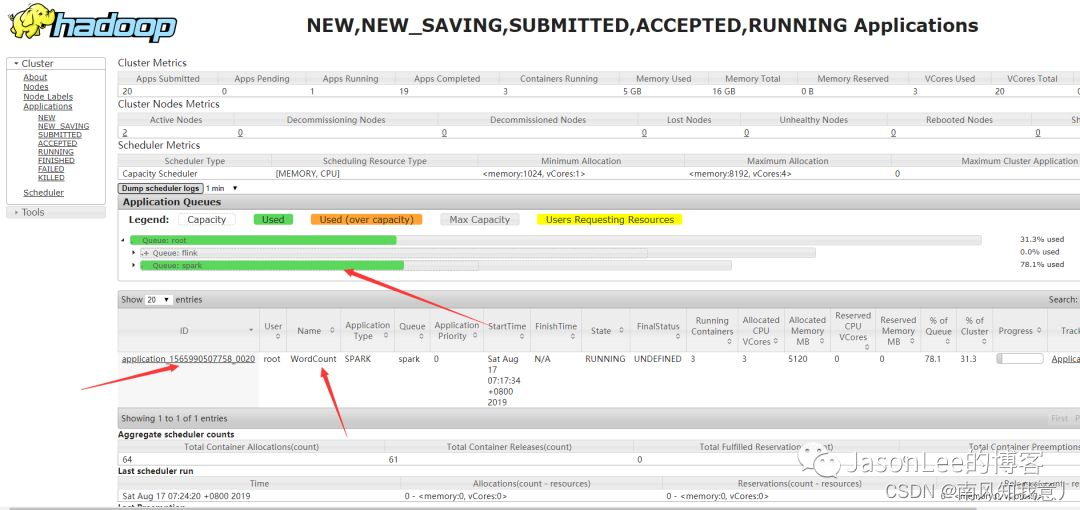
Idea remotely submits spark tasks to the yarn cluster
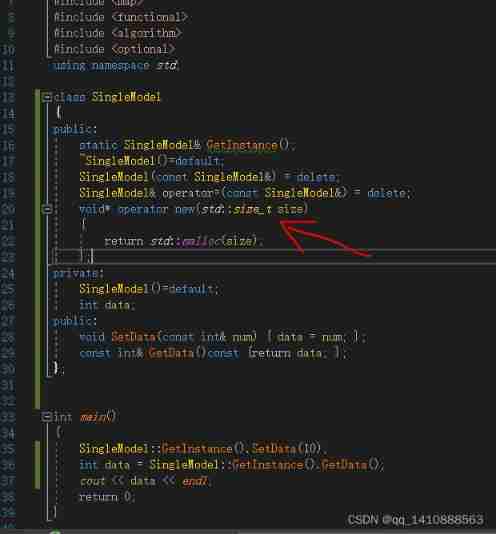
Differences between standard library functions and operators
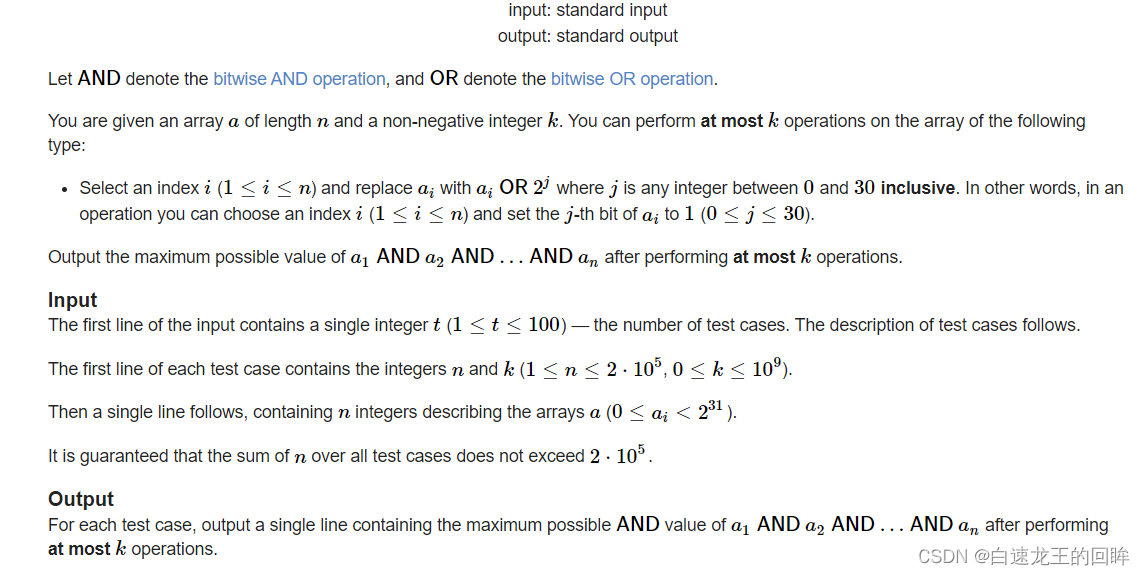
cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】

Comment faire votre propre robot
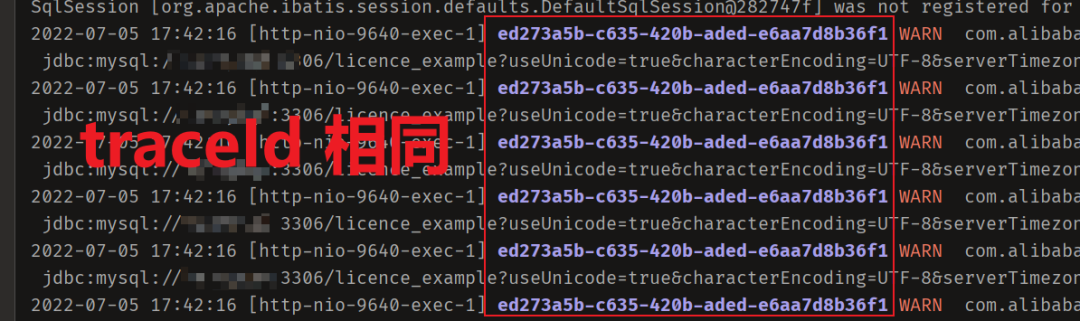
从 1.5 开始搭建一个微服务框架——调用链追踪 traceId
随机推荐
Spark AQE
MCU通过UART实现OTA在线升级流程
Opencv classic 100 questions
MIT博士论文 | 使用神经符号学习的鲁棒可靠智能系统
Logstash clear sincedb_ Path upload records and retransmit log data
Analysis of the combination of small program technology advantages and industrial Internet
Pointer pointer array, array pointer
curlpost-php
STM32 key chattering elimination - entry state machine thinking
几百行代码实现一个 JSON 解析器
Browser reflow and redraw
直播系统代码,自定义软键盘样式:字母、数字、标点三种切换
[groovy] XML serialization (use markupbuilder to generate XML data | create sub tags under tag closures | use markupbuilderhelper to add XML comments)
The third season of ape table school is about to launch, opening a new vision for developers under the wave of going to sea
Fibonacci number
Meta AI西雅图研究负责人Luke Zettlemoyer | 万亿参数后,大模型会持续增长吗?
《强化学习周刊》第52期:Depth-CUPRL、DistSPECTRL & Double Deep Q-Network
synchronized 和 ReentrantLock
2022-02-13 work record -- PHP parsing rich text
Spark AQE