当前位置:网站首页>OWASP top 10 vulnerability Guide (2021)
OWASP top 10 vulnerability Guide (2021)
2022-07-05 04:15:00 【Two ladies' post it notes】
What is? OWASP TOP 10?
OWASP, Full name “ open Web Application Security Project ” It's a non-profit organization ,2003 The organization first published “Top 10”, That is to say 10 The most serious Web Application security risk list .
Top 10 Sum up Web Applications are most likely 、 Most common 、 The top ten most dangerous security vulnerabilities .
In recent years OWASP TOP The change of 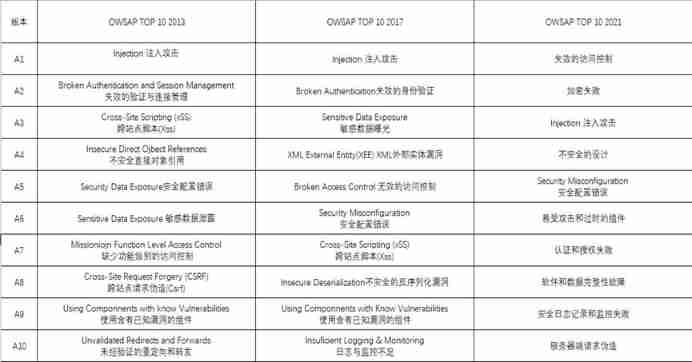
A1 Invalid access control
summary
Invalid access control , Also called ultra vires , Attackers use various means to increase their privileges , Beyond access control , Disable access control , In this way, the attacker can impersonate the user 、 Administrators or privileged users , Or create 、 visit 、 Update or delete any records .
Common access vulnerabilities include :
1. By modifying the URL、 Internal application status or HTML page , Or just use custom API Attack tools to bypass access control checks .
2. Allow to change the primary key to another user's record , Allow viewing or editing other people's accounts .
3. Privilege Promotion . Act as a user without logging in or as an administrator when logging in as a user .
4. Metadata operations , For example, replay or tamper JSON Web token (JWT) Access control token , Or used to promote authority or abuse JWT Invalid cookie Or hide fields .
5.CORS Incorrect configuration allows unauthorized API visit .
6. Force authenticated pages to be viewed as unauthenticated users or privileged pages to be viewed as standard users . visit API Lack of right POST、PUT and DELETE Access control .
classification
Vertical ultra vires , An attacker can access an application from ordinary user privileges to administrator privileges
The level is beyond authority , An attacker can get information from ordinary users A Upgrade your permissions to ordinary users B To access the application
defense
Access control only in trusted server-side code or no server API Effective in , An attacker cannot modify access control checks or metadata .
1. In addition to public resources , Default refusal .
2. Implement access control mechanisms once and reuse them throughout the application , Including minimizing CORS Use .
3. Model access control should enforce record ownership , Instead of accepting that users can create 、 Read 、 Update or delete any records .
4. Unique application business constraints should be enforced by the domain model .
5. Ban Web List the server directories and ensure that the file metadata ( for example .git) And backup files are not in Web In the root directory .
6. Record access control failed , Remind the administrator when appropriate ( for example , Repeat failed ).
7. Rate limit API And controller access , To minimize the harm of automatic attack tools .
8. After cancellation ,JWT The token should expire on the server .
A2 Encryption failed
summary
Previously known as sensitive data disclosure . The first is to determine the protection requirements for transmission and static data . for example , password 、 Credit card number 、 Health records 、 Personal information and trade secrets need additional protection , Mainly if the data belongs to privacy law ( For example, the EU's general data protection regulations (GDPR)) Or regulations ( For example, financial data protection ) for example PCI Data security standards (PCI DSS). For all such data :
1. Is there any data transmitted in clear text ? This involves HTTP、SMTP and FTP Such agreement . External Internet traffic is dangerous . Verify all internal flows , for example , Load balancer 、Web Traffic between servers or back-end systems .
2. Whether any old or weak encryption algorithms are used by default or in older code ?
3. Whether the default encryption key is being used 、 Generate or reuse weak encryption keys , Or lack of proper key management or rotation ?
4. Whether encryption is not enforced , for example , Are there any user agents missing ( browser ) Security directive or header ?
5. The user agent ( for example , Applications 、 Mail client ) Do not verify that the received server certificate is valid ?
defense
1. Handle the application 、 Classify stored or transmitted data . Under the privacy act 、 Regulatory requirements or business needs determine which data is sensitive .
2. Apply control according to classification .
3. Don't store sensitive data unnecessarily . Discard it or use it as soon as possible PCI DSS Tokenization and even truncation of . Unreserved data cannot be stolen .
4. Ensure that all static sensitive data is encrypted .
5. Ensure that you have the latest and powerful standard algorithms 、 Protocol and key ; Use appropriate key management .
6. Use security protocols ( For example, with perfect forward secrecy (PFS) Cryptographically TLS、 Password priority and security parameters of the server ) Encrypt all data in transmission . Use HTTP Strict transmission security (HSTS) Wait for instructions to force encryption .
7. Disable caching for responses that contain sensitive data .
8. Use with working factor ( Delay factor ) Strong adaptive and salt hash function for storing passwords , for example Argon2、scrypt、bcrypt or PBKDF2.
9. Independently verify the validity of the configuration and settings .
A3 Injection attack
summary
Applications are vulnerable in the following situations :
1. The application does not validate 、 Filter or clean up user provided data .
2. Dynamic queries or nonparametric calls without context aware escape are used directly in the interpreter .
3. In Object Relation Mapping (ORM) Use malicious data in search parameters to extract additional sensitive records .
4. Use or connect malicious data directly .SQL Or the command contains dynamic queries 、 Structures and malicious data in commands or stored procedures .
Some of the more common injections are SQL、NoSQL、OS command 、 Object relation mapping (ORM)、LDAP And expression language (EL) Or object graph navigation library (OGNL) Inject . This concept is the same among all interpreters . Source code review is the best way to detect whether an application is vulnerable to injection attacks . It is strongly recommended that all parameters 、 header 、URL、cookie、JSON、SOAP and XML Data input for automated testing . Organizations can incorporate static sources (SAST) And dynamic application testing (DAST) Tools include CI/CD In the pipeline , To identify incoming injection defects prior to production deployment .
Usually injected with sql Injection and os(Operating System) Inject
SQL Inject : It's through SQL Command insert into Web Form submit or input the query string of domain name or page request , Finally, to cheat the server to execute malicious SQL command . say concretely , It's about leveraging existing applications , take ( malice ) Of SQL Ability of command injection into background database engine , It can be Web Input in form ( malice )SQL Statement to get a database on a website with a security vulnerability , Not according to the designer's intention SQL sentence .
sql Injected defense
(1): Strict escaping and filtering of input .
(2): Data types are strictly defined , The data length is strictly regulated .
(3): adopt waf The device is enabled to prevent sql Injected strategy .
(4): Strictly restrict the access of the website to the database .
os Inject :Web In the programming language used for development , Most can pass Shell perform OS( operating system ) command . adopt Shell perform OS On command , Or a method used in the development uses Shell when , It's possible OS An arbitrary execution of a command . This phenomenon is called OS Command injection .
os Injected defense
1: Use safe function pairs to pass to OS Command parameters to escape .
2: Do not pass the external input string to the command line parameter .
3: Choose not to call OS How to implement the command .
defense
1. Preventing injection requires separating data from commands and queries .
2. The preferred option is to use secure API, It completely avoids the use of interpreters , Provide parameterized interface , Or migrate to the object relational mapping tool (ORM).
Be careful : Even when parameterized , If PL/SQL or T-SQL Connect queries and data or use EXECUTE IMMEDIATE or exec() Execute malicious data , The stored procedure will still introduce SQL Inject .
3. Use front or “ White list ” Server side input validation . This is not a complete defense , Because many applications require special characters , For example, a text area or a mobile application API.
For any residual dynamic queries , Use the interpreter's specific escape syntax to escape special characters .
Be careful : Table name 、 Name, etc SQL Structure cannot be escaped , Therefore, the structure name provided by the user is dangerous . This is a common problem in report writing software .
4. Use in query LIMIT And others SQL Control to prevent SQL In the case of injection, a large number of disclosure records .
A4 Unsafe design
defense
1. And AppSec Professionals establish and use a secure development lifecycle , To help evaluate and design security and privacy related controls
2. Build and use safe design pattern libraries or paved roads ready to use components
3. Use threat modeling for critical authentication 、 Access control 、 Business logic and critical flows
4. Write unit and integration tests to verify that all critical flows are resistant to threat models
A5 Security configuration error
summary
Security configuration error is a common vulnerability , Due to the improper configuration of the operator ( The default configuration , Temporary configuration , Open source cloud storage ,http Header configuration , And detailed errors containing sensitive information ), As a result, an attacker can use these configurations to obtain higher privileges , Security configuration errors can occur at all levels , Including platform 、web The server 、 application server 、 database 、 Architecture and code .
defense
1. The repeatable hardening process makes it quick and easy to deploy another properly locked environment . Development 、QA And production environments should be configured the same , Use different credentials in each environment . This process should be automated , To minimize the work required to set up a new security environment .
2. One does not have any unnecessary functions 、 Components 、 Minimal platform for documentation and examples . Remove or do not install unused features and frameworks .
3. As part of the patch management process , Review and update applicable to all safety instructions 、 Update and patch configuration tasks ( see also A06:2021- Vulnerable and outdated components ). View cloud storage permissions ( for example ,S3 Bucket permissions ).
4. Segmented application architecture through segmentation 、 Container or cloud security group (ACL) Provide effective and secure separation between components or tenants .
5. Send security instructions to the client , For example, security header .
6. An automated process to verify the effectiveness of configurations and settings in all environments .
A6 Vulnerable and outdated components
summary
You may be vulnerable :
1. If you don't know the versions of all the components you use ( Client side and server side ). This includes components you use directly and nested dependencies .
2. If the software is vulnerable 、 Unsupported or expired . This includes the operating system 、Web/ Application server 、 Database management system (DBMS)、 Applications 、API And all the components 、 Runtime environment and Libraries .
3. If you do not regularly scan for vulnerabilities and subscribe to security announcements related to the components you use .
4. If you don't repair or upgrade the underlying platform in a risk-based manner in time 、 Frameworks and dependencies . This usually occurs in environments where patching is a monthly or quarterly task under change control , Expose the organization to the risk of unnecessary exposure to fixed vulnerabilities for days or months .
5. If the software developer doesn't test the update 、 Compatibility of upgraded or patched Libraries .
6. If you do not protect the configuration of the component ( see also A05:2021- Security configuration error ).
defense
1. Delete unused dependencies 、 Unnecessary functions 、 Components 、 Files and documents .
2. Use version 、OWASP Dependency Check、retire.js And other tools continuously inventory client-side and server-side components ( For example, the framework 、 library ) And its dependencies . composition . Automate the process using software portfolio analysis tools . Subscribe to email alerts for security vulnerabilities related to the components you use .
3. Get components from official sources only via secure links . Signature packages are preferred to reduce the chance of containing modified malicious components ( see also A08:2021- Software and data integrity failure ).
4. Monitor libraries and components that are not maintained or security patches are not created for older versions . If you can't patch , Consider deploying a virtual patch to monitor 、 Detect or prevent problems found .
A7 Authentication and authorization failed
summary
Confirm the identity of the user 、 Authentication and session management are essential to prevent authentication related attacks . If the application has the following conditions , There may be authentication weaknesses :
1. Allow automatic attacks , For example, credential filling , Where the attacker has a list of valid user names and passwords .
2. Allow brute force cracking or other automatic attacks .
3. Allow default 、 Weak or known password , for example "Password1" or "admin/admin".
4. Use weak or invalid credentials to recover and forget passwords , for example " Knowledge based answers ", These processes cannot ensure safety .
5. Use plain text 、 Encrypted or weak hash password data storage ( Please see the A02:2021 - Encryption failed ).
6. With missing or invalid multiple authentication .
7. stay URL Public session identifier in .
8. Reuse session identifier after successful login .
9. The session is not properly ID invalid . User session or authentication token ( Mainly single sign on (SSO) token ) Not properly invalidated during logout or inactivity .
defense
1 Where possible , Implement multifactor authentication to prevent automatic credential filling 、 Brute force cracking and stolen credential reuse attacks .
2 Do not use any default credentials for delivery or deployment , Especially for administrator users .
3 Implement weak password checking , For example, for the former 10,000 A list of worst passwords to test new or changed passwords .
4 Change the password length 、 Complexity and rotation strategies and N alignment
5 By using the same message for all results , Make sure you register 、 Credential recovery and API Path can resist account enumeration attacks .
6 Limit or increasingly delay failed login attempts , But be careful not to cause a denial of service scenario . When voucher filling is detected 、 When brute force cracking or other attacks , Record all faults and remind the Administrator .
7 Use the server side 、 Security 、 Built in session manager , Generate a new high entropy random session after login ID. Session identifier should not be in URL in , Store safely , And sign out 、 Expires after idle and absolute timeout .
A8 Software and data integrity failure
summary
Software and data integrity failures are related to code and infrastructure that cannot prevent integrity violations . An example is application dependencies from untrusted sources 、 Repositories and content delivery networks (CDN) Plug in for 、 Library or module . unsafe CI/CD The pipeline may cause unauthorized access 、 Malicious code or system damage . Last , Many applications now include automatic updates , Where updates are downloaded without sufficient integrity verification and applied to previously trusted applications . Attackers may upload their own updates to distribute and run on all installations . Another example is when an object or data is encoded or serialized into a structure that an attacker can see and modify , Vulnerable to unsafe deserialization .
defense
- Use digital signatures or similar mechanisms to verify that software or data is from the intended source and has not been changed .
2 Ensure that libraries and dependencies ( for example npm or Maven) Using trusted Repository . If you have a high risk situation , Consider hosting a well-known repository that has been reviewed internally .
3 Ensure the use of software supply chain security tools ( for example OWASP Dependency Check or OWASP CycloneDX) To verify that the component does not contain known vulnerabilities
4 There is a process for reviewing and configuring the code , To minimize the chance that malicious code or configuration may be introduced into your software pipeline .
5 Make sure your CI/CD The pipeline has proper isolation 、 Configuration and access control , To ensure the integrity of the code flowing through the build and deployment process .
6 Ensure that unsigned or unencrypted serialized data is not sent to untrusted clients without some form of integrity check or digital signature , To detect tampering or playback of serialized data
A9 Security logging and monitoring failed
summary
It means without logging and monitoring , The vulnerability will not be detected , Such failures directly affect visibility 、 Incident alarm and evidence collection . Here are some risk types :
1. Do not record auditable Events , For example, log in 、 Failed logins and high value transactions .
2. Warnings and errors do not generate 、 Insufficient or unclear log messages .
3. Does not monitor applications and API Is there any suspicious activity in your log .
4. Logs are stored locally only .
5. Appropriate alert thresholds and response escalation processes are not in place or effective .
6. Dynamic application security testing (DAST) Tools ( for example OWASP ZAP) Penetration testing and scanning of the will not trigger alarms .
7. The application cannot detect... In real time or near real time 、 Upgrade or warn of active attacks .
defense
1. Ensure that all users are logged in 、 Both access control and server-side input validation failures can be recorded with sufficient user context , To identify suspicious or malicious accounts , And leave enough time to allow delay in forensic analysis .
2. Ensure that logs are generated in a format that can be easily used by the log management solution .
3. Ensure that the log data is encoded correctly , To prevent injection or attack on the log or monitoring system .
4. Ensure that high-value transactions have an audit trail with integrity controls , To prevent tampering or deletion , For example, append only database tables or similar .
5.DevSecOps The team should establish effective monitoring and alerts , In order to quickly detect and respond to suspicious activities .
6. Develop or adopt incident response and recovery plans , For example, the National Institute of standards and Technology (NIST) 800-61r2 Or later .
A10 Server request forgery (SSRF)
summary
whenever Web The application is not authenticating user provided URL When getting remote resources in the case of , Will appear SSRF defects . Even under the firewall 、VPN Or other types of network access control lists (ACL) The protection of the , It also allows attackers to force applications to send well-designed requests to unexpected destinations .
With modern times Web Applications provide convenient functions for end users , obtain URL Become a common situation . therefore ,SSRF The incidence rate is increasing . Besides , Due to the complexity of cloud services and Architecture ,SSRF The severity of is getting higher and higher .
SSRF(Server-Side Request Forgery: Server side Request Forgery ) It is a security vulnerability that is constructed by the attacker to form a request initiated by the server . In general ,SSRF Is to target the internal system of the website .( Because it's accessed from an internal system , All the internal systems that cannot be accessed through the external network can be attacked through it , That is to put the target website Inter man ).
defense
1. The blacklist
(1) Filter 10.0.0.0/8、172.16.0.0/12、12.168.0.0/16、localhost Private address 、Pv6 Address
(2) Filter file、dict:、 gopher:、ftp:/ dangerous schema
(3) Identify the returned content
(4) Intranet services enable authentication (Memcached, Redis, Elasticsearch and MongoDB
2. Best protection
(1) Use the address white list
(2) Identify the returned content
(3) Need to use Internet resources ( For example, post bar uses online pictures ) And you can't use whitelists : Disable first CURLOPT FOLLOWLOCATION: Then get the target through the domain name , And filter the inside ip; Finally, identify whether the returned content is consistent with the assumed content
边栏推荐
- 【刷题】BFS题目精选
- [untitled]
- Interview byte, pass the exam and directly work on three sides. As a result, I found an architect to hang me?
- Alibaba cloud ECS uses cloudfs4oss to mount OSS
- Rust blockchain development - signature encryption and private key public key
- web资源部署后navigator获取不到mediaDevices实例的解决方案(navigator.mediaDevices为undefined)
- Threejs realizes sky box, panoramic scene, ground grass
- Convert Boolean to integer value PHP - Convert Boolean to integer value PHP
- 基于TCP的移动端IM即时通讯开发仍然需要心跳保活
- Differences among 10 addressing modes
猜你喜欢
![[finebi] the process of making custom maps using finebi](/img/3a/d638dbac6a26c37087ec9550c35e63.png)
[finebi] the process of making custom maps using finebi
Looking back on 2021, looking forward to 2022 | a year between CSDN and me
MindFusion. Virtual Keyboard for WPF
Threejs Internet of things, 3D visualization of farms (I)
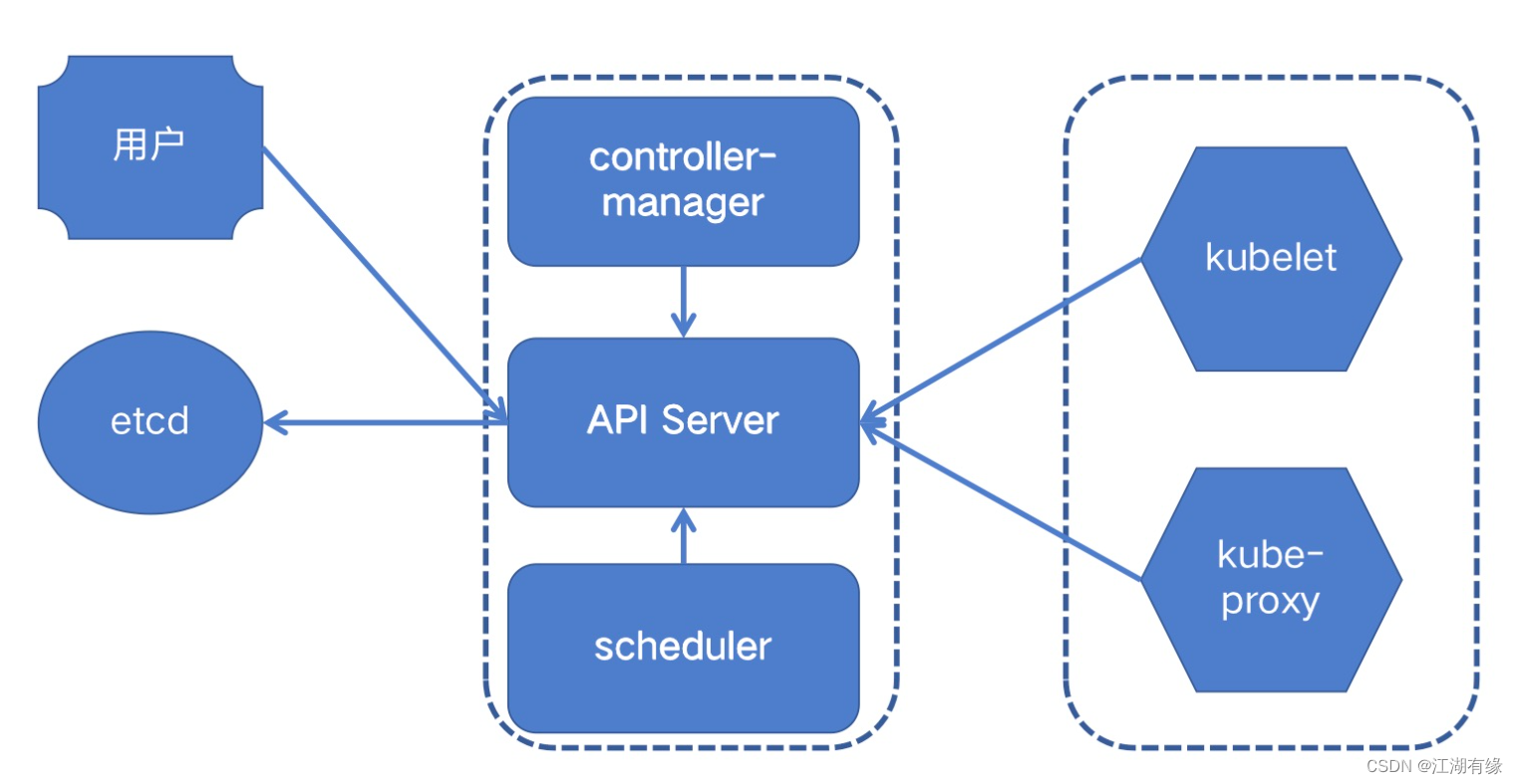
kubernetes集群之调度系统
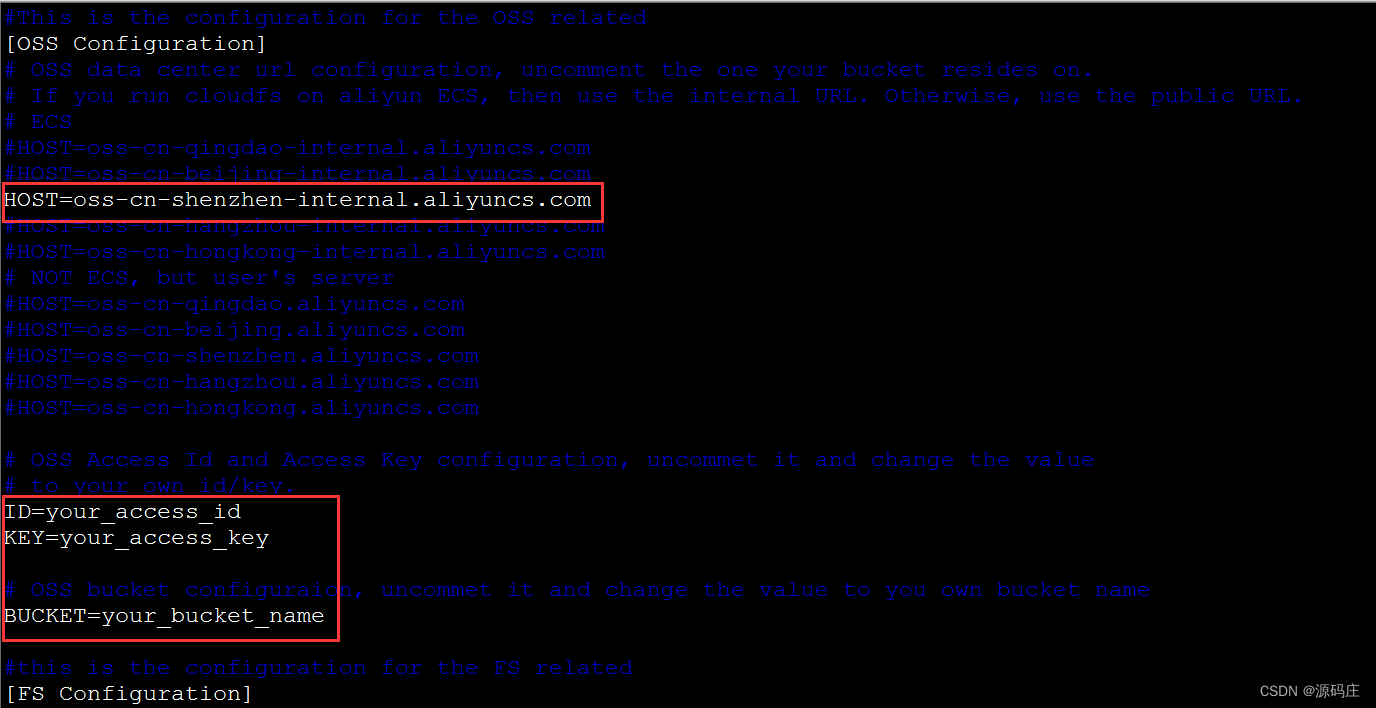
阿里云ECS使用cloudfs4oss挂载OSS
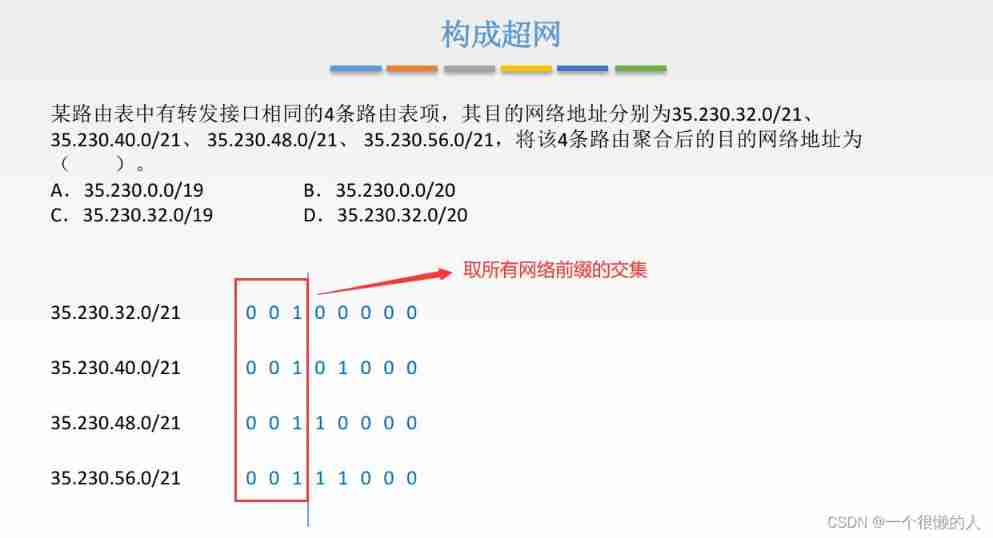
Network layer - forwarding (IP, ARP, DCHP, ICMP, network layer addressing, network address translation)
![[phantom engine UE] only six steps are needed to realize the deployment of ue5 pixel stream and avoid detours! (the principles of 4.26 and 4.27 are similar)](/img/eb/a93630aff7545c6c3b71dcc9f5aa61.png)
[phantom engine UE] only six steps are needed to realize the deployment of ue5 pixel stream and avoid detours! (the principles of 4.26 and 4.27 are similar)
【thingsboard】替换首页logo的方法
我国算力规模排名全球第二:计算正向智算跨越
随机推荐
The order of LDS links
BDF application - topology sequence
[thingsboard] how to replace the homepage logo
The new project Galaxy token just announced by coinlist is gal
Fuel consumption calculator
How is the entered query SQL statement executed?
provide/inject
Longyuan war "epidemic" 2021 network security competition web easyjaba
ActiveReportsJS 3.1 VS ActiveReportsJS 3.0
【虚幻引擎UE】运行和启动的区别,常见问题分析
Seven join join queries of MySQL
[untitled]
陇原战“疫“2021网络安全大赛 Web EasyJaba
Use threejs to create geometry and add materials, lights, shadows, animations, and axes
Behavior perception system
Study notes 7
Mixed compilation of C and CC
Machine learning -- neural network
[uniapp] system hot update implementation ideas
ClickPaaS低代码平台