当前位置:网站首页>Containerd series - detailed explanation of plugins
Containerd series - detailed explanation of plugins
2022-07-05 03:55:00 【PinkGranite】
containerd The functions provided by itself are very limited , however containerd It provides a very powerful plug-in system : By connecting various plug-ins, you can give containerd Many different grades , The ability not to function . This article will be about containerd The plug-in system of , Also on containerd The configuration mode of plug-in system of .
Catalog
1. containerd Introduction to plug-in system
- containerd Of Client Pattern : See the word and know its meaning ——Client Pattern representation containerd The upper layer of is also built with a more easy-to-use client model . Where is the meaning ? This makes containerd You can give up some problems that don't need to be solved by the daemon , Such as containers specification The construction of 、 Image warehouse management and so on . These functions can be provided by the upper Client To solve ( Possible Client Yes go client—— That is, by calling the relevant toolkit and API The way to solve these problems, rather than to daemon To solve ), Both decoupling and shrinking containerd The core volume of has also been further improved containerd The flexibility of the .
- Plug in system :containerd Support the effective expansion of its interface and functions through the plug-in system , Based on plug-ins, we can define our own runtime (runtime)( What is? runtime—— Reference series runc series )、 Container snapshot module 、 The enclosure even gRPC Module etc.
- plug-in unit : Plug ins provide dynamic extensions containerd The ability to function , An external plug-in can be used without recompiling containerd In the case of containerd The function of is to modify and change .containerd Two plug-in extension modes are provided :
- containerd PATH Binary files available in
- take containerd Configure as another gRPC Agent of service —— In other words, the plug-in that provides services in this way transfers the access mode to containerd Manage and forward
2. Various plug-ins and their configuration
2.1 V2 Runtimes
- containerd core Of runtime The sub module contains v2 Shim Interface , Allow various runtime ( for example runc) It is parsed as a secondary file on the system —— It also gives containerd Use many different runtime The flexibility of the ; These binaries will be used to open shim Process for container use , meanwhile containerd It can also be returned by runtime shim api To control the container
- containerd core Of runtime v2 Available for runtime Should have the function and api Interface is defined , It mainly designs the operation of container life cycle . More detailed information can be found in here
2.2 Proxy Plugins
- proxy The configuration of the plug-in is based on containerd Configuration of , When containerd Startup time , Complete the configured proxy The plug-in will start with the built-in plug-in .
- proxy Plug in through local socket And containerd Connect , It can be for containerd Of gRPC Service support .
- every last proxy The configuration of plug-ins is accompanied by type as well as name, The configuration method is basically the same as that of the built-in plug-in .
2.2.1 To configure
- It can be modified by containerd Configuration file for proxy Plug in configuration ,containerd The default profile location is
etc/containerd/config.toml. - By adding
[proxy_plugins]Segment and add[proxy_plugins.yourplugin]Section to configure the plug-in . amongaddressMust point to a local socket file (containerd Be able to access this socket file ); Currently supportedtypeIncludesnapshotas well ascontent. - Example :
[proxy_plugins] [proxy_plugins.customsnapshot] type = "snapshot" address = "/var/run/mysnapshotter.sock"```
2.2.2 Realization
- Achieve one proxy Plug in and implementation of a gRPC Our services are basically similar , For details, please refer to content store service And snapshotter service
- The following example comes from github file
package main import ( "fmt" "net" "os" "google.golang.org/grpc" snapshotsapi "github.com/containerd/containerd/api/services/snapshots/v1" "github.com/containerd/containerd/contrib/snapshotservice" "github.com/containerd/containerd/snapshots/native" ) func main() { // Provide a unix address to listen to, this will be the `address` // in the `proxy_plugin` configuration. // The root will be used to store the snapshots. if len(os.Args) < 3 { fmt.Printf("invalid args: usage: %s <unix addr> <root>\n", os.Args[0]) os.Exit(1) } // Create a gRPC server rpc := grpc.NewServer() // Configure your custom snapshotter, this example uses the native // snapshotter and a root directory. Your custom snapshotter will be // much more useful than using a snapshotter which is already included. // https://godoc.org/github.com/containerd/containerd/snapshots#Snapshotter sn, err := native.NewSnapshotter(os.Args[2]) if err != nil { fmt.Printf("error: %v\n", err) os.Exit(1) } // Convert the snapshotter to a gRPC service, // example in github.com/containerd/containerd/contrib/snapshotservice service := snapshotservice.FromSnapshotter(sn) // Register the service with the gRPC server snapshotsapi.RegisterSnapshotsServer(rpc, service) // Listen and serve l, err := net.Listen("unix", os.Args[1]) if err != nil { fmt.Printf("error: %v\n", err) os.Exit(1) } if err := rpc.Serve(l); err != nil { fmt.Printf("error: %v\n", err) os.Exit(1) } }
2.3 Use
- Based on the above proxy Implementation and configuration of plug-ins ,containerd You can use the plug-in
- The following example is also from the above document :
# Start plugin in one terminal $ go run ./main.go /var/run/mysnapshotter.sock /tmp/snapshots # Use ctr in another $ CONTAINERD_SNAPSHOTTER=customsnapshot ctr images pull docker.io/library/alpine:latest
- You can see , After implementing the corresponding plug-ins and interfaces , Just register the plug-in to containerd in ,containerd We can call our own plug-ins in the form of service requests , Very flexible and convenient .
2.3 Built in plug-ins (built-in)
2.3.1 Introduce
- containerd Ensure the low coupling of its internal implementation by means of plug-ins , stability ; Although it is called internal plug-in , but containerd Look at internal and external plug-ins in the same way .
- By command
ctr plugins lsView all containerd Built in plug-ins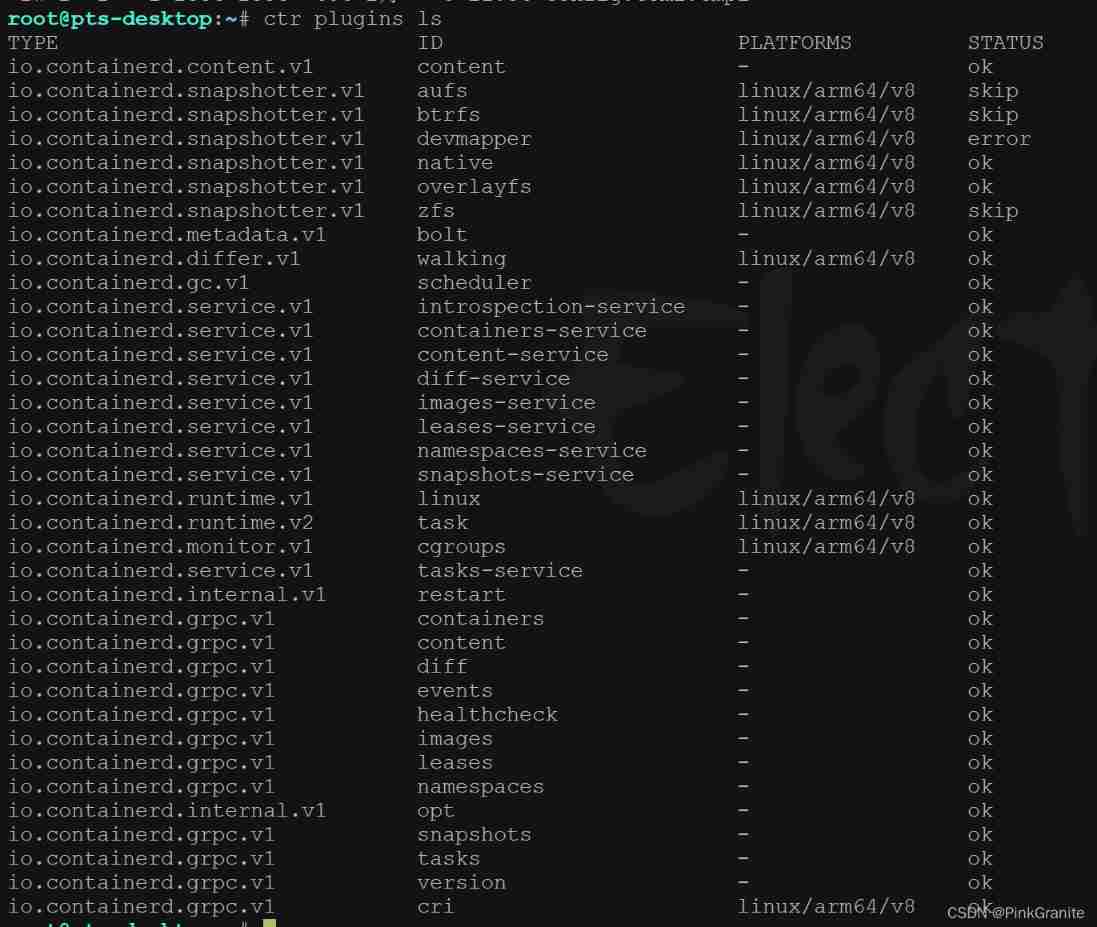
- Based on the output results in the above figure, we can see all the plug-ins loaded by the results and those in abnormal status ( The status is marked as
errorPlug in for ); By looking at log Log to determine why the plug-in failed to load .ctr plugins ls -d id== The plugin name id==xxx id==xxx( Note that you can use id Specify to view the status of one or more plug-ins )
2.3.2 To configure
- It can be done by containerd Add... To the configuration file
[plugins]Section to configure the built-in plug-ins , For specific plug-ins, you can use[plugins.id]Independent configuration - The following examples are from official documents :
[plugins] [plugins.cgroups] no_prometheus = false [plugins.cri] stream_server_address = "" stream_server_port = "10010" enable_selinux = false sandbox_image = "k8s.gcr.io/pause:3.6" stats_collect_period = 10 systemd_cgroup = false [plugins.cri.containerd] snapshotter = "overlayfs" [plugins.cri.containerd.default_runtime] runtime_type = "io.containerd.runtime.v1.linux" runtime_engine = "" runtime_root = "" [plugins.cri.containerd.untrusted_workload_runtime] runtime_type = "" runtime_engine = "" runtime_root = "" [plugins.cri.cni] bin_dir = "/opt/cni/bin" conf_dir = "/etc/cni/net.d" [plugins.cri.registry] [plugins.cri.registry.mirrors] [plugins.cri.registry.mirrors."docker.io"] endpoint = ["https://registry-1.docker.io"]
边栏推荐
- Operation flow of UE4 DMX and grandma2 onpc 3.1.2.5
- Kubernetes - Multi cluster management
- 【PHP特性-变量覆盖】函数的使用不当、配置不当、代码逻辑漏洞
- [wp][入门]刷弱类型题目
- 灵魂三问:什么是接口测试,接口测试怎么玩,接口自动化测试怎么玩?
- Anti debugging (basic principles of debugger Design & NT NP and other anti debugging principles)
- 深度学习——LSTM基础
- [wp]bmzclub writeup of several questions
- 面试字节,过关斩将直接干到 3 面,结果找了个架构师来吊打我?
- Timing manager based on C #
猜你喜欢
Clickhouse同步mysql(基于物化引擎)
C语言课设:影院售票管理系统
UI自動化測試從此告別手動下載瀏覽器驅動
A brief introduction to the behavior tree of unity AI

PlasticSCM 企业版Crack

Interview summary: This is a comprehensive & detailed Android interview guide

How about programmers' eyesight| Daily anecdotes

Redis source code analysis: redis cluster
JWT漏洞复现
Multimedia query
随机推荐
[vérification sur le Web - divulgation du code source] obtenir la méthode du code source et utiliser des outils
About the recent experience of writing questions
@Transactional 注解导致跨库查询失效的问题
provide/inject
[groovy] string (string injection function | asBoolean | execute | minus)
[groovy] string (string splicing | multi line string)
Smart pointer shared_ PTR and weak_ Difference of PTR
UI自动化测试从此告别手动下载浏览器驱动
花了2晚,拿到了吴恩达@斯坦福大学的机器学习课程证书
JWT vulnerability recurrence
Analysis of glibc strlen implementation mode
【web审计-源码泄露】获取源码方法,利用工具
[安洵杯 2019]不是文件上传
面试汇总:这是一份全面&详细的Android面试指南
Thread Basics
A brief introduction to the behavior tree of unity AI
Timing manager based on C #
Kubernetes - identity and authority authentication
English essential vocabulary 3400
UI自動化測試從此告別手動下載瀏覽器驅動