当前位置:网站首页>[software reverse - basic knowledge] analysis method, assembly instruction architecture
[software reverse - basic knowledge] analysis method, assembly instruction architecture
2022-07-05 03:37:00 【Black zone (rise)】
Catalog
3、 ... and 、 Assembly instruction architecture
The instructions mainly include :
x86 Application Binary Interface
x64 Application Binary Interface
One 、 brief introduction :
1.1、 The process :
It is mainly about binary machine code ------> Disassembly ------> Assembly code ( Functional analysis )
1.2、 shortcoming :
The decompiled assembly code is missing symbols from the source code 、 Data structure and other information
It is necessary to restore the above information through reverse analysis as much as possible , In order to analyze the original logic and functions of the program
1.3、 Handle
The code structure ( The framework of the program --- trunk )、 data structure ( Branch --- Leaf )、 operation ( The branches of the )
1.4、 classification :
The main method : Static analysis 、 Dynamic analysis .
1.5、 Ideas
Constant discrimination ( Built in constant )、 Data structure characteristics ( Function behavior )、 Network behavior characteristics ( internal data , Algorithm and its operation mechanism )
Two 、 Analysis method :
2.1、 Static analysis
Without executing the code file , A method of static analysis of code , Instead, observe the external characteristics of the code file , It mainly includes : File type analysis and static disassembly 、 Decompile .
File type analysis is mainly used to understand what language the program is written in or what compiler it is compiled with , And whether the program has been encrypted .
In the reverse process , It mainly uses the disassembly tool to view the internal code , Analyze code structure .
2.2、 Dynamic analysis
A method of dynamic analysis of code during the execution of program files , Analyze the code through debugging , Get the status of memory, etc .
In the reverse process , The debugger is usually used to analyze the internal structure and implementation principle of the program .
Common reverse goals are Windows、Linux Under the platform x86、x64 Binary executable
3、 ... and 、 Assembly instruction architecture
3.1、 brief introduction :
The processor architecture of reverse analyzers is usually Intel framework
therefore ,Intel x86 and x64 Command system : Including register group 、 Instruction set 、 Call specification
3.2、x86 Command system
Register group
General registers : Include EAX、EBX、ECX、EDX、ESI、EBP、ESP
Instruction pointer register (EIP): Point to the current instruction to be executed
Status identification register (EFLAGS): Control the branch jump of the program according to the value of the state in the state identification register .
Segment register :CS、DS、SS、ES、FS、GS. In the current operating system ,CS、DS、SS and ES The base address of the segment register of is usually 0.
Special register : Include DR0-DR7, Used to set hardware breakpoints .
Assembly instruction set
There are two grammatical notations :Intel and AT&T.
Common reverse analysis tools IDA Pro、Ollydbg and MASM Usually use Intel Notation , and UNIX Tools on the system gcc Usually comply with AT&T Notation .Intel Notation occupies a dominant position in practice , It is also the notation used in this book .
Intel Assembly language program statement format :
Action items Destination operands , Source operands
among , Operation items are generally some instructions in assembly language , such as add( Add )、mov( Move ) Such as instruction . The destination operand and the source operand are generally registers 、 Memory address or immediate number .
The instructions mainly include :
(1) Data transfer instructions ( The most frequently used instructions )
Format :MOV DEST,SRC
function : Put a byte 、 Word or doubleword from source operand SRC Passed to destination operand DEST.(2) Stack operation and function call
Stack operations include stacking (PUSH) And out of the stack (POP)
Function call and return pass through CALL/RET Instructions implement .CALL The instruction will change the current EIP Save to stack ,RET Instruction reads the stack , Get the return address .
(3) Count 、 Logical operation instructions
Such as add、sub、mul、div、and、or、xor etc.
(4) Control transfer instructions
cmp: Subtract two operands , Modify the status identification register .
test: Perform and operations on two operands , Modify the status identification register .
jmp: Force jump command .
jcc: Conditional jump instructions , Include jz、jnz etc. .
(5) Special instructions
Some special instructions :
int3 Instructions : The corresponding bytecode is 0xcc, It is mainly used to set soft breakpoints .
int 0x80:Linux In the system 32 Bit system call instruction .
x86 Application Binary Interface
Call convention refers to a series of rules , It specifies how function calls are made at the machine level . For a particular system , It is composed of application binary interface (Application Binary Interface,ABI) Defined .
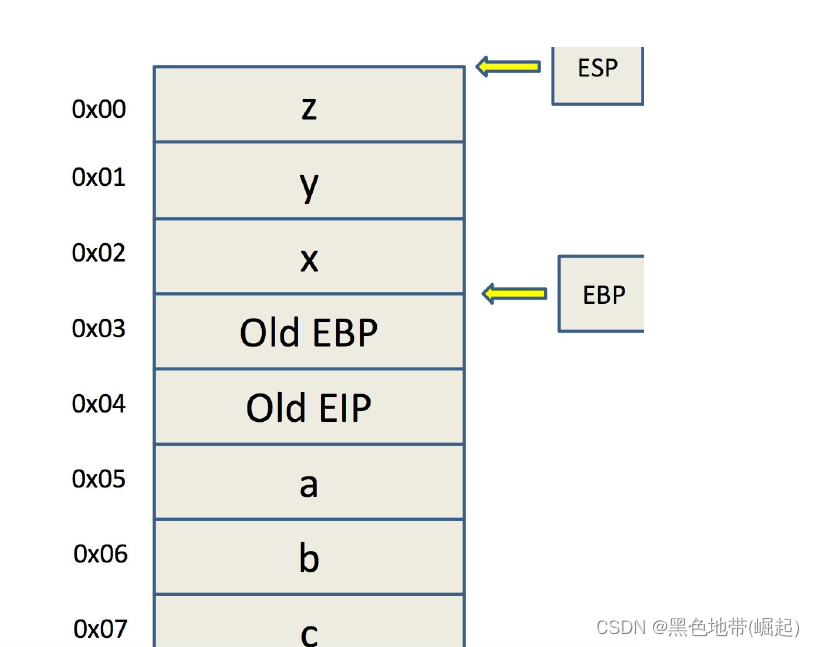
When a function call occurs , First, add the parameters to the stack from right to left , And then through call Instruction pushes the return address of a function onto the stack . Last , In the new function, the previous ebp Save to stack , meanwhile esp Will subtract a certain value , Leave some stack space for local variables .
3.3、x64 Command system
x64 Instruction system and x86 The instruction system is roughly the same , Here we mainly explain the differences
Register group
RAX、RBX、RDX、RCX、RBP、RDI、RSI、RSP,R8~R15.
System call instructions
syscall/sysret yes Linux 64 System call mode of bit operating system .
x64 Application Binary Interface
Microsoft’s x64 ABI:
It is mainly used for Windows In the operating system 64 Bit program
Microsoft’s x64 ABI Before 4 A parameter passes through the register RCX、RDX、R8、R9 Pass on , The rest is passed through the stack , But it will be reserved on the stack 0x20 Bytes of space is used before temporary saving 4 Parameters , The return value is RAX.
Corresponding function call form :RAX func(RCX, RDX, R8, R9, [rsp+0x20], [rsp+0x28], ……)
SysV x64 ABI:
It is mainly used for Linux、BSD、MAC Etc. in the operating system 64 Bit program
SysV x64 ABI Before 6 Parameters (RDI、RSI、RDX、RCX、R8、R9) Pass... By register , The rest is passed through the stack , There is no front on the stack 6 Parameters reserve space , The return value is RAX register .
Corresponding function call form :RAX func(RDI, RSI, RDX, RCX, R8, R9, [RSP+8], [RSP+0x10], ……)
边栏推荐
- Three line by line explanations of the source code of anchor free series network yolox (a total of ten articles, which are guaranteed to be explained line by line. After reading it, you can change the
- Performance of calling delegates vs methods
- MySQL winter vacation self-study 2022 11 (10)
- Quick start of UI component development of phantom engine [umg/slate]
- Leetcode42. connect rainwater
- SQL injection exercise -- sqli Labs
- The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
- A brief introduction to the behavior tree of unity AI
- Solve the problem that sqlyog does not have a schema Designer
- Subversive cognition: what does SRE do?
猜你喜欢
![[2022 repair version] community scanning code into group activity code to drain the complete operation source code / connect the contract free payment interface / promote the normal binding of subordi](/img/ab/e90177c22edc77238250e56c1a0a46.jpg)
[2022 repair version] community scanning code into group activity code to drain the complete operation source code / connect the contract free payment interface / promote the normal binding of subordi
New interesting test applet source code_ Test available
![Quick start of UI component development of phantom engine [umg/slate]](/img/8b/cee092ec1ab105a7e234143bd56861.jpg)
Quick start of UI component development of phantom engine [umg/slate]
Talk about the SQL server version of DTM sub transaction barrier function

This + closure + scope interview question
![[system security] ten thousand words summary system virtualization container bottom layer principle experiment](/img/c6/1bdb29a0acb0739f67b882fa6b3b47.jpg)
[system security] ten thousand words summary system virtualization container bottom layer principle experiment
【web審計-源碼泄露】獲取源碼方法,利用工具
Anchor free series network yolox source code line by line explanation Part 2 (a total of 10, ensure to explain line by line, after reading, you can change the network at will, not just as a participan
![[groovy] string (string type variable definition | character type variable definition)](/img/d8/f02e6ad760fb039873718ff7a97b0a.jpg)
[groovy] string (string type variable definition | character type variable definition)
【web源码-代码审计方法】审计技巧及审计工具
随机推荐
有个疑问 flink sql cdc 的话可以设置并行度么, 并行度大于1会有顺序问题吧?
[wp]bmzclub几道题的writeup
Logstash、Fluentd、Fluent Bit、Vector? How to choose the appropriate open source log collector
[web Audit - source code disclosure] obtain source code methods and use tools
Ubantu disk expansion (VMware)
[安洵杯 2019]不是文件上传
【web审计-源码泄露】获取源码方法,利用工具
有個疑問 flink sql cdc 的話可以設置並行度麼, 並行度大於1會有順序問題吧?
A brief introduction to the behavior tree of unity AI
Ask, does this ADB MySQL support sqlserver?
【PHP特性-变量覆盖】函数的使用不当、配置不当、代码逻辑漏洞
Sqoop installation
Monitoring web performance with performance
How to make the listbox scroll automatically when adding a new item- How can I have a ListBox auto-scroll when a new item is added?
El tree whether leaf node or not, the drop-down button is permanent
Learning notes of raspberry pie 4B - IO communication (I2C)
Technology sharing swift defense programming
Dart series: collection of best practices
Devtools的简单使用
Anchor free series network yolox source code line by line explanation Part 2 (a total of 10, ensure to explain line by line, after reading, you can change the network at will, not just as a participan