当前位置:网站首页>开源 | HMGNN:异构小图神经网络及其在拉新裂变风控场景的应用
开源 | HMGNN:异构小图神经网络及其在拉新裂变风控场景的应用
2020-11-09 10:50:00 【InfoQ】
版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://www.infoq.cn/article/UVkmZNHqYbUKgWdF9wXv?utm_source=rss&utm_medium=article
边栏推荐
- How does pipedrive support quality publishing with 50 + deployments per day?
- 自然语言处理(NLP)路线图 - kdnuggets
- Operation 2020.11.7-8
- Exception capture and handling in C + +
- How to do thread dump analysis in Windows Environment
- 1450. Number of students doing homework at a given time
- This program cannot be started because msvcp120.dll is missing from your computer. Try to install the program to fix the problem
- File queue in Bifrost (1)
- C++之异常捕获和处理
- EasyNTS上云网关设备在雪亮工程项目中的实战应用
猜你喜欢

Ten year itch of programmer
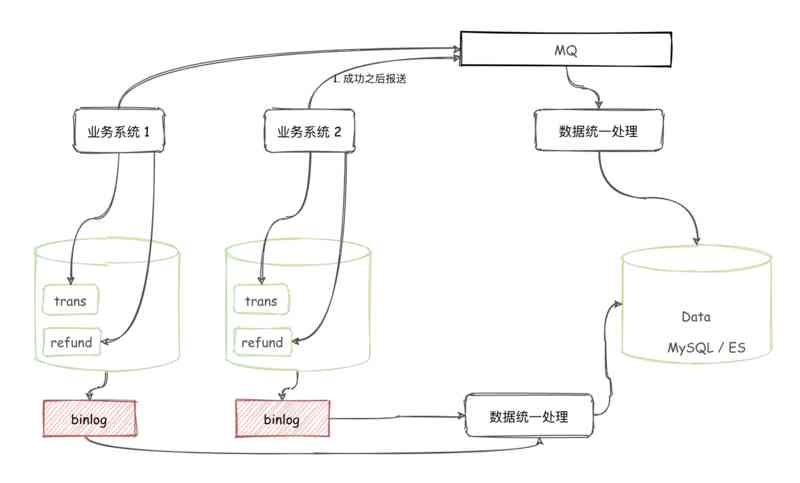
Have you ever thought about why the transaction and refund have to be split into different tables
JT-day09

1450. Number of students doing homework at a given time

搭建全分布式集群全过程

商品管理系统——商品新增本地保存实现部分

5 个我不可或缺的开源工具

Detailed analysis of OpenGL es framework (8) -- OpenGL es Design Guide

FC 游戏机的工作原理是怎样的?

3.你知道计算机是如何启动的吗?
随机推荐
How to do thread dump analysis in Windows Environment
结合阿里云 FC 谈谈我对 FaaS 的理解
1450. 在既定时间做作业的学生人数
Tips in Android Development: requires permission android.permission write_ Settings solution
Linked list
range_sensor_layer
EasyNTS上云网关设备在雪亮工程项目中的实战应用
商品管理系统——商品新增本地保存实现部分
Why don't we use graphql? - Wundergraph
When we talk about data quality, what are we talking about?
[Python从零到壹] 五.网络爬虫之BeautifulSoup基础语法万字详解
OSChina 周一乱弹 —— 程序媛的青春
Rainbow sorting | Dutch flag problem
Dark网站的后端为什么选择F#? - darklang
B. protocal has 7000eth assets in one week!
卧槽,这年轻人不讲武德,应届生凭“小抄”干掉5年老鸟,成功拿到字节20Koffer
3.你知道计算机是如何启动的吗?
Android emulator error: x86 emulation currently requires hardware acceleration solution
Detailed analysis of OpenGL es framework (8) -- OpenGL es Design Guide
Linked blocking queue based on linked list