当前位置:网站首页>Use onedns to perfectly solve the optimization problem of office network
Use onedns to perfectly solve the optimization problem of office network
2022-07-07 17:40:00 【Lin [email protected]】
Preface
Enterprise Office , Do you often encounter the following problems :
- Some inexplicable applications are installed on your computer , Slow down the computer , Affect office efficiency ;
- There are always some advertising pop ups on the computer desktop from time to time , It's annoying ;
- There are other people who always open websites forbidden by the company during working hours , Like web games 、 Gambling websites, etc ;
- The company server always restarts inexplicably in the middle of the night , Suspected of being “ Mining in bad faith ”, But I can't find the specific infected file ……
It's a common problem , Probably DNS Hijack or encounter CSRF attack .
DNS hijacked
DNS Hijacking is domain name hijacking , By matching the original domain name to IP Address to replace , This allows users to access the wrong website , Or an attack that prevents users from accessing the website normally .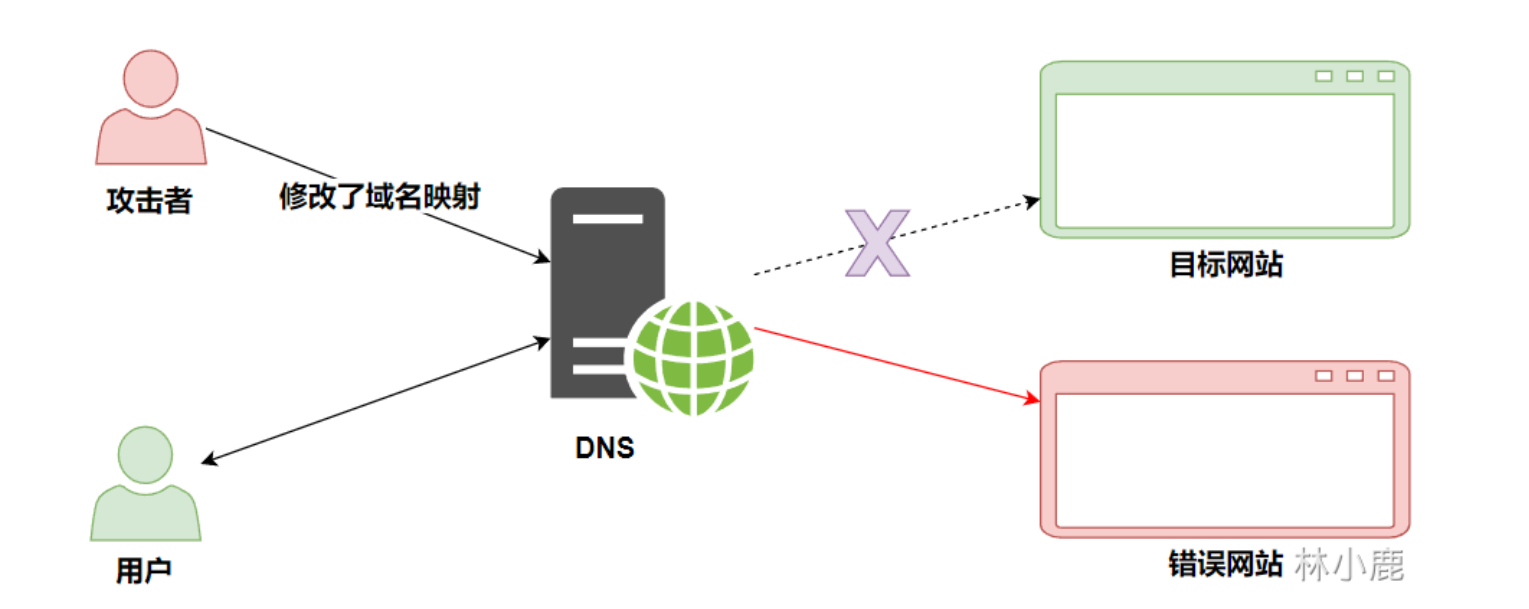
CSRF attack
CSRF, Cross-site request forgery ( The full English name is Cross-site request forgery), It is a method of holding a user to log in at the current time Web An attack method that performs unintended operations on an application .
Example :
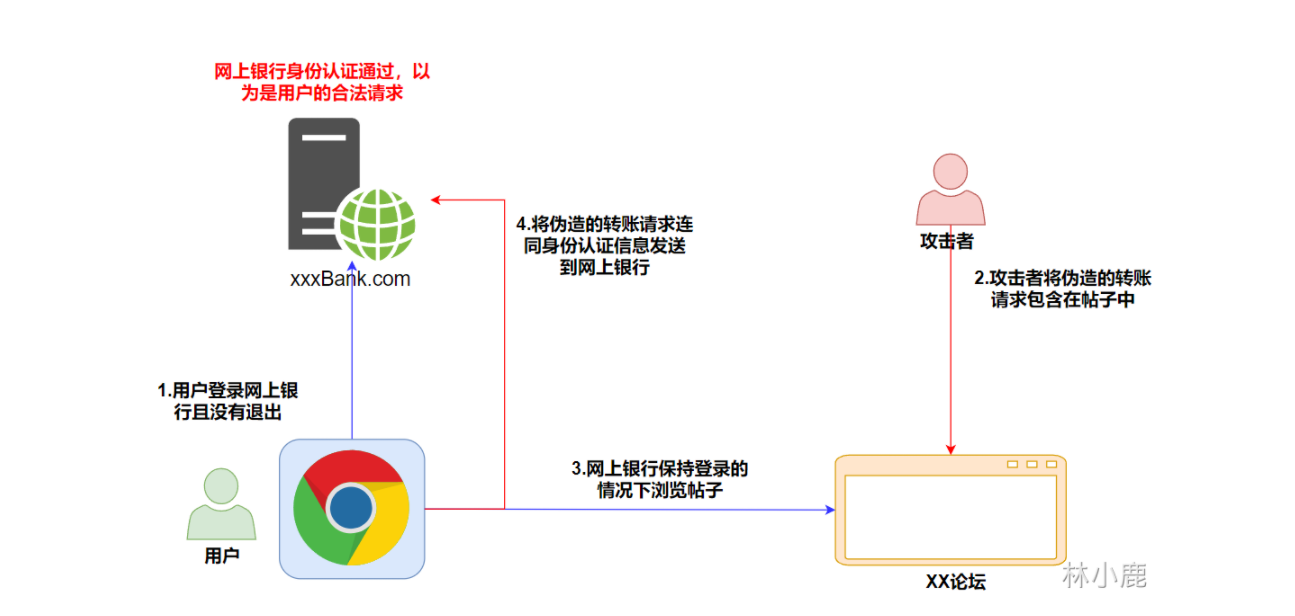
- The user logs in to the bank , Didn't quit , The browser contains the user's identity authentication information in the bank .
- The attacker will falsify the transfer request , Included in the post .
- When the user keeps logging in the bank website , Browse posts .
- Fake transfer request together with authentication information , Send it to the bank website .
- Bank websites see authentication information , Think it is the legitimate operation of the user , Finally, it causes the loss of users' funds .
How to solve DNS Hijacking and avoidance CSRF attack ?
Method 1
solve DNS hijacked :
Directly through IP Address visit website , To avoid the DNS hijacked
Because domain name hijacking can only be carried out within a specific network , Therefore, some advanced users can make DNS Point to the normal domain name server to achieve normal access to the target web address , For example, computers are preferred DNS The address of the server is fixed as 8.8.8.8.
avoid CSRF attack
- Check Referer Field :HTTP In the header Referer The field records the HTTP The source address of the request . In general , Requests to access a security restricted page come from the same website , And if hackers want to do it CSRF attack , He can only build requests on his own website . therefore , Can be verified by Referer It's worth defending CSRF attack .
- Add validation token: stay HTTP Was added a request in the form of randomly generated parameter token, And build an interceptor on the server side to verify this token, If not in the request token perhaps token The content is not correct , Think it might be CSRF Attack and reject the request .
- Sensitive operation multiple check : For some sensitive operations , In addition to verifying the user's authentication information , You can also confirm by email 、 The verification code confirms multiple verification in this way .
Method 2
install OneDNS
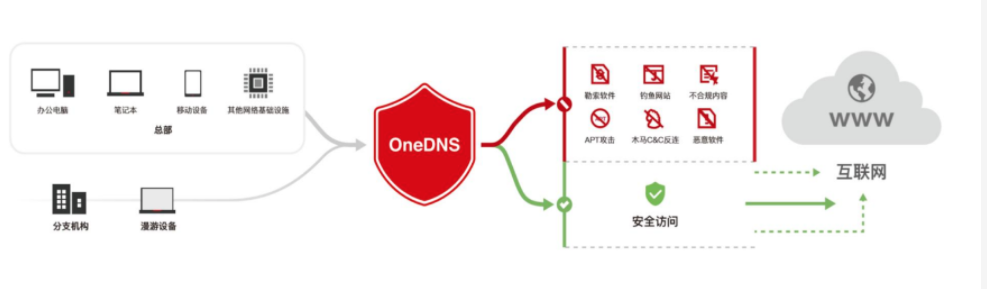
OneDNS Protection principle
OneDNS Get the requested domain name , Real time collision with cloud intelligence base , Secure domain name stable and efficient resolution , Return resolution IP Give users access ; detected Malicious domain names are not resolved , Direct interception , Return to the interception page , Achieve security protection .
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-kuQywXzY-1656981370210)( Use OneDNS Perfectly solve the problem of office network optimization .assets/image-20220704220827948.png)]](/img/38/c6645343037a28a0ff4274da254473.png)
OneDNS install
It's easy to install , Direct will DNS The address to OneDNS Of IP address , Interception upon access .
版权声明
本文为[Lin [email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/188/202207071534044468.html
边栏推荐
猜你喜欢
【解惑】App处于前台,Activity就不会被回收了?
简单的loading动画
![[re understand the communication model] the application of reactor mode in redis and Kafka](/img/d6/8a6124bb7f96be92bf8c6d3aeef12d.png)
[re understand the communication model] the application of reactor mode in redis and Kafka
Share the latest high-frequency Android interview questions, and take you to explore the Android event distribution mechanism
状态模式 - Unity(有限状态机)
基于百度飞浆平台(EasyDL)设计的人脸识别考勤系统
datepicket和timepicket,日期、时间选择器的功能和用法
目标管理【管理学之十四】
Examen des lois et règlements sur la sécurité de l'information

麒麟信安云平台全新升级!
随机推荐
Function and usage of calendar view component
面试官:页面很卡的原因分析及解决方案?【测试面试题分享】
阿富汗临时政府安全部队对极端组织“伊斯兰国”一处藏匿点展开军事行动
[distributed theory] (II) distributed storage
yolo训练过程中批量导入requirments.txt中所需要的包
Dateticket and timeticket, functions and usage of date and time selectors
第3章业务功能开发(实现记住账号密码)
【重新理解通信模型】Reactor 模式在 Redis 和 Kafka 中的应用
数字化转型的主要工作
[tpm2.0 principle and Application guide] Chapter 1-3
【网络攻防原理与技术】第7章:口令攻击技术 第8章:网络监听技术
DatePickerDialog and trimepickerdialog
How to choose the appropriate automated testing tools?
Mysql 索引命中级别分析
使用OneDNS完美解决办公网络优化问题
基于PyTorch利用CNN对自己的数据集进行分类
LeetCode 515(C#)
本周小贴士#134:make_unique与私有构造函数
到底有多二(Lua)
redis主从、哨兵主备切换搭建一步一步图解实现