当前位置:网站首页>What is weak reference? What are the weak reference data types in ES6? What are weak references in JS?
What is weak reference? What are the weak reference data types in ES6? What are weak references in JS?
2022-07-06 01:15:00 【imkaifan】
Weak reference :
WeakSet The objects in are all weak references , Garbage collection mechanism does not consider WeakSet Reference to the object , in other words , If no other object references that object , Then the garbage collection mechanism will automatically reclaim the memory occupied by the object , Regardless of whether the object still exists in WeakSet In .
This is because the garbage collection mechanism depends on the reachability of objects (reachability) To determine recycling , If the object can still be accessed , The garbage collection mechanism will not free this memory . After you finish using this value , Sometimes I forget to dereference , Causes memory not to be released , This can lead to memory leaks .WeakSet The quotation in it , Not included in the garbage collection mechanism , So there is no such problem . therefore ,WeakSet Suitable for temporary storage of a group of objects , And storing information bound to objects . As long as these objects disappear outside , It's in WeakSet The references in it will disappear automatically .
Because of the above characteristics ,WeakSet Members of are not suitable for reference , Because it will disappear at any time . in addition , because WeakSet How many members are there inside , Depends on whether the garbage collection mechanism is running , It is likely that the number of members before and after running is different , And when the garbage collection mechanism will run is unpredictable , therefore ES6 Regulations WeakSet Non traversal . And of course not size attribute , Because the amount of data is also uncertain .
These features also apply to WeakMap structure
边栏推荐
- Some features of ECMAScript
- Illustrated network: the principle behind TCP three-time handshake, why can't two-time handshake?
- Zhuhai laboratory ventilation system construction and installation instructions
- 关于#数据库#的问题:(5)查询库存表中每本书的条码、位置和借阅的读者编号
- Five challenges of ads-npu chip architecture design
- Synchronized and reentrantlock
- General operation method of spot Silver
- golang mqtt/stomp/nats/amqp
- Live broadcast system code, custom soft keyboard style: three kinds of switching: letters, numbers and punctuation
- How to extract MP3 audio from MP4 video files?
猜你喜欢

General operation method of spot Silver
Unity | two ways to realize facial drive
After Luke zettlemoyer, head of meta AI Seattle research | trillion parameters, will the large model continue to grow?
关于softmax函数的见解
Test de vulnérabilité de téléchargement de fichiers basé sur dvwa

The third season of ape table school is about to launch, opening a new vision for developers under the wave of going to sea
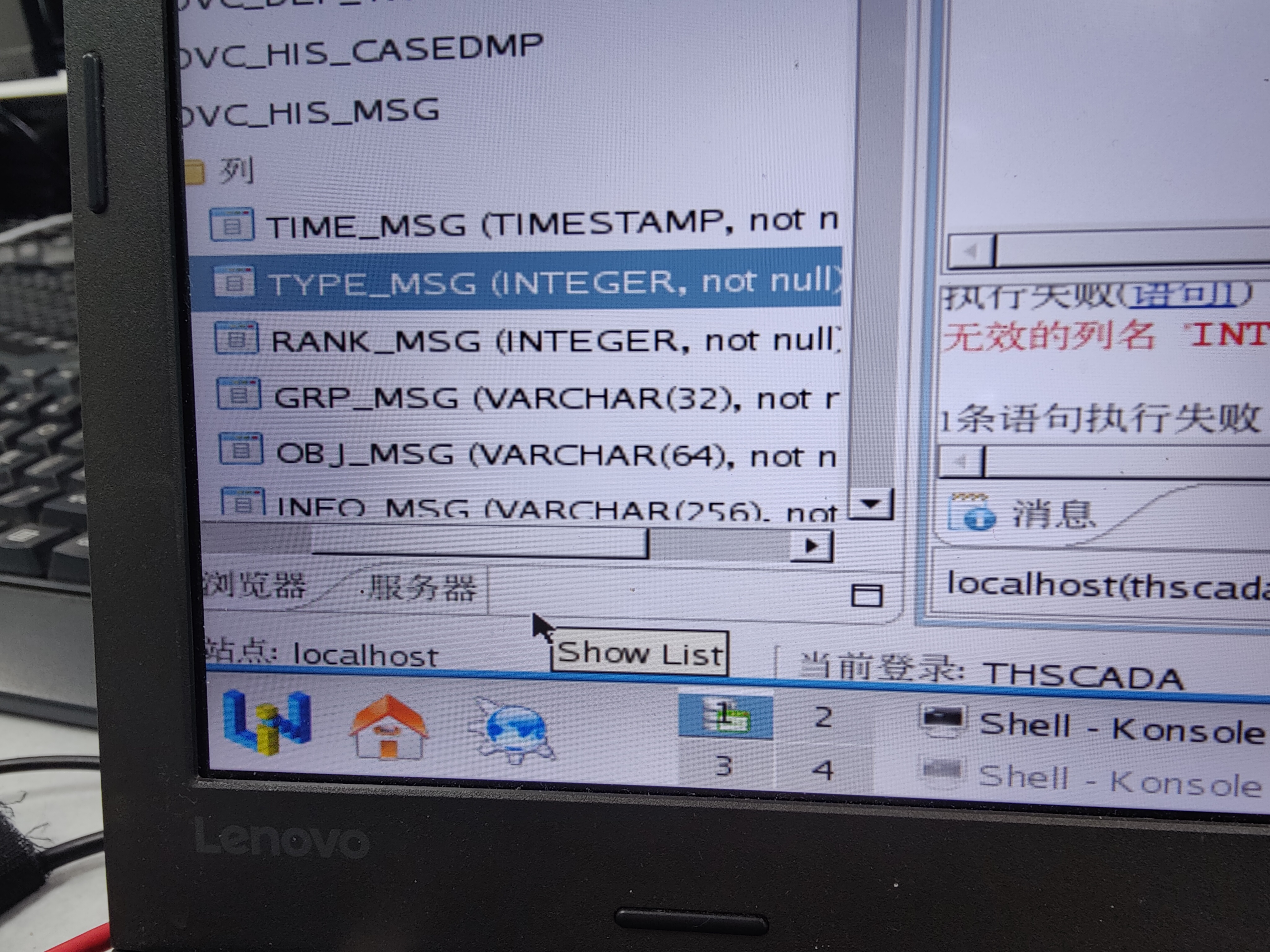
有谁知道 达梦数据库表的列的数据类型 精度怎么修改呀

Questions about database: (5) query the barcode, location and reader number of each book in the inventory table
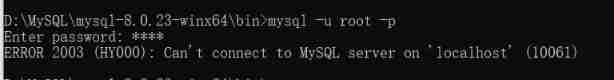
About error 2003 (HY000): can't connect to MySQL server on 'localhost' (10061)

程序员搞开源,读什么书最合适?
随机推荐
ORA-00030
Pbootcms plug-in automatically collects fake original free plug-ins
Overview of Zhuhai purification laboratory construction details
VMware Tools installation error: unable to automatically install vsock driver
Cve-2017-11882 reappearance
How to get the PHP version- How to get the PHP Version?
WordPress collection plug-in automatically collects fake original free plug-ins
DD's command
Dede collection plug-in free collection release push plug-in
ORA-00030
Getting started with devkit
IP storage and query in MySQL
Recommended areas - ways to explore users' future interests
网易智企逆势进场,游戏工业化有了新可能
关于#数据库#的问题:(5)查询库存表中每本书的条码、位置和借阅的读者编号
esxi的安装和使用
Zhuhai's waste gas treatment scheme was exposed
[day 30] given an integer n, find the sum of its factors
Dynamic programming -- linear DP
3D model format summary