当前位置:网站首页>MySQL grants the user the operation permission of the specified content
MySQL grants the user the operation permission of the specified content
2022-07-06 15:57:00 【Flame car】
Grant users a library 、 The permissions of a table or a column can be easily found (GRANT), But there is a problem: how to grant the user the operation permission of the specified content ??
A problem of database experiment :
Suppose a user is CS Department managers , The authority that needs to be given to him only includes adding, deleting, checking and modifying the information of the computer department teacher , How to achieve ?
At first, I thought it was the same as specifying a column , Nothing more than specifying a certain line . Then Baidu spent a long time and found that it didn't say what to do at all ? Then it's time to go to bed , Suddenly thought of whether to re create a table and specify the rows of the things on that table ( Department of Computer Science ) Let it go ?
Come here , I suddenly remembered that one of the videos given by the teacher was view operation ( Why didn't I see it ???), I wonder if I should map the table to the view first , Then give the permission of the view to the user ? Then I checked again , You can modify the original table by modifying the view , That is to say, it really does .
summary : The user is not directly authorized to operate the specified content GRANT, You need to create a view through conditions and then grant users the operation permission of the view to achieve this effect .
Specific operation :
CREATE VIEW cs_instructor AS
SELECT *
FROM instructor
WHERE dept_name = 'Comp. Sci.'
Create a view , Inside is the information of the computer department teacher .
GRAND SELECT ON cs_instructor TO 'name'@'localhost';
In this way, the permission is granted to the user ,TO The following single quotation mark can be added or not .
Then you may have to modify the permissions of the view , hold Definer Change it to Invoker, But I don't know why I use it instead Definer To open ……
边栏推荐
- C 基本语法
- [exercise-1] (UVA 673) parentheses balance/ balanced brackets (stack)
- Penetration testing (5) -- a collection of practical skills of scanning King nmap and penetration testing tools
- Gartner:关于零信任网络访问最佳实践的五个建议
- Information security - threat detection - detailed design of NAT log access threat detection platform
- 动态规划前路径问题
- HDU-6025-Coprime Sequence(女生赛)
- 毕业才知道IT专业大学生毕业前必做的1010件事
- 渗透测试 ( 1 ) --- 必备 工具、导航
- 【练习-7】Crossword Answers
猜你喜欢
![[exercise-7] crossover answers](/img/66/3dcba2e70a4cd899fbd78ce4d5bea2.png)
[exercise-7] crossover answers
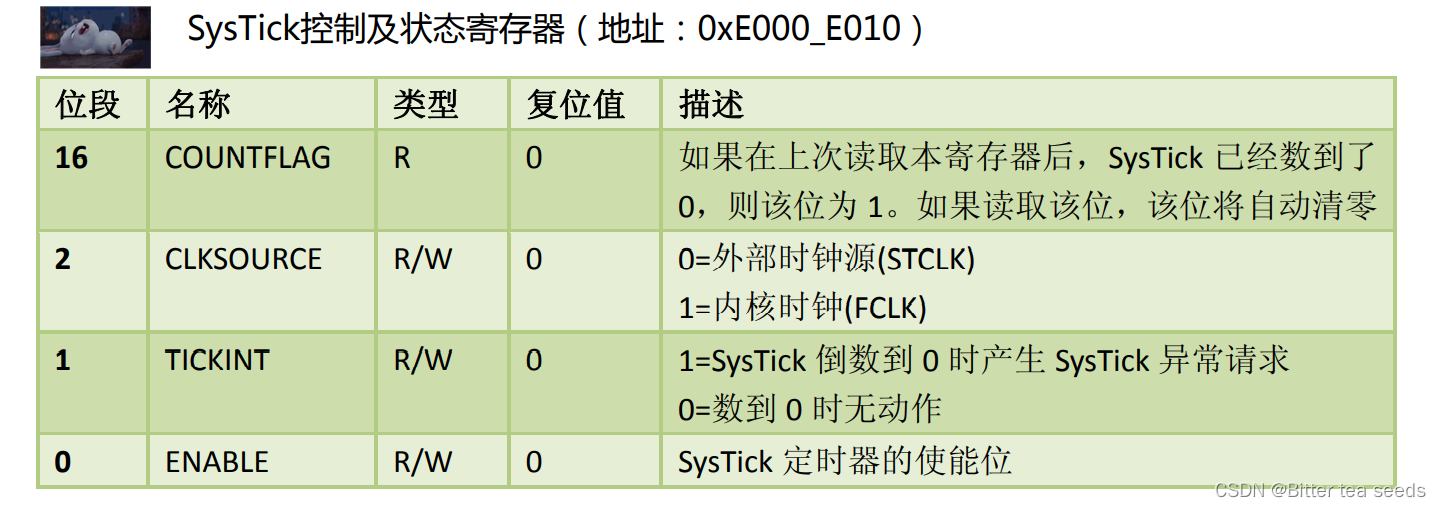
Learning record: understand systick system timer and write delay function

C语言必背代码大全

信息安全-威胁检测引擎-常见规则引擎底座性能比较
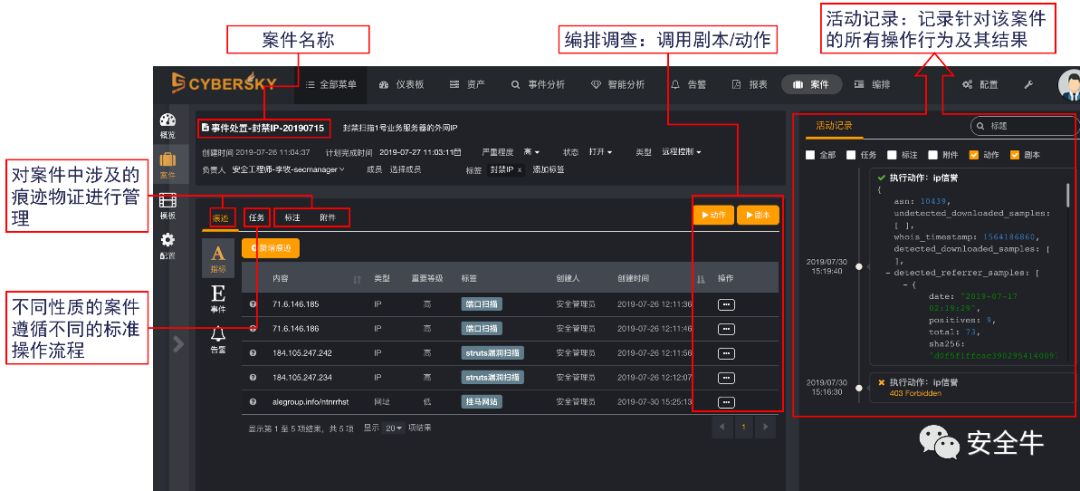
Information security - Analysis of security orchestration automation and response (soar) technology
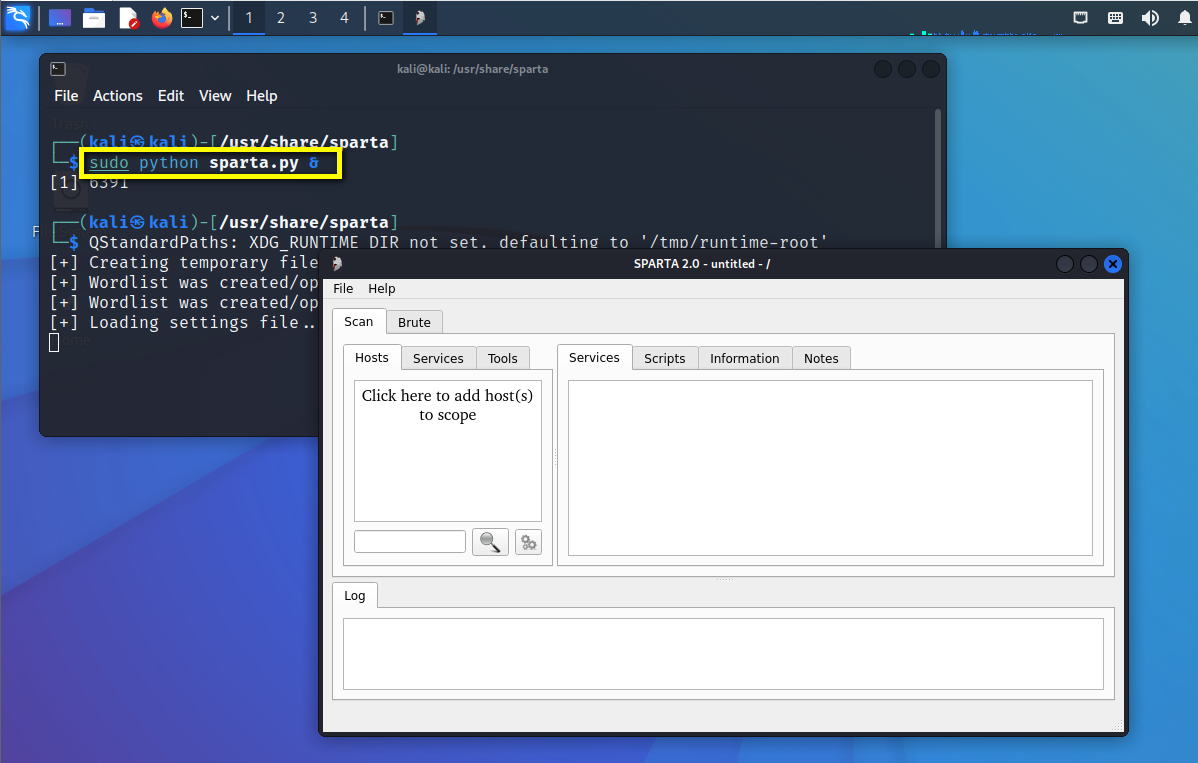
Essai de pénétration (1) - - outils nécessaires, navigation

信息安全-安全编排自动化与响应 (SOAR) 技术解析
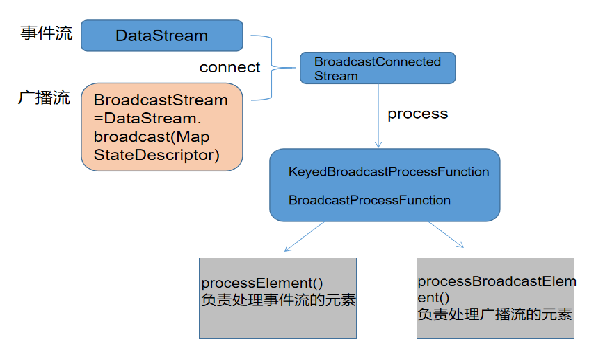
信息安全-威胁检测-flink广播流BroadcastState双流合并应用在过滤安全日志
用C语言写网页游戏

Information security - threat detection engine - common rule engine base performance comparison
随机推荐
基于web的照片数码冲印网站
Market trend report, technical innovation and market forecast of geosynthetic clay liner in China
通俗地理解什么是编程语言
MySQL import database error [err] 1273 - unknown collation: 'utf8mb4_ 0900_ ai_ ci’
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
Cost accounting [20]
X-Forwarded-For详解、如何获取到客户端IP
The most complete programming language online API document
Nodejs+vue网上鲜花店销售信息系统express+mysql
Opencv learning log 31 -- background difference
Optimization method of path problem before dynamic planning
信息安全-史诗级漏洞Log4j的漏洞机理和防范措施
C语言数组的概念
Cost accounting [14]
Penetration test (1) -- necessary tools, navigation
Cost accounting [23]
想应聘程序员,您的简历就该这样写【精华总结】
差分(一维,二维,三维) 蓝桥杯三体攻击
cs零基础入门学习记录
STM32 how to use stlink download program: light LED running light (Library version)