当前位置:网站首页>Daily question brushing plan-2-13 fingertip life
Daily question brushing plan-2-13 fingertip life
2022-07-06 02:54:00 【Konjak_ Konnyaku】
「 This is my participation 2022 For the first time, the third challenge is 25 God , Check out the activity details : 2022 For the first time, it's a challenge
BC140 KiKi Design class inheritance
describe
KiKi Understand that inheritance can make code reuse , He now defines a base class shape, Private data is coordinate point x,y, Derived from it Rectangle Classes and Circle class , They all have member functions GetArea() Find the area . Derived class Rectangle Class has data : The length and width of the rectangle ; Derived class Circle Class has data : The radius of the circle .Rectangle Class derives square Square class , Define and test . Enter three sets of data , They are the length and width of the rectangle 、 The radius of the circle 、 The side length of a square , Output three groups of data , They are rectangles 、 round 、 The square area . PI by 3.14 Calculation .
Input description :
Enter three lines ,
The first line is the length and width of the rectangle ,
The second line is the radius of the circle ,
The third line is the side length of the square .
Output description :
Three elements , They are rectangles 、 round 、 The square area .
Example 1
Input :
Copy
Output :
Copy
Function knowledge
1. Functions cannot be nested , But you can nest calls
2.printf() : Returns the number of characters printed on the screen , If an error occurs , Return negative
3.scanf() : Returns the number of valid characters successfully read
4. Functions can be accessed in a chain
5. You can use global variables to pass parameters
6. Functions can have no return value
7. The definition of a function can be placed anywhere , The declaration of a function must be placed before the use of the function
- The declaration of a function simply tells the compiler the type of the return value of the function 、 Function name and parameters required by the function , The function definition is to explain how the function is implemented
- Formal parameters are instantiated only when the function is called , To open up memory space
- When passing parameters, whether by value or pointer , All the formal parameters get is a copy of the argument
- Formal parameters are instantiated only when the function is called , To open up memory space
- main The position of the function can be anywhere , Top note, but if you call those functions before the main function , Must be in main The header file that contains the life of the called function or the called function before the function .
- Variables defined in compound statements within a function can only be used in compound statements , Not valid within the scope of this function
- The formal parameters of a function are generally passed by pressing the stack of parameters , The formal parameters in the function are saved in the stack
- Different functions belong to different scopes , Therefore, variables with the same name defined in different functions will not conflict
- Variables defined in functions , It's called a local variable , Local variables can only be used in the functions they define , Variables defined within a function are valid only within the scope of this function
边栏推荐
- How to read excel, PDF and JSON files in R language?
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15
- Differences and usage scenarios between TCP and UDP
- codeforces每日5题(均1700)-第六天
- [Digital IC manual tearing code] Verilog asynchronous reset synchronous release | topic | principle | design | simulation
- Shell script updates stored procedure to database
- PMP practice once a day | don't get lost in the exam -7.5
- OCR文字识别方法综述
- 【若依(ruoyi)】启用迷你导航栏
- A copy can also produce flowers
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 10](/img/89/1c2f98973b79e8d181c10d7796fbb5.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 10

codeforces每日5題(均1700)-第六天
Gifcam v7.0 minimalist GIF animation recording tool Chinese single file version
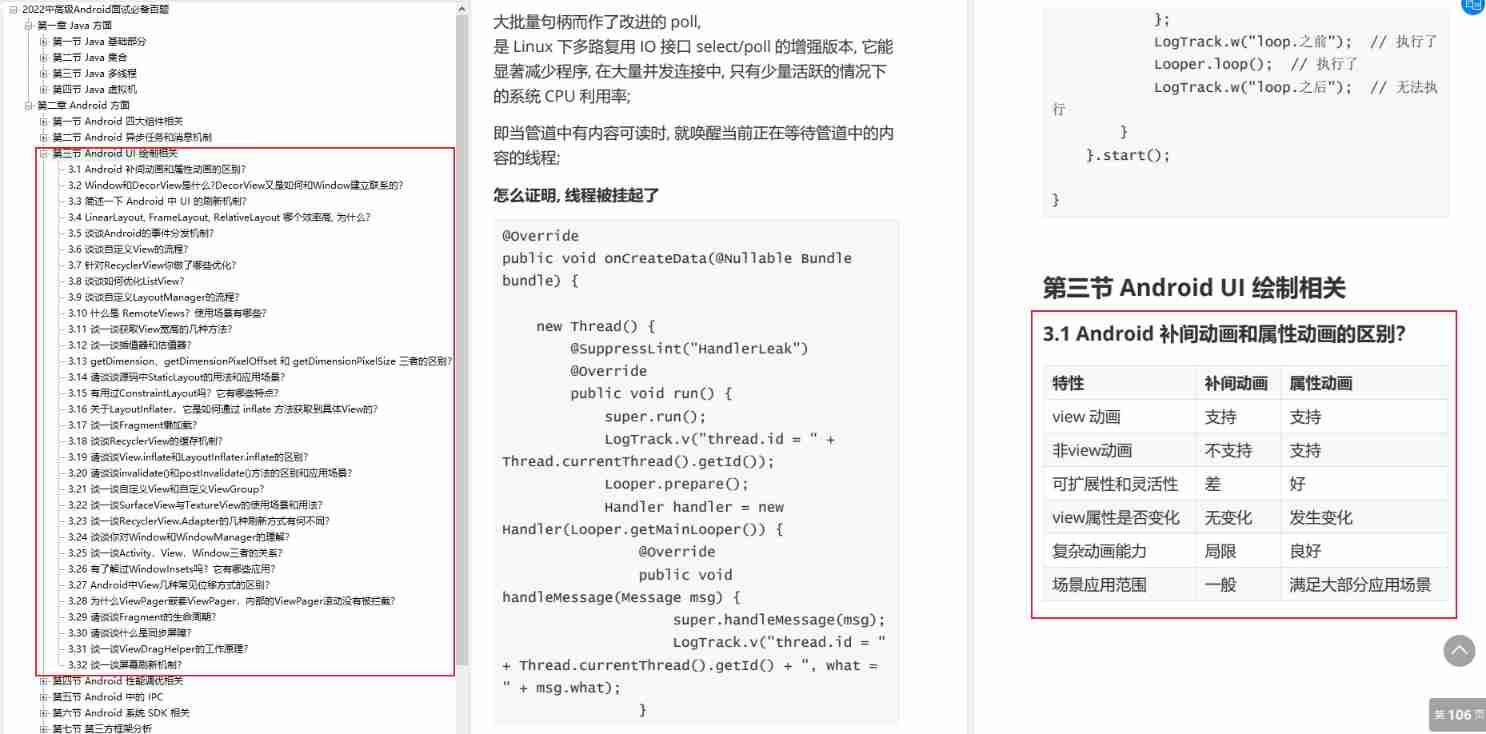
I sorted out a classic interview question for my job hopping friends
Referenceerror: primordials is not defined error resolution
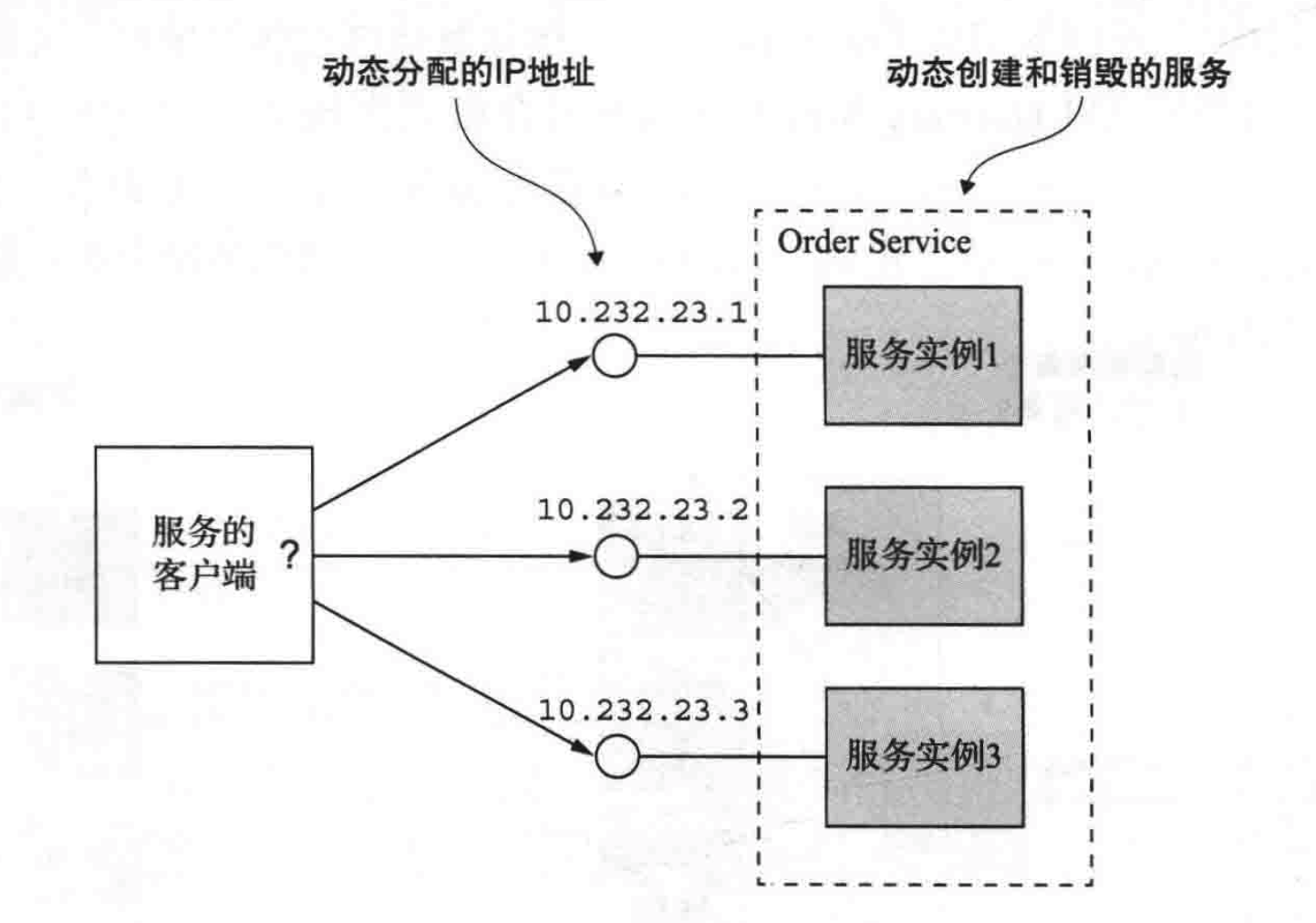
微服务注册与发现
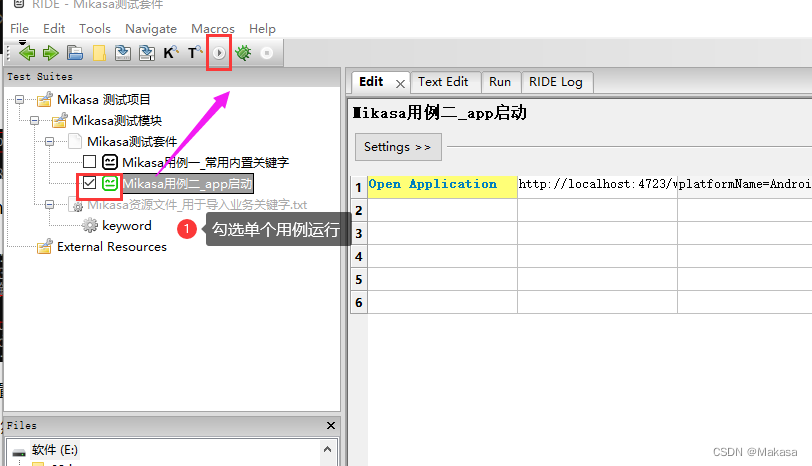
Introduction to robotframework (II) app startup of appui automation
微软语音合成助手 v1.3 文本转语音工具,真实语音AI生成器

Codeforces 5 questions par jour (1700 chacune) - jour 6
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22](/img/e0/21367eeaeca10c0a2f2aab3a4fa1fb.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22
随机推荐
How to read excel, PDF and JSON files in R language?
有没有完全自主的国产化数据库技术
Introduction to robotframework (II) app startup of appui automation
Linear programming matlab
Li Kou today's question -729 My schedule I
#PAT#day10
CobaltStrike-4.4-K8修改版安装使用教程
【指针训练——八道题】
Self made CA certificate and SSL certificate using OpenSSL
[ruoyi] enable Mini navigation bar
Redis delete policy
会员积分营销系统操作的时候怎样提升消费者的积极性?
解决:AttributeError: ‘str‘ object has no attribute ‘decode‘
C # create self host webservice
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15
Introduction to robotframework (I) brief introduction and use
4. File modification
原型图设计
DDoS "fire drill" service urges companies to be prepared
XSS challenges bypass the protection strategy for XSS injection