当前位置:网站首页>What does security capability mean? What are the protection capabilities of different levels of ISO?
What does security capability mean? What are the protection capabilities of different levels of ISO?
2022-07-07 01:23:00 【Xingyun housekeeper】
At present, China's classified protection is divided into five levels , Different levels of security protection requirements are determined for different levels . Now let's talk about what security protection capability means ? What are the protection capabilities of different levels of ISO ?
What does security capability mean ?
《 Information security technology basic requirements for network security level protection 》 Security protection capability is defined as the ability to resist threats 、 The extent to which safety incidents are found and the previous state can be restored after damage .
What are the protection capabilities of different levels of ISO ?
The basic safety protection capabilities of objects protected at different levels are as follows :
1、 Level 1 security protection capability : It should be able to protect against... From individuals 、 Malicious attacks by threat sources with few resources 、 Ordinary natural disasters , And the damage to key resources caused by other threats of considerable harm , After their own damage , It can restore some functions .
2、 Second level security protection capability : It should be able to protect the system from small external organizations 、 Threat sources with a small amount of resources launch malicious attacks , General natural disasters 、 And other important resource damage caused by threats with a considerable degree of harm , After the system is damaged , It can restore some functions within a period of time .
3、 Level 3 security protection capability : It shall be able to protect the system from external organized groups under a unified security policy 、 Threat sources with rich resources launch malicious attacks 、 More serious natural disasters 、 And other major resource damage caused by threats with a considerable degree of harm , Be able to find security vulnerabilities and security time , After the system is damaged , It can recover most functions quickly .
4、 Level 4 security protection capability : It should be able to protect against... From the national level under the unified security policy 、 Of hostile organizations 、 Malicious attacks launched by threat sources with rich resources 、 Serious natural disasters , And the damage to resources caused by other threats of considerable harm , Be able to find out in time 、 Detect security events that detect attacks , After their own damage , Able to quickly restore all functions .
边栏推荐
- [Niuke] b-complete square
- ClickHouse字段分组聚合、按照任意时间段粒度查询SQL
- 2022 Google CTF segfault Labyrinth WP
- Byte P7 professional level explanation: common tools and test methods for interface testing, Freeman
- Eventbus source code analysis
- LLDP兼容CDP功能配置
- Metauniverse urban legend 02: metaphor of the number one player
- mysql: error while loading shared libraries: libtinfo. so. 5: cannot open shared object file: No such
- Taro2.* 小程序配置分享微信朋友圈
- Your cache folder contains root-owned files, due to a bug in npm ERR! previous versions of npm which
猜你喜欢
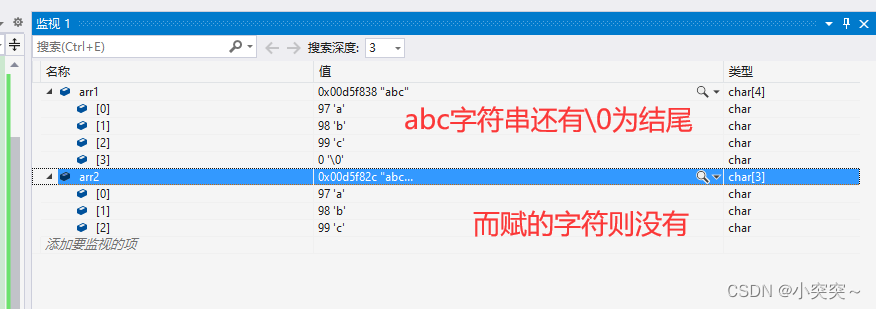
C language - array
资产安全问题或制约加密行业发展 风控+合规成为平台破局关键
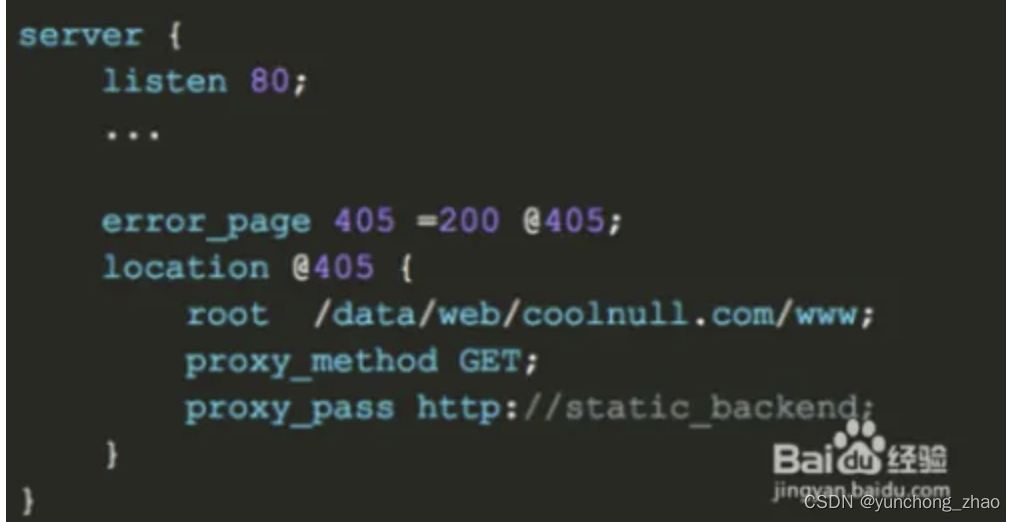
405 method not allowed appears when the third party jumps to the website
Make Jar, Not War

golang中的Mutex原理解析
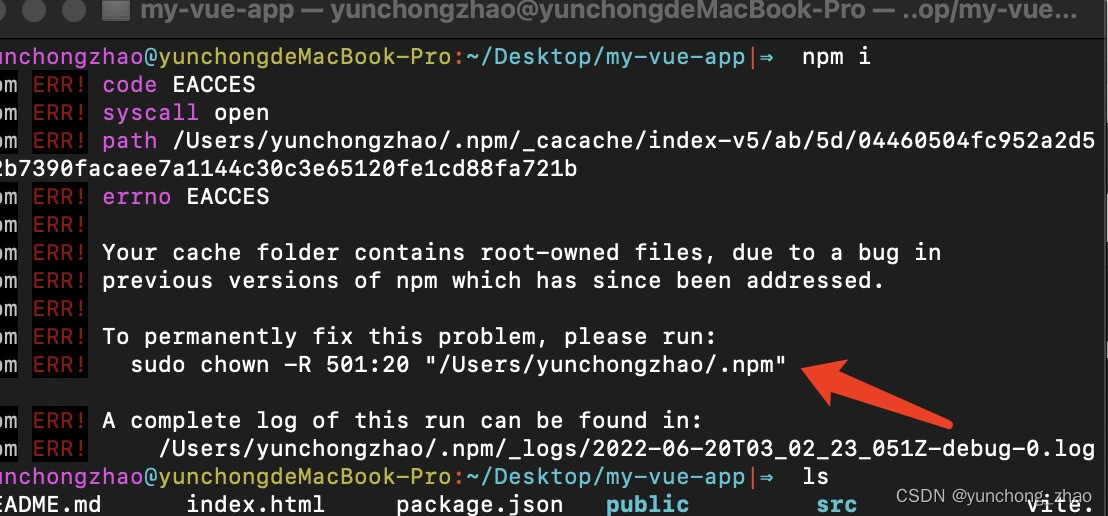
Your cache folder contains root-owned files, due to a bug in npm ERR! previous versions of npm which

云呐|工单管理办法,如何开展工单管理
Let's see through the network i/o model from beginning to end
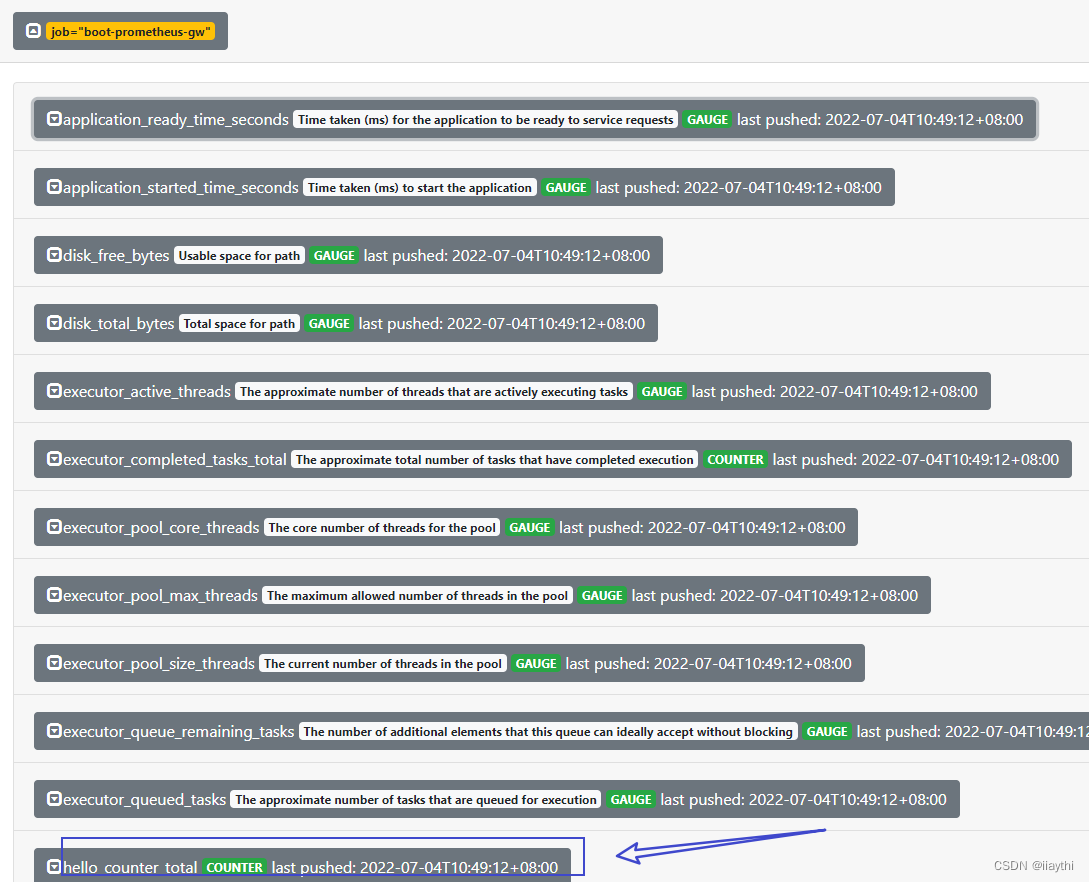
boot - prometheus-push gateway 使用
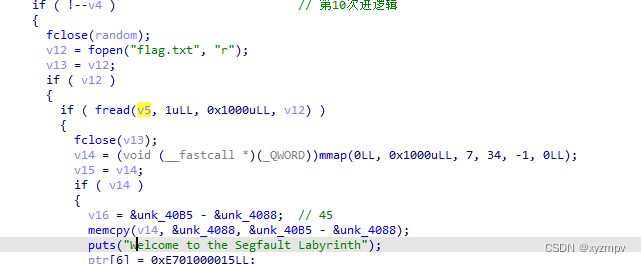
2022 Google CTF segfault Labyrinth WP
随机推荐
C# 计算农历日期方法 2022
[signal and system]
Install Firefox browser on raspberry pie /arm device
Oracle: Practice of CDB restricting PDB resources
AI 从代码中自动生成注释文档
Google发布安全更新,修复Chrome中已被利用的0 day
736. Lisp 语法解析 : DFS 模拟题
安利一波C2工具
The MySQL database in Alibaba cloud was attacked, and finally the data was found
Anfulai embedded weekly report no. 272: 2022.06.27--2022.07.03
taro3.*中使用 dva 入门级别的哦
剑指 Offer II 035. 最小时间差-快速排序加数据转换
from . cv2 import * ImportError: libGL. so. 1: cannot open shared object file: No such file or direc
golang中的WaitGroup实现原理
Neon Optimization: summary of performance optimization experience
[case sharing] basic function configuration of network loop detection
"Exquisite store manager" youth entrepreneurship incubation camp - the first phase of Shunde market has been successfully completed!
405 method not allowed appears when the third party jumps to the website
Analysis of mutex principle in golang
table表格设置圆角