当前位置:网站首页>[case sharing] basic function configuration of network loop detection
[case sharing] basic function configuration of network loop detection
2022-07-07 01:08:00 【Weisi xmws】
 Configuration requirements
Configuration requirements
Three devices Device A、Device B and Device C Form a physical ring network .
By means of Device A Configure the loop detection function on , Enable the system to shut down automatically Device A The port on which the loop appears , And inform users to check the network by printing log information .
Networking diagram

chart 1-3 Network diagram of basic function configuration of loop detection
Configuration steps
(1) To configure Device A
# establish VLAN 100, And open the global VLAN Loop detection function in .
<DeviceA> system-view
[DeviceA] vlan 100
[DeviceA–vlan100] quit
[DeviceA] loopback-detection global enable vlan 100
# configure port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 by Trunk type , And allow VLAN 100 adopt .
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] port link-type trunk
[DeviceA-GigabitEthernet1/0/1] port trunk permit vlan 100
[DeviceA-GigabitEthernet1/0/1] quit
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] port link-type trunk
[DeviceA-GigabitEthernet1/0/2] port trunk permit vlan 100
[DeviceA-GigabitEthernet1/0/2] quit
# The processing mode of global configuration loop detection is Shutdown Pattern .
[DeviceA] loopback-detection global action shutdown
# The time interval for configuring loop detection is 35 second .
[DeviceA] loopback-detection interval-time 3
(2) To configure Device B
# establish VLAN 100.
<DeviceB> system-view
[DeviceB] vlan 100
[DeviceB–vlan100] quit
# configure port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 by Trunk type , And allow VLAN 100 adopt .
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] port link-type trunk
[DeviceB-GigabitEthernet1/0/1] port trunk permit vlan 100
[DeviceB-GigabitEthernet1/0/1] quit
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] port link-type trunk
[DeviceB-GigabitEthernet1/0/2] port trunk permit vlan 100
[DeviceB-GigabitEthernet1/0/2] qui
(3) To configure Device C
# establish VLAN 100.
<DeviceC> system-view
[DeviceC] vlan 100
[DeviceC–vlan100] quit
# configure port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 by Trunk type , And allow VLAN 100 adopt .
[DeviceC] interface gigabitethernet 1/0/1
[DeviceC-GigabitEthernet1/0/1] port link-type trunk
[DeviceC-GigabitEthernet1/0/1] port trunk permit vlan 100
[DeviceC-GigabitEthernet1/0/1] quit
[DeviceC] interface gigabitethernet 1/0/2
[DeviceC-GigabitEthernet1/0/2] port link-type trunk
[DeviceC-GigabitEthernet1/0/2] port trunk permit vlan 100
[DeviceC-GigabitEthernet1/0/2] qui
Verify configuration
When configuration is complete , The system is within a loop detection interval Device A The port of GigabitEthernet1/0/1 and GigabitEthernet1/0/2 Loops have been detected on , So the two ports are automatically closed , And printed the following log information :
[DeviceA]
%Feb 24 15:04:29:663 2013 DeviceA LPDT/4/LPDT_LOOPED: Loopback exists on GigabitEthernet1/0/1.
%Feb 24 15:04:29:665 2013 DeviceA LPDT/4/LPDT_VLAN_LOOPED: Loopback exists on GigabitEthernet1/0/1 in VLAN 100.
%Feb 24 15:04:29:667 2013 DeviceA LPDT/4/LPDT_LOOPED: Loopback exists on GigabitEthernet1/0/2.
%Feb 24 15:04:29:669 2013 DeviceA LPDT/4/LPDT_VLAN_LOOPED: Loopback exists on GigabitEthernet1/0/2 in VLAN 100.
%Feb 24 15:04:44:240 2013 DeviceA LPDT/5/LPDT_RECOVERED: Loopback on GigabitEthernet1/0/1 in VLAN 100 recovered.
%Feb 24 15:04:44:243 2013 DeviceA LPDT/5/LPDT_RECOVERED: Loopback on GigabitEthernet1/0/1 recovered.
%Feb 24 15:04:44:245 2013 DeviceA LPDT/5/LPDT_RECOVERED: Loopback on GigabitEthernet1/0/2 in VLAN 100 recovered.
%Feb 24 15:04:44:248 2013 DeviceA LPDT/5/LPDT_RECOVERED: Loopback on GigabitEthernet1/0/2 recovered
Use display loopback-detection Commands can be viewed Device A Configuration and operation of upper loop detection :
# Show Device A Configuration and operation of upper loop detection .
[DeviceA] display loopback-detection
Loopback detection is enabled.
Loopback detection interval is 35 second(s).
No loopback is detected.
thus it can be seen ,Device A Is not shown on the port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 Loop detected on , This is because the loop detection function operates in Shutdown In mode , port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 After the loop appears on the, it has been automatically closed , Therefore, the loop on these two ports has been eliminated . here , Use display interface Command to view separately Device A On the port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 Status information :
# Show Device A On the port GigabitEthernet1/0/1 Status information .
[DeviceA] display interface gigabitethernet 1/0/1
GigabitEthernet1/0/1 current state: DOWN (Loopback detection down)
...
# Show Device A On the port GigabitEthernet1/0/2 Status information .
[DeviceA] display interface gigabitethernet 1/0/2
GigabitEthernet1/0/2 current state: DOWN (Loopback detection down)
...
thus it can be seen , port GigabitEthernet1/0/1 and GigabitEthernet1/0/2 Have been automatically turned off by the loop detection module .
end
边栏推荐
- 城联优品入股浩柏国际进军国际资本市场,已完成第一步
- 【JokerのZYNQ7020】AXI_ EMC。
- [100 cases of JVM tuning practice] 04 - Method area tuning practice (Part 1)
- New feature of Oracle 19C: automatic DML redirection of ADG, enhanced read-write separation -- ADG_ REDIRECT_ DML
- Let's talk about 15 data source websites I often use
- 【js】获取当前时间的前后n天或前后n个月(时分秒年月日都可)
- 第五篇,STM32系统定时器和通用定时器编程
- Threejs image deformation enlarge full screen animation JS special effect
- Come on, don't spread it out. Fashion cloud secretly takes you to collect "cloud" wool, and then secretly builds a personal website to be the king of scrolls, hehe
- Dr selection of OSPF configuration for Huawei devices
猜你喜欢

Telerik UI 2022 R2 SP1 Retail-Not Crack
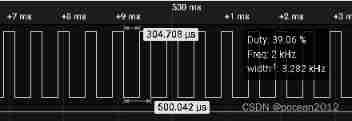
ESP Arduino (IV) PWM waveform control output

pytorch之数据类型tensor
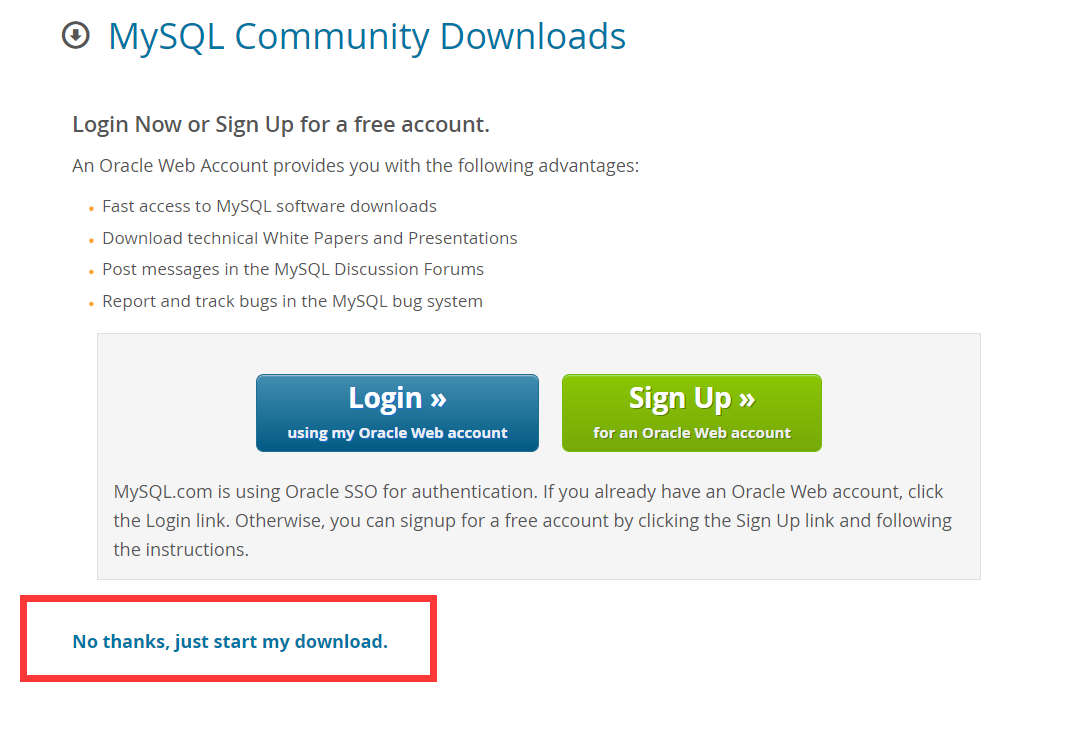
Windows installation mysql8 (5 minutes)
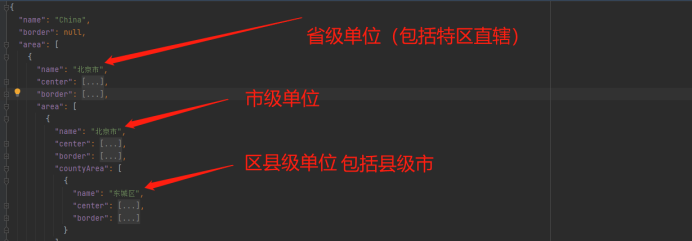
Provincial and urban level three coordinate boundary data CSV to JSON
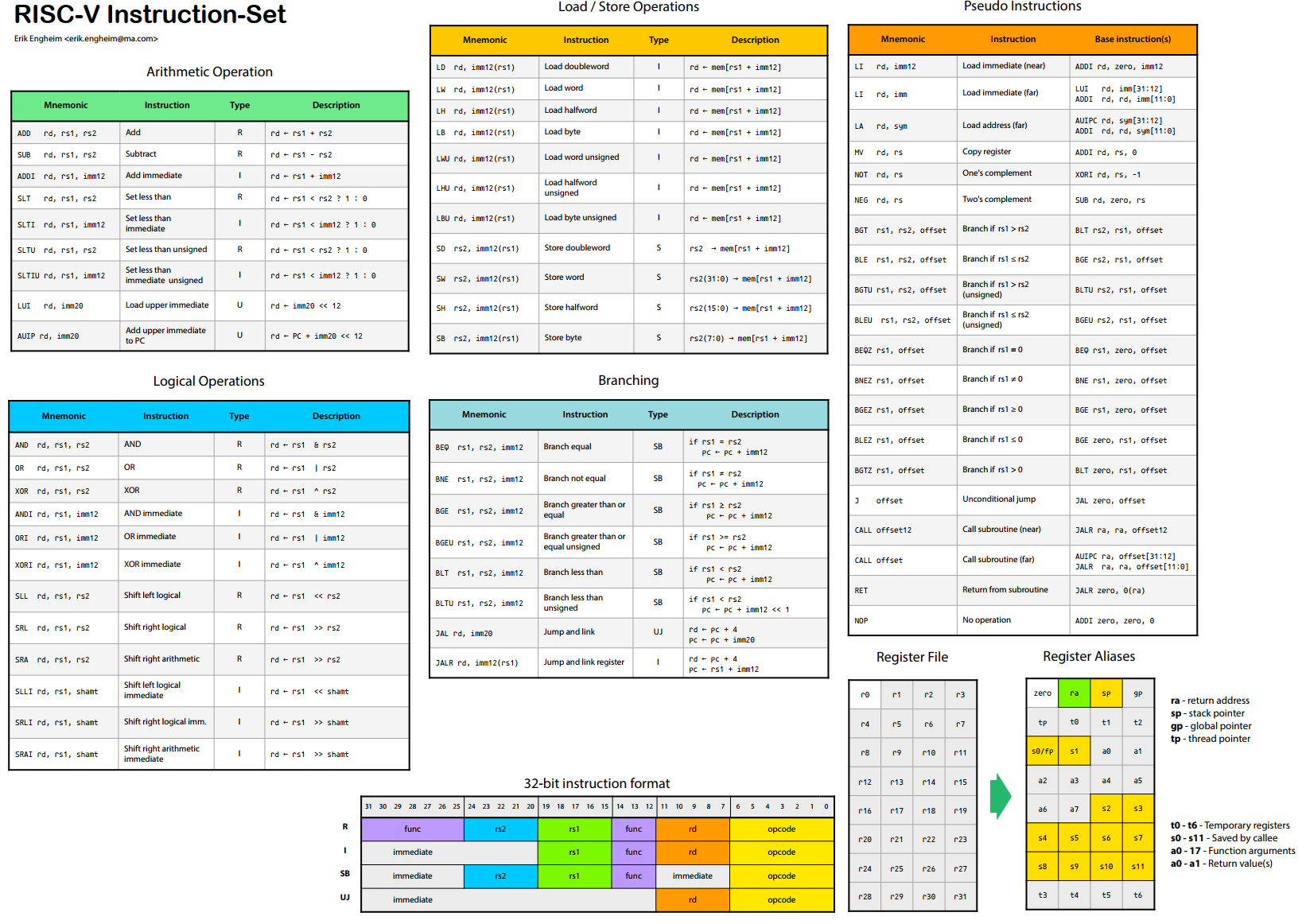
《安富莱嵌入式周报》第272期:2022.06.27--2022.07.03
Threejs image deformation enlarge full screen animation JS special effect
线段树(SegmentTree)
Do you understand this patch of the interface control devaxpress WinForms skin editor?
Make a simple graphical interface with Tkinter
随机推荐
How to get started and improve test development?
Installation of torch and torch vision in pytorch
第五篇,STM32系统定时器和通用定时器编程
[Niuke] [noip2015] jumping stone
资产安全问题或制约加密行业发展 风控+合规成为平台破局关键
Levels - UE5中的暴雨效果
Tensorflow 1.14 specify GPU running settings
【JVM调优实战100例】05——方法区调优实战(下)
Batch obtain the latitude coordinates of all administrative regions in China (to the county level)
Slow database query optimization
OSPF configuration command of Huawei equipment
Come on, don't spread it out. Fashion cloud secretly takes you to collect "cloud" wool, and then secretly builds a personal website to be the king of scrolls, hehe
Rainstorm effect in levels - ue5
[software reverse - solve flag] memory acquisition, inverse transformation operation, linear transformation, constraint solving
Configuring the stub area of OSPF for Huawei devices
pyflink的安装和测试
Chenglian premium products has completed the first step to enter the international capital market by taking shares in halber international
Learning notes 5: ram and ROM
Learn self 3D representation like ray tracing ego3rt
Explain in detail the matrix normalization function normalize() of OpenCV [norm or value range of the scoped matrix (normalization)], and attach norm_ Example code in the case of minmax