当前位置:网站首页>The difference between synchronized and lock
The difference between synchronized and lock
2022-07-04 06:57:00 【No trace after wind 2018】
Synchronized and Lock The difference between
First synchronized yes java Built in keywords ,Lock It's a java Interface ;
synchronized Unable to determine whether to acquire the lock state ,Lock It can be judged whether the lock is obtained (trylock);
synchronized Will automatically release the lock ( The lock will be released after the synchronization code is executed or an exception occurs ),Lock Need to be in finally Release the lock by hand (unlock() Method release lock ), Otherwise, it is easy to cause thread deadlock ;
use synchronized Two threads of keyword 1 And thread 2, If the current thread 1 Gets the lock , Threads 2 Thread waiting . If the thread 1 Blocking , Threads 2 Then I will wait all the time , and Lock The lock doesn't have to wait , If an attempt to acquire a lock fails , Threads can end without waiting all the time ;
synchronized The lock of can be re entered 、 Non interruptible 、 Unfair , and Lock The lock can be reentered 、 interruptible (interrupt)、 Fair enough ( Either way )
Lock Lock is suitable for a large number of synchronized code synchronization problems ,synchronized Locks are suitable for synchronization problems with a small amount of code .
边栏推荐
- Deep profile data leakage prevention scheme
- 金盾视频播放器拦截的软件关键词和进程信息
- Campus network problems
- Summary of leetcode BFS question brushing
- Lottery system test report
- How does the recv of TCP socket receive messages of specified length?
- 期末周,我裂开
- Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
- What is the use of cloud redis? How to use cloud redis?
- kubernetes集群之Label管理
猜你喜欢

颈椎、脚气
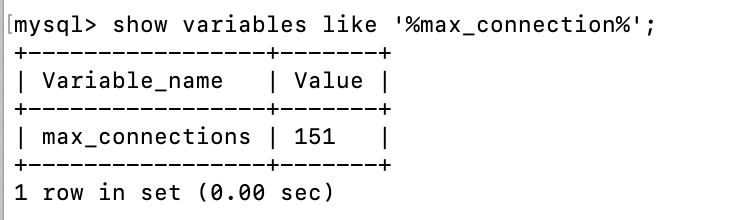
【问题记录】03 连接MySQL数据库提示:1040 Too many connections
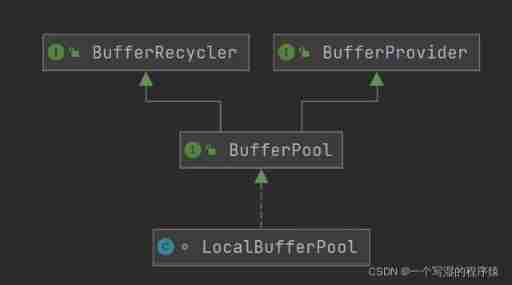
Flink memory model, network buffer, memory tuning, troubleshooting
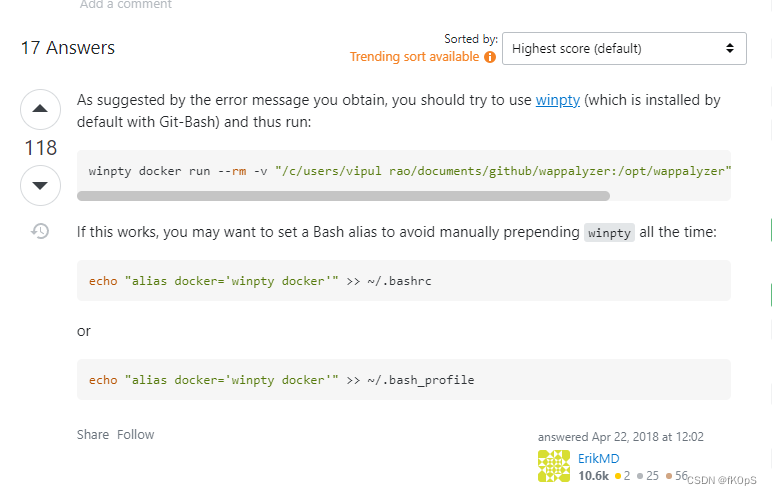
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
P26-P34 third_ template
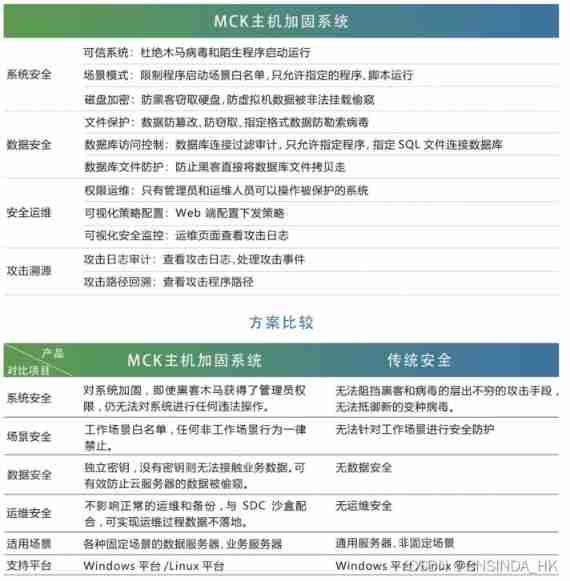
What is industrial computer encryption and how to do it

A new understanding of how to encrypt industrial computers: host reinforcement application

The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native
![[Valentine's day] - you can change your love and write down your lover's name](/img/ab/402872ad39f9dc58fd27dd6fc823ef.jpg)
[Valentine's day] - you can change your love and write down your lover's name
随机推荐
tars源码分析之9
tars源码分析之3
Set JTAG fuc invalid to normal IO port
Boosting the Performance of Video Compression Artifact Reduction with Reference Frame Proposals and
[FPGA tutorial case 7] design and implementation of counter based on Verilog
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
校园网络问题
Mysql 45讲学习笔记(六)全局锁
Selenium ide plug-in download, installation and use tutorial
How can the old version of commonly used SQL be migrated to the new version?
Tar source code analysis 8
响应式——媒体查询
CMS source code of multi wechat management system developed based on thinkphp6, with one click curd and other functions
请问旧版的的常用SQL怎么迁移到新版本里来?
What is a spotlight effect?
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
tars源码分析之7
Bottom problem of figure
Redis interview question set