当前位置:网站首页>Paradigm in database: first paradigm, second paradigm, third paradigm
Paradigm in database: first paradigm, second paradigm, third paradigm
2022-07-05 10:53:00 【It was delicious when I was young】
Tuples : A line in the table
code : A column in the table
Candidate code : can Unique identification , Such as through ( Id card number ) perhaps ( School , class , Student number ) Can uniquely identify a person ; Main attribute : Attributes that have appeared in the candidate code
Main code : Also called primary key , Choose a boss from the candidate code
Foreign code is also called foreign key . If An attribute in a relationship yes The main code in another relationship Then this attribute is foreign code
First normal form , Second normal form , Super simple introduction of the third paradigm
First normal form : Can not be further divided
For example, there are two attributes in a table :
company 、 goods ( name 、 Number ), However, the commodity can be identified by its name 、 Quantity means , Do not conform to the , andcompany 、 name 、 Numberaccord with
Second normal form : Based on the first paradigm , Eliminate partial dependence
| The order number | Product number | Product quantity | Product discounts | product price | Order amount | The order time |
|---|---|---|---|---|---|---|
| 10001 | 25 | 100 | 0.9 | 9 | 5000 | 2022-07-22 |
| 10001 | 26 | 200 | 0.8 | 9 | 7000 | 2022-07-23 |
book single Number 、 production product Number → production product Count The amount 、 production product fold buckle 、 production product price grid book single Number → book single gold forehead 、 book single when between The order number 、 Product number \to Product quantity 、 Product discounts 、 product price \\ The order number \to Order amount 、 The order time book single Number 、 production product Number → production product Count The amount 、 production product fold buckle 、 production product price grid book single Number → book single gold forehead 、 book single when between
‘ The order number ’ and ‘ Product number ’ Is the primary key of the table ( Main code ), These two fields together determine ‘ Product quantity ‘ ’ Product discounts ‘ ’ product price ‘ ,
and ‘ Order amount ’ and ‘ The order time ’ Only by ‘ The order number ’ decision , Not by Primary key (‘ The order number ’ and ‘ Product number ’) Joint decision , therefore ‘ Order amount ’ and ‘ The order time ’ yes Depends in part on the primary key
Correct version
| The order number | Product number | Product quantity | Product discounts | product price |
|---|---|---|---|---|
| 10001 | 25 | 100 | 0.9 | 9 |
| 10001 | 26 | 200 | 0.8 | 9 |
| The order number | Order amount | The order time |
|---|---|---|
| 10001 | 5000 | 2022-07-22 |
| 10001 | 7000 | 2022-07-23 |
Third normal form : Based on the second paradigm , Eliminate delivery dependency
| ID number | full name | Gender | Age |
|---|---|---|---|
| 34666666666 | Zhang San | male | 22 |
body Share Prove → surname name → sex other 、 year age Id card \to full name \to Gender 、 Age body Share Prove → surname name → sex other 、 year age
“ Gender ” and “ Age ” Although indirect dependence ‘ ID number ’, but Directly dependent on Yes. “ full name ”, Correct version
| ID number | full name |
|---|---|
| 34666666666 | Zhang San |
| full name | Gender | Age |
|---|---|---|
| Zhang San | male | 22 |
The transfer function depends on : body Share Prove → surname name → sex other 、 year age but yes sex other 、 year age ↛ surname name ↛ body Share Prove Id card \to full name \to Gender 、 Age ~~~~~~ however ~~~~~~ Gender 、 Age \not\to full name \not\to Id card body Share Prove → surname name → sex other 、 year age but yes sex other 、 year age → surname name → body Share Prove
边栏推荐
- beego跨域问题解决方案-亲试成功
- How to close the log window in vray5.2
- 脚手架开发进阶
- uniapp
- Crawler (9) - scrape framework (1) | scrape asynchronous web crawler framework
- 中职组网络安全C模块全漏洞脚本讲解包含4个漏洞的脚本
- 微信核酸检测预约小程序系统毕业设计毕设(8)毕业设计论文模板
- Honing · fusion | know that the official website of Chuangyu mobile terminal is newly launched, and start the journey of digital security!
- 2022 Pengcheng cup Web
- About the use of Vray 5.2 (self research notes)
猜你喜欢
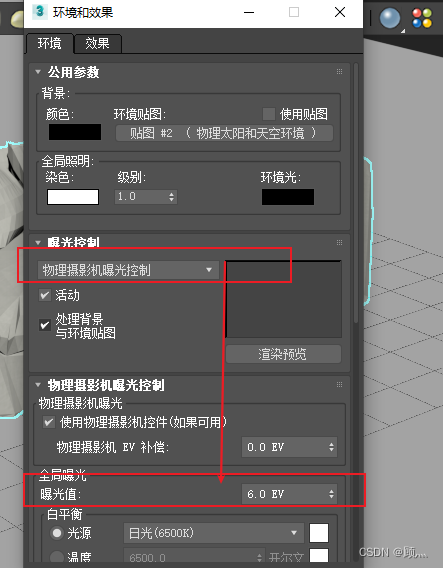
About the use of Vray 5.2 (self research notes)
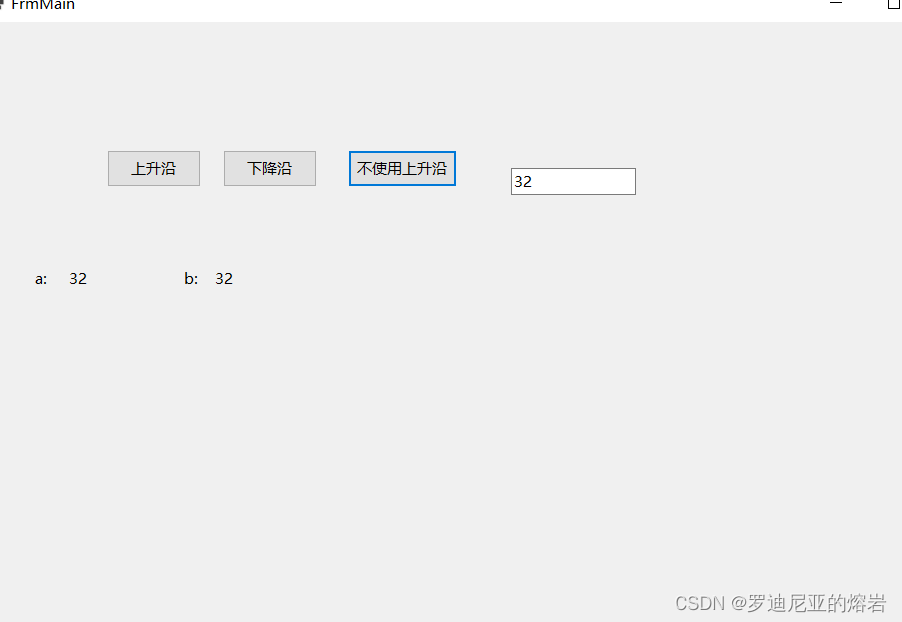
在C# 中实现上升沿,并模仿PLC环境验证 If 语句使用上升沿和不使用上升沿的不同

Web3 Foundation grant program empowers developers to review four successful projects
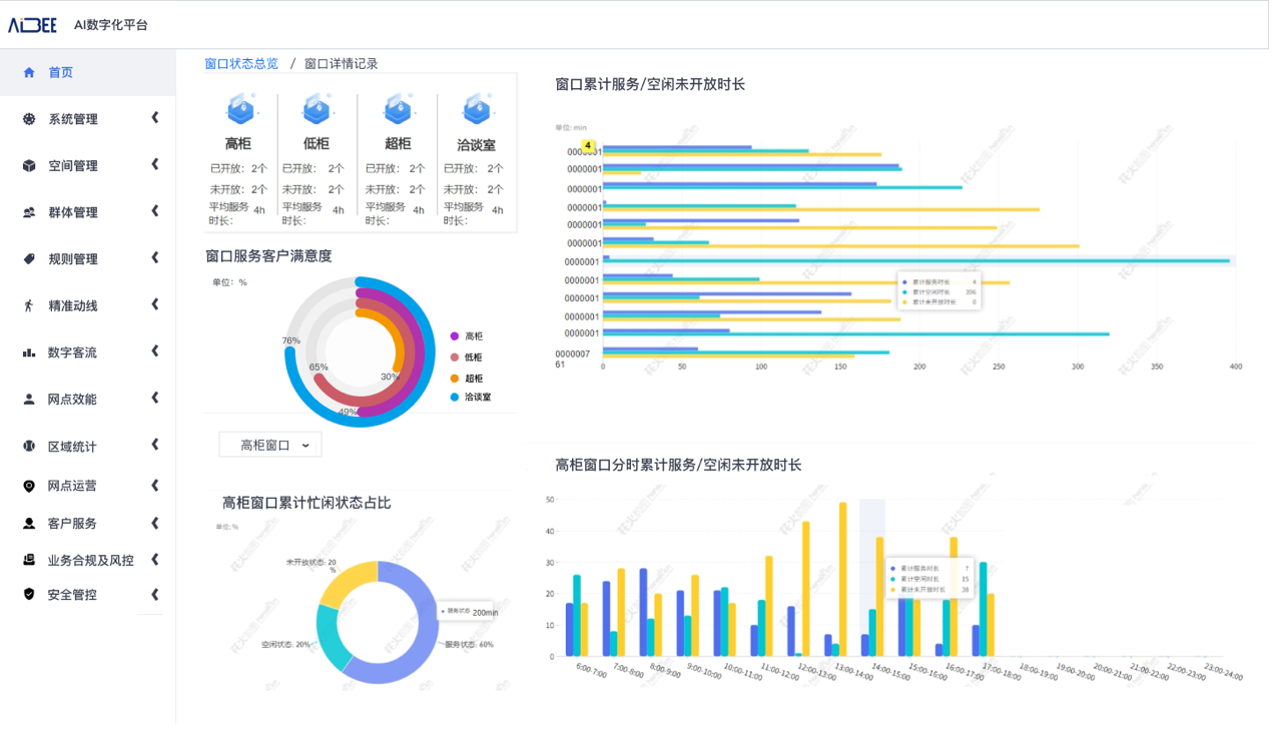
Based on shengteng AI Aibi intelligence, we launched a digital solution for bank outlets to achieve full digital coverage of information from headquarters to outlets
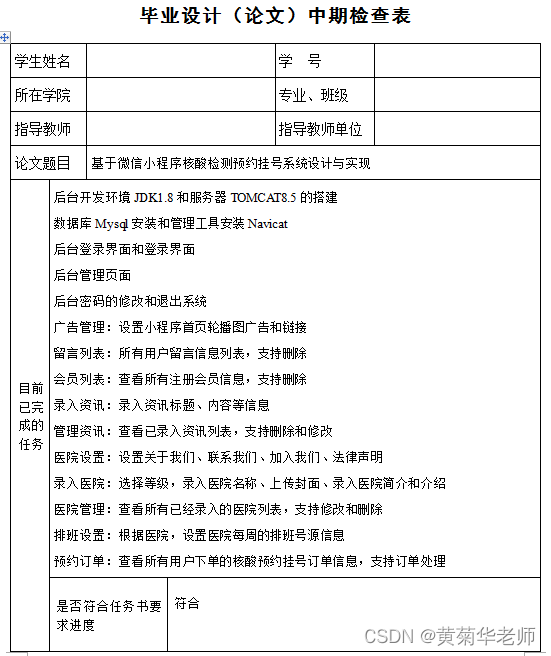
微信核酸检测预约小程序系统毕业设计毕设(7)中期检查报告
风控模型启用前的最后一道工序,80%的童鞋在这都踩坑
关于vray 5.2的使用(自研笔记)(二)

第五届 Polkadot Hackathon 创业大赛全程回顾,获胜项目揭秘!
2022 t elevator repair operation certificate examination questions and answers

2022 mobile crane driver examination question bank and simulation examination
随机推荐
关于vray 5.2的使用(自研笔记)(二)
一个可以兼容各种数据库事务的使用范例
【DNS】“Can‘t resolve host“ as non-root user, but works fine as root
Bidirectional RNN and stacked bidirectional RNN
流程控制、
使用GBase 8c数据库过程中报错:80000502,Cluster:%s is busy,是怎么回事?
C language QQ chat room small project [complete source code]
Crawler (9) - scrape framework (1) | scrape asynchronous web crawler framework
爬虫(9) - Scrapy框架(1) | Scrapy 异步网络爬虫框架
Question bank and answers of special operation certificate examination for main principals of hazardous chemical business units in 2022
Operation of simulated examination platform of special operation certificate examination question bank for safety production management personnel of hazardous chemical production units in 2022
Data types ntext and varchar are incompatible in the not equal to operator - 95 small pang
App各大应用商店/应用市场网址汇总
Go语言-1-开发环境配置
SqlServer定时备份数据库和定时杀死数据库死锁解决
Ad20 make logo
Pull up loading principle
Node の MongoDB Driver
埋点111
Applet framework taro