The first week task of information security course design (7 Analysis of instructions )
summary : This blog mainly introduces openssl Of 7 Specific functions and implementation of instructions .
7 The instructions are as follows :
dsaparam dsa enc
md_gost94
bf-ecb bf-ofb
camellia-128-cbc
One 、openssl and DSA Algorithm related instructions
openssl in DSA There are three main algorithm instructions , Namely
| Instructions | function |
| dsaparam | Generate 、 Handle DSA Key parameters , You can also generate DSA secret key |
| dsa | Handle DSA Key format conversion |
| gendsa | according to DSA The key parameter generates a DSA secret key |
This article mainly introduces the first two
1.dsaparam Instructions
dsaparam Primary user generated key parameters , It can also generate DSA The key is used as follows :
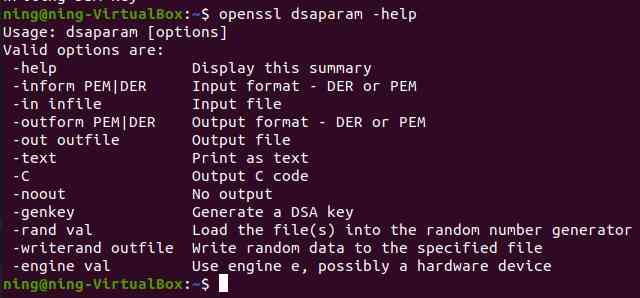
Instruction interpretation :
1.[-help]: Show summary
2.[-inform PEM|DER]:PEM|DER Input format - DER perhaps PEM
3.[-in infile]: Input file
4.[-outform PEM|DER]:PEM|DER Output format - DER perhaps PEM
5.[-out outfile]: The output file
6.[-text]: Print text as text
7.[-C]: Output C Code
8.[-noout]: No output
9.[-genkey]: Generate a DSA secret key
10.[-rand val]: Load file into random number generator
11.[-writerand outfile]: Write random data to the specified file
12.[-engine val]: Whether the engine uses the engine e, It could be hardware
Concrete realization :
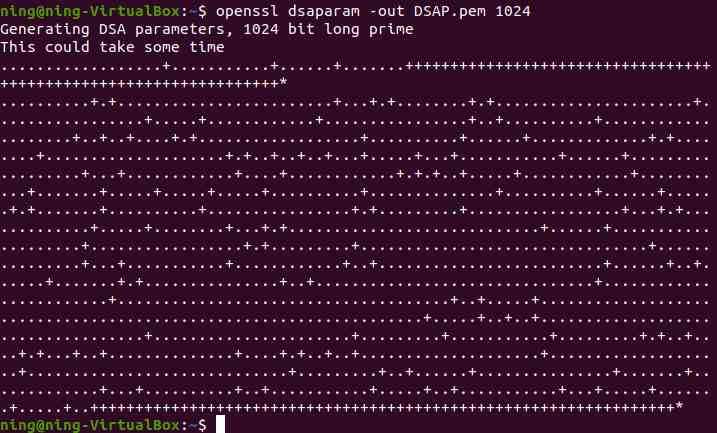
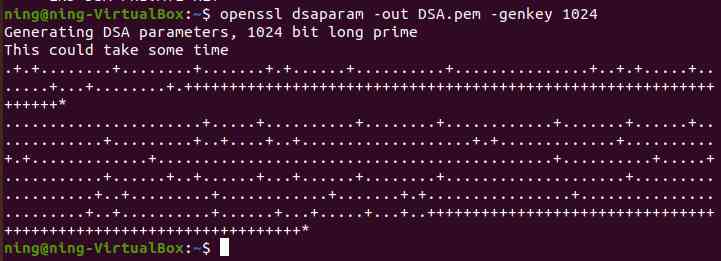
1、 Generate key parameters and view their values
(1) Generate 1024 Bit key parameter
(2) Plaintext view the value of the key parameter
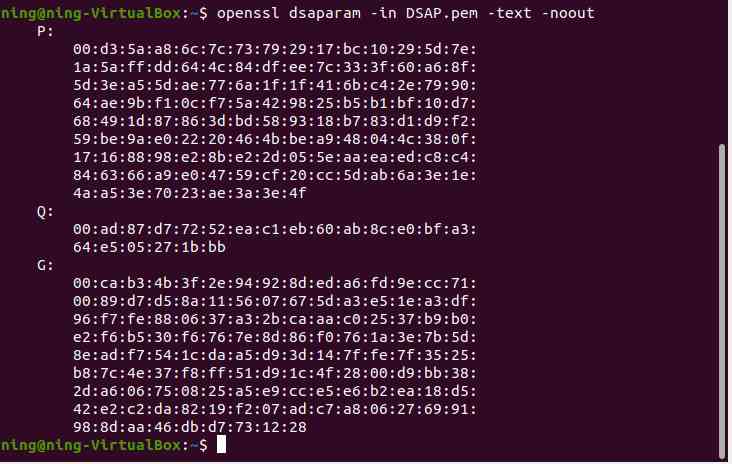
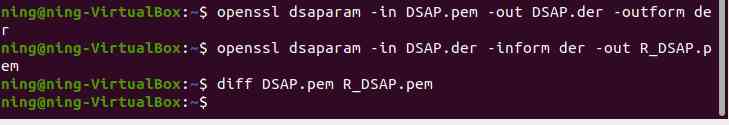
2、 Conversion between key parameter formats
The first instruction is pem The key parameters in the format are changed to der Format
The second and third order is der The key parameters in the format are changed to pem Format
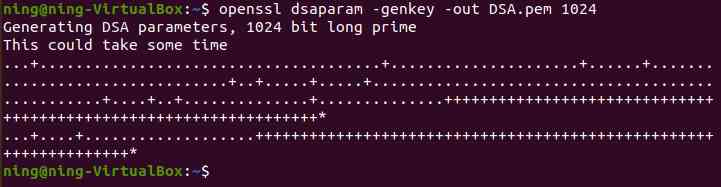
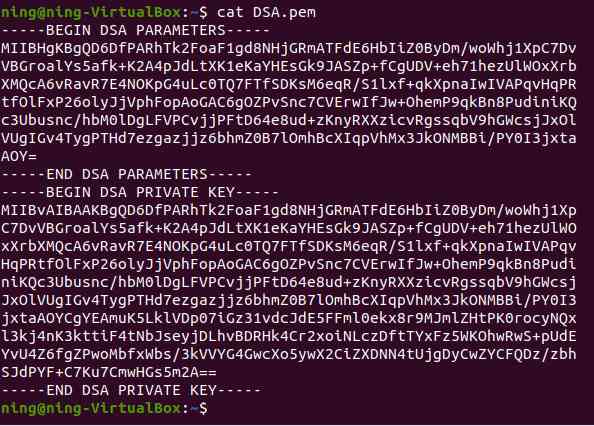
3、 Directly generate DSA secret key
(1) Directly generate DSA secret key
(2) see DSA secret key , The known parameters and keys are placed in the output file , In essence, it is a parameter , Then use the parameters to generate the key
2.dsa Instructions
dsa The command functions are as follows :
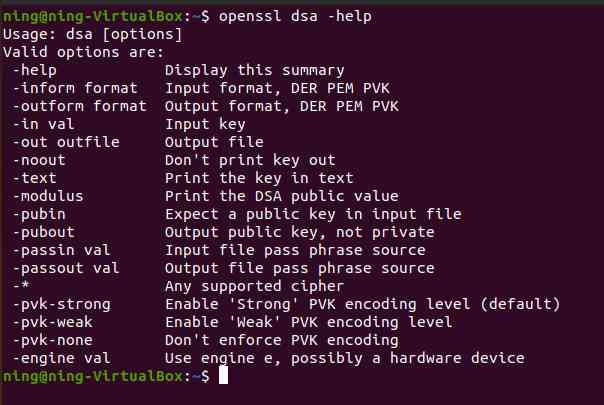
Instruction interpretation :
1.[-help]: Show summary
2.[-inform format]: Input format DER PEM PVK
3.[-outform format]: Output format DER PEM PVK
4.[- in val]: Enter the key
5.[-out outfile]: The output file
6.[-noout]: No output
7.[-text]: Print text as text
8.[-modulus]: Print DSA Public value
9.[-pubin]: Expect a public key in the input file
10.[-pubout]: Output public key , Not the private key
11.[-passin val]: Input file pass phrase source file
12.[-passout val]: Output file pass phrase source file
13.[-pvk-strong]: Enable ' strong 'PVK Coding level ( Default )
14.[-pvk-weak]: Enable ' weak 'PVK Coding level
15.[-pvk-none]: Don't force PVK code
16.[-engine val]: Whether the engine uses the engine e, It could be hardware
17.[-*]: Any supported password
Concrete realization :
1、 Encryption key and decryption key
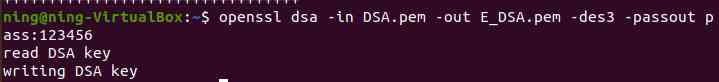
(1) Generate unencrypted DSA secret key
(2) Use des3 encryption DSA secret key
(3) Decrypt DSA secret key
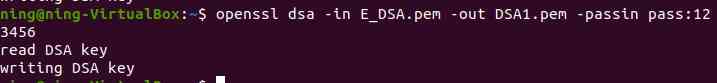
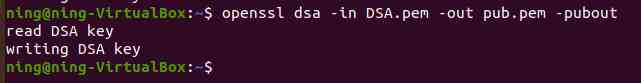
2、 extract DSA The public key
Two 、openssl Symmetric encryption algorithm enc
openssl The encryption algorithm library provides a wealth of symmetric encryption algorithms , We can go through openssl The symmetric encryption algorithm instructions are provided in the form of .
openssl Symmetric encryption algorithm instructions are mainly used to encrypt and decrypt data ,openssl Basically, it provides the application of instruction for all symmetric encryption algorithms supported by it , The names of these application instructions are basically the name of the symmetric encryption algorithm itself plus the number of digits 、 Encryption mode or combination of other attributes .
Check this machine Ubuntu edition :
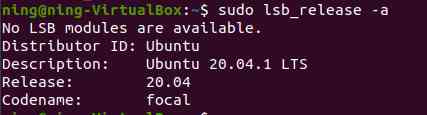
1.Ubuntu20.04 openssl edition enc The command functions are as follows :
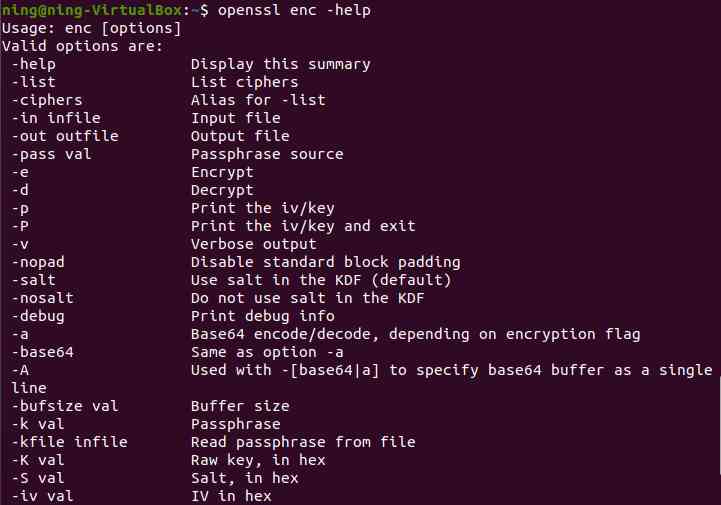
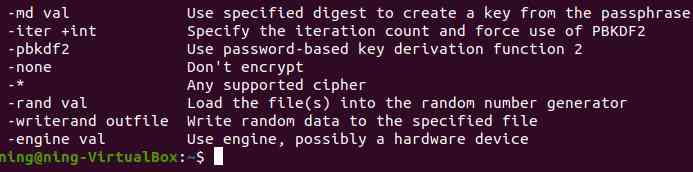
1.[-help]: Show this summary
2.[-list]: Password list
3.[-ciphers]: The nickname is attached with some
4.[-in infile]: Input file
5.[--out outfile]: The output file
6.[-pass val]: The source of the code
7.[-e/-d]: encryption
8.[-p]: Print iv/key
9.[-P]: Print iv/key And exit
10.[-v]: Detailed output
11.[-nopad]: Disable standard block padding
12.[-salt]: stay KDF Use salt in ( Default )
13.[-nosalt]: stay KDF No salt
14.[-debug]: Print debug information
15.[-a]:Base64 code / decode , Depending on the encryption flag
16:[-base64]: Same as -a
17.[-A]: And -[base64|a] Use it together , take base64 The buffer is specified as a single
18.[-bufsize val]: Buffer size
19.[-k val]: password
20.[-kfile infile]: Read the password from the file
21:[-K val]:Raw key , Hexadecimal
22.[-S val]: salt , In hexadecimal
23.[-iv val]:IV In hexadecimal
24.[-md val]: Creates a key from the pass phrase using the specified digest
25.[-iter +int]: Specifies the iteration count and PBKDF2Use Password based key derivation function 2 Mandatory use of
26.[-none]: No encryption
27.[-*]: Any supported password
28.[-rand val]: Load the file into the random number generator
29.[-writerand outfile]: Write random data to the specified file
30.[-engine val]: Whether the engine uses the engine e, It could be hardware
2. Concrete realization :
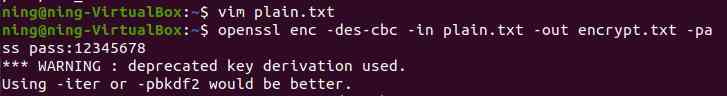
(1) Use symmetric encryption instructions as enc Instruction parameter :
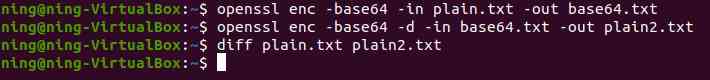
(2) Only on files base64 code , Instead of using encryption and decryption
a. On the file base64 code
b. Yes base64 Format file for decryption operation
c. Use diff Command view shows that the plaintext is the same before and after decoding
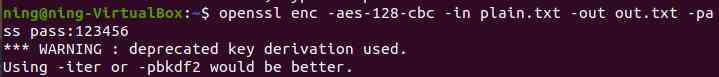
(3) Different ways of password input
a. Command line input :
b. File input :
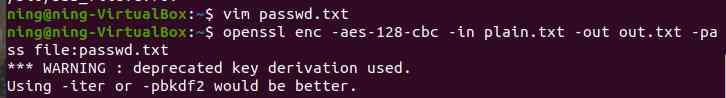
c. File description input :
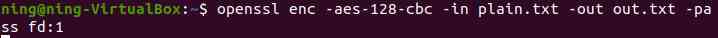
d. Input from standard input :
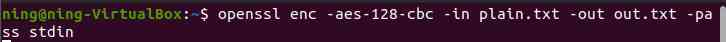
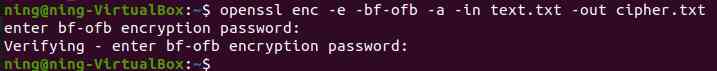
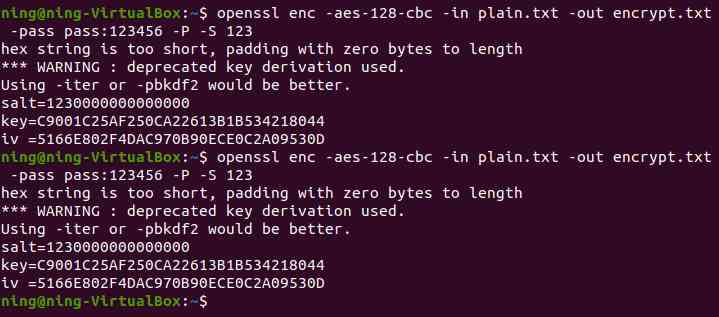
(4) Fix salt Value encryption
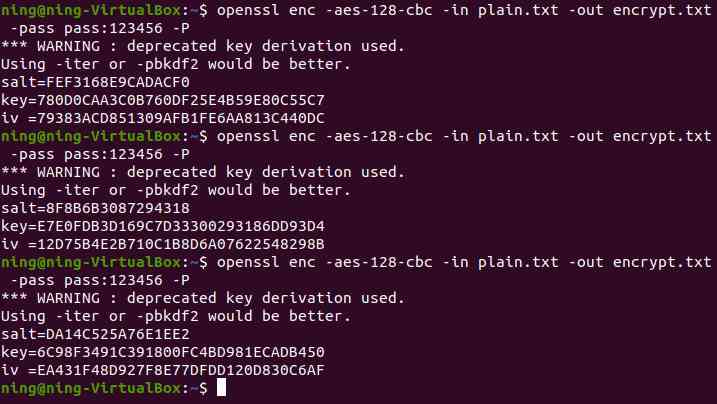
You can see , Don't use -S Parameters ,salt Parameters are generated randomly ,key and iv The values are constantly changing , When slat When the value is fixed ,key and iv The value is also fixed .
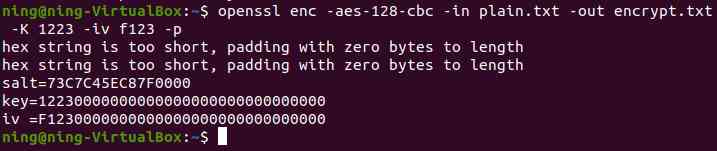
(5) Specify manually Key and IV value
Specify manually key and iv value ,salt Fix
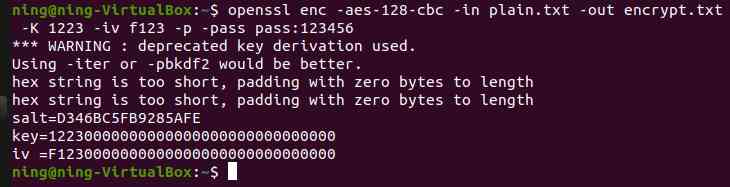
Appoint pass password , It doesn't work , Be careful Key and IV The value is 16 Base number
3、 ... and 、 Message digest command :md_gost94
Find and md_gost94 Relevant information
Encrypt the private key and PKCS12
To generate and MagPro CSP Compatible PKcs12 file , Need to use
Yes PKcs12 Document and GOST R34.11-94 The file is encrypted GOST Algorithm
Hash of the key derived from the password
Openssl pksc12-export-inkey gost.pem-in gost_cert.pem-keypbe gost89 - certpbe gost89 - macalg md_gost94
Four 、 Password command :
bf-ecb bf-ofb camellia-128-cbc
In cryptography ,camellia It means block code .Camellia The length of each block is 128 Bit , The key length can be used 128、192 or 256 Bit . Have and AES The same level of safety intensity and calculation . The two commands described here are that the key length is 256 Bits are two different encryption and decryption modes .
1.camellia-128-cbc The implementation of the
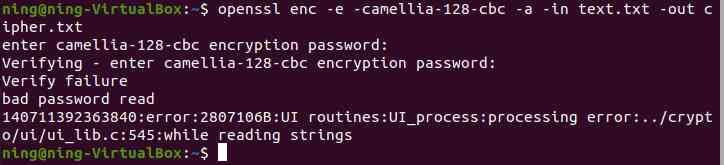
2.bf-ecb and bf-ofd The implementation of the :