当前位置:网站首页>Golang DNS write casually
Golang DNS write casually
2022-07-06 07:57:00 【Dynamic for a while, reconstructing the crematorium】
golang With built-in go Parser and based on cgo There are two kinds of system parsers DNS Analytical way
Among them in Linux The default is go built-in go Parser
DNS What is it? ? what are you having? ? What do you do ?
The domain name system ( DNS) It's a TCP/IP Distributed database of applications , It provides the host name and IP Address conversion and routing information about email
From the perspective of application , Yes DNS Is accessed through an address resolver ( resolver ) To complete . Parsers are not like TCP/IP The protocol is the kernel of the operating system .
When nameResolver Issue query request , And return... In the response TC( Delete the standard ) by 1 when , It means that the response length exceeds 512 byte , And only before returning 512 byte . So in this case ,nameResolver Usually use TCP Resend the original query request (TCP Allow responses to exceed 512 byte ).
But most of them still UDP more , It also means that for DNS Client procedure , A good retransmission and timeout program is more important
Message format
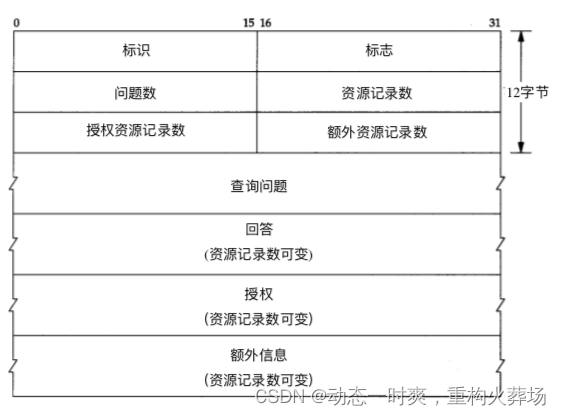
The message is sent by 12bytes The first and 4 It consists of variable length fields
identification : from client Set by server Return results , To confirm whether the response and query match
sign :
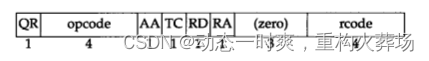
OR: 0 Representative query ,1 Represents the response message
opcode: 0 Standard query ,1 Direction query ,2 Server status request
AA: Identify authorized answers
TC: Truncated . Use UDP when , Indicates that the total length of the response exceeds 512 byte , Just before returning 512 byte
RD: Expect recursion .
This bit can be set in a query , And return... In the response . This flag tells the name server that the query must be processed , Also known as a recursive query . Such as If the position is 0, And the requested name server does not have an authorization answer , It returns a that can answer the query List of other nameservers , This is called an iterative query
RA: You can use recursion .nameServer Support recursive query
rcode: Return code field . Usually it is 0( There is no mistake ) and 3( Wrong name , Indicates that the query domain name does not exist )
Number of questions 、 Number of resource records 、 The number of authorized resource records and the number of additional resource records correspond to the last 4 Number of entries contained in variable length fields
For inquiry messages , The number of questions is usually 1, Others 3 Xiang Junwei 0; For a reply message , The number of answers is at least 1, The remaining two can be 0 Or not 0;
Query questions :
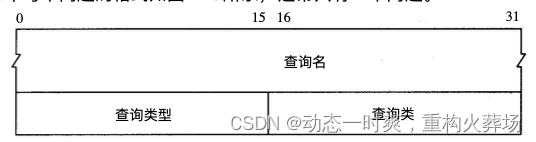
Query name : You're looking for DNS name , It is essentially a character sequence with segmented length .
Such as baidu.com. It is expressed as a character sequence
5 b a i d u 3 c o m 0Query type : Corresponding resource record type . such as A Record , Write it down as 1
Query class : Usually it is 1, Internet address (IP)
answer :
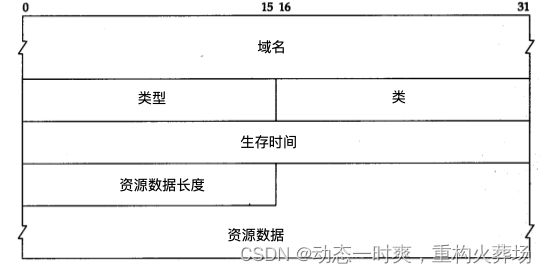
The domain name is the name corresponding to the resource data in the record . Its format is the same as the query name field format introduced above ( chart identical .
Type specification R R The type code of . Its value is the same as the query type value described earlier . Class is usually Internet data .
The time to live field is the number of seconds the client keeps the resource record . The normal lifetime value of a resource record is 2 God .
The length of resource data indicates the amount of resource data . The format of the data depends on the value of the type field . For type 1(A Record ) The resource data is 4 Bytes of I P Address .
Resource records
- A: 32bit Binary number , Record ipv4 Address
- AAAA: ipv6 Address
- cname: Indicates the name of the specification (canonical name). Used to represent a domain name
go dns technological process
- Read /etc/resolv.conf
- Judgment analytic network type . Default ipv4、ipv6 All analysis , If specified ip type , Only this type .
- according to /etc/resolv.conf in single-request and single-request-reopen Parameters , Decide whether serial or parallel requests ip type
- Traverse nameserver And parsing ip type , In order to get cname、ip Information
cgo vs go
cgo It's called getaddrinfo.
int getaddrinfo(const char *restrict node,
const char *restrict service,
const struct addrinfo *restrict hints,
struct addrinfo **restrict res);
Compared with ,go The advantage is that in case of congestion , Only one coordination process will be consumed , and cgo It will block the system thread
DNS Related configuration Introduction
/etc/resolv.conf The file is introduced
resolv.conf Used for setting up DNS Server's ip Address and DNS domain name , It also includes the host domain name search order
The main parameters are as follows
- nameserver: Definition DNS The server IP Address
- domain: Define local domain name
- search: Define the domain name search list . Indicate the order of domain name query , When there is no domain Will use search
- sortlist: Sort the returned domain name
And optional parameters
- ndots: If the number of parameter points of the requested domain name is greater than ndots Small , Will follow the configuration search Content , Add the corresponding suffixes in turn to get the address after domain name resolution
For example, request www.baidu.com when , because www.baidu.com There are two points smaller than the configured 3 A little bit , Then it will
nameserver 169.254.20.10
nameserver 172.16.0.10
search meipian-test.svc.cluster.local svc.cluster.local cluster.local
options ndots:3
| Domain name resolution | Query type | dns server |
|---|---|---|
| www.baidu.com.meipian-test.svc.cluster.local. | A | 169.254.20.10 |
| www.baidu.com.meipian-test.svc.cluster.local. | A | 172.16.0.10 |
| www.baidu.com.meipian-test.svc.cluster.local. | AAAA | 169.254.20.10 |
| www.baidu.com.meipian-test.svc.cluster.local. | AAAA | 172.16.0.10 |
| www.baidu.com.svc.cluster.local. | A | 169.254.20.10 |
| www.baidu.com.svc.cluster.local. | A | 172.16.0.10 |
| www.baidu.com.svc.cluster.local. | AAAA | 169.254.20.10 |
| www.baidu.com.svc.cluster.local. | AAAA | 172.16.0.10 |
| www.baidu.com.cluster.local. | A | 169.254.20.10 |
| www.baidu.com.cluster.local. | A | 172.16.0.10 |
| www.baidu.com.cluster.local. | AAAA | 169.254.20.10 |
| www.baidu.com.cluster.local. | AAAA | 172.16.0.10 |
| www.baidu.com. | A | 169.254.20.10 |
| www.baidu.com. | A | 172.16.0.10 |
| www.baidu.com. | AAAA | 169.254.20.10 |
| www.baidu.com. | AAAA | 172.16.0.10 |
Look at the long string above , We can't help asking why we need such splicing , And the last reason why there is one more point
This leads to a new concept ——FQDN(fully qualified domain name).FQDN Is the full domain name , With . End means FQDN
about FQDN The system will directly query DNS server
But not for FQDN It will be used ndots combination search Combination for FQDN
go built-in DNS Default resolution ipv6
Because many domain names do not support ipv6, And the processing strategies that are not supported are not consistent .
For example, use 114.114.114.114 DNS Server query baidu ipv6 You'll get noerror, It is said that the query was successful , But only soa
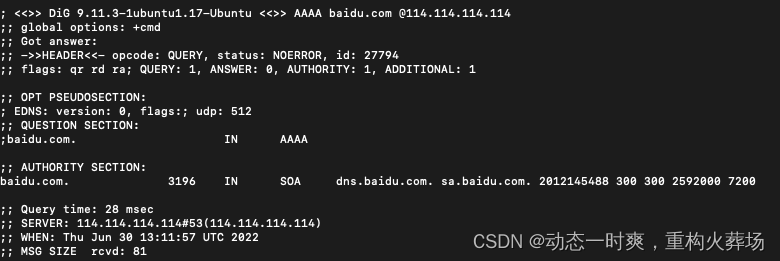
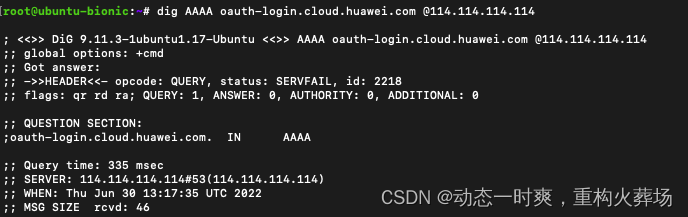
Another example is the same 114.114.114.114 DNS Server query oauth-login.cloud.huawei.com ipv6, But I got servfail, And the inquiry time is really touching . So many scenes are disabled ipv6 Parsing is still very meaningful
stay go1.17 after , We can specify the network type by , Reach query host ip Is disabled ipv6 Purpose .
r:=net.Resolver{
PreferGo: true}
ip, err := r.LookupIP(context.Background(), "ip4", host)
if err != nil {
t.Fatal(err)
}
fmt.Println(ip)
DNS attack
DDOS
Distributed denial of service attacks (distributed denial-of-service, DDoS) It's a malicious attack , The purpose is through a large number of Internet Traffic , Make the target server or its surrounding infrastructure unbearable , Thus destroying the target server 、 Normal traffic to a service or network .
DDoS The attack is realized by using multiple damaged computer systems as the source of attack traffic . The machines used can include computers and other networking resources , Like Internet of things devices .
At a high level ,DDoS The attack is like a sudden traffic jam on the highway , Make the normal traffic unable to reach the destination .
Attackers use botnets to create different ports , Send massive messages to the victim's domain name server at the same time DNS request .
In response , We can limit attackers ip
ip cheating
IP Spoofing is the creation of a modified source address Internet agreement (IP) Data packets , The purpose is either to hide the identity of the sender , Or impersonate other computer systems , Or both . Malicious users often use this technology to launch attacks on target devices or surrounding infrastructure DDoS attack
DNS Default dependency UDP, But due to the UDP Didn't like TCP The process of shaking hands , This makes ip Cheating becomes easier .
And for many based on UDP Applications may be fooled to use larger UDP Respond to small UDP Inquire about , This will result in greater bandwidth waste . This phenomenon is called amplification effect .
Answer ip Deception can be passed
- DNS cache : Absorb through cache DNS Traffic . However, it is worth noting that attackers may also take advantage of this , Add a large number of errors to the cache ip Address
- Inlet filtration : Check incoming at the network edge device ip Is the packet its source
DNS Tunnel
DNS The tunnel passes through DNS The parser creates a hidden connection between the attacker and the target , Firewall can be bypassed , Used to implement attacks such as data disclosure . in the majority of cases ,DNS The tunnel needs to use an infected system that can connect to the external network as a springboard , To access internal with network access DNS The server .
DNS Hijacking
stay DNS Hijacking , The attacker redirects the query to another domain name server . This can be done through malware or unauthorized DNS Server modification to achieve . Although the result is similar to DNS The result of cheating is similar , But this is a very different attack , Because its target is the website on the domain name server DNS Record , Instead of the parser cache .
Ref
- https://studygolang.com/topics/15021
- https://blog.csdn.net/mybelief321/article/details/10049429
- https://ieevee.com/tech/2019/06/22/ndots.html
- 《TCP/IP Detailed explanation 》
- https://zhengyinyong.com/post/go-dns-library/
- https://juejin.cn/post/6948469896007122974
- https://www.infoq.cn/article/99agzwzlewtvqjvgrtth
- https://www.cloudflare.com/en-gb/learning/ddos/what-is-a-ddos-attack
- https://www.cloudflare.com/zh-cn/learning/ddos/glossary/ip-spoofing/
- https://security.stackexchange.com/questions/155082/how-realistic-is-it-to-spoof-a-specific-udp-ip-address
边栏推荐
- Epoll and IO multiplexing of redis
- Solution: intelligent site intelligent inspection scheme video monitoring system
- Risk planning and identification of Oracle project management system
- HTTP cache, forced cache, negotiated cache
- Pre knowledge reserve of TS type gymnastics to become an excellent TS gymnastics master
- Opencv learning notes 9 -- background modeling + optical flow estimation
- Flash return file download
- http缓存,强制缓存,协商缓存
- WebRTC系列-H.264预估码率计算
- [cf gym101196-i] waif until dark network maximum flow
猜你喜欢

In the era of digital economy, how to ensure security?
A Closer Look at How Fine-tuning Changes BERT
Simulation of holographic interferogram and phase reconstruction of Fourier transform based on MATLAB
解决方案:智慧工地智能巡检方案视频监控系统
ROS learning (IX): referencing custom message types in header files
Esrally domestic installation and use pit avoidance Guide - the latest in the whole network
Document 2 Feb 12 16:54

Three no resumes in the software testing industry. What does the enterprise use to recruit you? Shichendahai's resume
Secure captcha (unsafe verification code) of DVWA range

数字经济时代,如何保障安全?
随机推荐
[cf gym101196-i] waif until dark network maximum flow
Type of data in energy dashboard
Compliance and efficiency, accelerate the digital transformation of pharmaceutical enterprises, and create a new document resource center for pharmaceutical enterprises
Three no resumes in the software testing industry. What does the enterprise use to recruit you? Shichendahai's resume
edge浏览器 路径获得
"Designer universe": "benefit dimension" APEC public welfare + 2022 the latest slogan and the new platform will be launched soon | Asia Pacific Financial Media
[t31zl intelligent video application processor data]
Leetcode question brushing record | 203_ Remove linked list elements
实现精细化生产, MES、APS、ERP必不可少
Simulation of Teman green interferometer based on MATLAB
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
08- [istio] istio gateway, virtual service and the relationship between them
Get the path of edge browser
Position() function in XPath uses
A Closer Look at How Fine-tuning Changes BERT
[untitled]
Is the super browser a fingerprint browser? How to choose a good super browser?
[Yugong series] February 2022 U3D full stack class 010 prefabricated parts
[nonlinear control theory]9_ A series of lectures on nonlinear control theory
MFC 给列表控件发送左键单击、双击、以及右键单击消息