Whether it's Android app still Jar application , Once the code is distributed , Will be in some form in an untrustworthy environment , It's hard to avoid being analyzed and cracked by people who have the intention . The secret hidden in the code , Whether it's a private algorithm , Or private agreements , Or encryption and decryption key , Can be cracked by attackers , Then infringe on the original author's commercial interests or intellectual property rights . So reverse cracking is one of the sources of business risk .
#1: Mobile application security status analysis
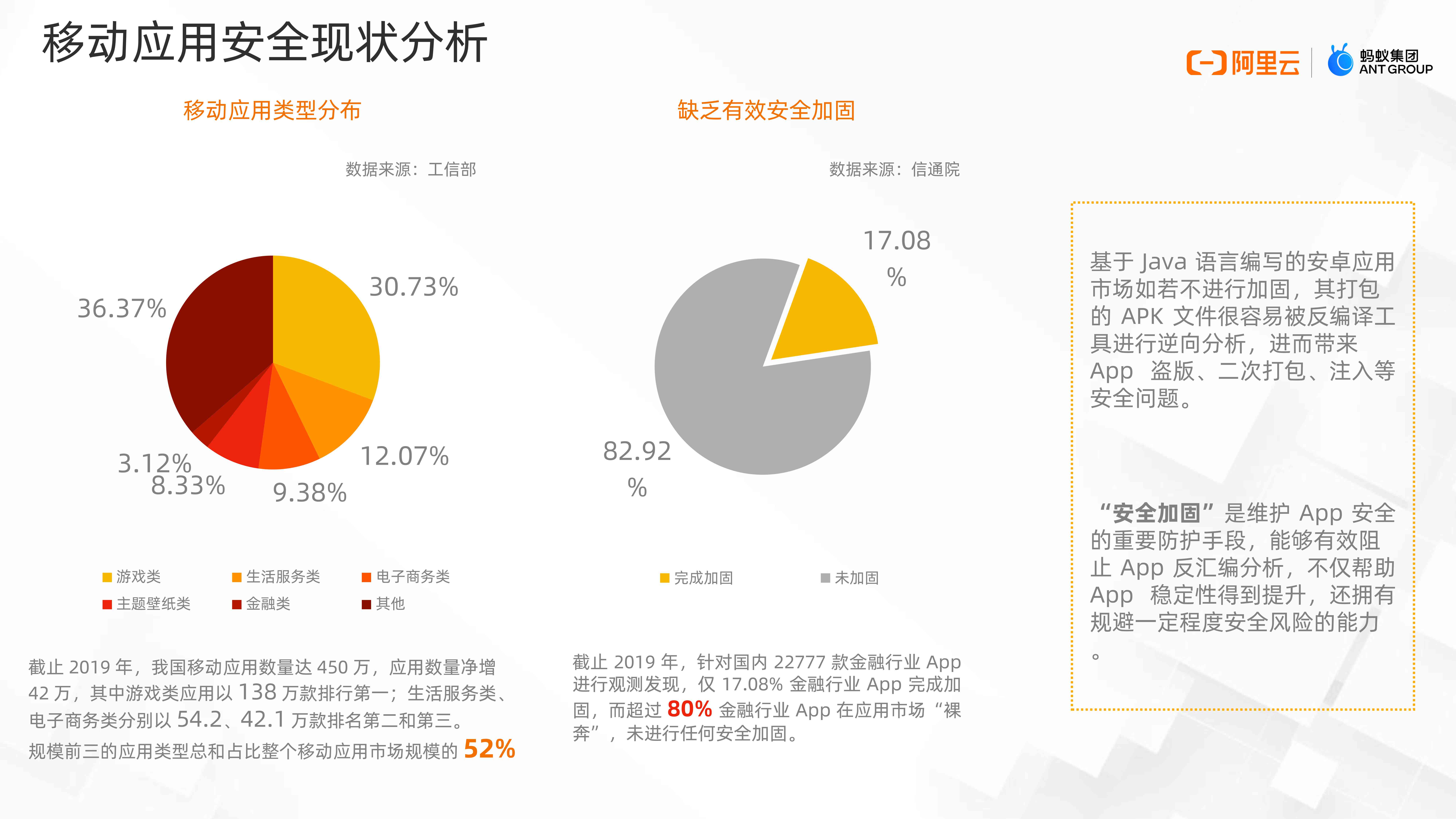
According to the Ministry of industry and information technology , end 2019 year , The number of mobile applications in China has reached 450 m , Among them, the game class 、 Life service 、 E-commerce App Top three .
Market segmentation , Let's look at the financial industry , According to the information and Communication Institute , stay 2019 year , For domestic 22777 Financial industry App Make observations and find out , only 17.08% Financial industry App Complete the reinforcement , More than 80% Financial industry App In the application market “ streaking ”, No safety reinforcement has been carried out . Look at the whole industry through the financial industry , Other industries have similar problems .
Let's look at regulatory policy again :
For the financial industry —— The people's Bank of China issued the security management specification for mobile financial client application software , Clearly regulate the mobile App Safety reinforcement requirements of .
For the education industry —— Issued by the Ministry of education 《 Opinions on guiding and standardizing the orderly and healthy development of educational mobile Internet applications 》 as well as 《 Special governance action plan for mobile Internet application in management and service education of colleges and universities 》, Education is definitely put forward by education App You should go through a security assessment before you go online , And timely through the security reinforcement to repair the hidden danger .
Through finance 、 The regulatory requirements of the education industry and the background of the country's increasing attention to the mobile Internet , Other industries may also introduce relevant safety policy requirements in succession
#2: New mobile application security protection strategy
The following describes the process of upgrading and iteration of Alibaba's internal mobile security protection strategy .
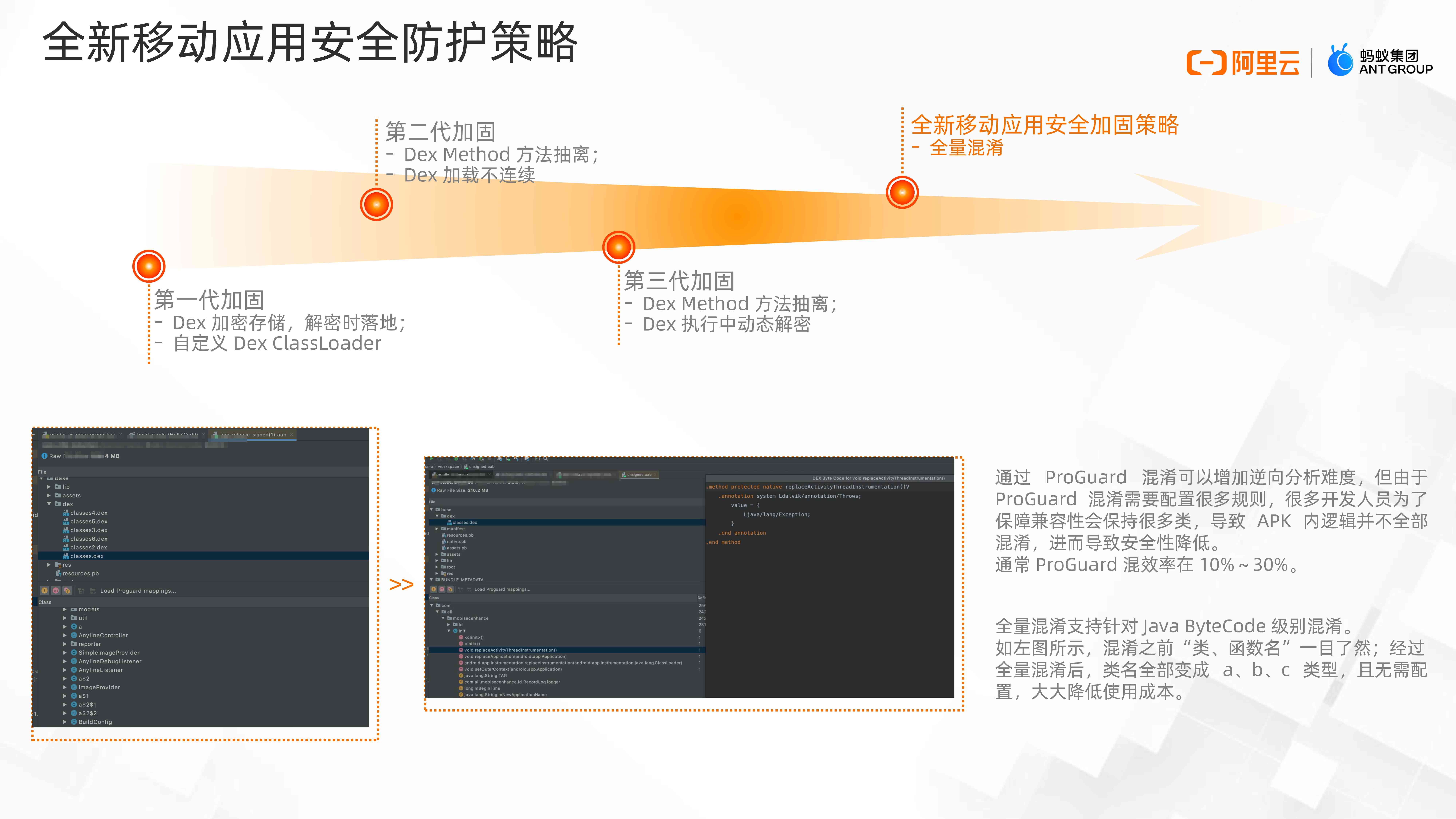
On the first and second generation reinforcement schemes , Mainly aimed at APK In the case of protection , Yes dex To hide , Encryption at the same time dex, Dynamically load encrypted at run time dex And do the shelling operation . The advantage of shell reinforcement is that it will not increase the application volume , meanwhile dex Be hidden , Can fight against dex Static analysis of .
As the means of attack continue to escalate , Alibaba mobile security reinforcement has upgraded its new capabilities . Now it has developed to the third generation of reinforcement :Java Bytecode to Native Binary code .
Ali's internal reinforcement principles and objectives adhere to not only to fully improve their own security capabilities , Increase the difficulty and cost of the attack , We should also try our best to reduce the access cost of the business side , It's also about efficiency and volume .
The main risk points to deal with :
- Java/Smali Bytecode is decompiled by the tool as Java Source code
- Java/Smali Bytecode is read directly
- native Assembly code is decompiled by the tool to C Source code
Java Bytecode because of format and instruction restrictions , There is an upper limit to the security capability . however ,native Binary code is relative to Java Bytecode cracking is much more difficult . So we convert bytecode to native Binary code , Code logic shifts to so Inside , Turned out to be Java Function call , Now it's JNI call . Of the attacker Java Reverse related skills fail directly , Forced to reverse native Binary system , And this is much more difficult than reverse bytecode .
#3:mPaaS Mobile security reinforcement heavy online
Combined with the upgrading of Alibaba's internal mobile application security reinforcement capability , We are mPaaS China and foreign countries officially launched mobile application security reinforcement capability .
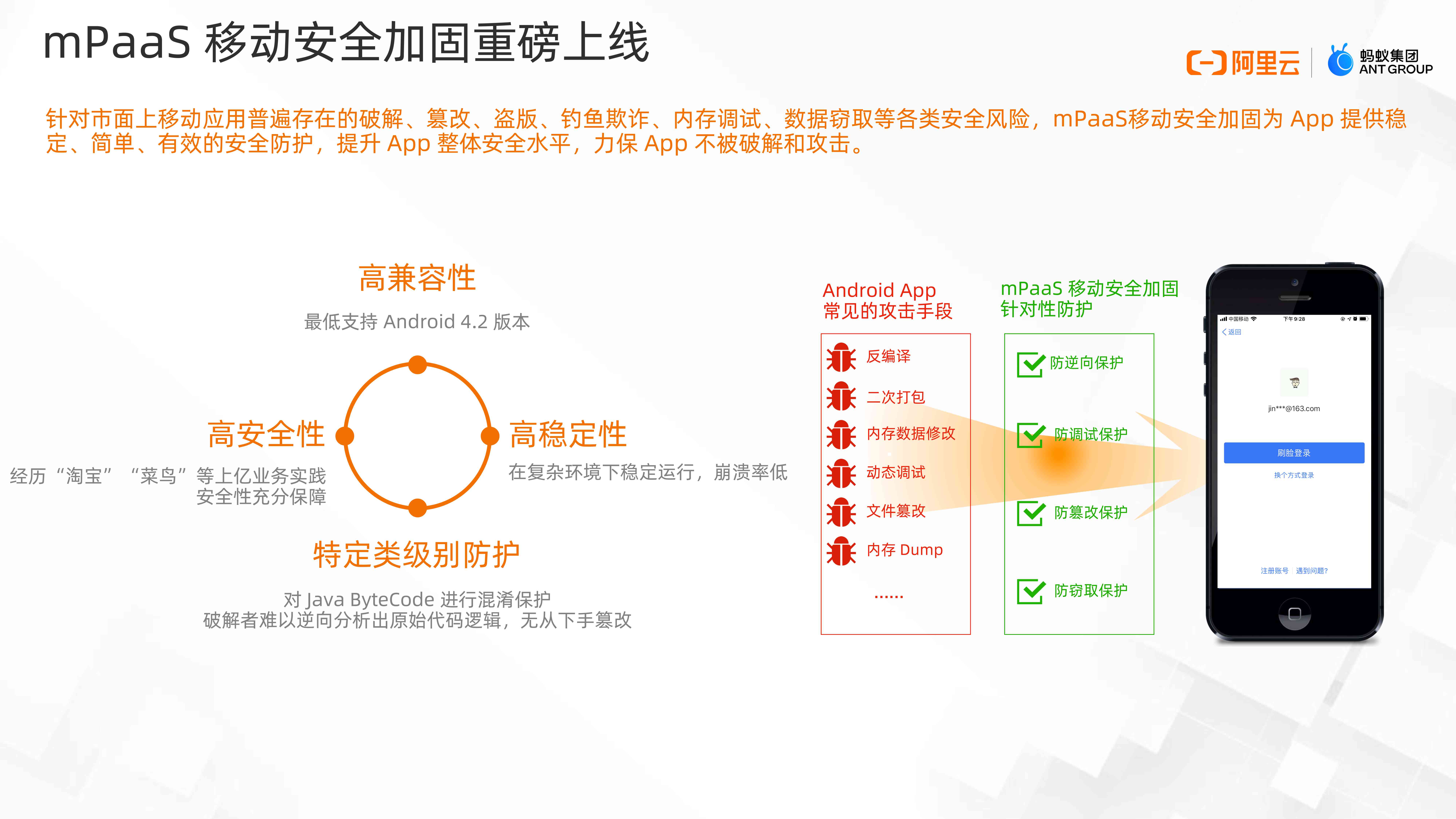
In view of the widespread mobile applications on the market 、 Tampering 、 Pirate 、 A fishing scam 、 Memory debugging 、 Data theft and other security risks ,mPaaS Mobile security reinforcement is App Provide stability 、 Simple 、 Effective safety protection , promote App Overall safety level , To ensure App Not to be cracked or attacked .
In response Android Common means of attack , such as Decompile 、 Second packing 、 Dynamic debugging, etc , We also focus on performance and compatibility .
- Strengthening ability has gone through Taobao 、 The practice of hundreds of millions of businesses such as rookies , In terms of security ;
- On compatibility , We support 4.2 To Android Q Of edition ;
- Able to support arm、x86、x64 System architecture , Stable operation in complex environment , The rate of running out is low ;
- in addition , Protection by obfuscation of classes , Increase attacker reverse App The difficulty of , Make the attack impossible .
The core value of the product
Through the previous introduction , I'm sure you're interested in mPaaS Mobile application reinforcement has a preliminary understanding , Here's a summary mPaaS Advantages of mobile application security reinforcement .
- It's easy to operate , Upload the reinforcement package on the console , Open the box . Develop students 、 Project managers, etc. can use ;
- High stability and compatibility , The collapse rate is extremely low ;
- After Taobao and other Ali Department App Validation of the , In terms of security ;
- Support at the same time Android 4.2 To Android Q And arm、x86、x64 System architecture ;
- in addition , Support Javabytecode Level of confusion protection , Increase attacker reverse App Cost of , Maximum protection App The security of .

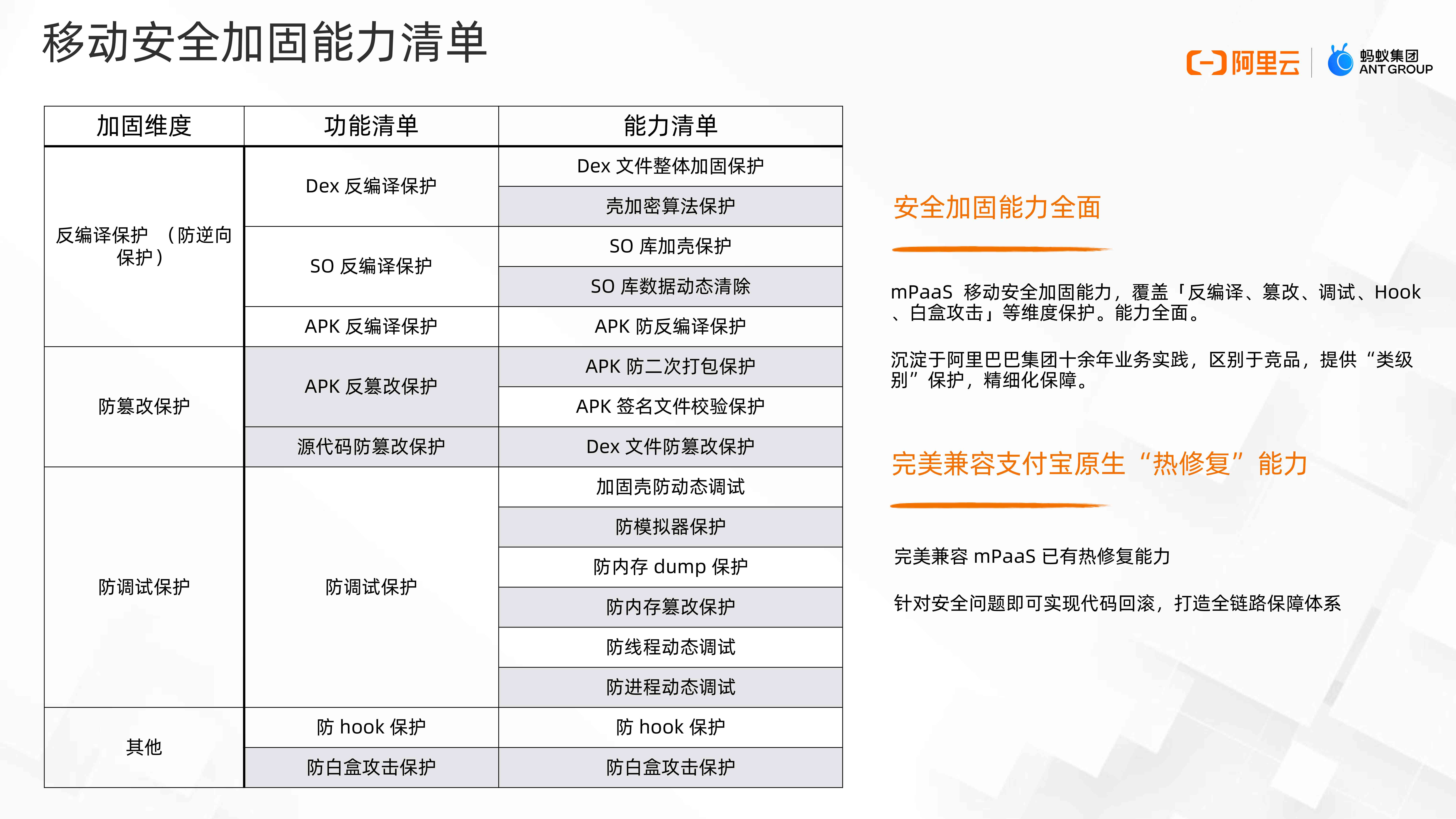
List of mobile security reinforcement capabilities
We protect from decompilation 、 Tamper protection 、 Anti debugging protection and other dimensions to do security , in the light of dex file 、so Documents and all kinds of hook The framework has made corresponding security policies , The list of capabilities is as follows :
meanwhile ,mPaaS Mobile security reinforcement is perfectly compatible mPaaS The thermal repair ability of , Through the ability to heat repair , Can quickly fix online version problems , No need to publish , Ensure business continuity , You can go to mPaaS The ability of the console to experience hot fixes .
Performance performance

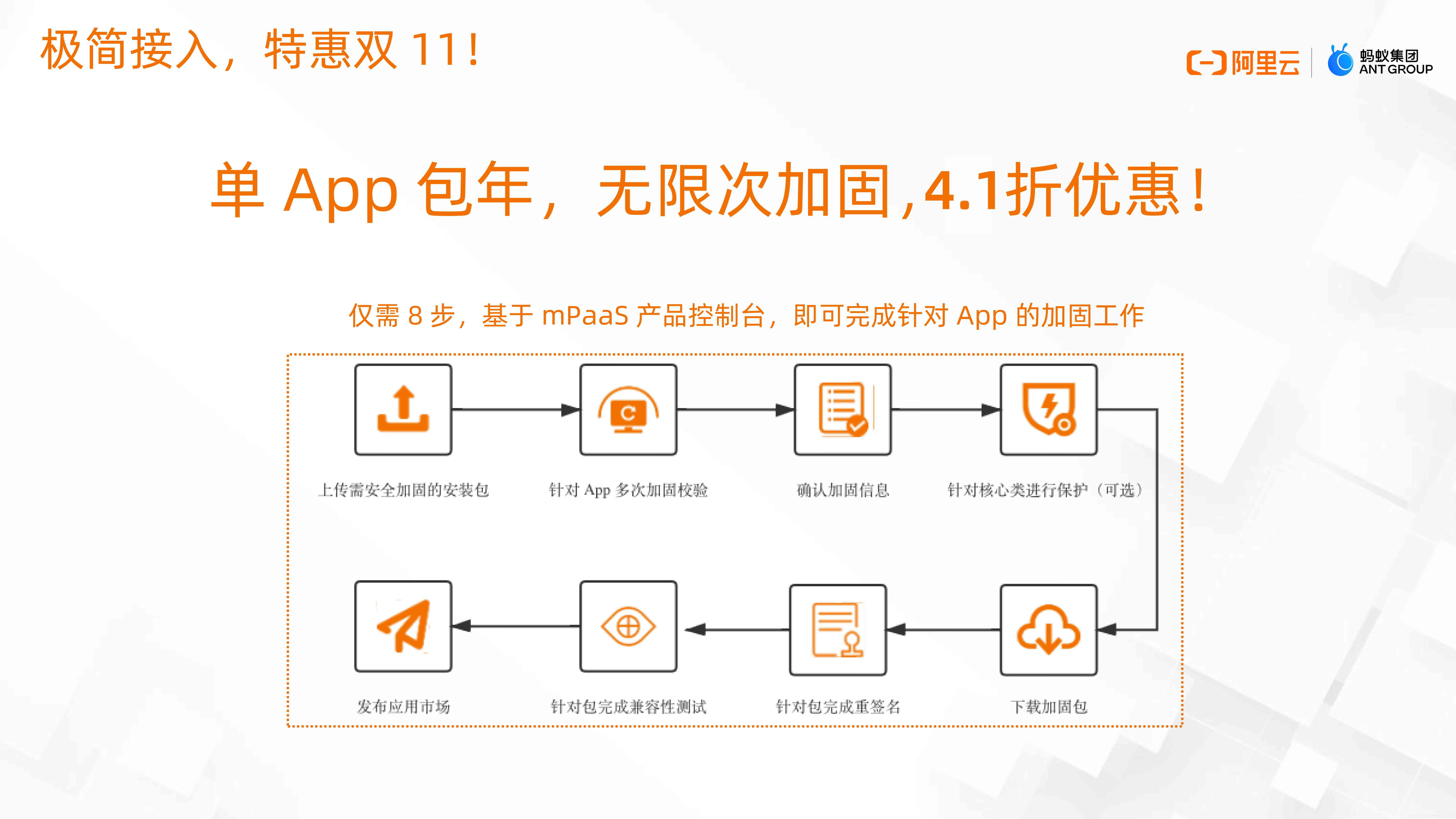
Simple access , Special offer double 11
Mobile application security reinforcement , Easy access , just 8 Step is done in no time . And in double 11 When it comes ,mPaaS Mobile security reinforcement will be officially launched on alicloud , Welcome to join the trial .
Click me back to watch live to get 4.1 Special offer for folding and reinforcing

- Hard to develop App By Shanzhai ?mPaaS Help you for APK Put on the reinforced lock
- land !Let's Start Coding
Official account “mPaaS”, reply “ Safety reinforcement ”, Get complete PPT Content