当前位置:网站首页>Use case diagram
Use case diagram
2022-07-07 14:14:00 【sinat_ thirty-six million seven hundred and eighty-nine thousan】
One 、 participants : The trigger of the use case , The trigger may be the user , It may be the agent of the event . The so-called time agent is the operation of the timing function set automatically for the system , When it reaches a certain time , The system will automatically perform the corresponding functions
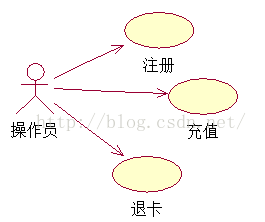
Two 、 Use cases : A use case is a series of actions performed in a system , These actions will generate value results visible to specific performers . A use case defines a set of use case instances .
Identify use case pithy : The performer uses the system to use cases
3、 ... and 、 Relationship : It describes the relationship between the performer and the use case . The relationships involved in use case diagrams are : relation 、 generalization 、 contain 、 Expand .
The relationship between the performer and the use case
In the use case diagram , The performer interacts with the use case , The relationship between them is represented by a straight line , It is called Correlation (Association) Or communication relationship (Communication)
The generalized relationship between executors
There can be generalization between executors (Generalization) Relationship ( Also known as “ Inherit ” Relationship )

Between use cases Inclusion relation
Describe common behaviors that exist in multiple use cases , By use case A Point to use case B, Represents a use case A Use cases are used in B The act or function of , Containment is achieved by applying <<include>> Structural type ( stereotype ) To represent the

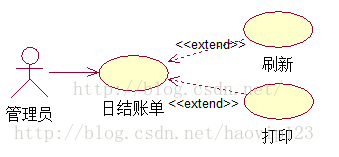
Between use cases Extended relationship
a, Extended use cases can add new behaviors on top of the base use cases , But the base use case must declare something specific “ The extension point ”, And extension use cases can only extend new behaviors on these extension points .
b, Expanding (extend) In relationship , Basic use cases (Base) There are one or more named extension points defined in , Extending a relationship means extending a use case (Extension) The event flow of is inserted into the basic use case according to the corresponding extension point under certain conditions (Base) in .
c, Extended relationships are achieved by applying <<extend>> Structural type ( stereotype ) To represent the .
Between use cases Generalization relation
a, When multiple use cases share a similar structure and behavior , Their commonalities can be abstracted as parent use cases , Other use cases as sub use cases in generalization relationship .
b, In the generalization of use cases , A child use case is a special form of a parent use case , The child use case inherits all the structure of the parent use case 、 Behavior and relationships .
c, Generalized relationships are rarely used .

边栏推荐
- 手把手教会:XML建模
- 648. Word replacement: the classic application of dictionary tree
- UML 顺序图(时序图)
- UML sequence diagram (sequence diagram)
- Introduction to sakt method
- IP address home location query full version
- Laravel5 call to undefined function openssl cipher iv length() 报错 PHP7开启OpenSSL扩展失败
- 交换机和路由器的异同
- SAKT方法部分介绍
- 2022-7-6 sigurg is used to receive external data. I don't know why it can't be printed out
猜你喜欢
通过 iValueConverter 给datagrid 的背景颜色 动态赋值
How to check the ram and ROM usage of MCU through Keil

Social responsibility · value co creation, Zhongguancun network security and Information Industry Alliance dialogue, wechat entrepreneur Haitai Fangyuan, chairman Mr. Jiang Haizhou
Parsing of XML files
Redis 核心数据结构 & Redis 6 新特性详
一个简单LEGv8处理器的Verilog实现【四】【单周期实现基础知识及模块设计讲解】
2022-7-6 Leetcode 977. Square of ordered array

Help tenants
Redis can only cache? Too out!
2022-7-6 beginner redis (I) download, install and run redis under Linux
随机推荐
【立体匹配论文阅读】【三】INTS
FCOS3D label assignment
The delivery efficiency is increased by 52 times, and the operation efficiency is increased by 10 times. See the compilation of practical cases of financial cloud native technology (with download)
最长上升子序列模型 AcWing 482. 合唱队形
Advanced Mathematics - Chapter 8 differential calculus of multivariate functions 1
常用數字信號編碼之反向不歸零碼碼、曼徹斯特編碼、差分曼徹斯特編碼
PHP中用下划线开头的变量含义
2022-7-6 Leetcode27. Remove the element - I haven't done the problem for a long time. It's such an embarrassing day for double pointers
[untitled]
3D detection: fast visualization of 3D box and point cloud
SSRF vulnerability file pseudo protocol [netding Cup 2018] fakebook1
Million data document access of course design
Vscode configuration uses pylint syntax checker
Laravel Form-builder使用
ES日志报错赏析-Limit of total fields
Realization of search box effect [daily question]
Help tenants
C # use TCP protocol to establish connection
Data flow diagram, data dictionary
First choice for stock account opening, lowest Commission for stock trading account opening, is online account opening safe