当前位置:网站首页>Leetcode exercise - 206 Reverse linked list
Leetcode exercise - 206 Reverse linked list
2022-07-05 17:50:00 【SK_ Jaco】
1. Title Description
Here's the head node of the list head , Please reverse the list , And return the inverted linked list .
Example 1:
Input :head = [1,2,3,4,5]
Output :[5,4,3,2,1]
Example 2:
Input :head = [1,2]
Output :[2,1]
Example 3:
Input :head = []
Output :[]
2. Problem solving ideas and codes
2.1 Their thinking
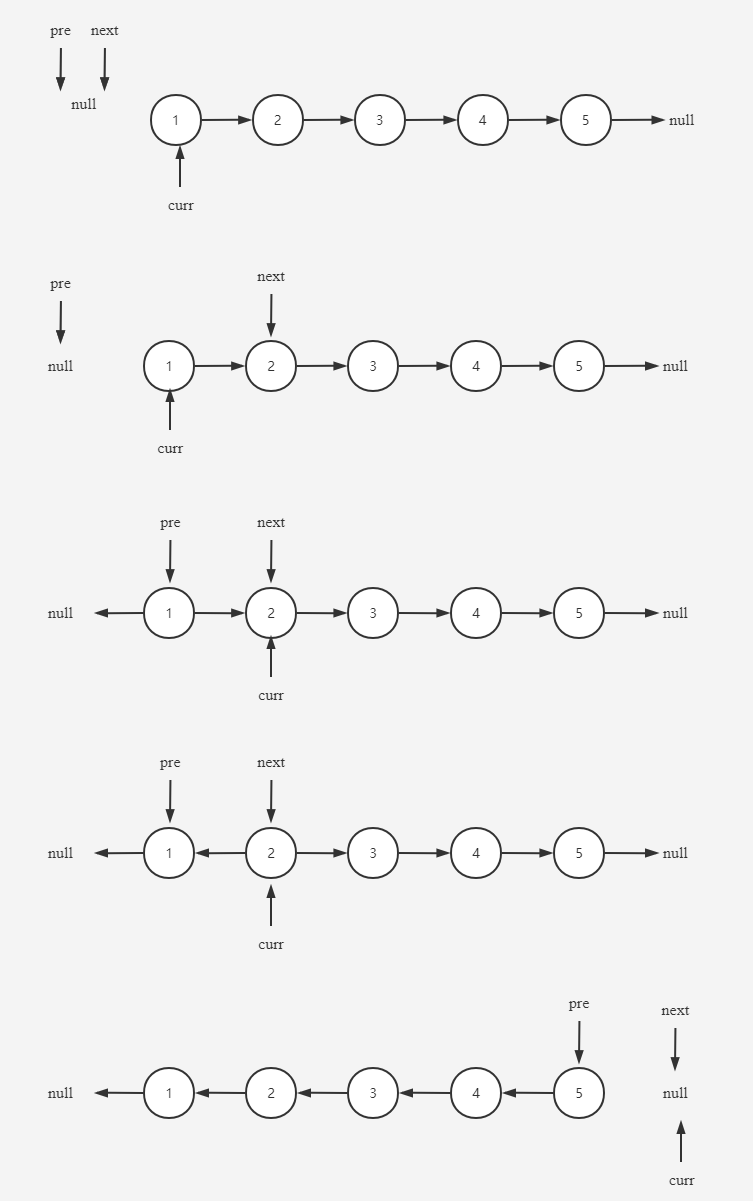
This question is relatively simple , But it is also a very common topic in the interview . The title requires reversing the linked list , You can use the stack violently to solve , But this is not simple enough, and you can't get points in the face market , And you need to traverse twice . So use three reference variables pre、next、curr To refer to the previous node 、 Next node and current node . Begin to curr Point to Head node and traverse from the head node ,next Point to the next node of the current node , Then let the current node next Point to previous node , That is to say pre. Move back pre and curr, send pre Point to the current node curr , Current node curr Move back to next. Examples of topics below 1->2->3->4->5->NULL To illustrate :
- First curr Point to the head node 1,pre and next Point to null;
- then next Point to curr The next node of 2;
- curr Of next Point to pre, also curr Move back to 2;
- Repeat the above steps , until curr Point to null, Return at this time pre Point to the node , That is, the inverted head node
2.2 Code
class Solution {
public ListNode reverseList(ListNode head) {
if (head == null) {
return null;
}
ListNode pre = null;
ListNode next = null;
ListNode curr = head;
while (curr != null) {
next = curr.next;
curr.next = pre;
pre = curr;
curr = next;
}
return pre;
}
}
2.3 test result
Pass the test
3. summary
- This is a very simple application in linked lists , Often appear in interviews
- Use pre、curr、next Three variables to complete the inversion , The whole process is not difficult, just sort out the ideas clearly
- This problem is related to The finger of the sword Offer 24. Reverse a linked list identical
边栏推荐
- 查看自己电脑连接过的WiFi密码
- 如何保存训练好的神经网络模型(pytorch版本)
- Cmake tutorial step6 (add custom commands and generate files)
- ICML 2022 | Meta提出魯棒的多目標貝葉斯優化方法,有效應對輸入噪聲
- leetcode每日一练:旋转数组
- ICML 2022 | Meta propose une méthode robuste d'optimisation bayésienne Multi - objectifs pour faire face efficacement au bruit d'entrée
- Thesis reading_ Medical NLP model_ EMBERT
- leetcode每日一题:字符串中的第一个唯一字符
- What are the requirements for PMP certification? How much is it?
- This 17-year-old hacker genius cracked the first generation iPhone!
猜你喜欢
ICML 2022 | meta proposes a robust multi-objective Bayesian optimization method to effectively deal with input noise

2022新版PMP考试有哪些变化?
Cmake tutorial Step4 (installation and testing)
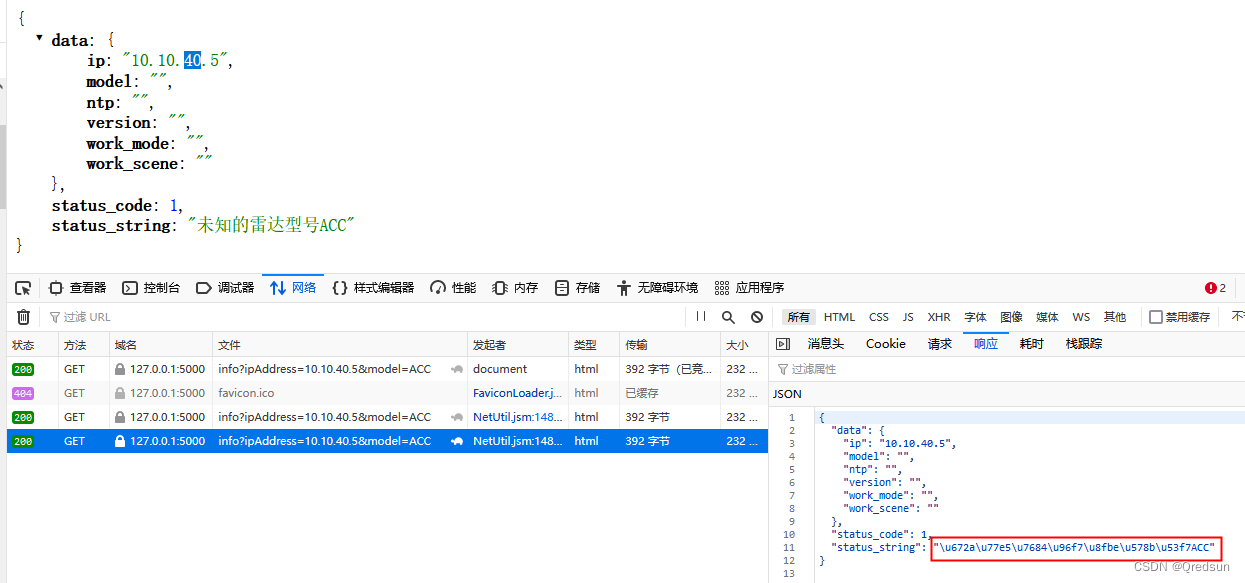
Unicode processing in response of flash interface
北京内推 | 微软亚洲研究院机器学习组招聘NLP/语音合成等方向全职研究员

What are the requirements for PMP certification? How much is it?
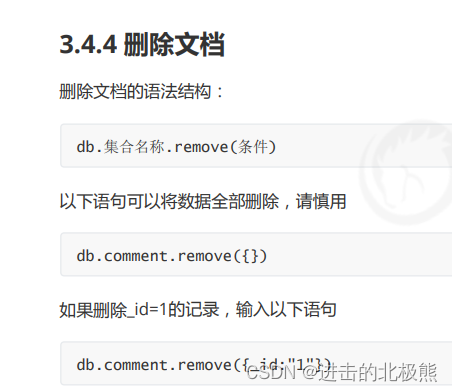
Mongodb (quick start) (I)

Beijing internal promotion | the machine learning group of Microsoft Research Asia recruits full-time researchers in nlp/ speech synthesis and other directions
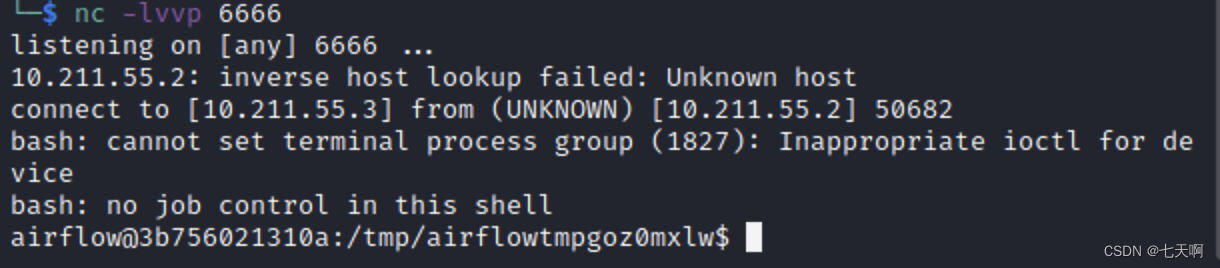
漏洞复现----48、Airflow dag中的命令注入(CVE-2020-11978)
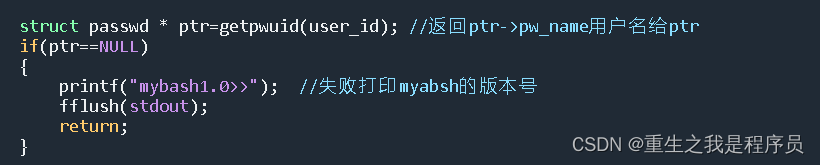
mybash
随机推荐
How to save the trained neural network model (pytorch version)
Leetcode daily practice: rotating arrays
QT console printout
2022 information system management engineer examination outline
哈趣K1和哈趣H1哪个性价比更高?谁更值得入手?
Simple query cost estimation
IDEA 项目启动报错 Shorten the command line via JAR manifest or via a classpath file and rerun.
Use QT designer interface class to create two interfaces, and switch from interface 1 to interface 2 by pressing the key
Sentinel-流量防卫兵
漫画:寻找无序数组的第k大元素(修订版)
云主机oracle异常恢复----惜分飞
ITK Example
Thesis reading_ Chinese NLP_ LTP
Abnormal recovery of virtual machine Oracle -- Xi Fenfei
Zabbix
Configure pytorch environment in Anaconda - win10 system (small white packet meeting)
LeetCode 练习——206. 反转链表
Flask solves the problem of CORS err
漫画:如何实现大整数相乘?(整合版)
Seven Devops practices to improve application performance