当前位置:网站首页>Stealing others' vulnerability reports and selling them into sidelines, and the vulnerability reward platform gives rise to "insiders"
Stealing others' vulnerability reports and selling them into sidelines, and the vulnerability reward platform gives rise to "insiders"
2022-07-06 17:51:00 【CSDN information】
Arrangement | Yu Xuan
Produce | Programmed life (ID:coder_life)
In today's highly developed network big data era , The development of each company depends on the blessing of the Internet . But at the same time , Various security vulnerabilities 、 Illegal cracking and other problems emerge in endlessly , No matter how perfect the system is, it will also be vulnerable Bug.
In this context , Instead of letting hackers find and attack security vulnerabilities that are hard to find , It's better to pay “ White hat hacker ” Disclose first , Then make repairs as soon as possible .
As mentioned in this article HackerOne Is a world-famous “ White hat hacker ” Gathering place , It is used to coordinate vulnerability disclosure , And provide an intermediary platform for vulnerability hunters who submit security reports with monetary rewards .

Picture source :CSDN Paid download from the East IC
But in recent days ,HackerOne It was revealed that one of its internal employees stole the vulnerability report submitted by others through the vulnerability reward platform , And disclose the relevant reports to the affected customers to obtain economic rewards .

The culprit is locked
6 month 22 Japan ,HackerOne Received a request from a customer , Ask them to investigate a use "rzlr " Suspicious vulnerabilities disclosed by the person of the account through non platform communication channels . The customer noticed , The same security issue has been passed before HackerOne Submitted .
Generally speaking , Vulnerability collision , That is, multiple researchers find and report the same safety problems , It happens all the time . under these circumstances , There are obvious similarities between real reports and reports from threat actors , This urges people to observe carefully .
HackerOne After investigation, it is determined , One of its employees is from 4 month 4 Joined the company on the th to 6 month 23 Japan , The platform system has been accessed for more than two months , Seven companies were contacted to report vulnerabilities that had been disclosed through their systems .

The theft vulnerability report is sold off as a sideline
The company said , The rogue employee received a reward from some reports submitted by him . This makes HackerOne Be able to track the whereabouts of money , And determine whether the perpetrator is “ Numerous customer projects ” One of the staff who disclosed the diversion vulnerability .
“ The threat actor created a HackerOne Puppet account , And received a reward in a few disclosures . After determining that these rewards may be improper , The company contacted the relevant payment supplier , They cooperated with us to provide more information .”——HackerOne
After analyzing the network traffic of the threat actor ,HackerOne More evidence has been found to link their main accounts on the platform with puppet accounts . Finally, less than... After the investigation 24 Hours of time ,HackerOne Identified the threatening actor , And terminated his system access 、 Locked his laptop remotely .
In the next few days ,HackerOne The suspect's computer was imaged and analyzed by remote forensics , And reviewed the data access log of the employee during work , To identify all vulnerability bounty projects that the threat actor has interacted with .
6 month 30 Japan ,HackerOne Fired the threatening actor :
“ According to the examination with the lawyer , We will decide whether it is appropriate to conduct criminal transfer of this matter . We continue to conduct forensic analysis on logs generated by former employees and equipment used .”—— HackerOne
HackerOne Pointed out that , Its former employees used “ Threatening ” and “ Intimidating ” Language , And urge customers to contact the company when they receive the disclosure made in an offensive tone .
HackerOne Express ,“ In the vast majority of cases ”, It has no evidence that vulnerable data has been misused . However , Reports of visits by internal threat actors , Whether for malicious or legal purposes , Have been separately informed of the access date and time of each vulnerability disclosure .
HackerOne He also sent an email to inform hackers who submitted content on the platform that had been visited by rogue employees :
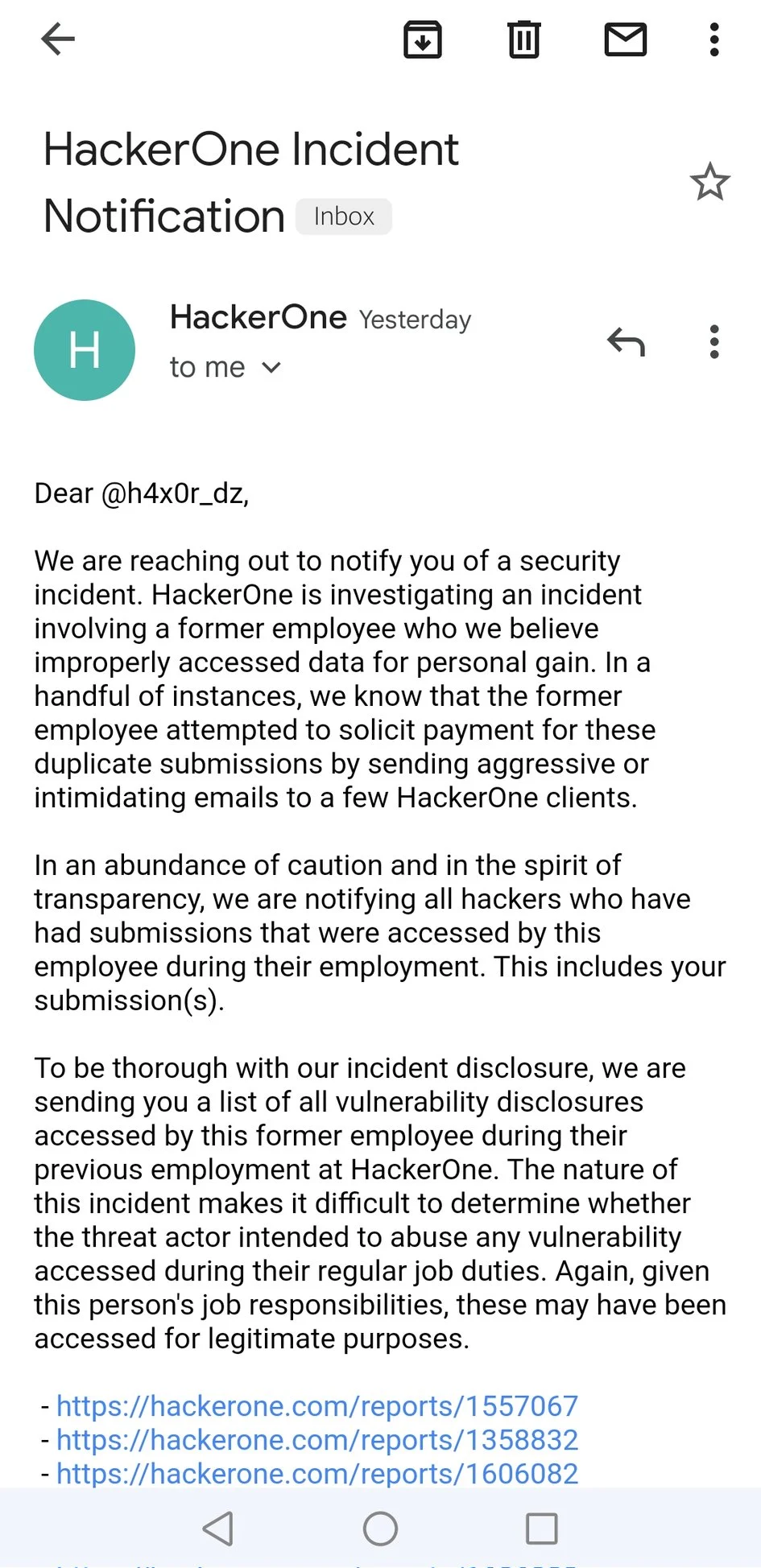
source :@H4x0r-DZ twitter
Email the hackers concerned about the incident , It also includes a list of reports of legitimate visits by threatening actors , As part of its work , Or intended to abuse the submitted vulnerability report . Besides , All reports submitted by this former employee are marked as duplicates , It will not affect the payment of legal security personnel .
HackerOne In the event report, it is concluded that :“ To make a long story short , This is a serious incident . We believe that the access of internal personnel has now been controlled . Internal threat is one of the most insidious threats in network security , We are ready to make every effort to reduce the possibility of such events in the future .”
Reference link :
https://hackerone.com/reports/1622449
https://www.bleepingcomputer.com/news/security/rogue-hackerone-employee-steals-bug-reports-to-sell-on-the-side/
https://www.pcmag.com/news/a-hackerone-employee-stole-vulnerability-reports-from-security-researchers
— Recommended reading —
* Apple let iPhone “ Squeeze toothpaste ”, Because Mac?
*IntelliJ IDEA、.NET Tools become expensive ,JetBrains Announce a rise in the price of family barrels !
* Apple 5G Chip development failed ? It's too early to get rid of Qualcomm 
边栏推荐
- Debug and run the first xv6 program
- kivy教程之在 Kivy 中支持中文以构建跨平台应用程序(教程含源码)
- How to output special symbols in shell
- BearPi-HM_ Nano development board "flower protector" case
- 基本磁盘与动态磁盘 RAID磁盘冗余阵列区分
- Xin'an Second Edition: Chapter 23 cloud computing security requirements analysis and security protection engineering learning notes
- 偷窃他人漏洞报告变卖成副业,漏洞赏金平台出“内鬼”
- Flet教程之 13 ListView最常用的滚动控件 基础入门(教程含源码)
- 面试突击63:MySQL 中如何去重?
- EasyCVR平台通过接口编辑通道出现报错“ID不能为空”,是什么原因?
猜你喜欢
PyTorch 提取中间层特征?

Selected technical experts from China Mobile, ant, SF, and Xingsheng will show you the guarantee of architecture stability
Uipath browser performs actions in the new tab

Pourquoi Li shufu a - t - il construit son téléphone portable?
In terms of byte measurement with an annual salary of 30W, automated testing can be learned in this way
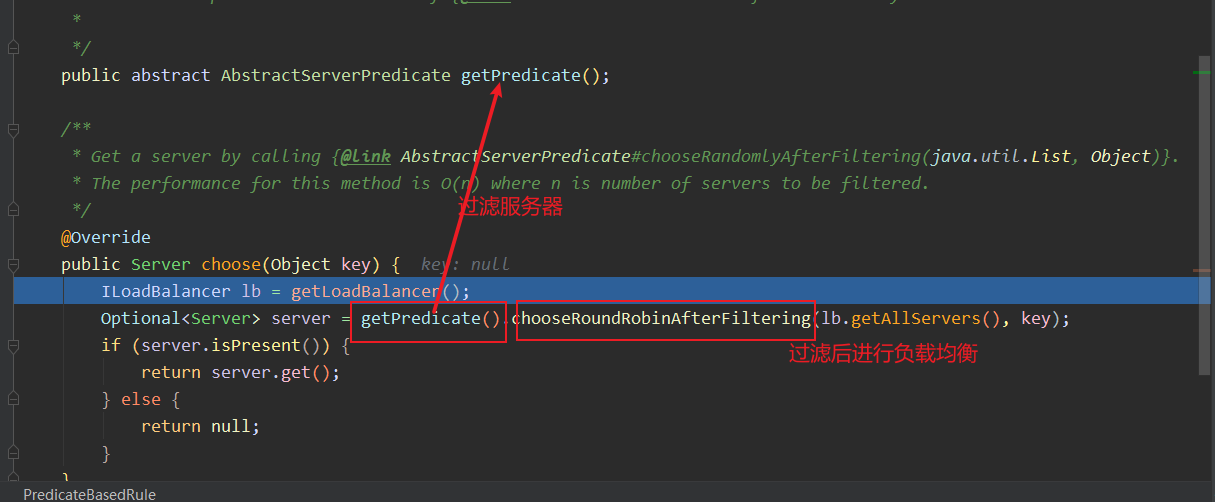
分布式不来点网关都说不过去
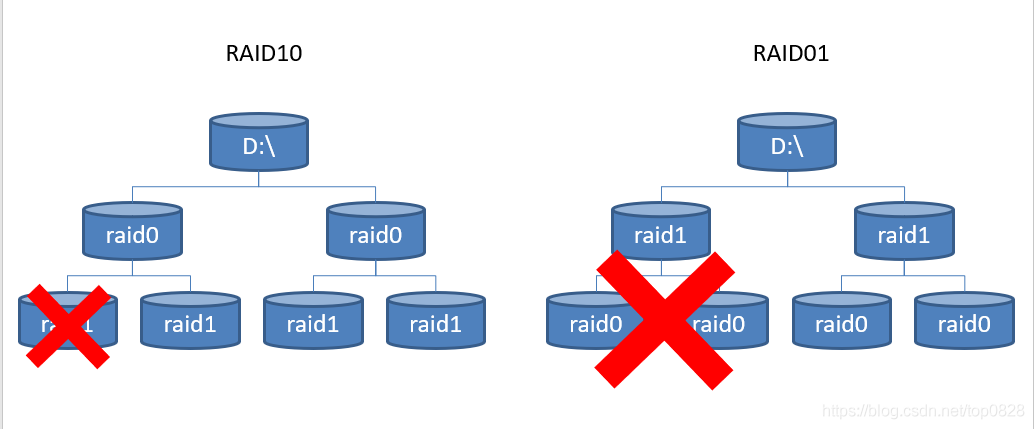
Distinguish between basic disk and dynamic disk RAID disk redundant array
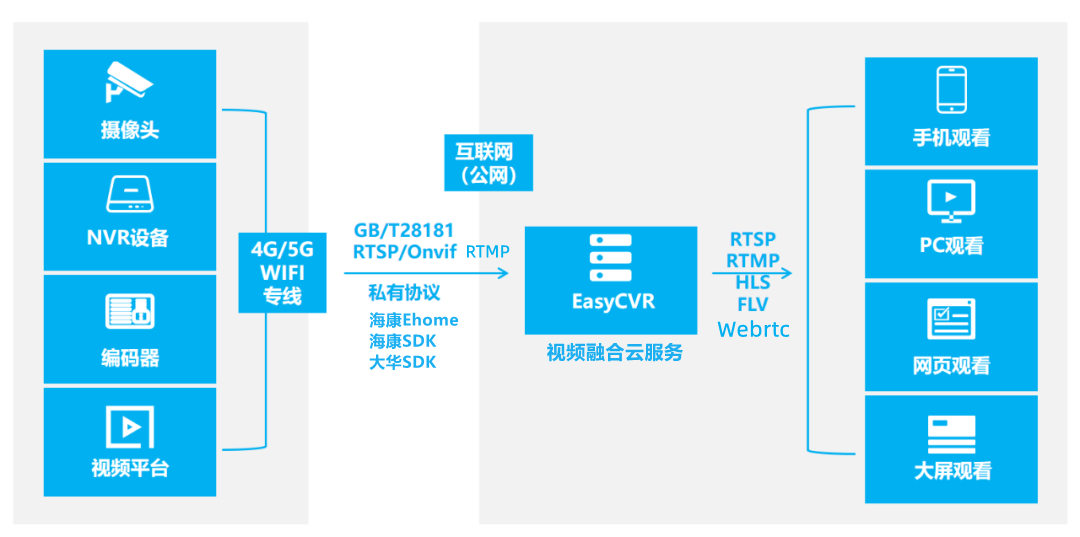
The easycvr authorization expiration page cannot be logged in. How to solve it?
Zen integration nails, bugs, needs, etc. are reminded by nails
Automatic operation and maintenance sharp weapon ansible Foundation
随机推荐
Automatic operation and maintenance sharp weapon ansible Playbook
How to use scroll bars to dynamically adjust parameters in opencv
微信小程序获取手机号
The art of Engineering (3): do not rely on each other between functions of code robustness
重磅!蚂蚁开源可信隐私计算框架“隐语”,主流技术灵活组装、开发者友好分层设计...
Growth of operation and maintenance Xiaobai - week 7
Summary of study notes for 2022 soft exam information security engineer preparation
Solrcloud related commands
The problem of "syntax error" when uipath executes insert statement is solved
node の SQLite
Nodejs 开发者路线图 2022 零基础学习指南
酷雷曼多种AI数字人形象,打造科技感VR虚拟展厅
C # nanoframework lighting and key esp32
Distributed (consistency protocol) leader election (dotnext.net.cluster implements raft election)
Example of batch update statement combining update and inner join in SQL Server
The NTFS format converter (convert.exe) is missing from the current system
【MySQL入门】第四话 · 和kiko一起探索MySQL中的运算符
Xin'an Second Edition: Chapter 24 industrial control safety demand analysis and safety protection engineering learning notes
C# NanoFramework 点灯和按键 之 ESP32
Start job: operation returned an invalid status code 'badrequst' or 'forbidden‘